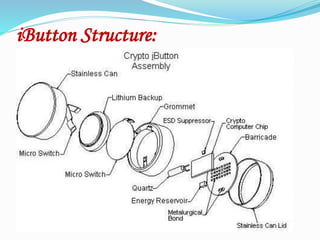
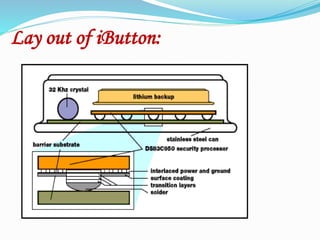
The document describes a Java ring, which is a finger ring containing a microprocessor and Java virtual machine. The ring can run applets to enable various functions like attendance tracking, door access, and car security. It contains RAM, ROM, a real-time clock, and an iButton - a stainless steel can housing a computer chip with a unique address. The iButton allows the ring to communicate with a reader and host system. The ring provides security through its stainless casing and ability to require a PIN. It has applications in access control and thermochron usage while being portable and rugged.