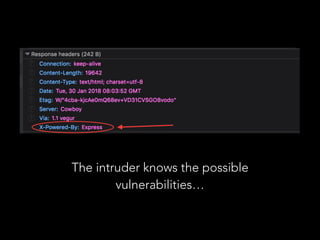
- Server-side JavaScript injection, cross-site scripting attacks, SQL injections, and cross-site request forgery are common security vulnerabilities in Node.js and Express applications. The document provides recommendations to prevent each vulnerability, including validating user input, escaping output, using prepared statements, and implementing CSRF tokens.
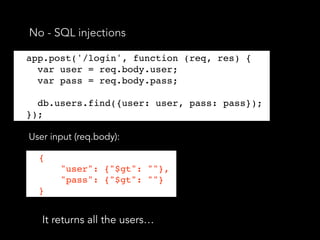
- Data validation and sanitization should be implemented for all endpoints accepting user data. Packages like express-validator can define validation schemas and sanitize input. Logging each request and response is also important for security monitoring and auditing.

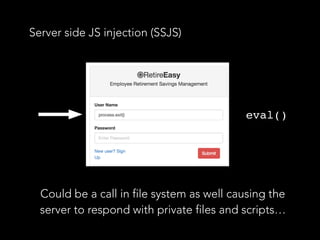
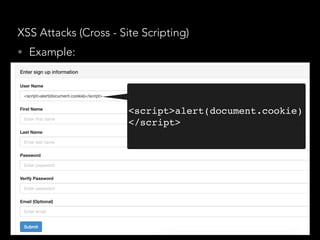
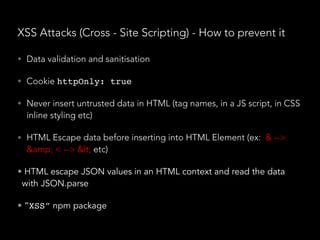
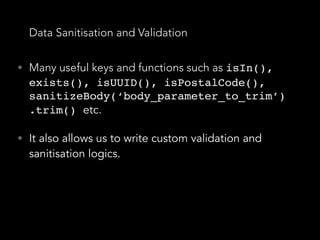
![SQL injections - How to prevent it
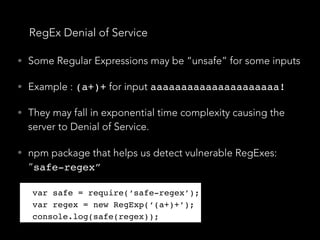
• (Once again…) Data validation and sanitisation
• “sqlstring” npm package, it escapes user input
values.
var sql = SqlString.format('SELECT * FROM users WHERE
id = ?', [userId]);
• “sql-query-builder” npm package
query().select([users.id.as('User'), users.id.count(1
)]).from(users).join(posts)
.on(posts.user_id).equals(users.id)
.groupBy(users.id);
• Far better than string concatenated SQL queries
var sql = SqlString.format('SELECT * FROM users WHERE
id = ?', [userId]);
query().select([users.id.as('User'), users.id.count(
1)]).from(users).join(posts)
.on(posts.user_id).equals(users.id)
.groupBy(users.id);](https://image.slidesharecdn.com/securitynode-180301210449/85/Security-in-Node-JS-and-Express-19-320.jpg)
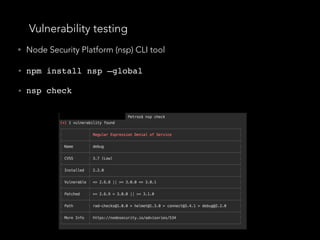
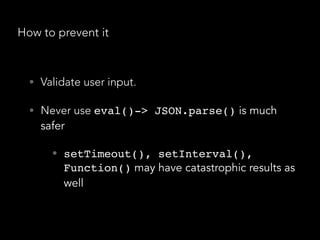
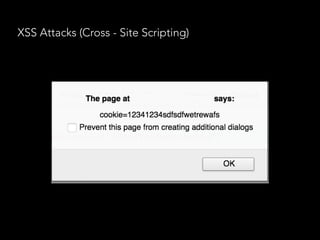
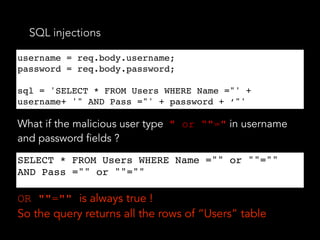
![No - SQL injections
• We have not set explicitly the query selector, so the
malicious user specified one for himself
db.users.find({user: {$in: [user]}, pass: {$in:
[pass]}});
db.users.find({user: { $in: [{ '$gt': '' }] },
pass: { $in: [{ '$gt': '' }] }});
• Now the query will return nothing.
• So we should always explicitly set the query selector!
• “mongoose” npm package - it escapes many of the
things mentioned above
db.users.find({user: {$in: [user]}, pass: {$in:
[pass]}});
db.users.find({user: { $in: [{ '$gt': '' }] },
pass: { $in: [{ '$gt': '' }] }});](https://image.slidesharecdn.com/securitynode-180301210449/85/Security-in-Node-JS-and-Express-21-320.jpg)


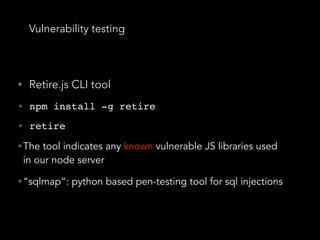
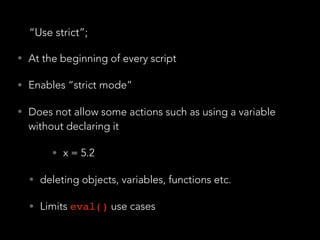
![Data Sanitisation and Validation
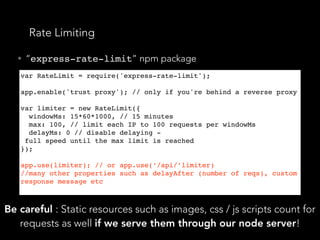
• “express-validator” allows us to create “check
schemas” for each endpoint in pure JSON.
app.put('/user/:id/password', checkSchema({
id: {
// The location of the field, can be one or more of body, cookies, headers,
params or query.
// If omitted, all request locations will be checked
in: ['params', 'query'],
errorMessage: 'ID is wrong',
isInt: true,
},
password: {
isLength: {
errorMessage: 'Password should be at least 7 chars long',
// Multiple options would be expressed as an array
options: { min: 7 }
}
}](https://image.slidesharecdn.com/securitynode-180301210449/85/Security-in-Node-JS-and-Express-28-320.jpg)