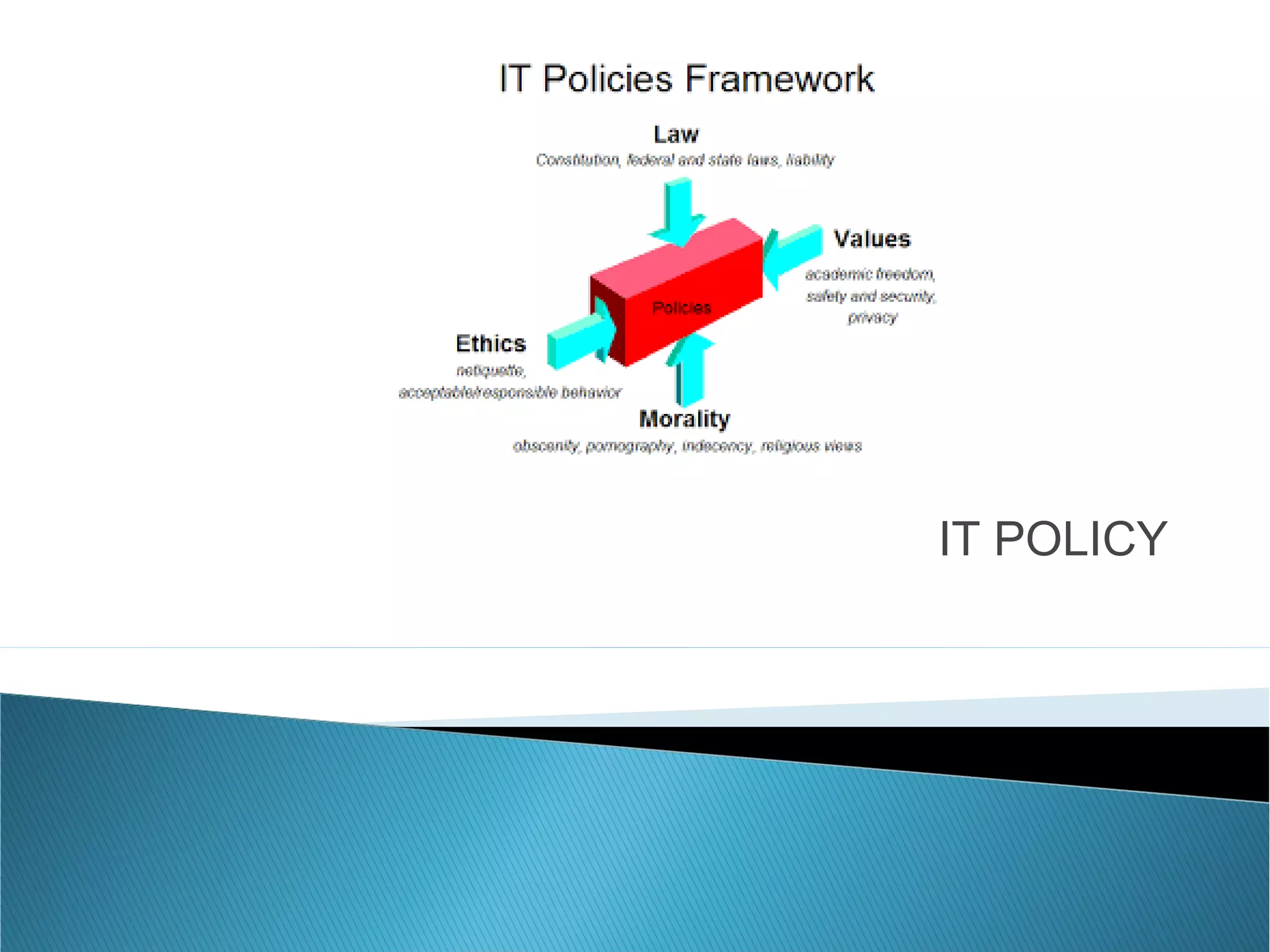
The document outlines the importance of establishing IT policies for companies. It discusses how policies help define appropriate and legal use of technology, protect sensitive data and intellectual property, and reduce security risks and legal liability. The document also describes how well-defined IT policies improve efficiency, compliance, and establish guidelines and culture of security for employees. Key aspects that policies may cover include email, internet, hardware and software usage, access controls, backups, and third party access. COBIT is referenced as a framework to help optimize IT investments and governance.