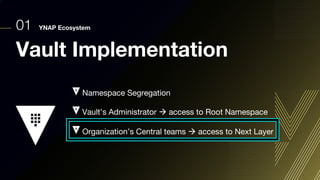
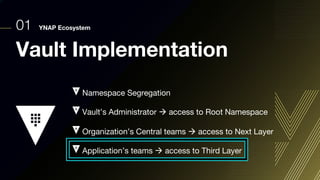
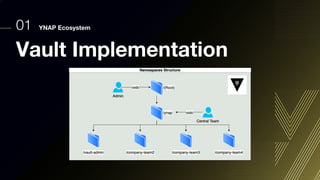
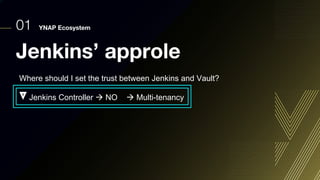
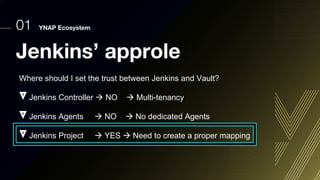
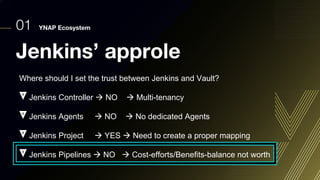
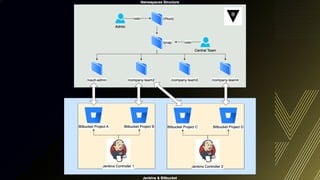
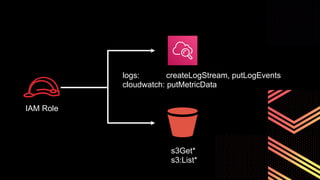
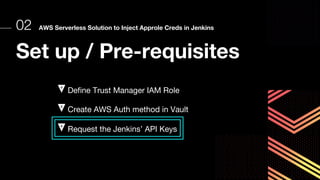
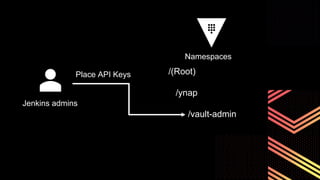
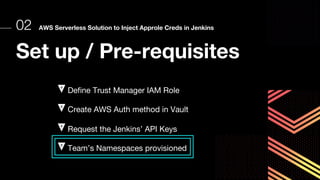
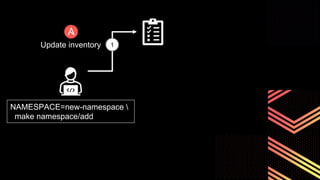
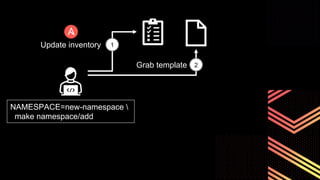
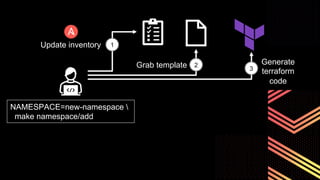
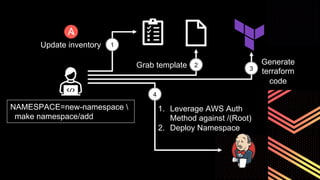
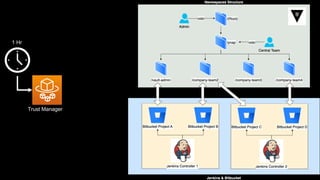
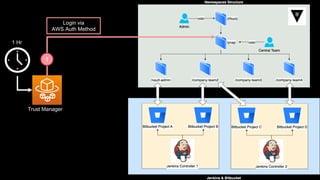
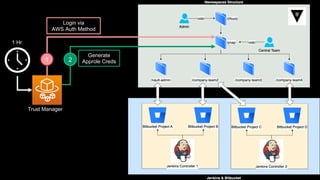
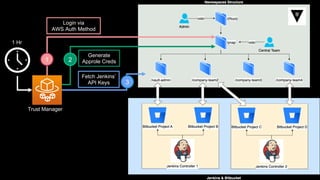
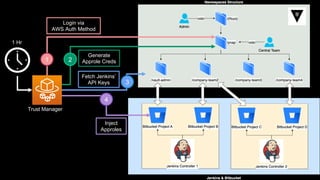
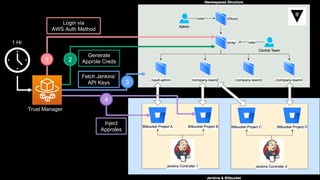
