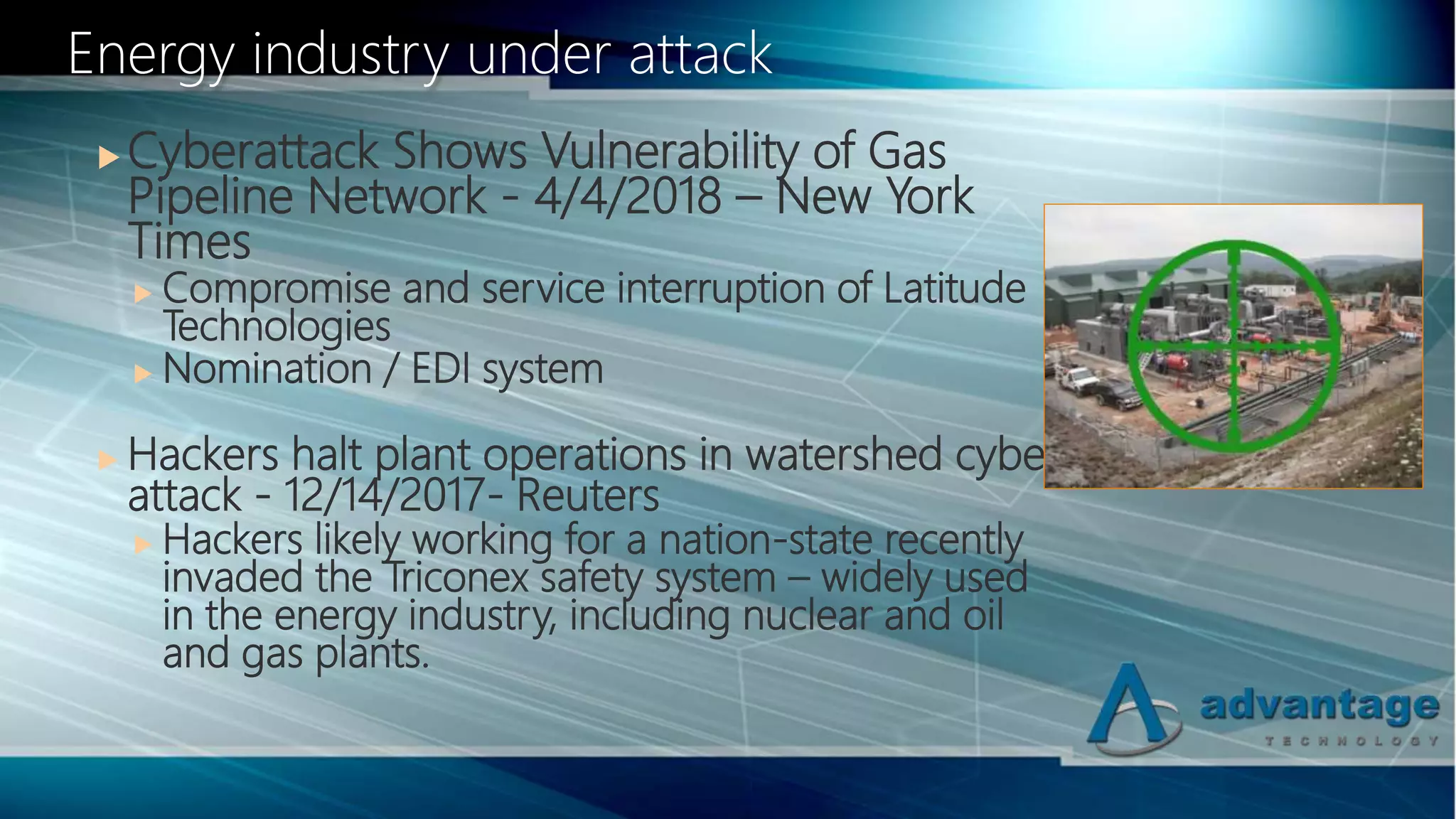
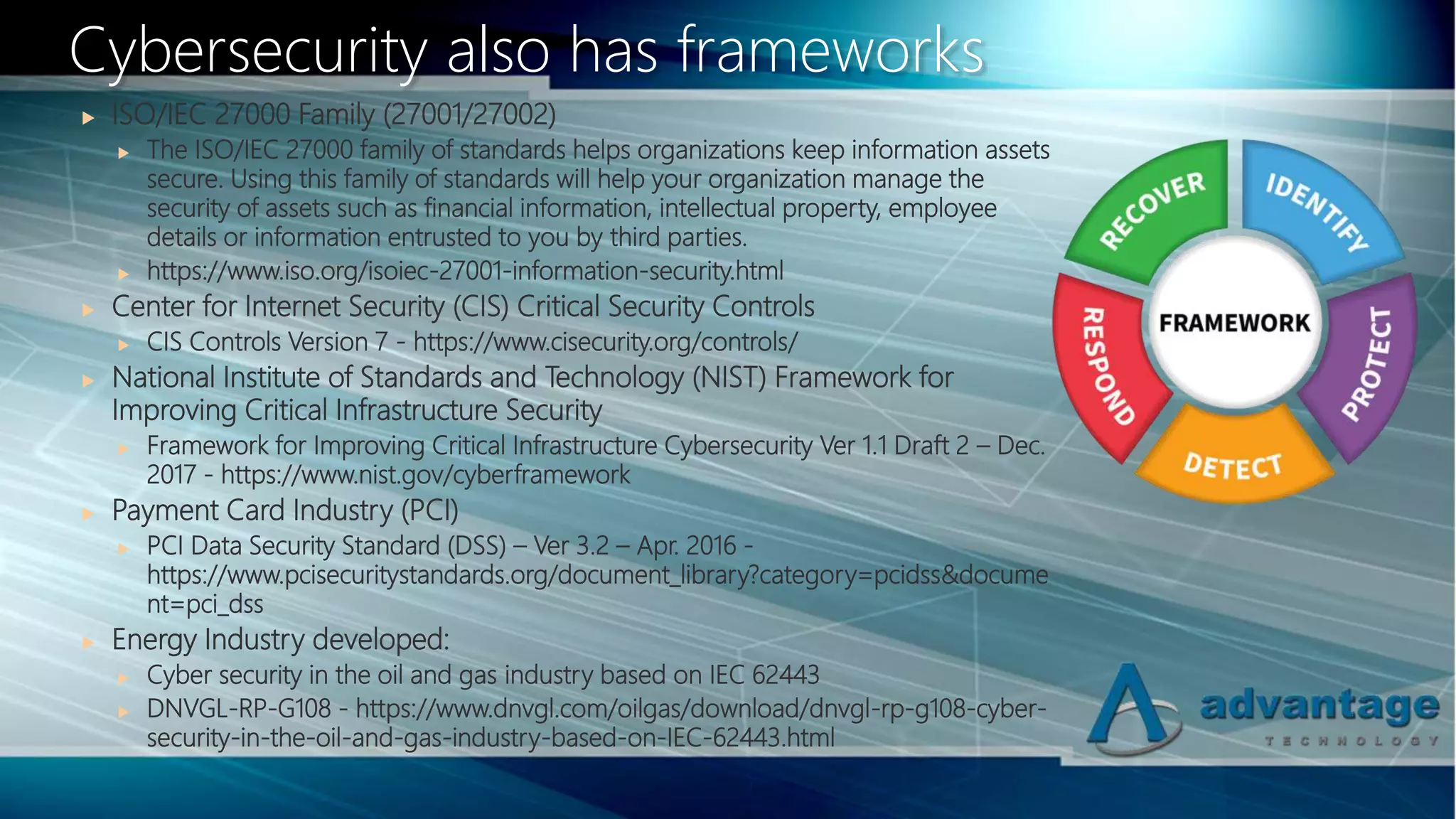
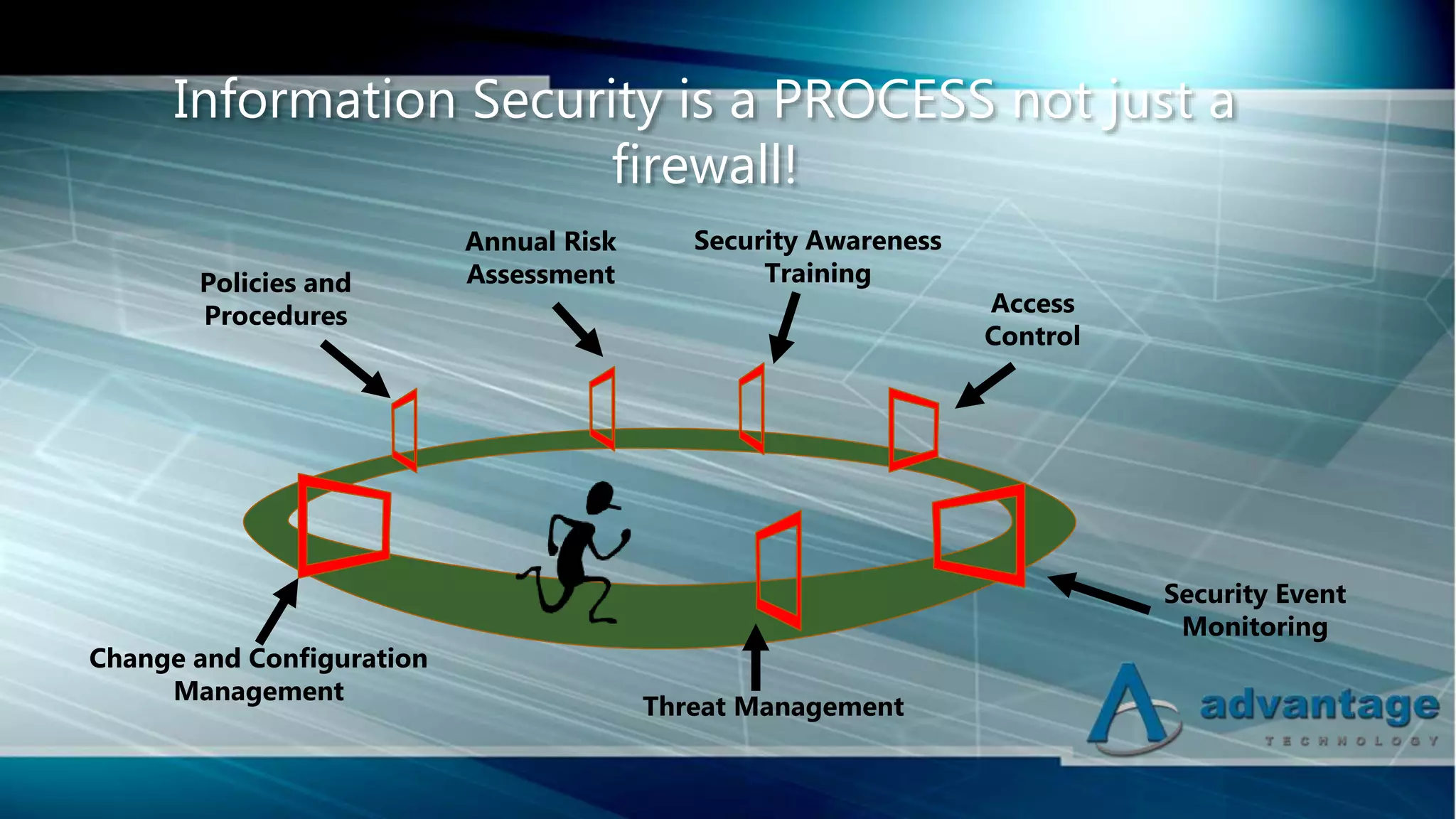
The document discusses cybersecurity vulnerabilities in the oil and gas industry and frameworks to address them. It notes recent cyber attacks on energy infrastructure and outlines factors that make the industry vulnerable, such as lack of training, remote work practices, outdated systems, and insufficient network separation. It then introduces several cybersecurity standards and frameworks that can help organizations in the industry implement effective security practices, including ISO 27001, NIST Framework, CIS Controls, and IEC 62443. The presentation emphasizes that information security requires an ongoing process rather than just technology solutions.