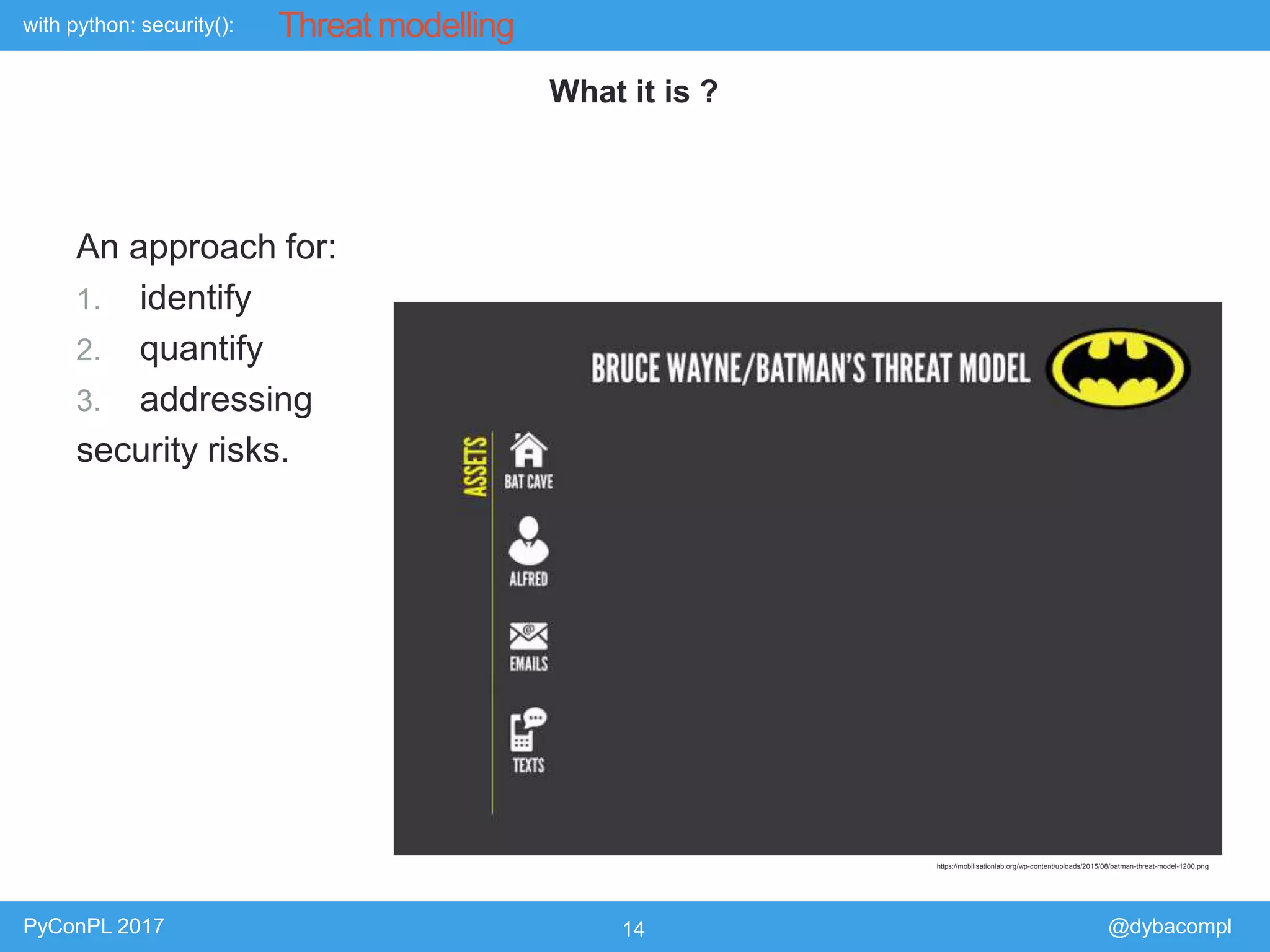
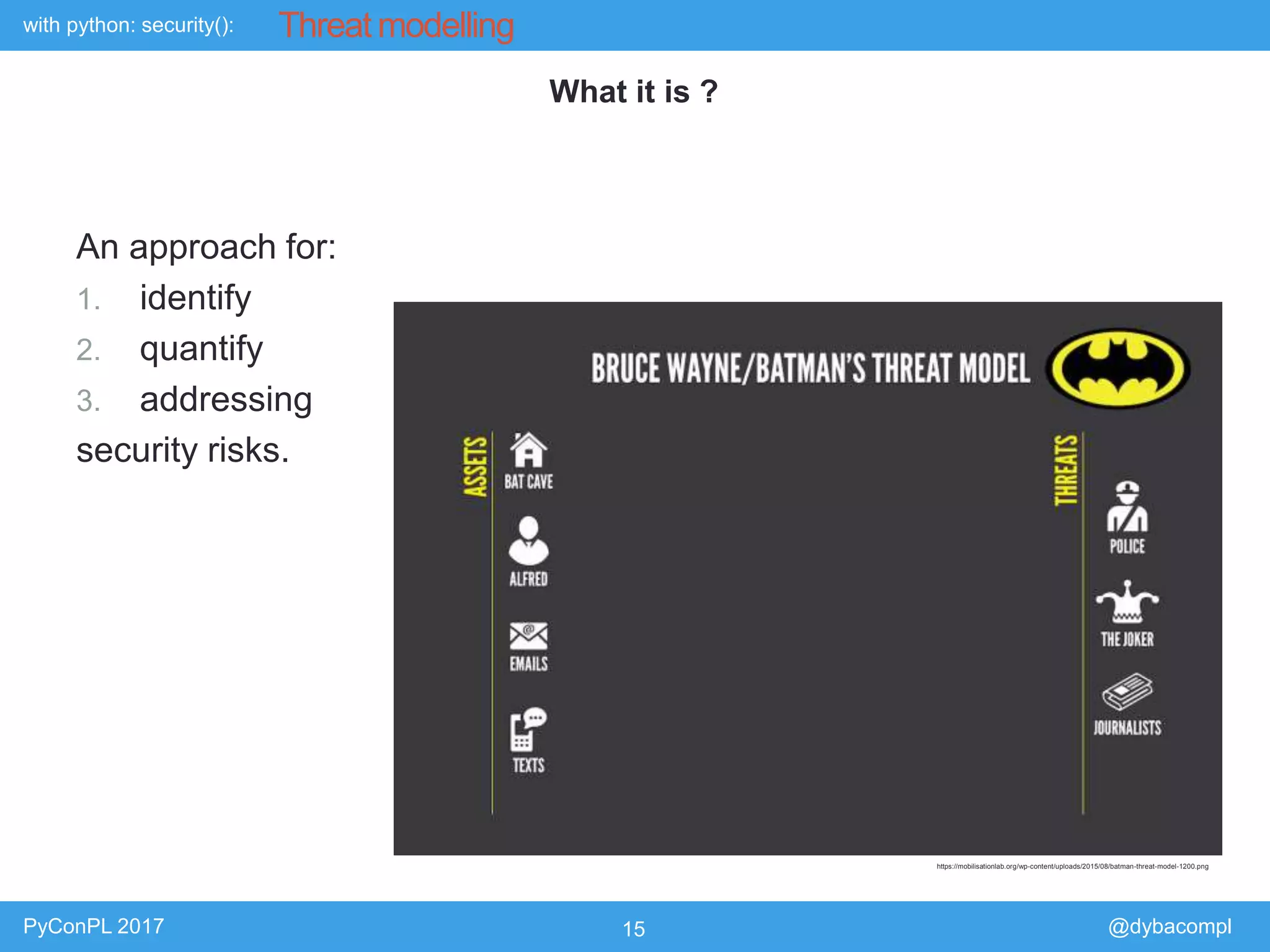
