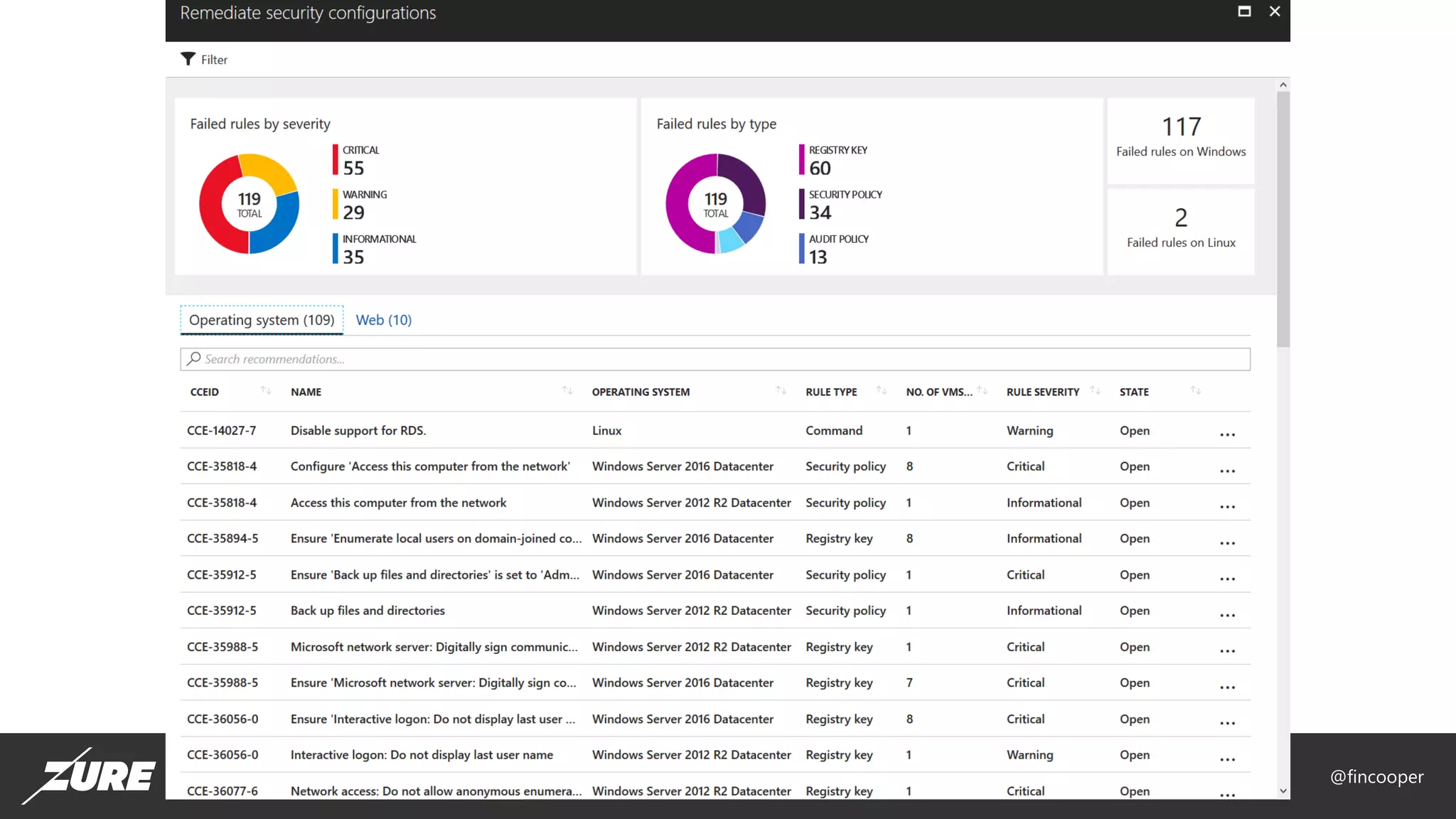
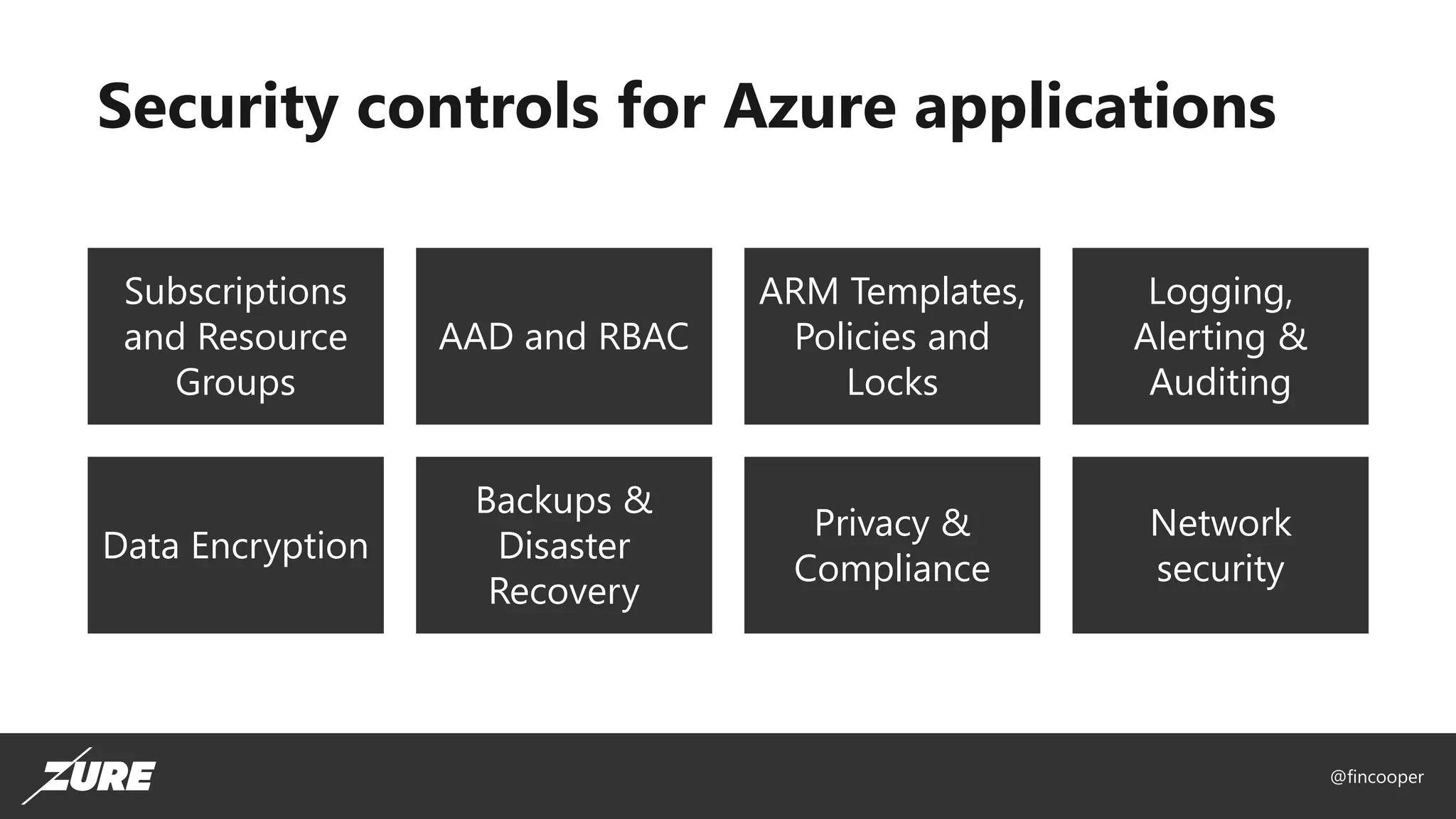
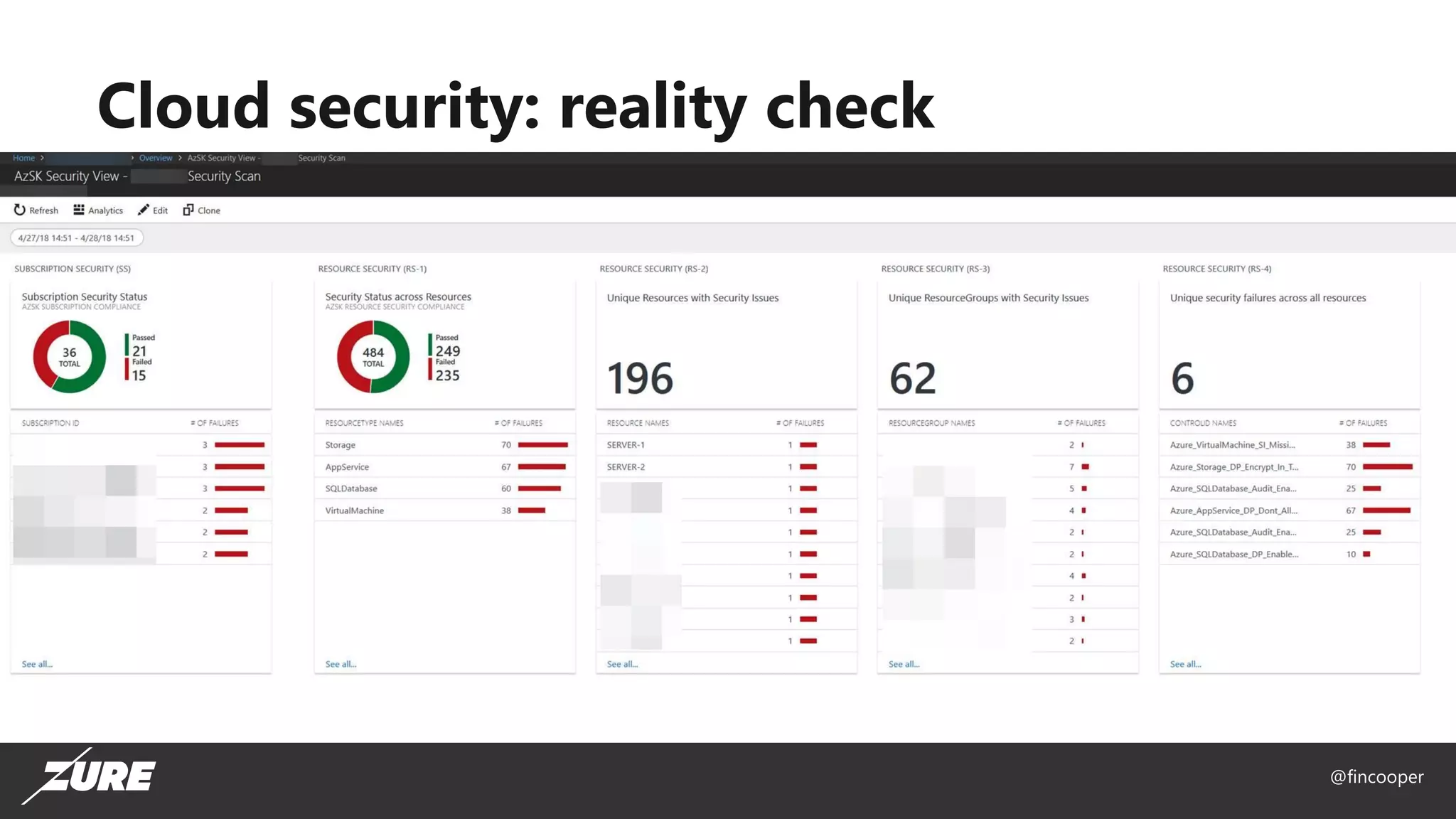
