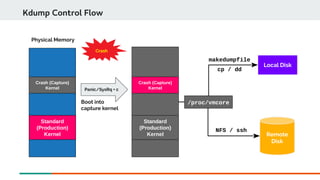
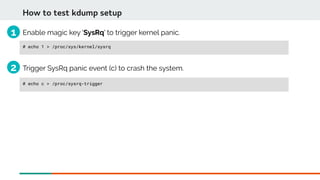
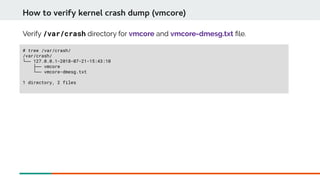
Kdump is a kernel crash dumping mechanism that uses kexec to load a separate crash kernel to capture a kernel memory dump (vmcore file) when the primary kernel crashes. It can be configured to dump the vmcore file to local storage or over the network. Testing involves triggering a kernel panic using SysRq keys which causes the crash kernel to load and dump diagnostic information to the configured target path for analysis.



![Kexec
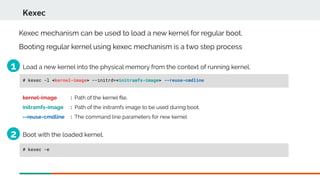
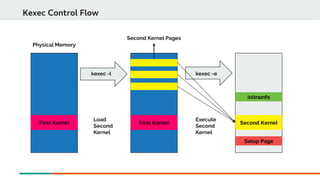
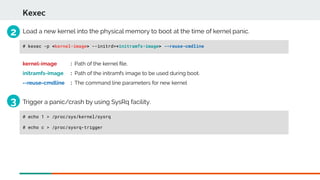
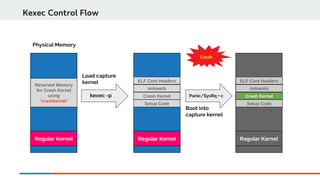
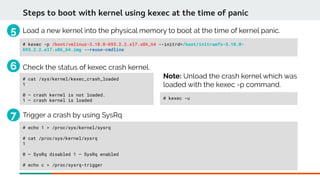
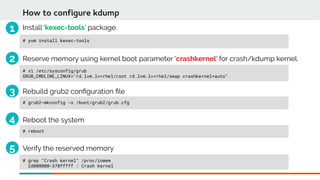
Booting with crash kernel using kexec mechanism is a three step process:
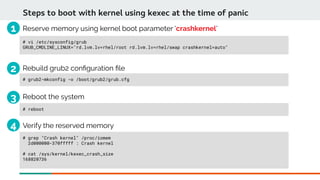
Reserve memory using kernel boot parameter 'crashkernel'.
Syntax:
The size of 'crashkernel' depends on:
Size of initramfs fle, machine IO devices complexity
Number of CPUs to be used in crash kernel
Total amount of installed system memory
128 MiB + 4 bits for every 4KB page
crashkernel=size[KMG][@offset[KMG]]
Eg: crashkernel=128M@16M or crashkernel=128M
crashkernel=range1:size1[,range2:size2,...][@offset]
Eg: crashkernel=0M-2G:128M,2G-6G:256M,6G-8G:512M,8G-:768M
crashkernel=auto
1
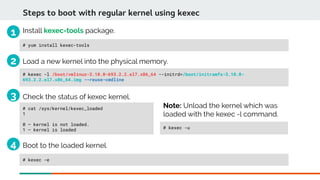
Kexec mechanism can also be used to load a new kernel to boot at the time of panic.](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-16-320.jpg)



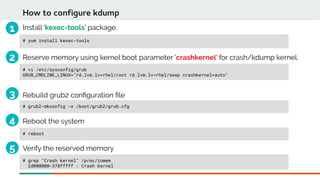

![Invoking crash
Typical postmortem debugging: [ ofine ]
# crash --osrelease vmcore
3.10.0-862.3.2.el7.x86_64
# crash vmcore /usr/lib/debug/lib/modules/3.10.0-862.3.2.el7.x86_64/vmlinux
# crash </path/to/vmlinux> </path/to/vmcore>
Live memory debugging: [ online ]
# crash /usr/lib/debug/lib/modules/3.10.0-862.3.2.el7.x86_64/vmlinux
/dev/crash used by default for live memory image.