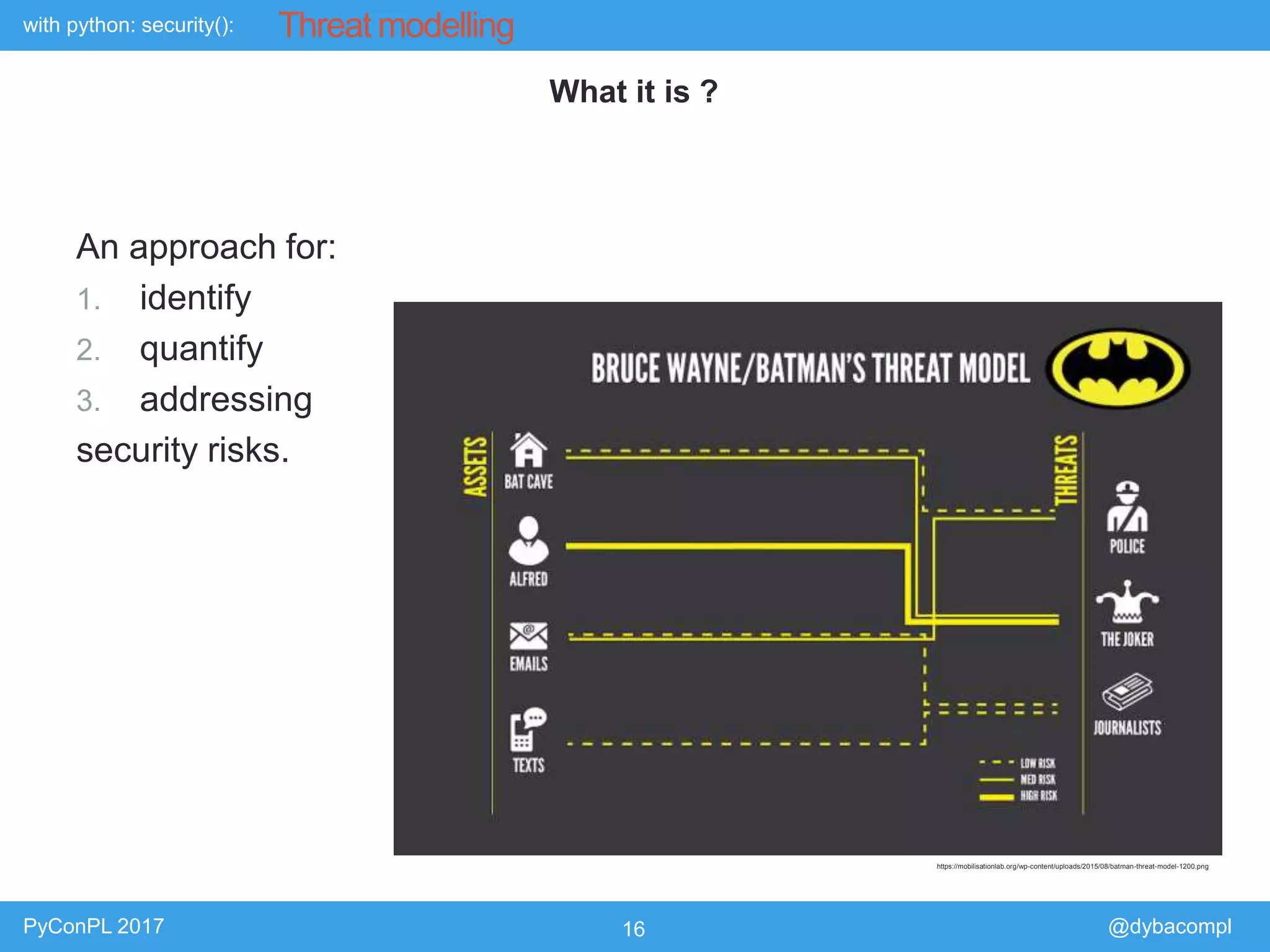