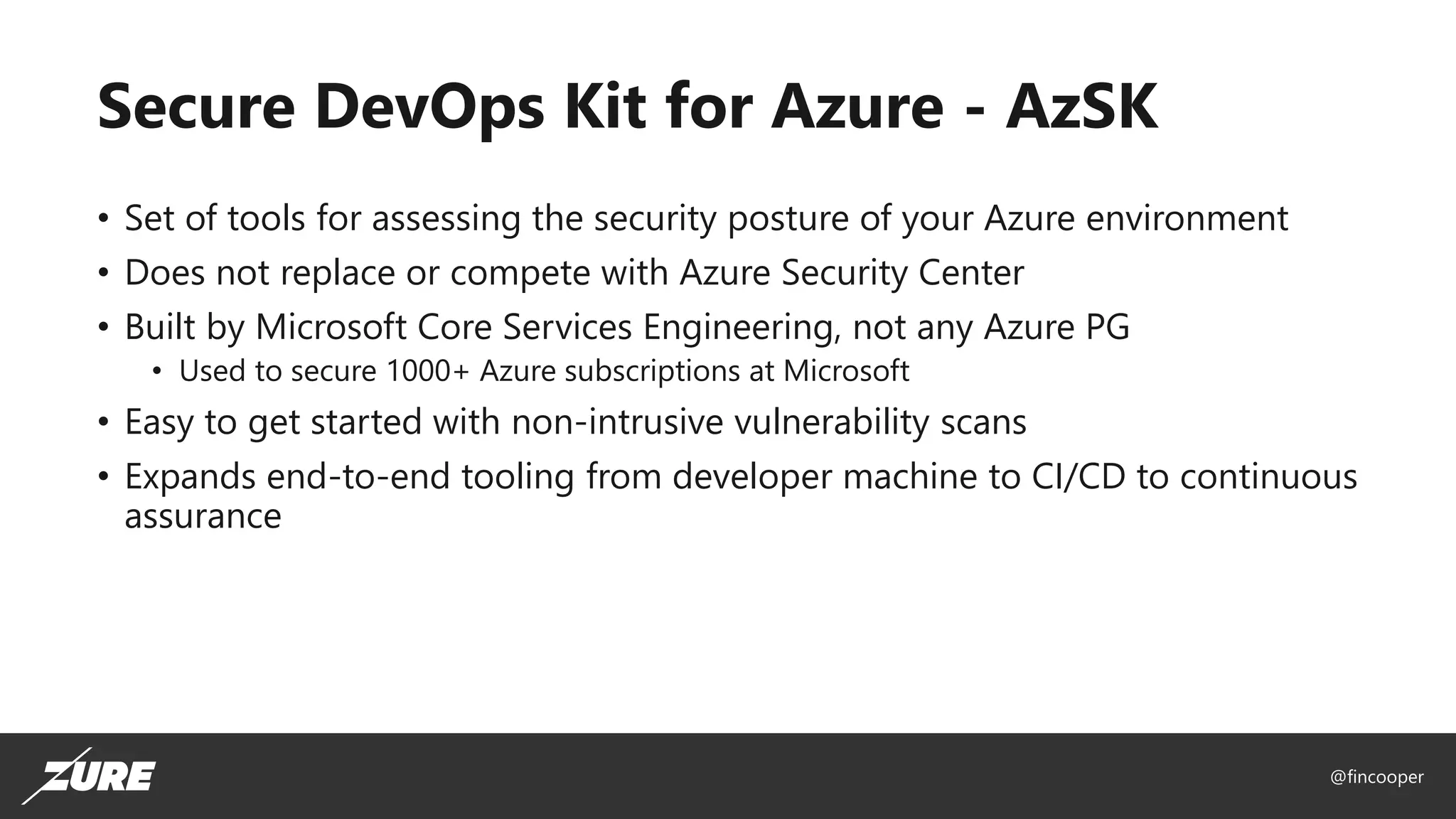
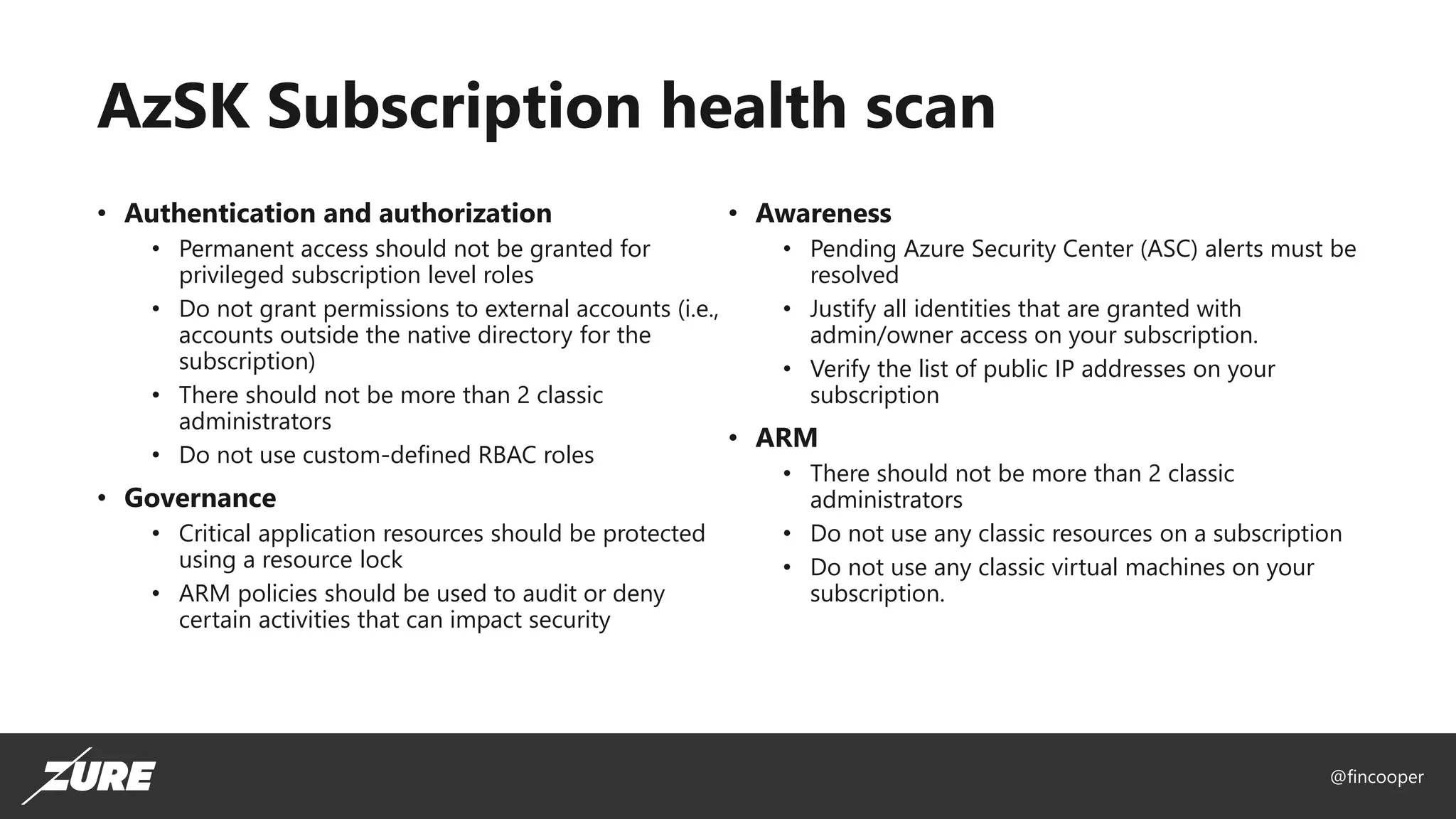
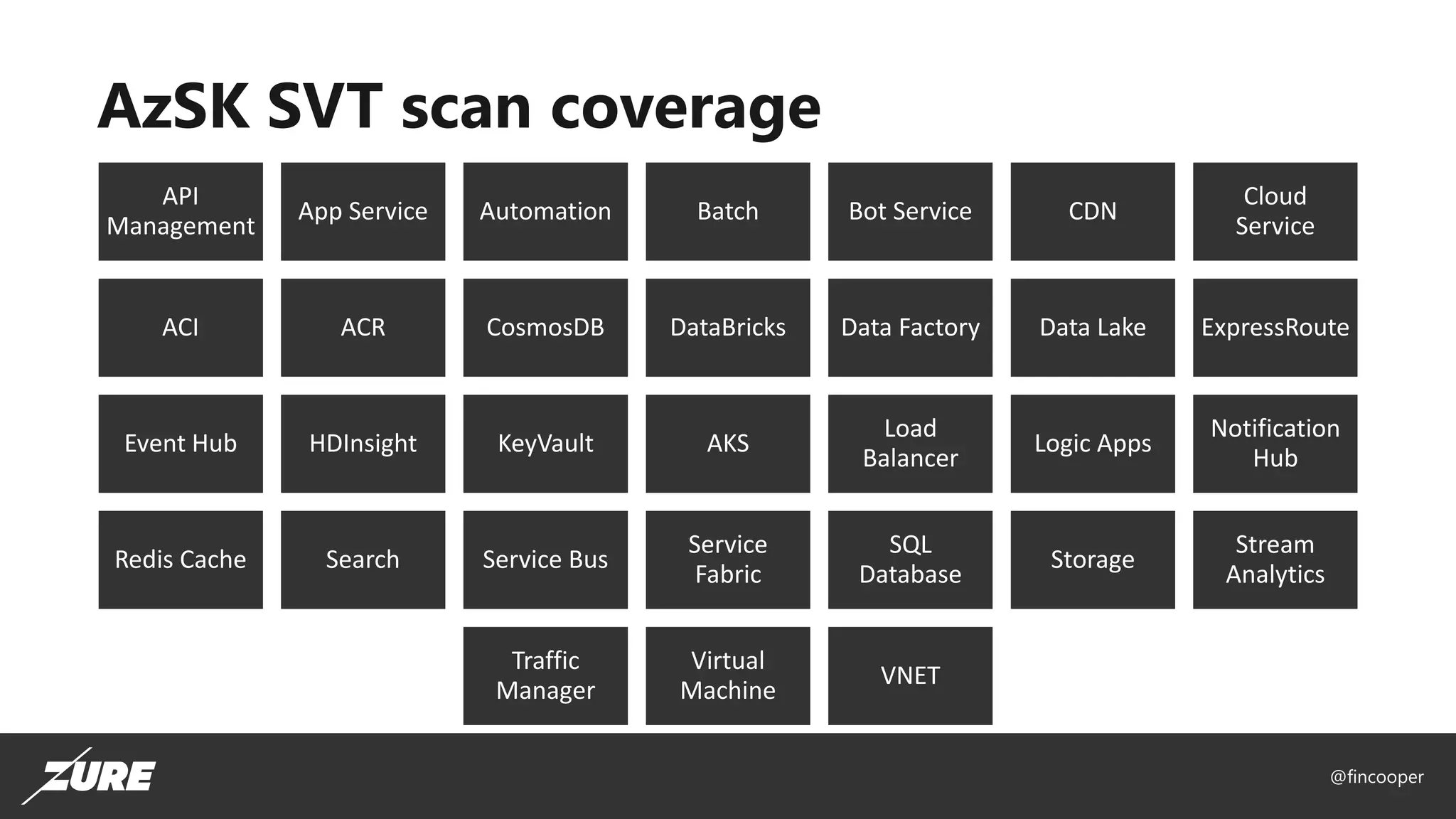
