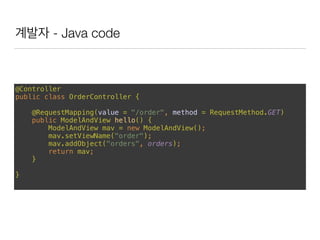
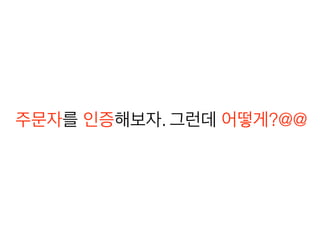
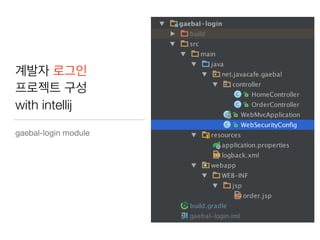
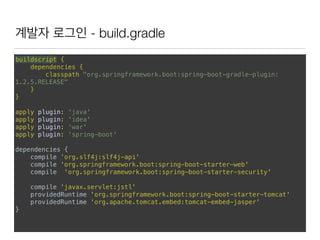
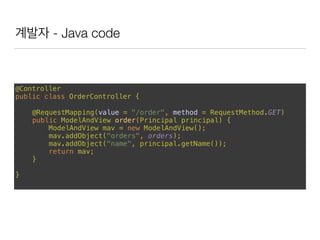
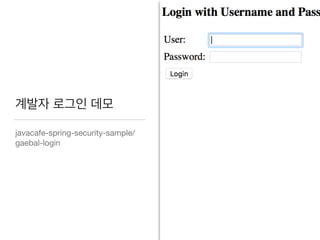
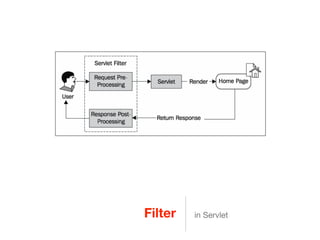
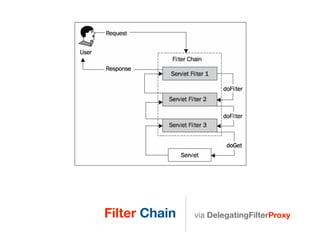
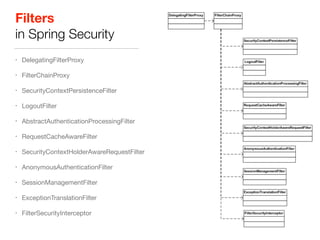
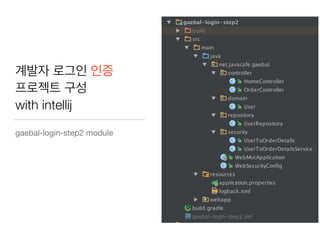
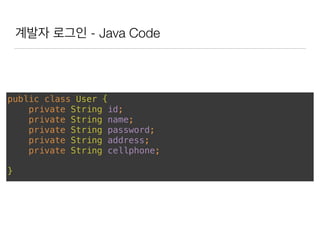
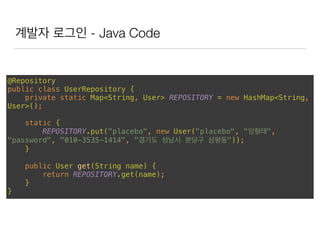
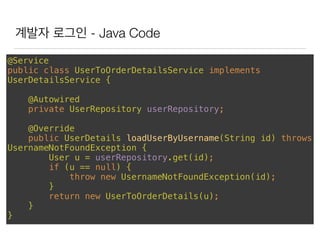
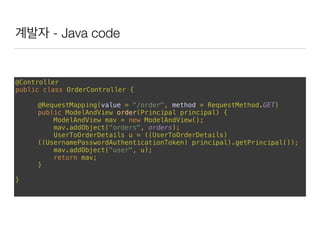
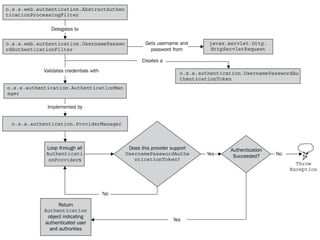
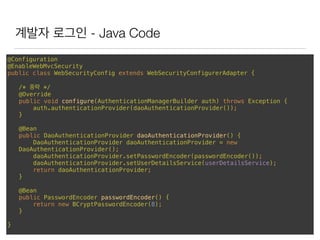
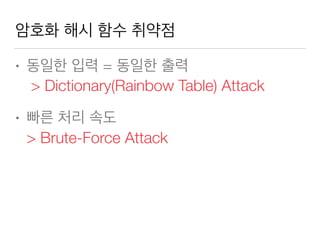
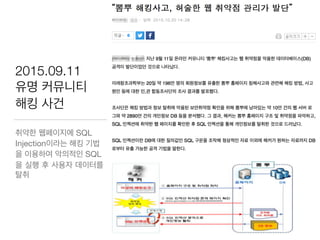
This document discusses using Spring Security and Spring Boot to add authentication to a web application. It introduces Spring Boot, which allows applications to "just run", and Spring Security which provides comprehensive authentication and authorization support. It then demonstrates adding login functionality to a sample web application called "Gaebal-ja" using Spring Security, including implementing a UserDetailsService to retrieve user information from a database. Authentication is handled using Spring Security filters.