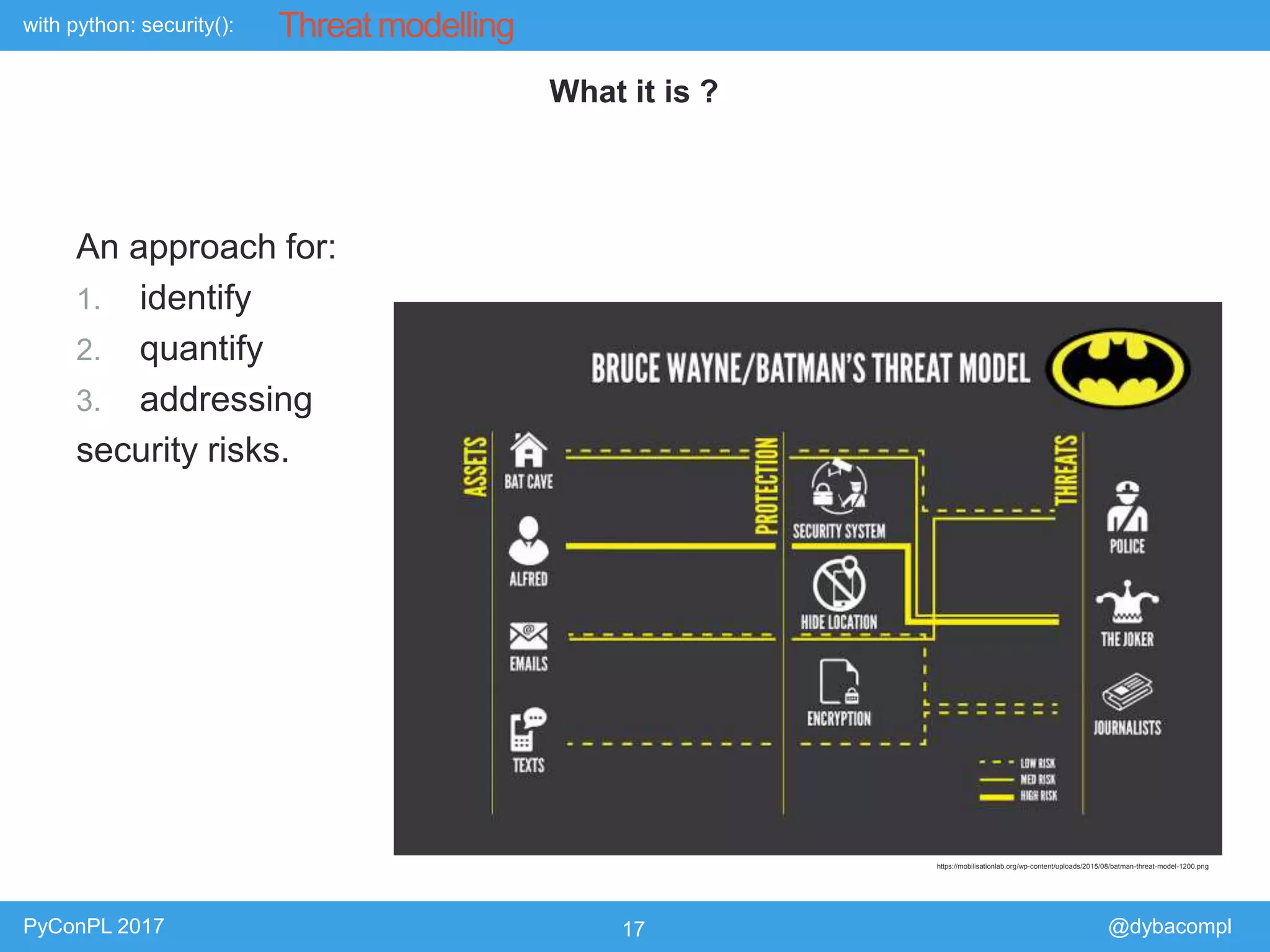
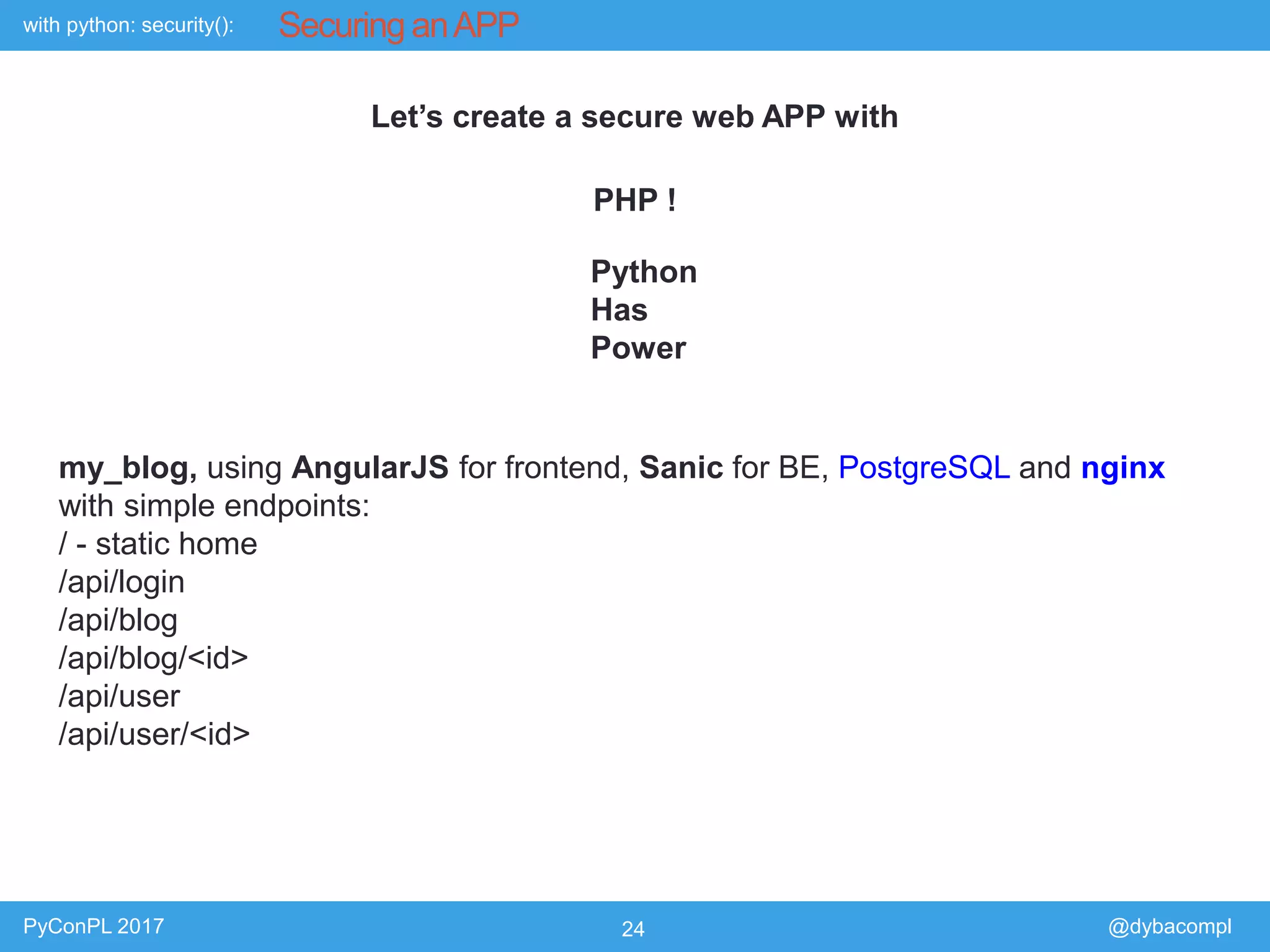