# crash </path/to/vmlinux>
1
2](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-38-320.jpg)

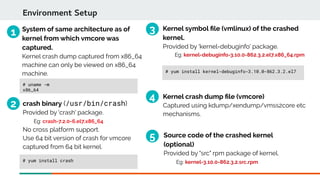
![sys command: system-specific data
crash> sys
KERNEL: /usr/lib/debug/lib/modules/3.10.0-693.el7.x86_64/vmlinux
DUMPFILE: vmcore [PARTIAL DUMP]
CPUS: 16
DATE: Fri May 11 15:34:17 2018
UPTIME: 83 days, 05:38:37
LOAD AVERAGE: 0.31, 0.54, 0.52
TASKS: 1222
NODENAME: server1.redhat.com
RELEASE: 3.10.0-693.el7.x86_64
VERSION: #1 SMP Thu Jul 6 19:56:57 EDT 2017
MACHINE: x86_64 (2600 Mhz)
MEMORY: 127.9 GB
PANIC: "BUG: unable to handle kernel NULL pointer dereference at 0000000000000008"
sys - System information
Date & time of crash
Cause of Panic
Version of running Kernel
Load on the system: 1-5-15 minute interval](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-40-320.jpg)
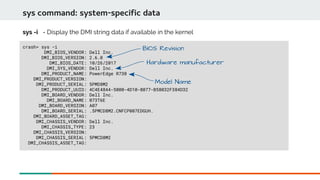
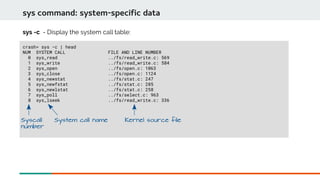
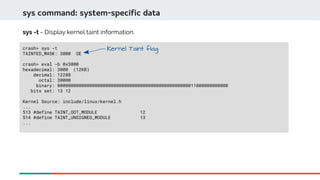
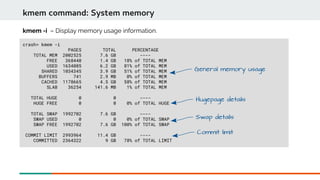
![crash> ps | head
PID PPID CPU TASK ST %MEM VSZ RSS COMM
0 0 0 ffffffff8cc16480 RU 0.0 0 0 [swapper/0]
0 0 1 ffff8e397cef2f70 RU 0.0 0 0 [swapper/1]
1 0 0 ffff8e397ce58000 IN 0.0 131616 3976 systemd
2 0 1 ffff8e397ce58fd0 IN 0.0 0 0 [kthreadd]
3 2 0 ffff8e397ce59fa0 IN 0.0 0 0 [ksoftirqd/0]
5 2 0 ffff8e397ce5bf40 IN 0.0 0 0 [kworker/0:0H]
7 2 0 ffff8e397ce5dee0 IN 0.0 0 0 [migration/0]
8 2 0 ffff8e397ce5eeb0 IN 0.0 0 0 [rcu_bh]
9 2 0 ffff8e397cef0000 RU 0.0 0 0 [rcu_sched]
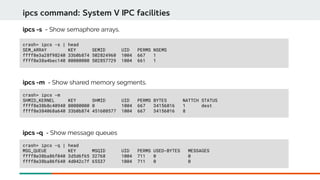
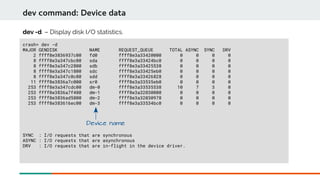
ps command: Display process status information
ps - Show the process status of all current tasks.
PID Of
process
Struct task_struct *
Process
State
Percent of
Memory used
Resident
Set Size
Process name](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-47-320.jpg)
![crash> ps -u | head
PID PPID CPU TASK ST %MEM VSZ RSS COMM
1 0 0 ffff8e397ce58000 IN 0.0 131616 3976 systemd
403 21790 1 ffff8e385f510000 IN 0.3 1009284 28036 db2fmp
404 21790 1 ffff8e3a1aef3f40 IN 0.3 1009284 28036 db2fmp
558 1 1 ffff8e383694cf10 IN 0.0 36988 1516 systemd-journal
582 1 1 ffff8e3a32d12f70 IN 0.0 348200 3768 lvmetad
598 1 0 ffff8e3a32d16eb0 IN 0.0 44944 3220 systemd-udevd
769 1 0 ffff8e3a2fee3f40 IN 0.0 114624 1816 auditd
787 1 0 ffff8e3a2fee2f70 IN 0.0 114624 1816 auditd
788 769 0 ffff8e3a2fee0000 IN 0.0 80268 988 audispd
ps command: Display process status information
ps -u - Restrict the output to only user tasks.
crash> ps -k | head
PID PPID CPU TASK ST %MEM VSZ RSS COMM
0 0 0 ffffffff8cc16480 RU 0.0 0 0 [swapper/0]
0 0 1 ffff8e397cef2f70 RU 0.0 0 0 [swapper/1]
2 0 1 ffff8e397ce58fd0 IN 0.0 0 0 [kthreadd]
3 2 0 ffff8e397ce59fa0 IN 0.0 0 0 [ksoftirqd/0]
5 2 0 ffff8e397ce5bf40 IN 0.0 0 0 [kworker/0:0H]
7 2 0 ffff8e397ce5dee0 IN 0.0 0 0 [migration/0]
8 2 0 ffff8e397ce5eeb0 IN 0.0 0 0 [rcu_bh]
9 2 0 ffff8e397cef0000 RU 0.0 0 0 [rcu_sched]
10 2 0 ffff8e397cef0fd0 IN 0.0 0 0 [lru-add-drain]
ps -k - Restrict the output to only kernel threads.](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-48-320.jpg)
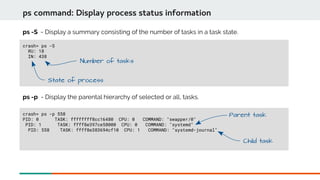
![crash> ps -c 558
PID: 558 TASK: ffff8e383694cf10 CPU: 1 COMMAND: "systemd-journal"
(no children)
ps command: Display process status information
ps -c - display the children of selected or all, tasks.
