This document provides information about computer viruses and firewalls in 3 paragraphs.
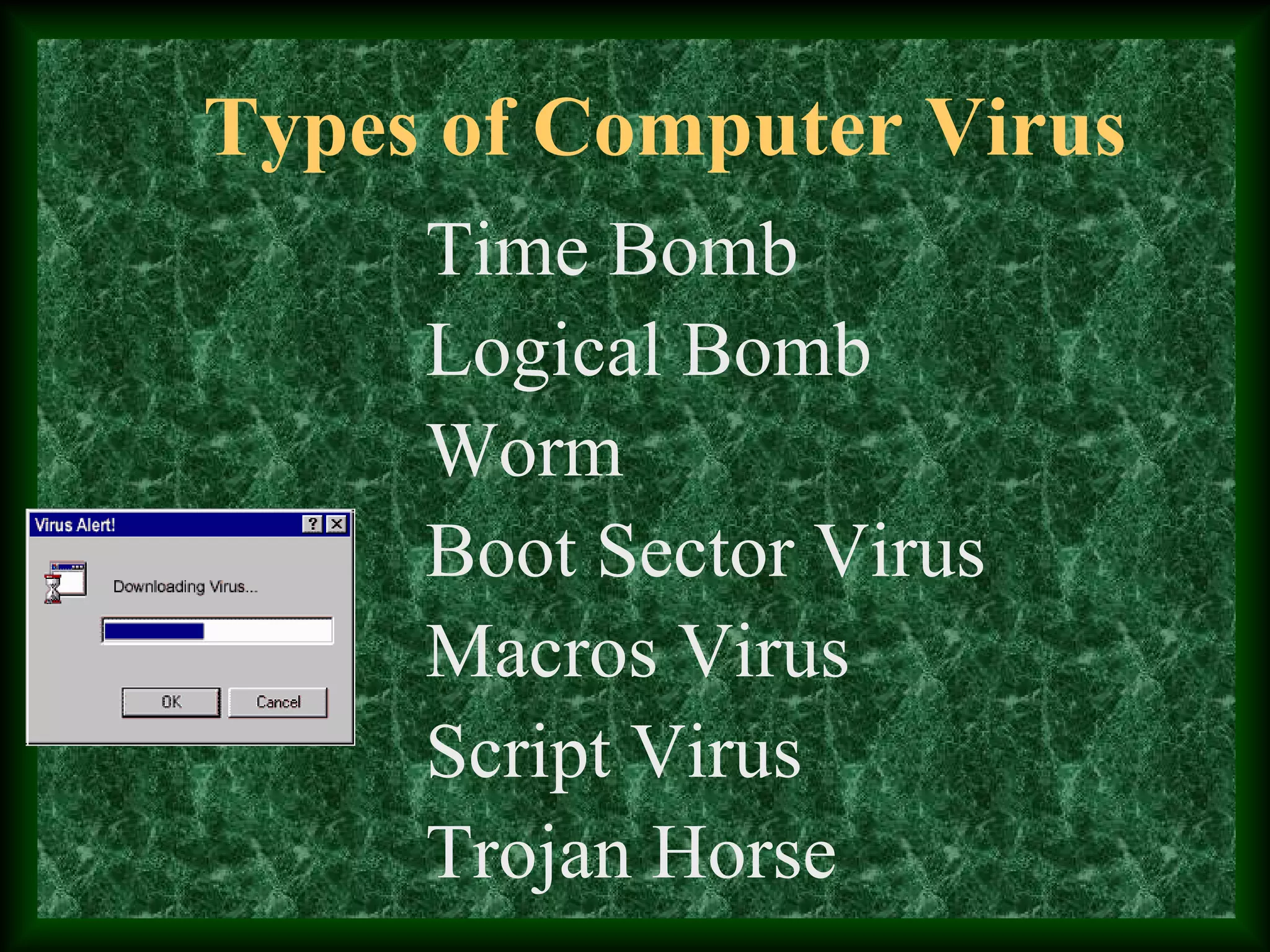
It first discusses various types of computer viruses like time bombs, logical bombs, worms, boot sector viruses, macro viruses, script viruses, and trojan horses.