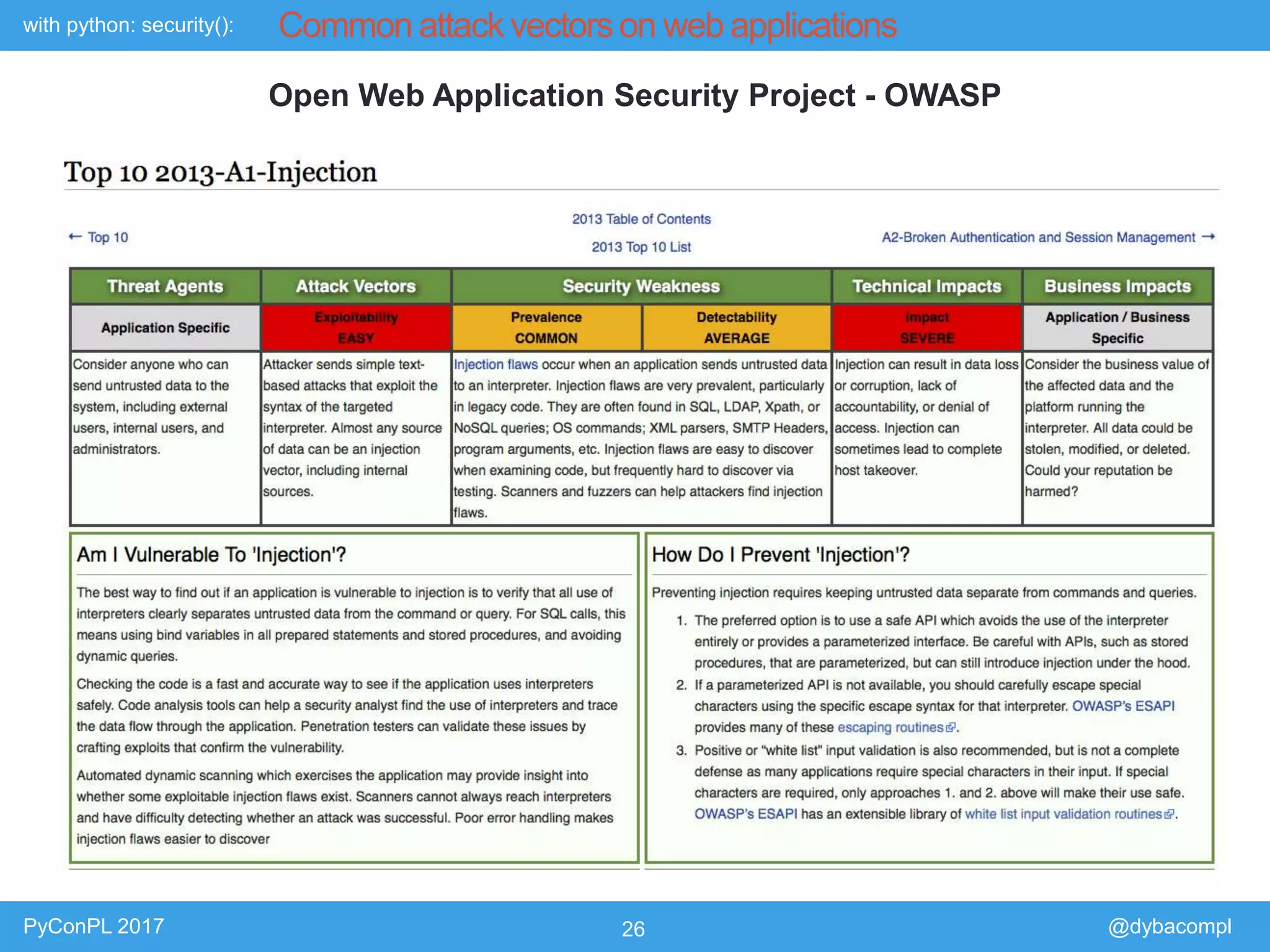