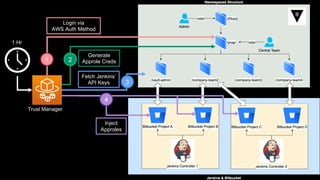
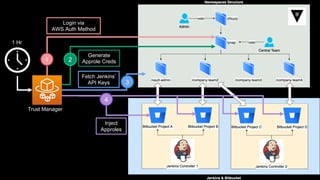
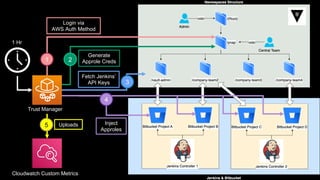
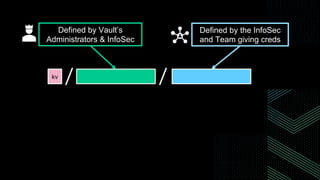
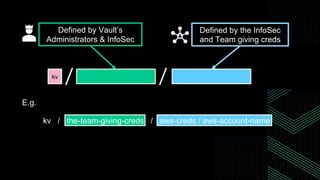
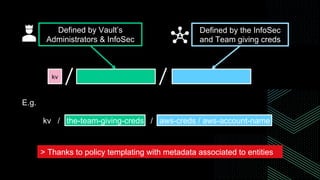
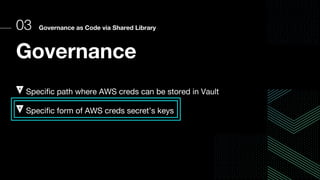
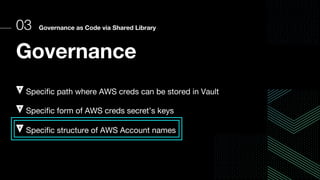
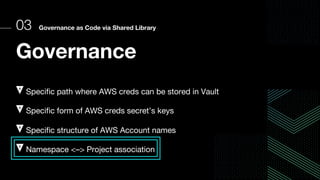
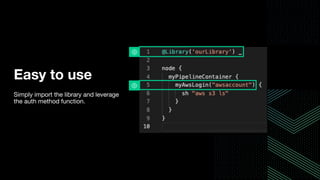
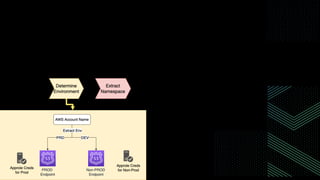
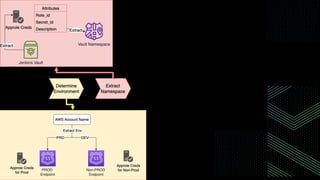
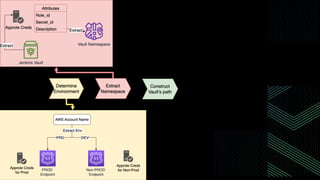
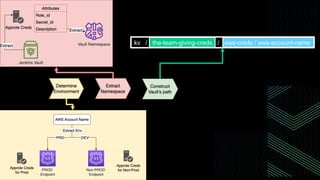
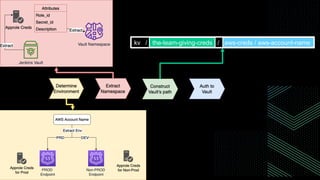
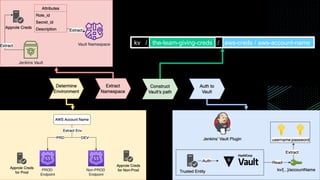
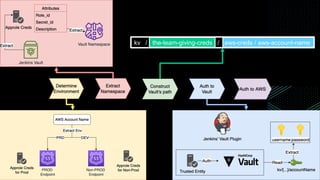
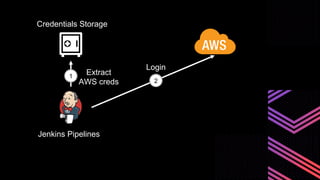
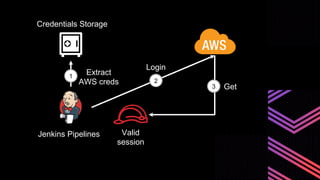
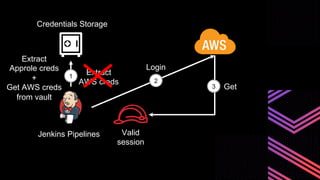
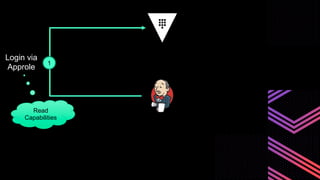
