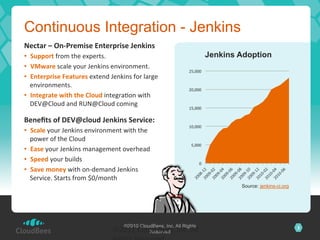
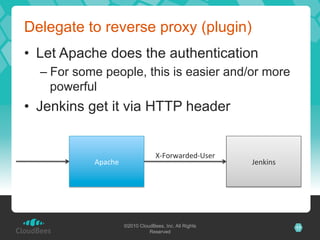
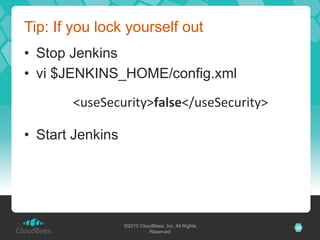
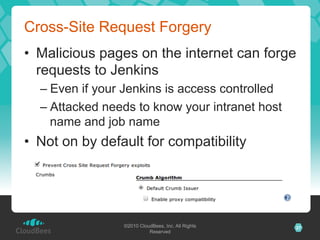
The document discusses the security architecture of Jenkins, focusing on access control, authentication, and authorization mechanisms. It outlines various authentication methods, including PAM, Active Directory, LDAP, and custom solutions, as well as detailing permission and authorization structures for safeguarding Jenkins environments. Additionally, it highlights potential security risks, such as cross-site request forgery, and suggests mitigation strategies for securing Jenkins and the builds it executes.