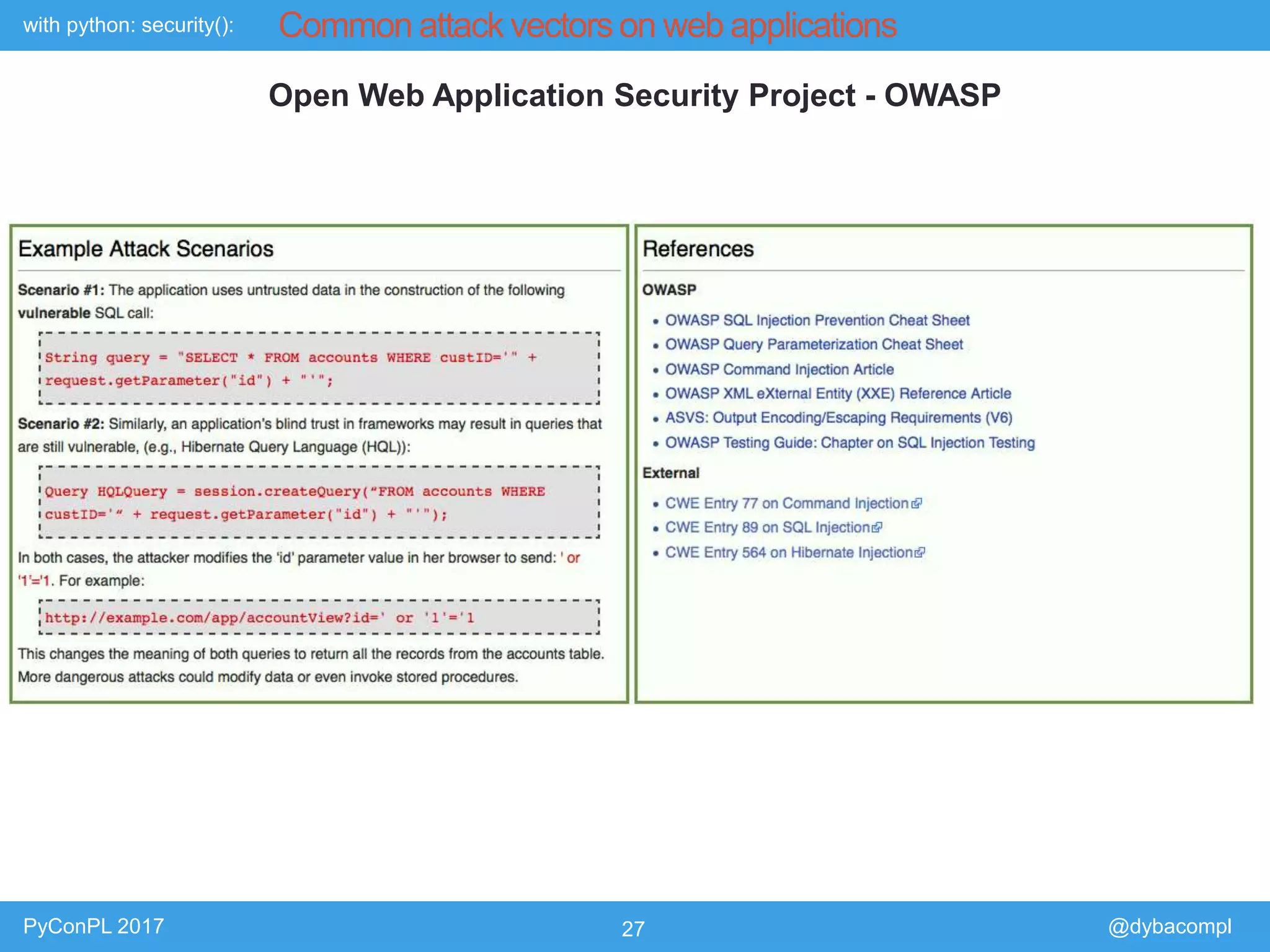
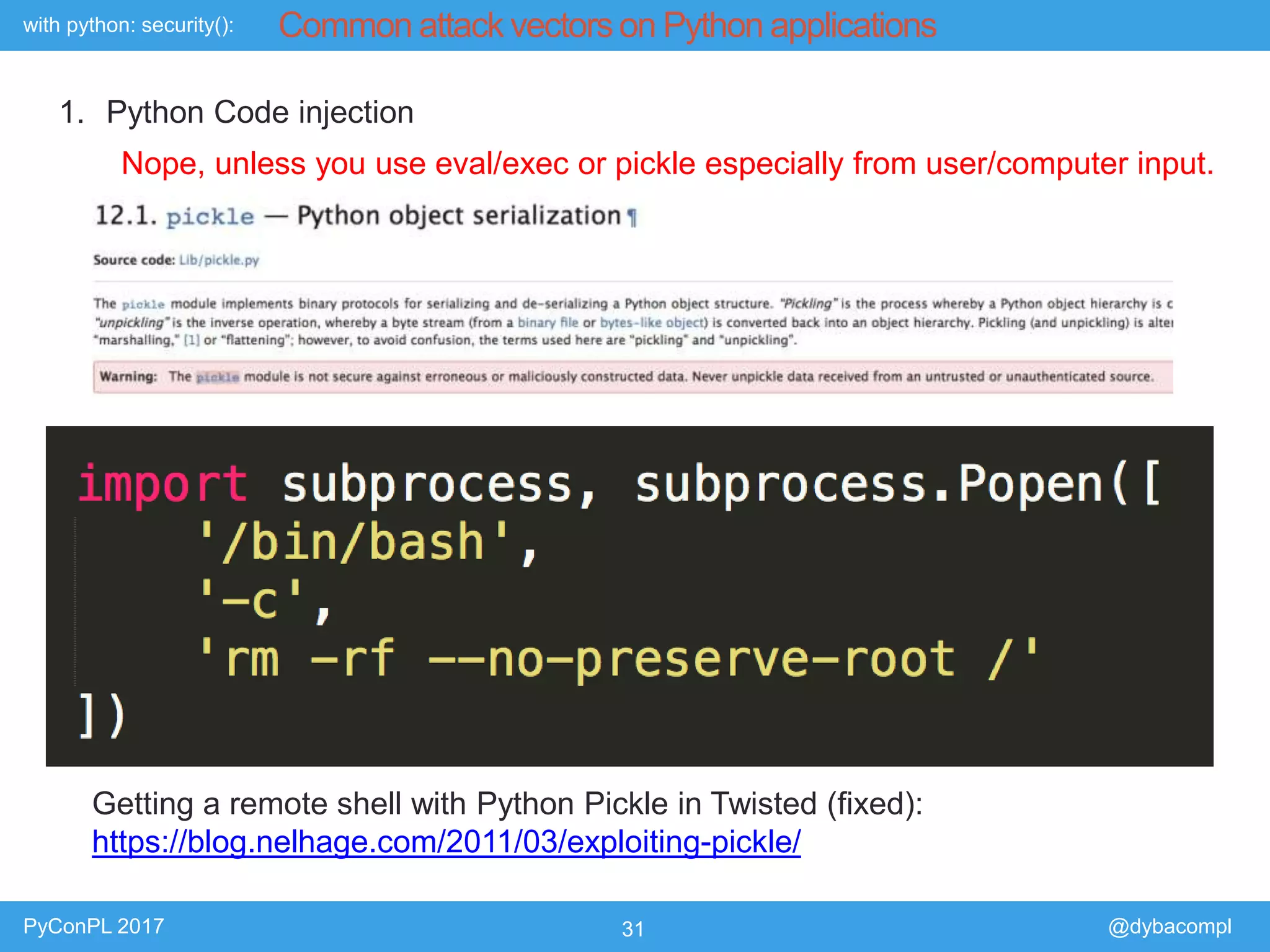
