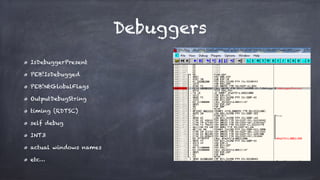
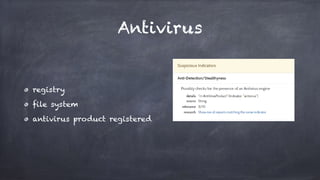
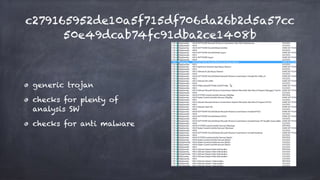
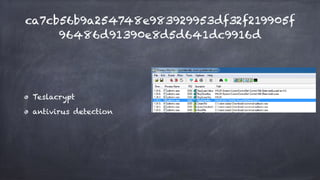
This document discusses how malware authors try to detect analysis environments like sandboxes, virtual machines, and debuggers in order to avoid analysis. It presents real world malware examples that use these detection techniques. The document then proposes potential "vaccination" techniques to emulate unhealthy environments in order to trick malware into thinking it is not being analyzed, making the researcher's job easier. It showcases some proof-of-concept tools developed by the author for this purpose, including tools to fake the presence of virtual machines and debuggers. Challenges with vaccination techniques are also discussed.