crash> ps -m | head
[0 00:00:00.000] [RU] PID: 20684 TASK: ffff8e39f9f39fa0 CPU: 0 COMMAND: "awk"
[0 00:00:00.000] [RU] PID: 1786 TASK: ffff8e3a36228000 CPU: 1 COMMAND: "ds_am"
[0 00:00:00.000] [IN] PID: 558 TASK: ffff8e383694cf10 CPU: 1 COMMAND: "systemd-journal"
[0 00:00:00.010] [RU] PID: 20685 TASK: ffff8e39f9f3bf40 CPU: 0 COMMAND: "awk"
[0 00:00:00.010] [IN] PID: 7 TASK: ffff8e397ce5dee0 CPU: 0 COMMAND: "migration/0"
[0 00:00:00.010] [RU] PID: 20686 TASK: ffff8e3a358e3f40 CPU: 1 COMMAND: "env"
[0 00:00:00.010] [RU] PID: 20683 TASK: ffff8e39f9f3cf10 CPU: 1 COMMAND: "awk"
[0 00:00:00.022] [RU] PID: 20687 TASK: ffff8e3a1aef2f70 CPU: 0 COMMAND: "awk"
[0 00:00:00.021] [IN] PID: 20179 TASK: ffff8e3a29683f40 CPU: 1 COMMAND: "kworker/u4:1"
[0 00:00:00.032] [RU] PID: 20681 TASK: ffff8e3840d28fd0 CPU: 0 COMMAND: "awk"
ps -m - Display the task's last-run timestamp value.
Days Hours Minutes Seconds Milliseconds](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-50-320.jpg)
![crash> runq
CPU 0 RUNQUEUE: ffff8e3a3fc18b00
CURRENT: PID: 20684 TASK: ffff8e39f9f39fa0 COMMAND: "awk"
RT PRIO_ARRAY: ffff8e3a3fc18ca0
[no tasks queued]
CFS RB_ROOT: ffff8e3a3fc18ba8
[120] PID: 22270 TASK: ffff8e3a34543f40 COMMAND: "db2sysc"
[120] PID: 21796 TASK: ffff8e3a3fce1fa0 COMMAND: "db2sysc"
[120] PID: 749 TASK: ffff8e3a32d14f10 COMMAND: "xfsaild/dm-3"
[120] PID: 9 TASK: ffff8e397cef0000 COMMAND: "rcu_sched"
[120] PID: 20681 TASK: ffff8e3840d28fd0 COMMAND: "awk"
[120] PID: 20685 TASK: ffff8e39f9f3bf40 COMMAND: "awk"
[120] PID: 20687 TASK: ffff8e3a1aef2f70 COMMAND: "awk"
CPU 1 RUNQUEUE: ffff8e3a3fd18b00
CURRENT: PID: 1786 TASK: ffff8e3a36228000 COMMAND: "ds_am"
RT PRIO_ARRAY: ffff8e3a3fd18ca0
[no tasks queued]
CFS RB_ROOT: ffff8e3a3fd18ba8
[120] PID: 474 TASK: ffff8e3a32a1cf10 COMMAND: "xfsaild/dm-1"
[120] PID: 815 TASK: ffff8e3a32d10000 COMMAND: "vmtoolsd"
[120] PID: 858 TASK: ffff8e3a3622dee0 COMMAND: "in:imjournal"
[120] PID: 20686 TASK: ffff8e3a358e3f40 COMMAND: "env"
[120] PID: 20688 TASK: ffff8e39eaa28fd0 COMMAND: "env"
[120] PID: 20683 TASK: ffff8e39f9f3cf10 COMMAND: "awk"
[120] PID: 20689 TASK: ffff8e39eaa2dee0 COMMAND: "awk"
runq command: Runqueue
runq - Display the tasks on an O(1) scheduler run queue.
Running task
Task waiting in run
queue of CPU 0
Struct rq * pointer of CPU 1](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-51-320.jpg)
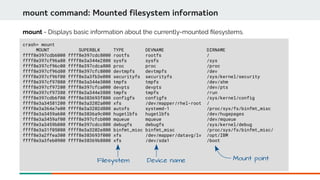
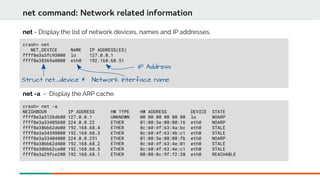
![crash> mod -s xfs
MODULE NAME SIZE OBJECT FILE
ffffffffc050d9e0 xfs 1003971 /usr/lib/debug/lib/modules/3.10.0-862.3.2.el7.x86_64/kernel/fs/xfs/xfs.ko.debug
mod command: Module information
mod -s - Load the symbolic and debugging data of the xfs module from its known location.