The second paragraph lists actions that can be taken to prevent virus infections, such as updating antivirus software weekly, backing up important files, and not opening unexpected email attachments.
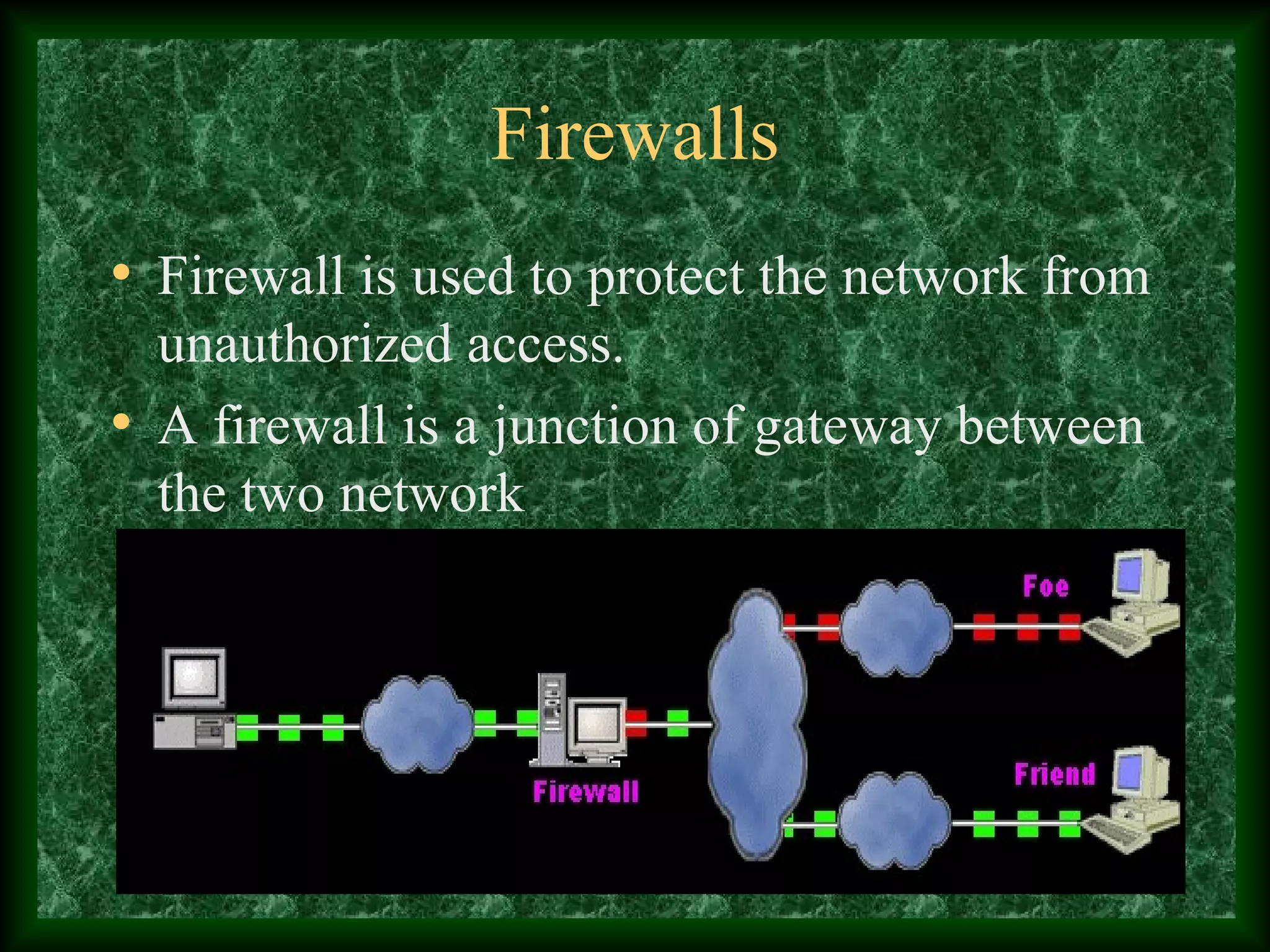
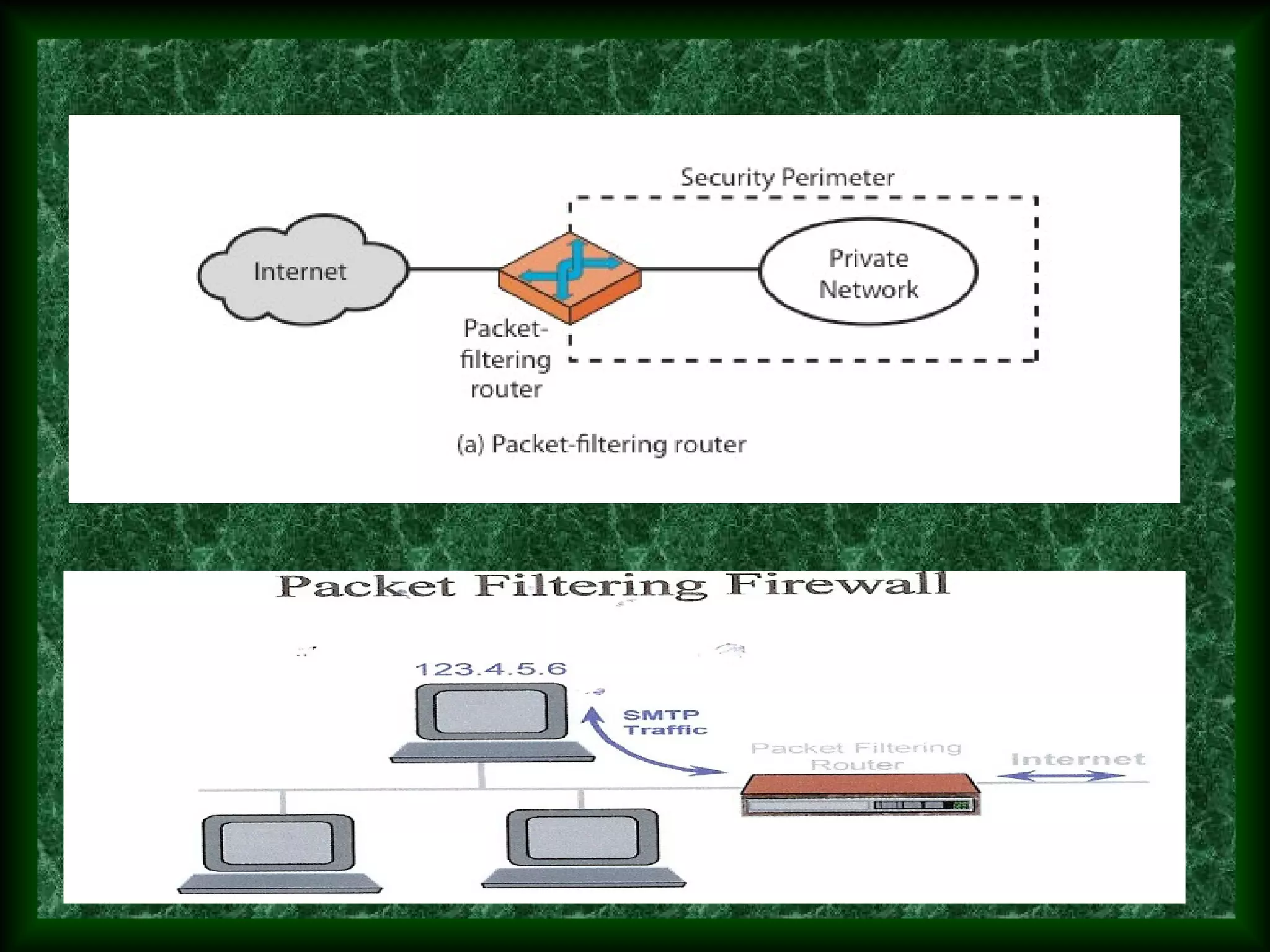
