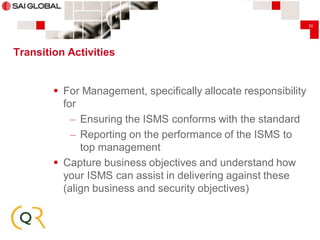
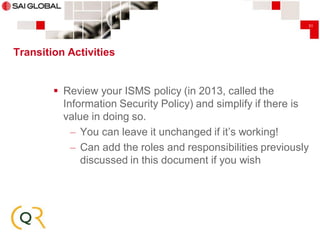
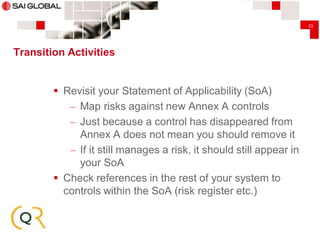
This document provides an overview of transitioning an information security management system (ISMS) from ISO/IEC 27001:2005 to ISO/IEC 27001:2013. It begins with introductions from SAI Global and CQR, both of which provide ISO 27001 consulting and certification services. The document then outlines the key changes between the 2005 and 2013 versions, including changes to mandatory clauses, risk management requirements, controls in Annex A, and transition activities. It emphasizes reviewing the ISMS scope, risk assessments, documentation, metrics, and certification timelines as part of the transition process. The presentation aims to help organizations understand the differences between the standards and plan their transition.