crash> mod -d xfs
crash> mod | grep xfs
ffffffffc050d9e0 xfs 1003971 (not loaded) [CONFIG_KALLSYMS]
mod -d - Deletes the symbolic and debugging data of the module specifed.](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-58-320.jpg)
![log command: Kernel ring buffer
crash> log
[2559941.344390] SysRq : Trigger a crash
[2559942.957195] BUG: unable to handle kernel NULL pointer dereference at (null)
[2559943.099378] IP: [<ffffffff8135f166>] sysrq_handle_crash+0x16/0x20
[2559944.783241] PGD 8000001331cce067 PUD 13a4d32067 PMD 0
[2559945.486950] Oops: 0002 [#1] SMP
[2559946.422806] last sysfs file: /sys/devices/system/cpu/online
[2559946.684623] CPU 6
[2559947.107669] Modules linked in: nfs lockd fscache auth_rpcgss nfs_acl tcp_diag inet_diag
oracleacfs(P)(U) oracleadvm(P)(U) dm_region_hash dm_log dm_mod [last unloaded: cbsensor]
[2559951.437296]
[2559951.945506] Pid: 5833, comm: cssdagent Tainted: P -------------- 2.6.32-696.18.7.el6.x86_64
#1 VMware, Inc. VMware Virtual Platform/440BX Desktop Reference Platform
[2559953.580469] RIP: 0010:[<ffffffff8135f166>] [<ffffffff8135f166>] sysrq_handle_crash+0x16/0x20
...
log – Display the kernel ring bufer.](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-59-320.jpg)
![bt command: Backtrace
crash> bt
PID: 28438 TASK: ffff88131860bf40 CPU: 11 COMMAND: "ls"
#0 [ffff882001a17728] machine_kexec at ffffffff8105c4cb
...
#9 [ffff882001a179d0] page_fault at ffffffff816ac508
[exception RIP: vnlayer_linux_new_clrvnode+21]
RIP: ffffffffc08b5f03 RSP: ffff882001a17a88 RFLAGS: 00010246
RAX: ffffffff81a8fdc0 RBX: 0000000000000000 RCX: 0000000000000002
RDX: 0000000000000001 RSI: 0000000000000000 RDI: ffff880144beae40
RBP: ffff882001a17ab0 R8: ffff88014055fa10 R9: 00000001802a002a
R10: ffff88203df59b80 R11: ffffea004599e8c0 R12: 0000000000000000
R13: ffff880144beae40 R14: ffff881fc87462f0 R15: 0000000000000000
ORIG_RAX: ffffffffffffffff CS: 0010 SS: 0018
#10 [ffff882001a17ab8] mvop_linux_lookup_component at ffffffffc08b289f [mvfs]
#11 [ffff882001a17af0] mvfs_lookup_ctx at ffffffffc086e57c [mvfs]
#12 [ffff882001a17b78] mvfs_linux_lookup_wrapper at ffffffffc08a8257 [mvfs]
#13 [ffff882001a17bd8] vnode_iop_lookup at ffffffffc08b056e [mvfs]
#14 [ffff882001a17c60] lookup_real at ffffffff8120b45d
#15 [ffff882001a17c80] __lookup_hash at ffffffff8120bd32
#16 [ffff882001a17cb0] lookup_slow at ffffffff816a1322
#17 [ffff882001a17ce8] path_lookupat at ffffffff8120f2db
#18 [ffff882001a17d80] filename_lookup at ffffffff8120f33b
#19 [ffff882001a17db8] user_path_at_empty at ffffffff81212e47
#20 [ffff882001a17e88] user_path_at at ffffffff81212eb1
#21 [ffff882001a17e98] vfs_fstatat at ffffffff81206463
#22 [ffff882001a17ee8] SYSC_newlstat at ffffffff81206a31
#23 [ffff882001a17f70] sys_newlstat at ffffffff81206cbe
#24 [ffff882001a17f80] system_call_fastpath at ffffffff816b4fc9
...
bt - Displays a task's kernel-stack backtrace.