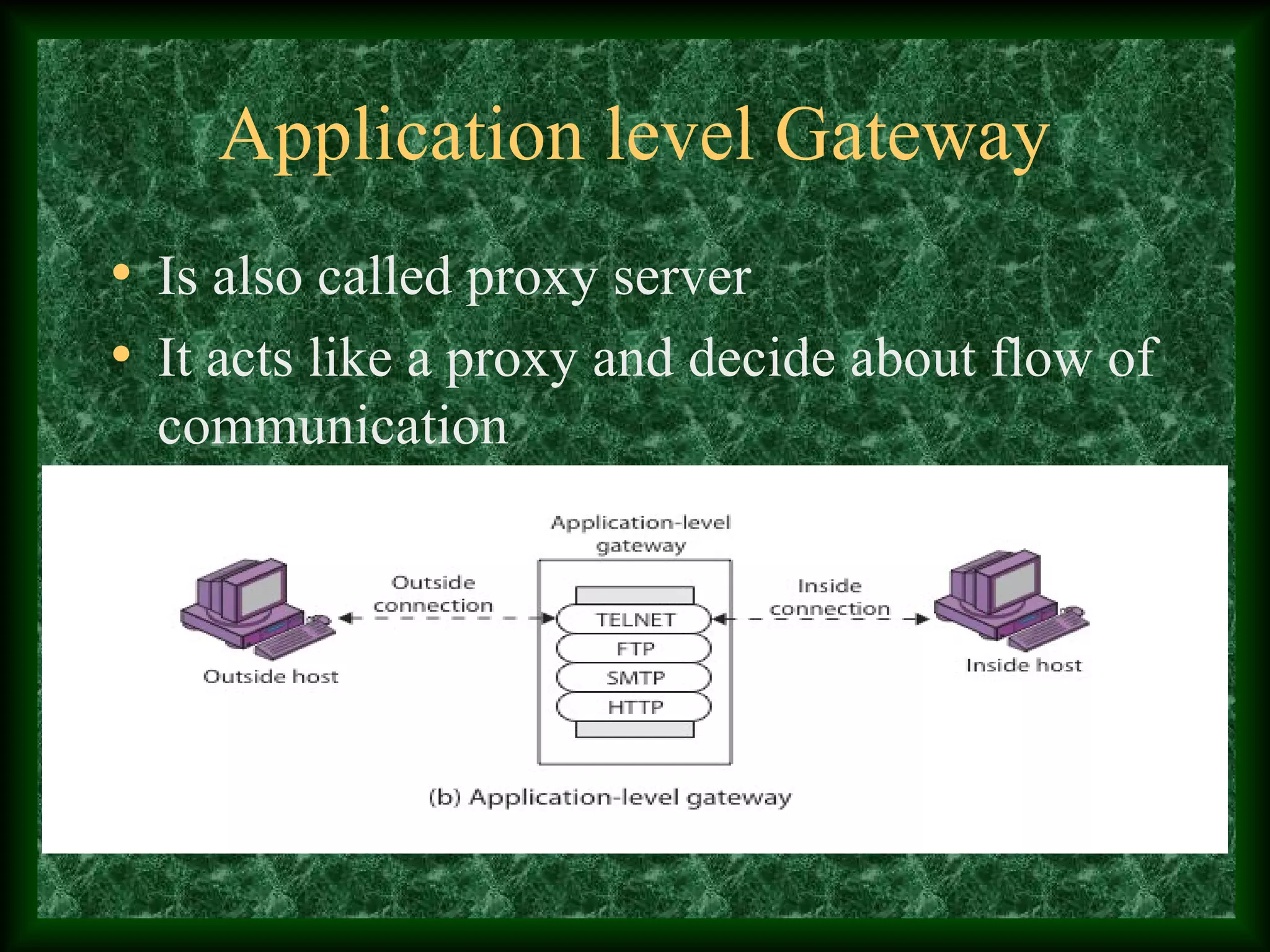
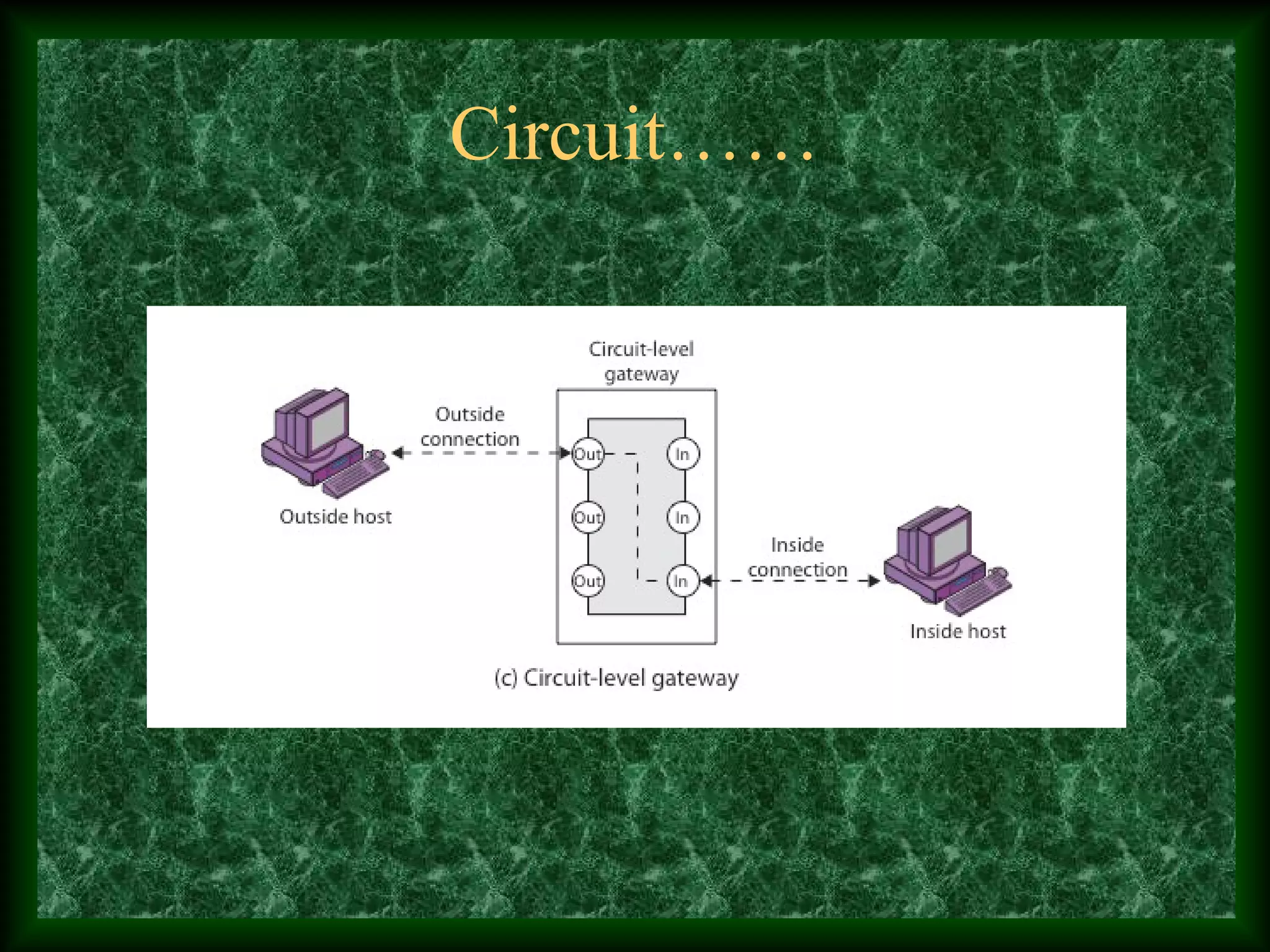
The third paragraph describes different types of firewalls - packet filtering firewalls, application gateways, and circuit level gateways - and provides brief details about how each works.