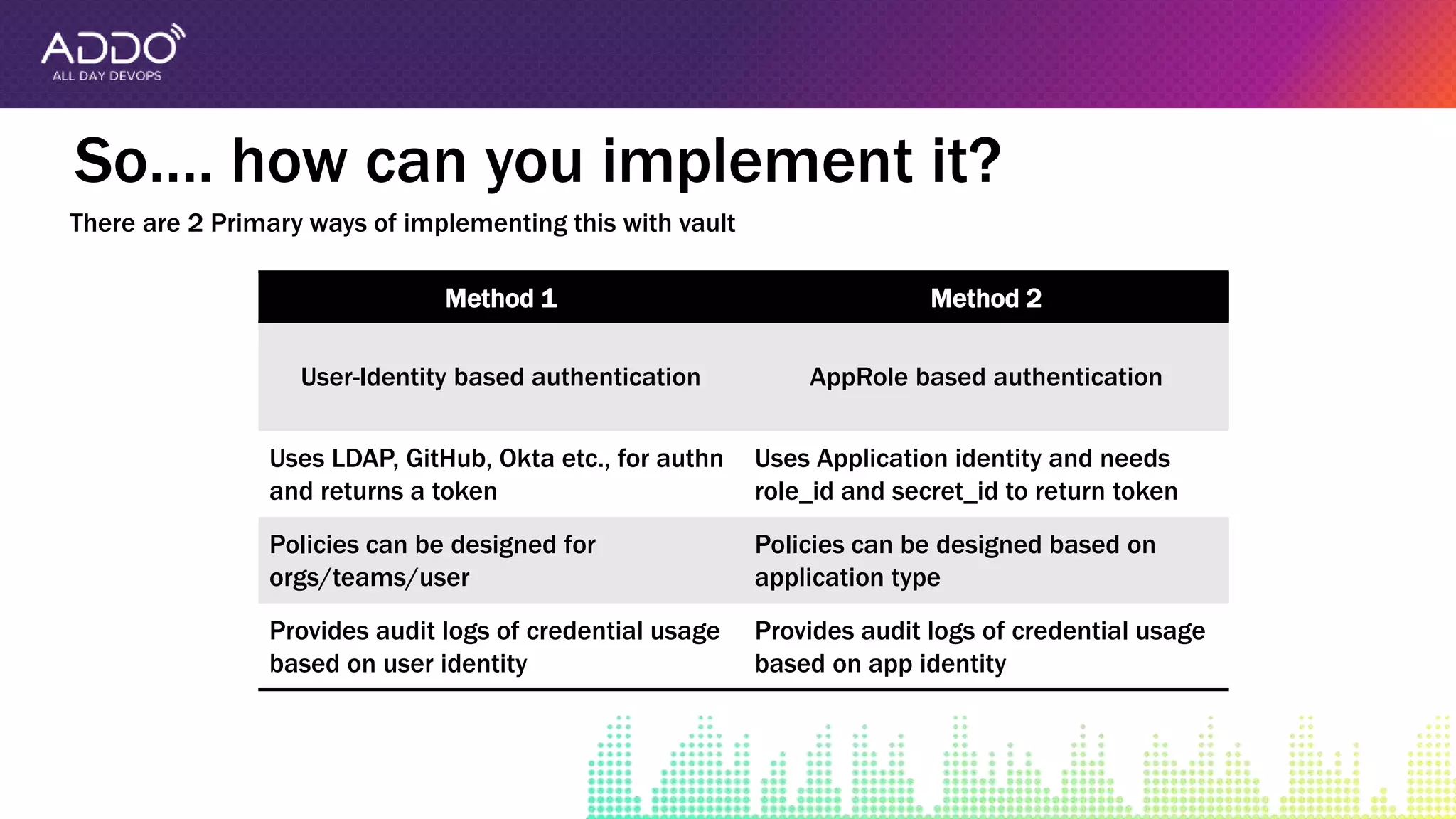
The document discusses the integration of Jenkins, Terraform, and Vault to automate cloud infrastructure deployment while securely managing credentials and secrets. It outlines the advantages of using Vault for centralized secret storage, access management, and auditing compared to Jenkins' credential store, highlighting two primary authentication methods: user-identity based and approle based. Additionally, it provides an implementation guide and emphasizes the importance of version control for pipelines and policies.