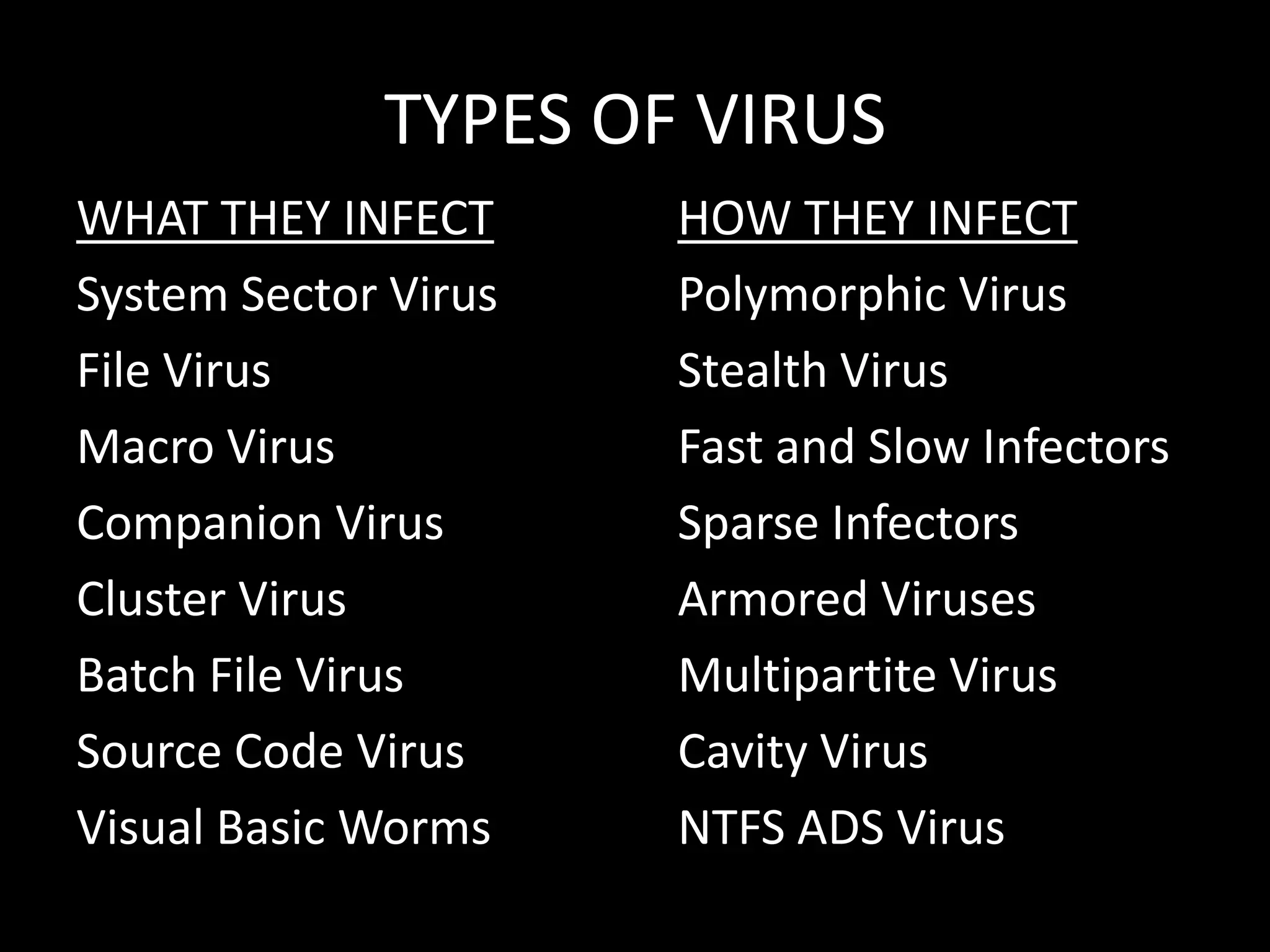
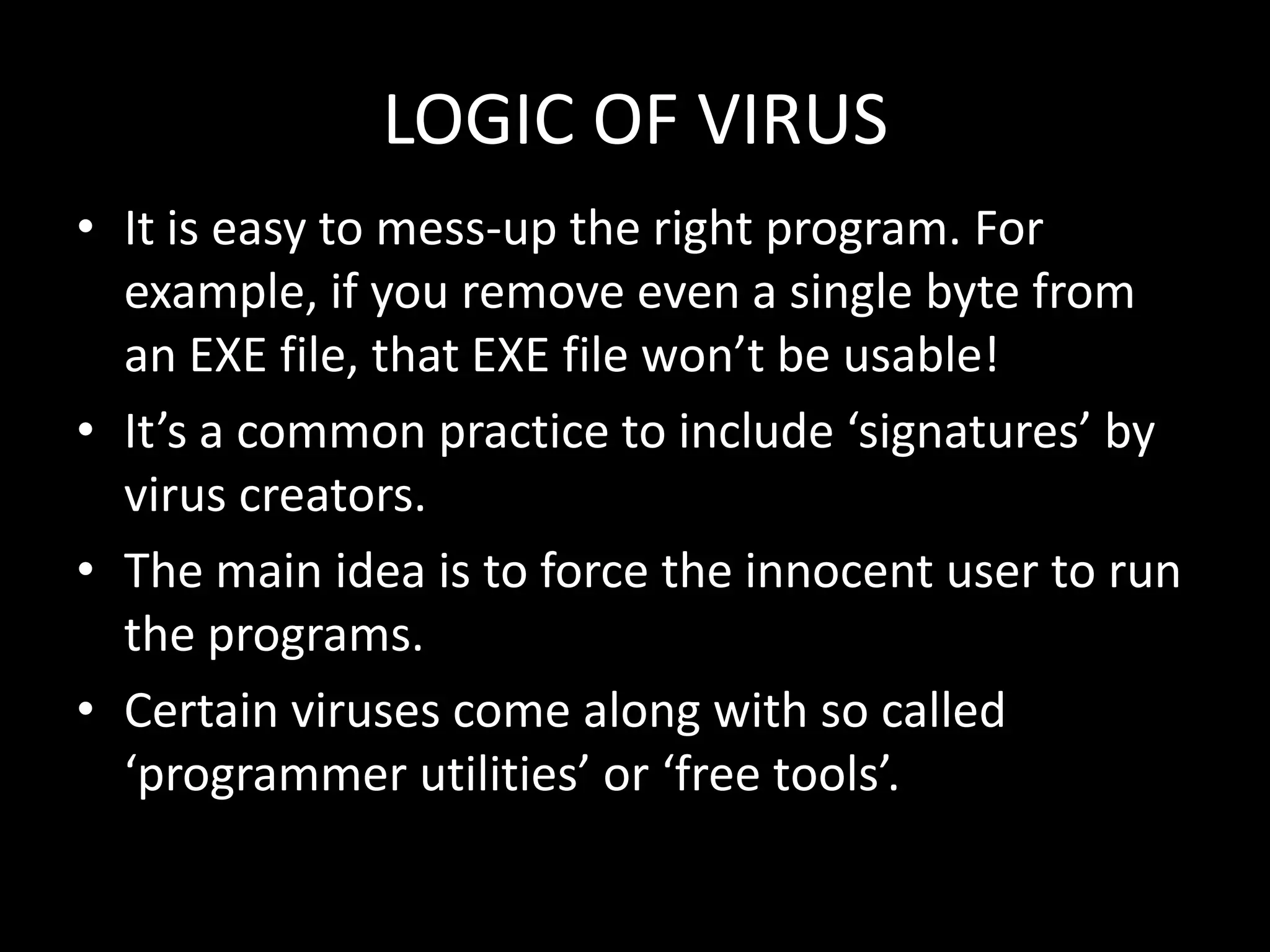
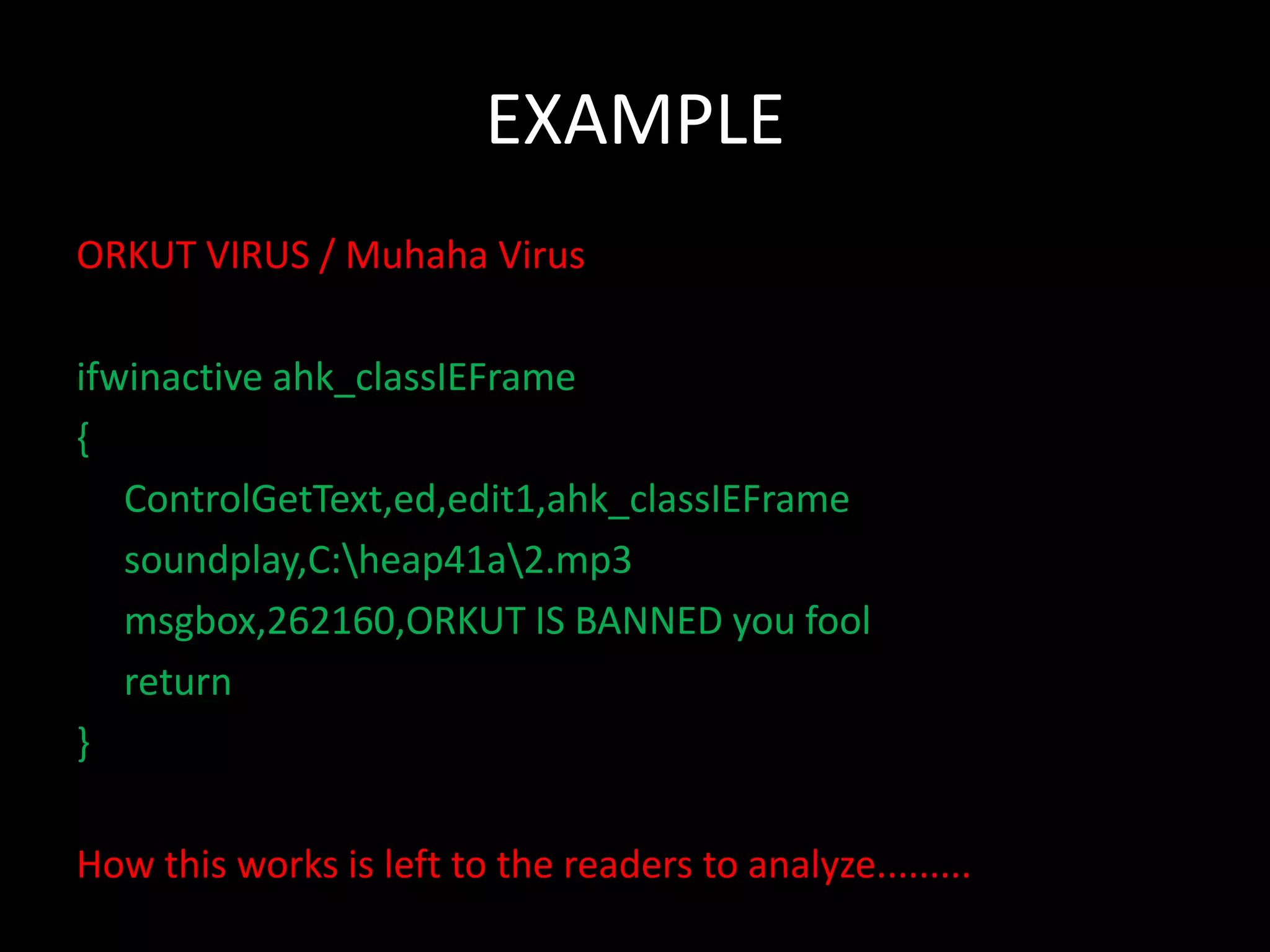
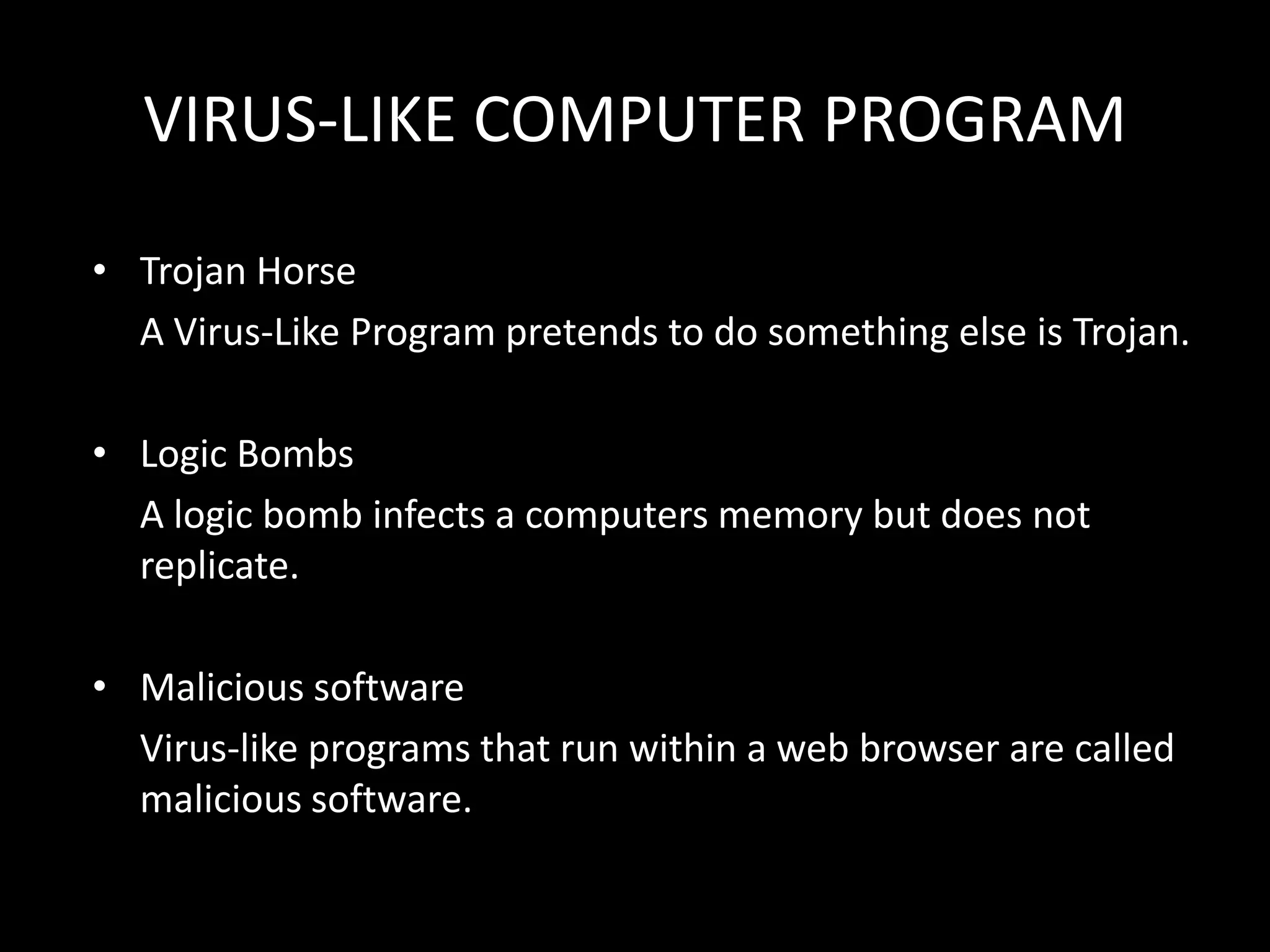
This document discusses computer viruses, including their introduction, etymology, history, types, logic, examples, signatures, and preventive measures. It defines computer viruses as self-replicating programs that infect files and spread. The first paper to use the term "virus" was in 1984, while the first viruses appeared in the early 1970s. Common types include file, macro, and boot sector viruses. Signatures help identify specific viruses, and anti-virus software using signatures and heuristics can detect and remove viruses.