Panic Location
Panic task
Content of CPU registers
at the time of panic
Return address
Module name
Stackframe
Functions on the stack](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-60-320.jpg)
![bt command: Backtrace
crash> bt -a
PID: 20684 TASK: ffff8e39f9f39fa0 CPU: 0 COMMAND: "awk"
#0 [ffff8e3840ec7ea8] crash_nmi_callback at ffffffff8c0537c7
#1 [ffff8e3840ec7eb8] nmi_handle at ffffffff8c71893c
#2 [ffff8e3840ec7f10] do_nmi at ffffffff8c718b5d
#3 [ffff8e3840ec7f50] nmi at ffffffff8c717d00
RIP: 00007fabec9c9c44 RSP: 00007fff4f634750 RFLAGS: 00000206
RAX: 0000000076036301 RBX: 0000000000f0b2ff RCX: 0000000000000000
RDX: 0000000000ca0000 RSI: 00007fff4f634848 RDI: 00000000000000bc
RBP: 00000000000000bc R8: 0000000000000007 R9: 0000000000000002
R10: 00007fff4f6345a0 R11: 00007fff4f6346a0 R12: 00007fff4f634770
R13: 00007fff4f634760 R14: 0000000000000001 R15: 00007fabecce5730
ORIG_RAX: ffffffffffffffff CS: 0033 SS: 002b
PID: 1786 TASK: ffff8e3a36228000 CPU: 1 COMMAND: "ds_am"
#0 [ffff8e38b8e9fa78] machine_kexec at ffffffff8c060f9a
#1 [ffff8e38b8e9fad8] __crash_kexec at ffffffff8c113732
#2 [ffff8e38b8e9fba8] crash_kexec at ffffffff8c113820
#3 [ffff8e38b8e9fbc0] oops_end at ffffffff8c718798
#4 [ffff8e38b8e9fbe8] no_context at ffffffff8c707fbe
#5 [ffff8e38b8e9fc38] __bad_area_nosemaphore at ffffffff8c708055
#6 [ffff8e38b8e9fc88] bad_area_nosemaphore at ffffffff8c7081c6
#7 [ffff8e38b8e9fc98] __do_page_fault at ffffffff8c71b750
#8 [ffff8e38b8e9fd00] do_page_fault at ffffffff8c71b945
#9 [ffff8e38b8e9fd30] page_fault at ffffffff8c717788
[exception RIP: gsch_install_hooks+136]
RIP: ffffffffc073b8d8 RSP: ffff8e38b8e9fde0 RFLAGS: 00010202
RAX: 0000000000000000 RBX: ffffffffc074a000 RCX: 0000000000000002
RDX: 0000000000000000 RSI: ffffffffc074a960 RDI: ffffffffc074a180
RBP: ffff8e38b8e9fe40 R8: 0000000030323863 R9: 0000000000000003
R10: 00000000000005dd R11: 3138666666666666 R12: ffffffffc074a180
R13: ffffffffc074a960 R14: ffffffff81803310 R15: 0000000000000000
ORIG_RAX: ffffffffffffffff CS: 0010 SS: 0018
...
bt -a - Displays the backtraces of the active tasks on all CPUs.
Backtrace of task on CPU 0
Backtrace of task on CPU 1](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-61-320.jpg)
![bt command: Backtrace
crash> bt -f
PID: 1786 TASK: ffff8e3a36228000 CPU: 1 COMMAND: "ds_am"
…
#5 [ffff8e38b8e9fc38] __bad_area_nosemaphore at ffffffff8c708055
ffff8e38b8e9fc40: 0000000000226c6c 0000000000000246
ffff8e38b8e9fc50: 0000000000000000 0000000000000000
ffff8e38b8e9fc60: 0000000000000000 ffffffff81803310
ffff8e38b8e9fc70: ffff8e38b8e9fd38 ffff8e3a36228000
ffff8e38b8e9fc80: ffff8e38b8e9fc90 ffffffff8c7081c6
#6 [ffff8e38b8e9fc88] bad_area_nosemaphore at ffffffff8c7081c6
ffff8e38b8e9fc90: ffff8e38b8e9fcf8 ffffffff8c71b750
#7 [ffff8e38b8e9fc98] __do_page_fault at ffffffff8c71b750
ffff8e38b8e9fca0: ffff8e38b8e9fcf8 ffff8e38b8e9fcb8
ffff8e38b8e9fcb0: 00000000f0a3d3eb 0000000000000000
ffff8e38b8e9fcc0: ffff8e3a29f49978 ffff8e3a29f49900
ffff8e38b8e9fcd0: ffff8e38b8e9fd38 0000000000000000
ffff8e38b8e9fce0: 0000000000000000 ffffffff81803310
ffff8e38b8e9fcf0: 0000000000000000 ffff8e38b8e9fd28
ffff8e38b8e9fd00: ffffffff8c71b945
#8 [ffff8e38b8e9fd00] do_page_fault at ffffffff8c71b945
ffff8e38b8e9fd08: ffffffffc074ab60 0000000000000001
ffff8e38b8e9fd18: ffffffffc074a180 ffffffffc074a960
ffff8e38b8e9fd28: ffff8e38b8e9fe40 ffffffff8c717788
#9 [ffff8e38b8e9fd30] page_fault at ffffffff8c717788
[exception RIP: gsch_install_hooks+136]
RIP: ffffffffc073b8d8 RSP: ffff8e38b8e9fde0 RFLAGS: 00010202
RAX: 0000000000000000 RBX: ffffffffc074a000 RCX: 0000000000000002
RDX: 0000000000000000 RSI: ffffffffc074a960 RDI: ffffffffc074a180
RBP: ffff8e38b8e9fe40 R8: 0000000030323863 R9: 0000000000000003
R10: 00000000000005dd R11: 3138666666666666 R12: ffffffffc074a180
R13: ffffffffc074a960 R14: ffffffff81803310 R15: 0000000000000000
bt -f – Display all stack data contained in a frame.
