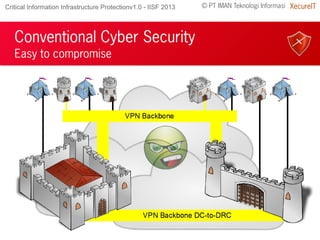
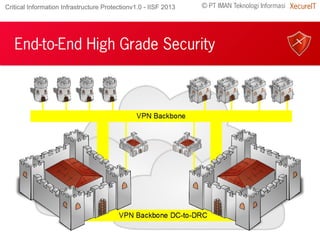
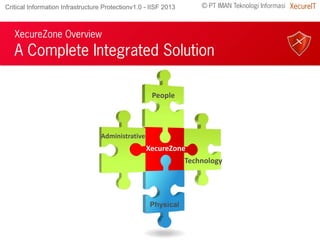
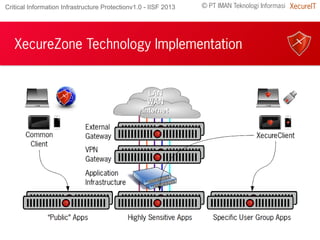
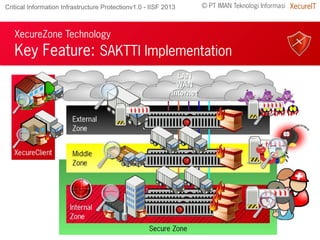
The document discusses the importance of robust cybersecurity measures and highlights the inadequacies of conventional security strategies. It introduces 'xecurezone', a comprehensive solution aimed at optimizing information security architecture (Saktti) and simplifying compliance processes. The approach emphasizes the need for a strong management commitment and competent professionals in addressing cybersecurity challenges.