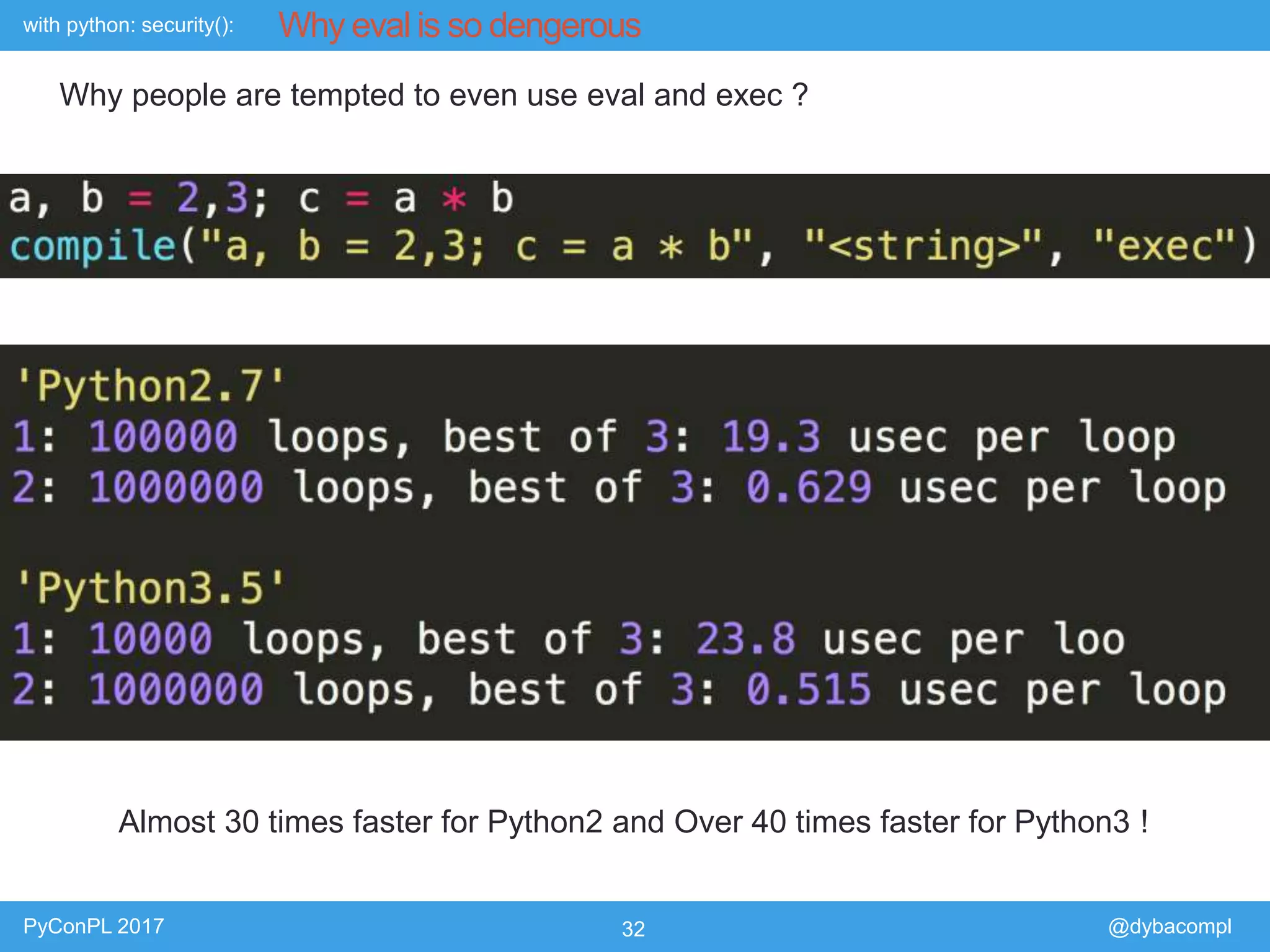
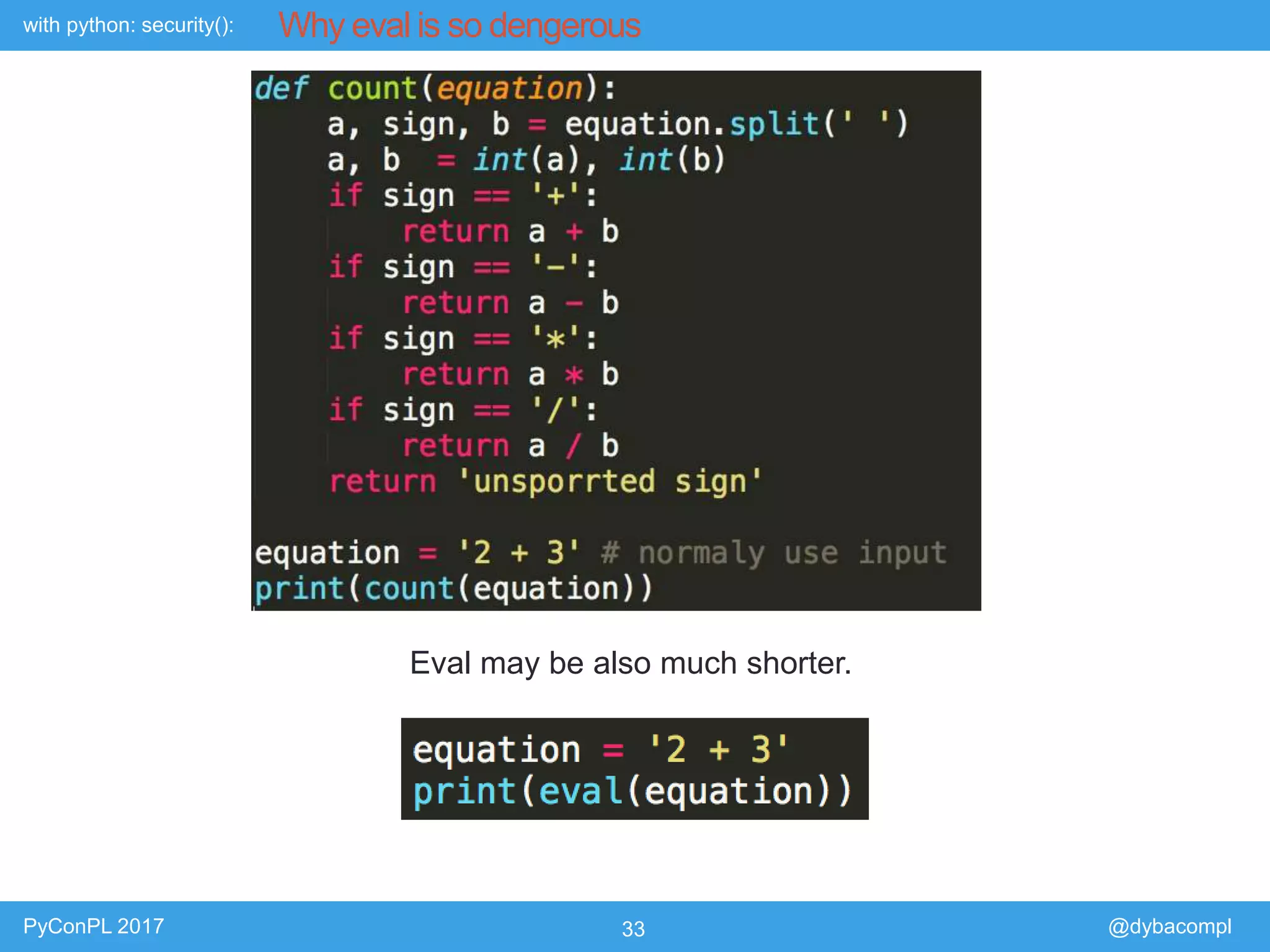