Return address
Data on the stack](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-62-320.jpg)
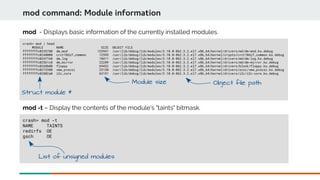
![dis command: Disassemble
crash> dis -r sysrq_handle_crash+22
0xffffffff9102f170 <sysrq_handle_crash>: nopl 0x0(%rax,%rax,1) [FTRACE NOP]
0xffffffff9102f175 <sysrq_handle_crash+5>: push %rbp
0xffffffff9102f176 <sysrq_handle_crash+6>: mov %rsp,%rbp
0xffffffff9102f179 <sysrq_handle_crash+9>: movl $0x1,0x8142d1(%rip) #
0xffffffff91843454
0xffffffff9102f183 <sysrq_handle_crash+19>: sfence
0xffffffff9102f186 <sysrq_handle_crash+22>: movb $0x1,0x0
dis -r <function+ofset> - Disassemble a function from the start to the specifed ofset.
CPU InstructionsFunction Offset](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-63-320.jpg)
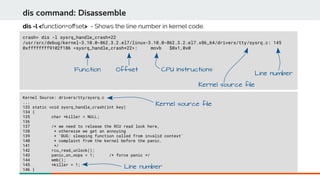
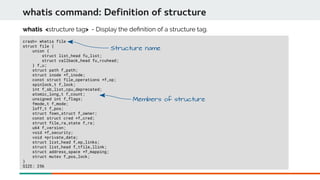
![crash> struct file -ox
struct file {
union {
struct list_head fu_list;
struct callback_head fu_rcuhead;
[0x0] } f_u;
[0x10] struct path f_path;
[0x20] struct inode *f_inode;
[0x28] const struct file_operations *f_op;
[0x30] spinlock_t f_lock;
[0x34] int f_sb_list_cpu_deprecated;
[0x38] atomic_long_t f_count;
[0x40] unsigned int f_flags;
[0x44] fmode_t f_mode;
[0x48] loff_t f_pos;
[0x50] struct fown_struct f_owner;
[0x70] const struct cred *f_cred;
[0x78] struct file_ra_state f_ra;
[0x98] u64 f_version;
[0xa0] void *f_security;
[0xa8] void *private_data;
[0xb0] struct list_head f_ep_links;
[0xc0] struct list_head f_tfile_llink;
[0xd0] struct address_space *f_mapping;
[0xd8] struct mutex f_pos_lock;
}
SIZE: 0x100
struct command: Structure contents
struct <struct-tag-name> [-o] [-x | -d] – display defnition and member ofsets.
Structure name
Members of structure
o is offset
d in decimal
x in hexadecimal](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-67-320.jpg)
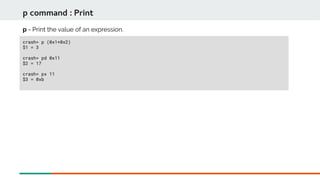
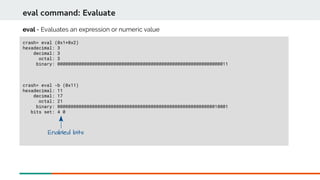
![crash> rd ffffffff9102f186 0x4
ffffffff9102f186: 01000000002504c6 550000441f0fc35d ..%.....]...D..U
ffffffff9102f196: 0081454e05c7c031 53e5894800000007 1...NE......H..S
crash> rd ffffffff9102f186
ffffffff9102f186: 01000000002504c6 ..%.....
rd command: Read memory
rd - read memory contents.
Memory location Data stored
Memory location Data stored
Address + range
ASCII representation
crash> rd c009bf2c -e c009bf60
c009bf2c: c009bf64 c01328c3 c009bf64 c0132838 d....(..d...8(..
c009bf3c: 0000002a 00000004 c57d77e8 00000104 *........w}.....
c009bf4c: 0000000b c009a000 7fffffff 00000000 ................
C009bf5c: 00000000
Read the range of memory from c009bf2c to c009bf60:](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-70-320.jpg)
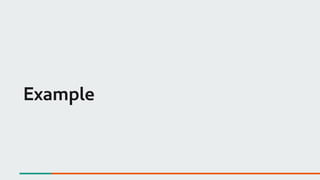
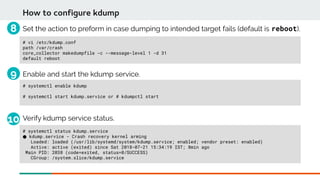
![System information
crash> sys
KERNEL: /usr/lib/debug/lib/modules/3.10.0-862.3.2.el7.x86_64/vmlinux
DUMPFILE: /var/crash/127.0.0.1-2018-07-30-17:38:26/vmcore [PARTIAL DUMP]
CPUS: 4
DATE: Mon Jul 30 17:38:19 2018
UPTIME: 00:02:26
LOAD AVERAGE: 0.10, 0.09, 0.04
TASKS: 260
NODENAME: localhost.localdomain
RELEASE: 3.10.0-862.3.2.el7.x86_64
VERSION: #1 SMP Tue May 15 18:22:15 EDT 2018
MACHINE: x86_64 (2808 Mhz)
MEMORY: 6 GB
PANIC: "divide error: 0000 [#1] SMP "](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-72-320.jpg)
![Kernel ring buffer
crash> log
[..]
[ 148.101287] DevConf: loading out-of-tree module taints kernel.
