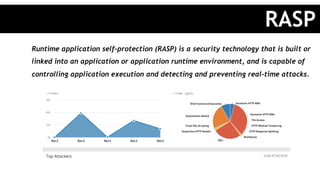
The document discusses various security vulnerabilities in Python applications, including SQL injection, cross-site scripting (XSS), and remote command execution, emphasizing their potential risks and impacts. It highlights best practices such as using parameterized queries, leveraging frameworks, and performing static code analysis to enhance application security. Additionally, it advocates for using security technologies like Runtime Application Self-Protection (RASP) and keeping frameworks and libraries up to date.



















![cp = subprocess.Popen(['ls', '-l'], shell=True)
# disables shell based features (like no pipe)
cp= subprocess.Popen(['ls', '-l’)
filename = 'somefile; rm -rf ~’
command = 'ls -l {}'.format(filename)
print(command) # noooooooooo
>>> ls -l somefile; rm -rf ~
filename = 'somefile; rm -rf ~’
command = 'ls -l {}'.format(quote(filename))
print(command) # better luck next time
>>> ls -l 'somefile; rm -rf ~’
shell & quote](https://image.slidesharecdn.com/isyourpythonapplicationsecure-pyconcanada-2015-11-07-151107172245-lva1-app6891/85/Is-your-python-application-secure-PyCon-Canada-2015-11-07-21-320.jpg)