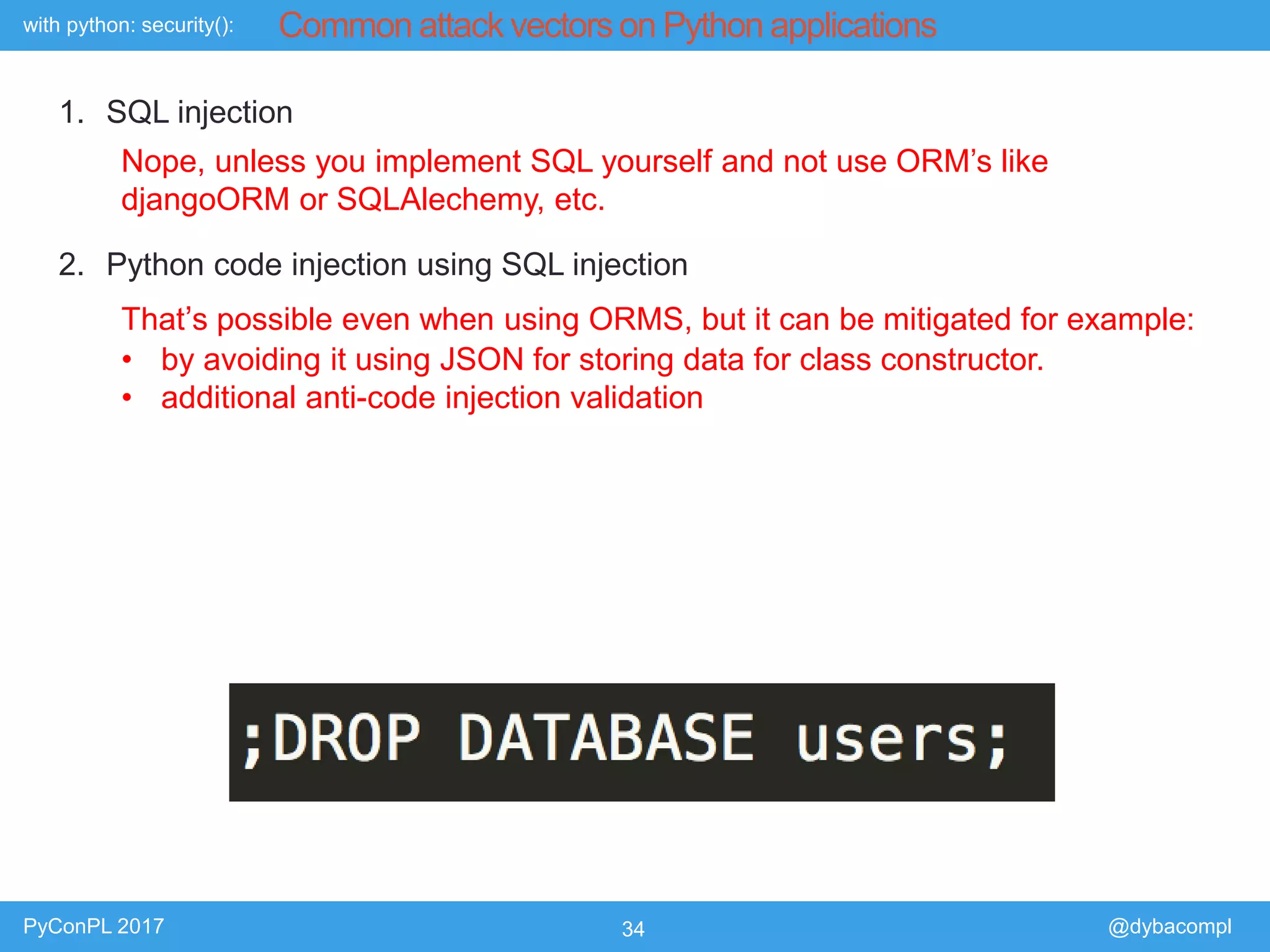