[ 148.111590] DevConf: module verification failed: signature and/or required key missing - tainting kernel
[ 148.132504] Hello, DevConf !
[ 148.133688] divide error: 0000 [#1] SMP
[ 148.135147] Modules linked in: DevConf(OE+) ip6table_filter
[ 148.161198] CPU: 1 PID: 2403 Comm: insmod Kdump: loaded Tainted: GOE ------------ 3.10.0-862.3.2.el7.x86_64 #1
[ 148.163796] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.10.2-1.fc26 04/01/2014
[ 148.165553] task: ffff97e0a9a28fd0 ti: ffff97e0b6780000 task.ti: ffff97e0b6780000
[ 148.167094] RIP: 0010:[<ffffffffc075301f>] [<ffffffffc075301f>] DevConf_module_init+0x1f/0x30 [DevConf]
[ 148.169081] RSP: 0018:ffff97e0b6783d30 EFLAGS: 00010246
[ 148.170157] RAX: 0000000000000001 RBX: ffffffff94016020 RCX: 0000000000000000
[ 148.171722] RDX: 0000000000000000 RSI: ffff97e0bfc93938 RDI: ffff97e0bfc93938
[ 148.173263] RBP: ffff97e0b6783d30 R08: 0000000000000000 R09: 0000000000000100
[ 148.174718] R10: 0000000000000417 R11: 0000000000aaaaaa R12: ffff97e0a2b09860
[ 148.176185] R13: ffffffffc0753000 R14: 0000000000000000 R15: ffffffffc0755000
[ 148.177636] FS: 00007efd309a1740(0000) GS:ffff97e0bfc80000(0000) knlGS:0000000000000000
[ 148.179305] CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
[ 148.180515] CR2: 0000000000413e60 CR3: 00000000b30e4000 CR4: 00000000003606e0
[ 148.182022] DR0: 0000000000000000 DR1: 0000000000000000 DR2: 0000000000000000
[ 148.183467] DR3: 0000000000000000 DR6: 00000000fffe0ff0 DR7: 0000000000000400
[ 148.184919] Call Trace:
[ 148.185424] [<ffffffff9340210a>] do_one_initcall+0xba/0x240
[ 148.186591] [<ffffffff9350f8dc>] load_module+0x272c/0x2bc0
[ 148.187757] [<ffffffff93776be0>] ? ddebug_proc_write+0xf0/0xf0
[ 148.189006] [<ffffffff9350b513>] ? copy_module_from_fd.isra.43+0x53/0x150
[ 148.190491] [<ffffffff9350ff26>] SyS_finit_module+0xa6/0xd0
[ 148.191952] [<ffffffff93b2082f>] system_call_fastpath+0x1c/0x21
[ 148.193418] Code: <f7> f9 5d c3 66 66 66 66 2e 0f 1f 84 00 00 00 00 00 0f 1f 44 00 00
[ 148.198450] RIP [<ffffffffc075301f>] DevConf_module_init+0x1f/0x30 [DevConf]
[ 148.201937] RSP <ffff97e0b6783d30>](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-73-320.jpg)
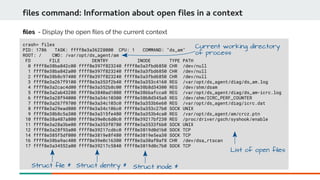
![Panic task and List of open files
crash> set -p
PID: 2403
COMMAND: "insmod"
TASK: ffff97e0a9a28fd0 [THREAD_INFO: ffff97e0b6780000]
CPU: 1
STATE: TASK_RUNNING (PANIC)
crash> files
PID: 2403 TASK: ffff97e0a9a28fd0 CPU: 1 COMMAND: "insmod"
ROOT: / CWD: /root/module
FD FILE DENTRY INODE TYPE PATH
0 ffff97dfbb56b300 ffff97e0ab111900 ffff97e0b72cf2e0 CHR /dev/pts/0
1 ffff97dfbb56b300 ffff97e0ab111900 ffff97e0b72cf2e0 CHR /dev/pts/0
2 ffff97dfbb56b300 ffff97e0ab111900 ffff97e0b72cf2e0 CHR /dev/pts/0
3 ffff97e09e691900 ffff97e0ab1e3540 ffff97dfafcb6e60 REG /root/module/DevConf.ko](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-74-320.jpg)
![Backtrace of panic task
crash> bt
PID: 2403 TASK: ffff97e0a9a28fd0 CPU: 1 COMMAND: "insmod"
#0 [ffff97e0b67839e0] machine_kexec at ffffffff93460f9a
#1 [ffff97e0b6783a40] __crash_kexec at ffffffff93513732
#2 [ffff97e0b6783b10] crash_kexec at ffffffff93513820
#3 [ffff97e0b6783b28] oops_end at ffffffff93b18798
#4 [ffff97e0b6783b50] die at ffffffff9342e96b
#5 [ffff97e0b6783b80] do_trap at ffffffff93b17f10
#6 [ffff97e0b6783bd0] do_divide_error at ffffffff9342b08e
#7 [ffff97e0b6783c80] divide_error at ffffffff93b23e4e
[exception RIP: init_module+31]