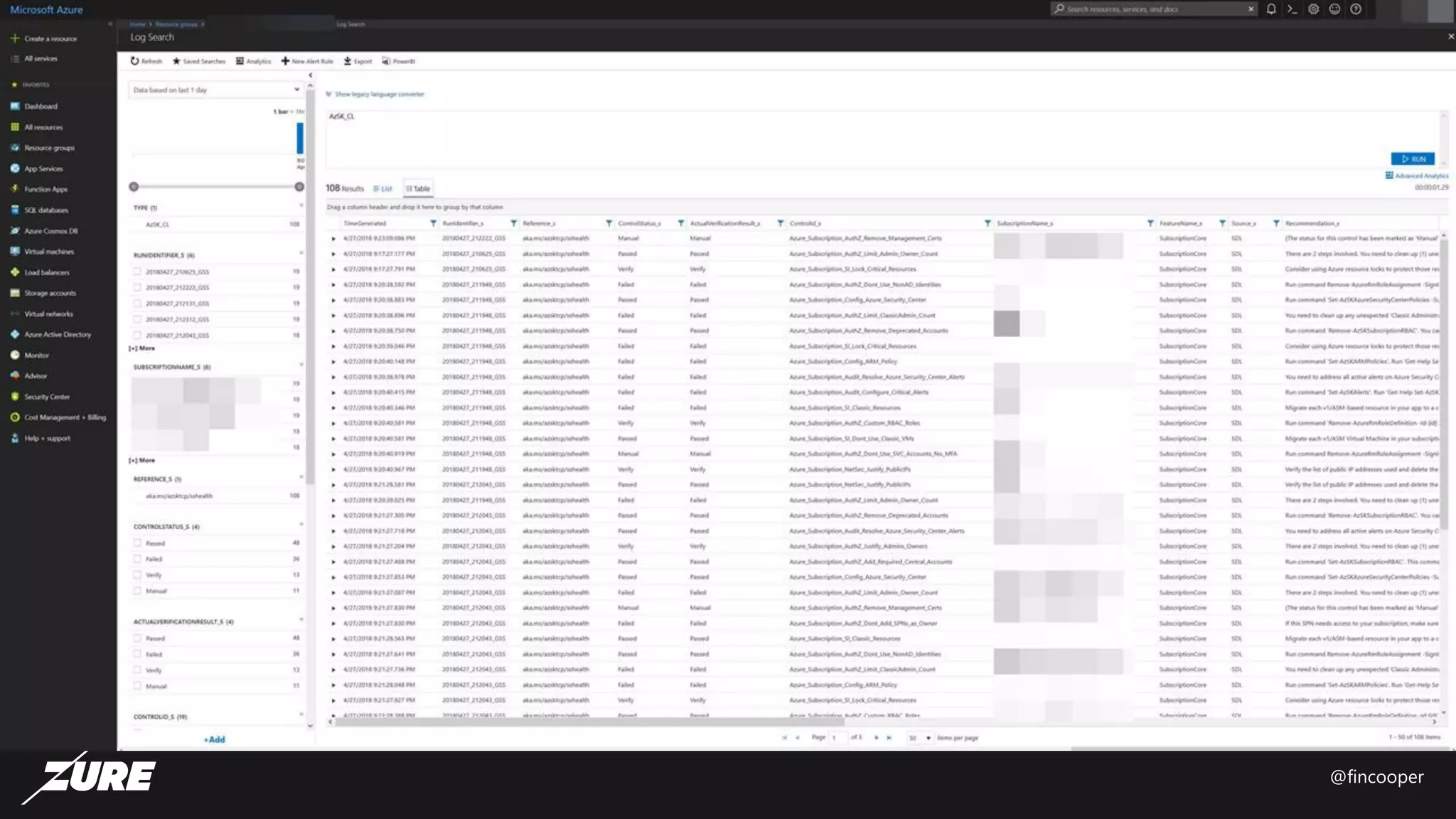
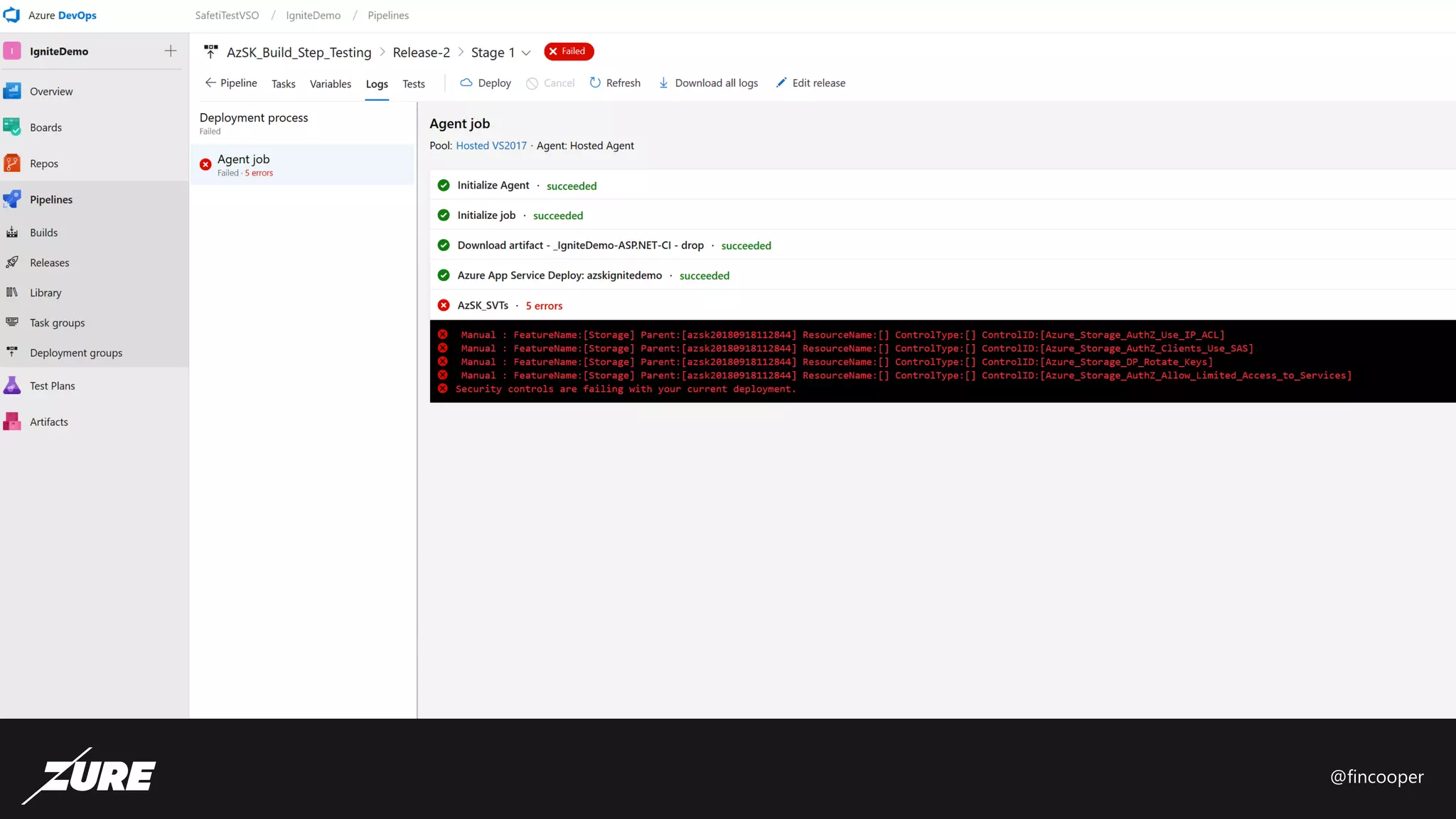
The document outlines a session on securing Azure applications, presenting an overview of Azure security controls, a crash course on the Secure DevOps Kit for Azure (AZSK), and various security practices. It discusses authentication, encryption, compliance, and specific vulnerabilities, emphasizing the importance of vulnerability scanning and continuous assurance. Additionally, it highlights the features and installation of AZSK and stresses that while AZSK aids in administrative security, comprehensive security must also involve threat modeling and addressing user access.