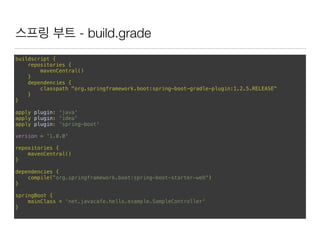
![스프링 부트 - Java code
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.EnableAutoConfiguration;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.ResponseBody;
@Controller
@EnableAutoConfiguration
public class SampleController {
@RequestMapping("/")
@ResponseBody
String home() {
return "<h1>Hello World!<br/>Hello Java Cafe!!</h1>";
}
public static void main(String[] args) throws Exception {
SpringApplication.run(SampleController.class, args);
}
}](https://image.slidesharecdn.com/random-151130013310-lva1-app6891/85/slide-11-320.jpg)

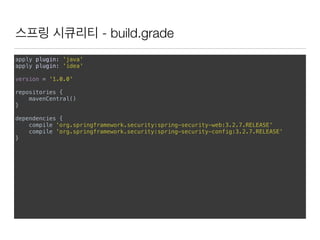
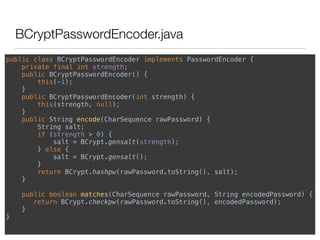
![스프링 시큐리티 - Java code
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.core.context.SecurityContextHolder;
public class AuthenticationExample {
static AuthenticationManager authenticationManager = new SampleAuthenticationManager();
public static void main(String[] args) throws Exception {
BufferedReader in = new BufferedReader(new InputStreamReader(System.in));
while (true) {
String name = in.readLine();
String password = in.readLine();
try {
Authentication req = new UsernamePasswordAuthenticationToken(name, password);
Authentication result = authenticationManager.authenticate(req);
SecurityContextHolder.getContext().setAuthentication(result);
break;
} catch (AuthenticationException e) {
System.out.println("Authentication failed: " + e.getMessage());
}
}
System.out.println(SecurityContextHolder.getContext().getAuthentication());
}
}](https://image.slidesharecdn.com/random-151130013310-lva1-app6891/85/slide-16-320.jpg)





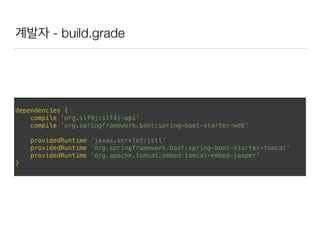
![계발자 - Java code
import org.springframework.boot.autoconfigure.EnableAutoConfiguration;
import org.springframework.boot.builder.SpringApplicationBuilder;
import org.springframework.boot.context.embedded.EmbeddedServletContainerCustomizer;
import org.springframework.boot.context.web.SpringBootServletInitializer;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.ComponentScan;
import org.springframework.context.annotation.Configuration;
@Configuration
@ComponentScan
@EnableAutoConfiguration
public class WebMvcApplication extends SpringBootServletInitializer {
@Override
protected SpringApplicationBuilder configure(SpringApplicationBuilder application) {
return application.sources(WebMvcApplication.class);
}
public static void main(String[] args) {
SpringApplicationBuilder builder = new SpringApplicationBuilder();
WebMvcApplication application = new WebMvcApplication();
application.configure(builder);
builder.run(args);
}
@Bean
public EmbeddedServletContainerCustomizer embeddedServletContainerCustomizer() {
return factory -> factory.setDocumentRoot(new File("gaebal-base/src/main/webapp"));
}
}](https://image.slidesharecdn.com/random-151130013310-lva1-app6891/85/slide-24-320.jpg)