RIP: ffffffffc075301f RSP: ffff97e0b6783d30 RFLAGS: 00010246
RAX: 0000000000000001 RBX: ffffffff94016020 RCX: 0000000000000000
RDX: 0000000000000000 RSI: ffff97e0bfc93938 RDI: ffff97e0bfc93938
RBP: ffff97e0b6783d30 R8: 0000000000000000 R9: 0000000000000100
R10: 0000000000000417 R11: 0000000000aaaaaa R12: ffff97e0a2b09860
R13: ffffffffc0753000 R14: 0000000000000000 R15: ffffffffc0755000
ORIG_RAX: ffffffffffffffff CS: 0010 SS: 0018
#8 [ffff97e0b6783d38] do_one_initcall at ffffffff9340210a
#9 [ffff97e0b6783d68] load_module at ffffffff9350f8dc
#10 [ffff97e0b6783eb8] sys_finit_module at ffffffff9350ff26
#11 [ffff97e0b6783f50] system_call_fastpath at ffffffff93b2082f
RIP: 00007efd2fe787f9 RSP: 00007ffc3eb99528 RFLAGS: 00010246
RAX: 0000000000000139 RBX: 0000000001b5d2e0 RCX: 000000000000001f
RDX: 0000000000000000 RSI: 000000000041a2d8 RDI: 0000000000000003
RBP: 000000000041a2d8 R8: 0000000000000000 R9: 00007ffc3eb99738
R10: 0000000000000003 R11: 0000000000000202 R12: 0000000000000000
R13: 0000000001b5d2c0 R14: 0000000000000000 R15: 0000000000000000
ORIG_RAX: 0000000000000139 CS: 0033 SS: 002b](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-75-320.jpg)
![Dis-assembly of exception RIP
crash> dis -rl ffffffffc075301f
0xffffffffc0753000 <DevConf_module_init>: nopl 0x0(%rax,%rax,1) [FTRACE NOP]
0xffffffffc0753005 <init_module+5> : push %rbp
0xffffffffc0753006 <init_module+6> : mov $0xffffffffc0754024,%rdi
0xffffffffc075300d <init_module+13>: xor %eax,%eax
0xffffffffc075300f <init_module+15>: mov %rsp,%rbp
0xffffffffc0753012 <init_module+18>: callq 0xffffffff93b08bc7 <printk>
0xffffffffc0753017 <init_module+23>: mov $0x1,%eax
0xffffffffc075301c <init_module+28>: xor %ecx,%ecx
0xffffffffc075301e <init_module+30>: cltd
0xffffffffc075301f <init_module+31>: idiv %ecx
[exception RIP: init_module+31]
RIP: ffffffffc075301f RSP: ffff97e0b6783d30 RFLAGS: 00010246
RAX: 0000000000000001 RBX: ffffffff94016020 RCX: 0000000000000000
RDX: 0000000000000000 RSI: ffff97e0bfc93938 RDI: ffff97e0bfc93938
RBP: ffff97e0b6783d30 R8: 0000000000000000 R9: 0000000000000100
R10: 0000000000000417 R11: 0000000000aaaaaa R12: ffff97e0a2b09860
R13: ffffffffc0753000 R14: 0000000000000000 R15: ffffffffc0755000](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-76-320.jpg)
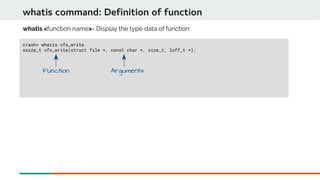
![Dis-assembly of exception RIP
crash> mod -s DevConf DevConf.o
MODULE NAME SIZE OBJECT FILE
ffffffffc0755000 DevConf 12514 DevConf.o
crash> dis -rl ffffffffc075301f
/root/module/DevConf.c: 10
0xffffffffc0753000 <DevConf_module_init>: nopl 0x0(%rax,%rax,1) [FTRACE NOP]
0xffffffffc0753005 <init_module+5> : push %rbp
/root/module/DevConf.c: 11
0xffffffffc0753006 <init_module+6> : mov $0xffffffffc0754024,%rdi
0xffffffffc075300d <init_module+13> : xor %eax,%eax
/root/module/DevConf.c: 10
0xffffffffc075300f <init_module+15> : mov %rsp,%rbp
/root/module/DevConf.c: 11
0xffffffffc0753012 <init_module+18> : callq 0xffffffff93b08bc7 <printk>
/root/module/DevConf.c: 12
0xffffffffc0753017 <init_module+23> : mov $0x1,%eax
0xffffffffc075301c <init_module+28> : xor %ecx,%ecx
0xffffffffc075301e <init_module+30> : cltd
0xffffffffc075301f <init_module+31> : idiv %ecx
crash> mod | grep -e NAME -e DevConf
MODULE NAME SIZE OBJECT FILE
ffffffffc0755000 DevConf 12514 (not loaded) [CONFIG_KALLSYMS]](https://image.slidesharecdn.com/kdumpandkernelcrashdumpanalysis-190324101226/85/Kdump-and-the-kernel-crash-dump-analysis-77-320.jpg)