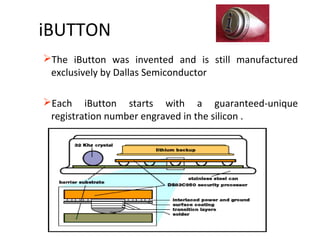
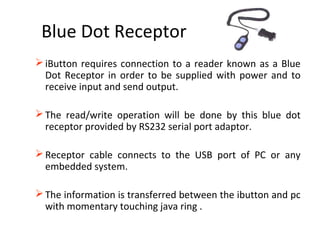
The document discusses Java Ring, which is a finger ring containing a microprocessor and capabilities for the user. It has a JVM, RAM, ROM, and connects to other devices using a blue dot receptor. Information is stored securely on the ring and the user can access accounts or unlock doors simply by touching the ring to the receptor. While convenient, Java Rings have limitations around cost, storage space, and potential for theft.