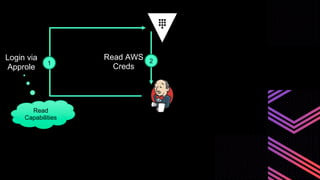
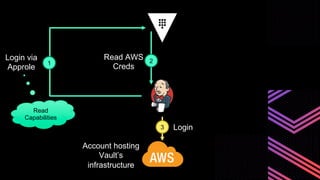
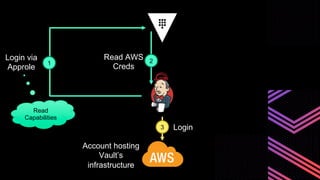
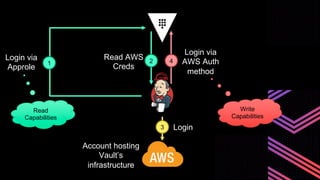
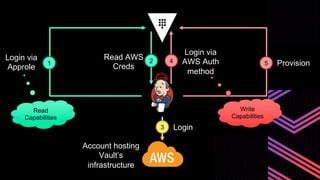
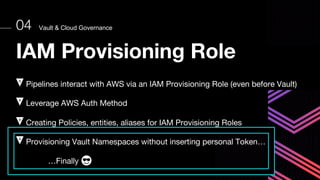
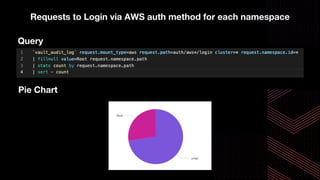
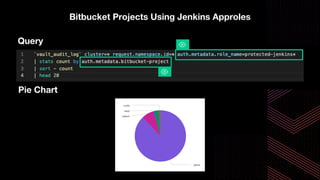
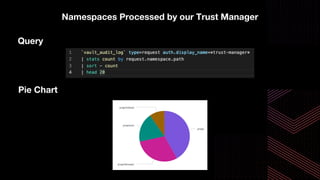
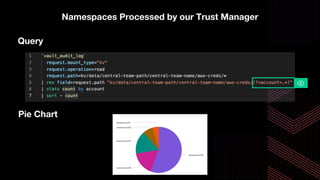
This document discusses integrating Hashicorp Vault with Jenkins for secrets management in a hybrid cloud scenario. It describes using AWS IAM roles to establish trust between Jenkins and Vault, encapsulating the authentication process in a shared Jenkins library, and provisioning Vault resources like namespaces in an automated fashion. This improves governance, standardizes processes, and provides better security and visibility through integration with tools like Splunk.