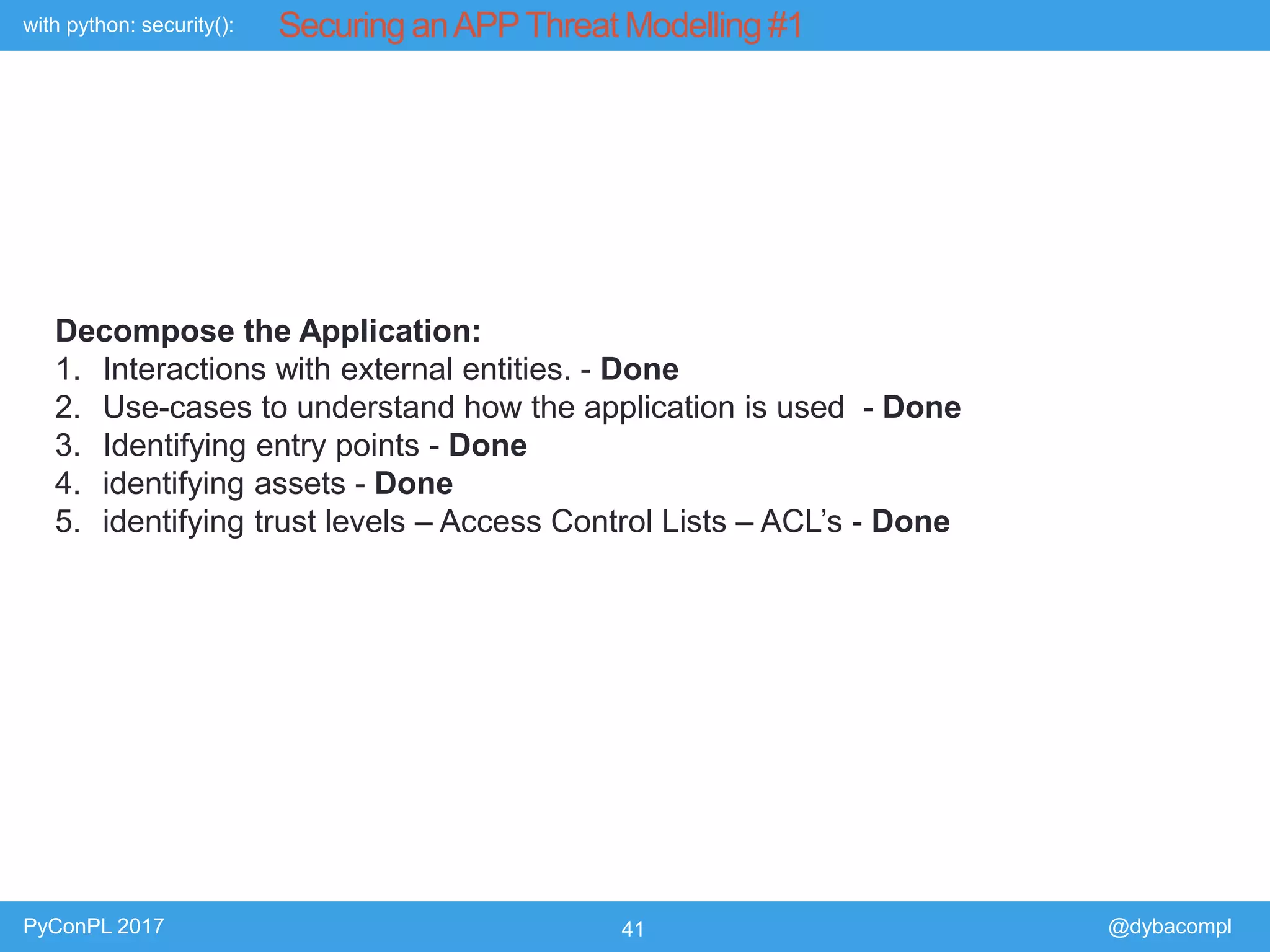
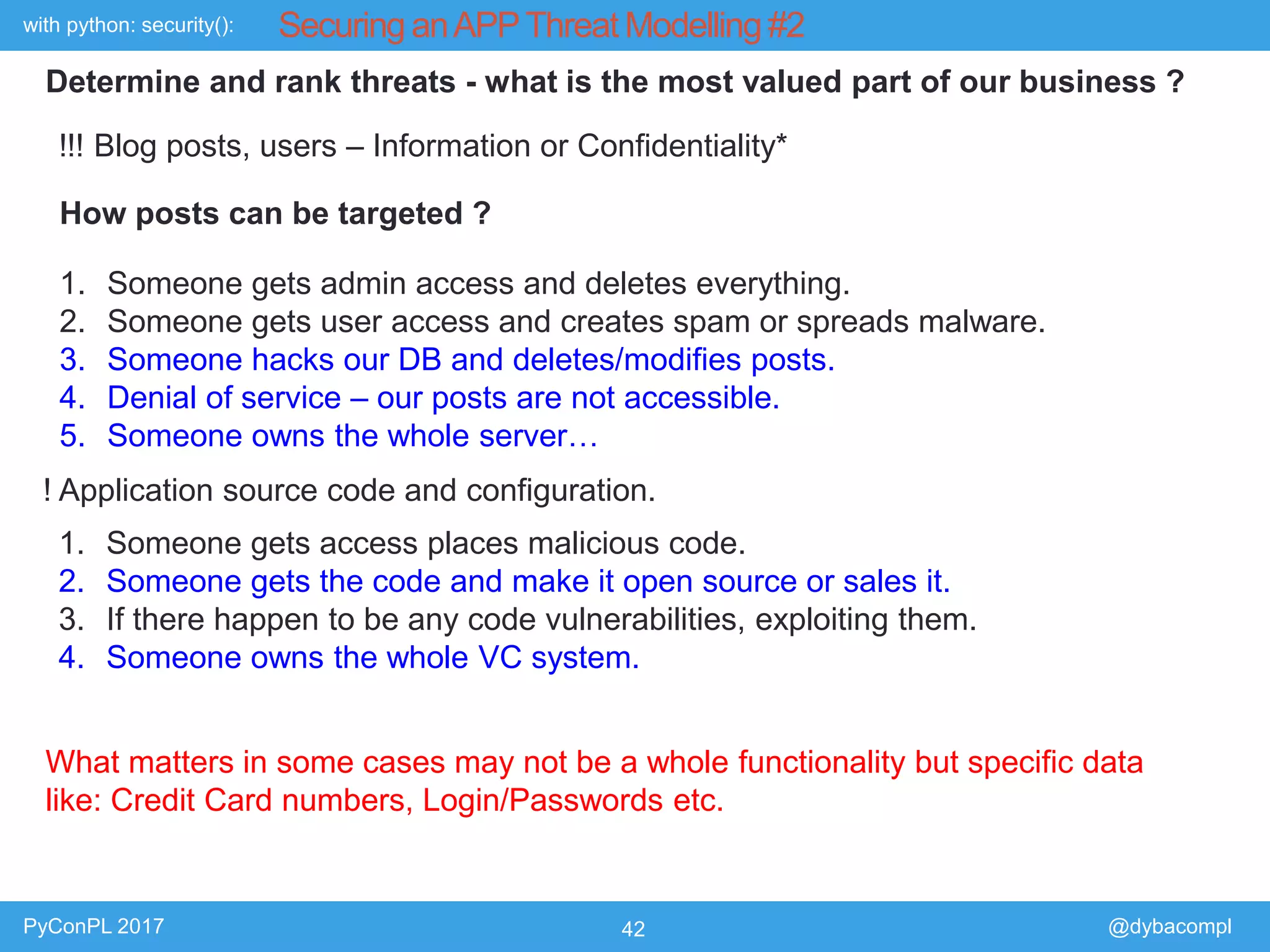
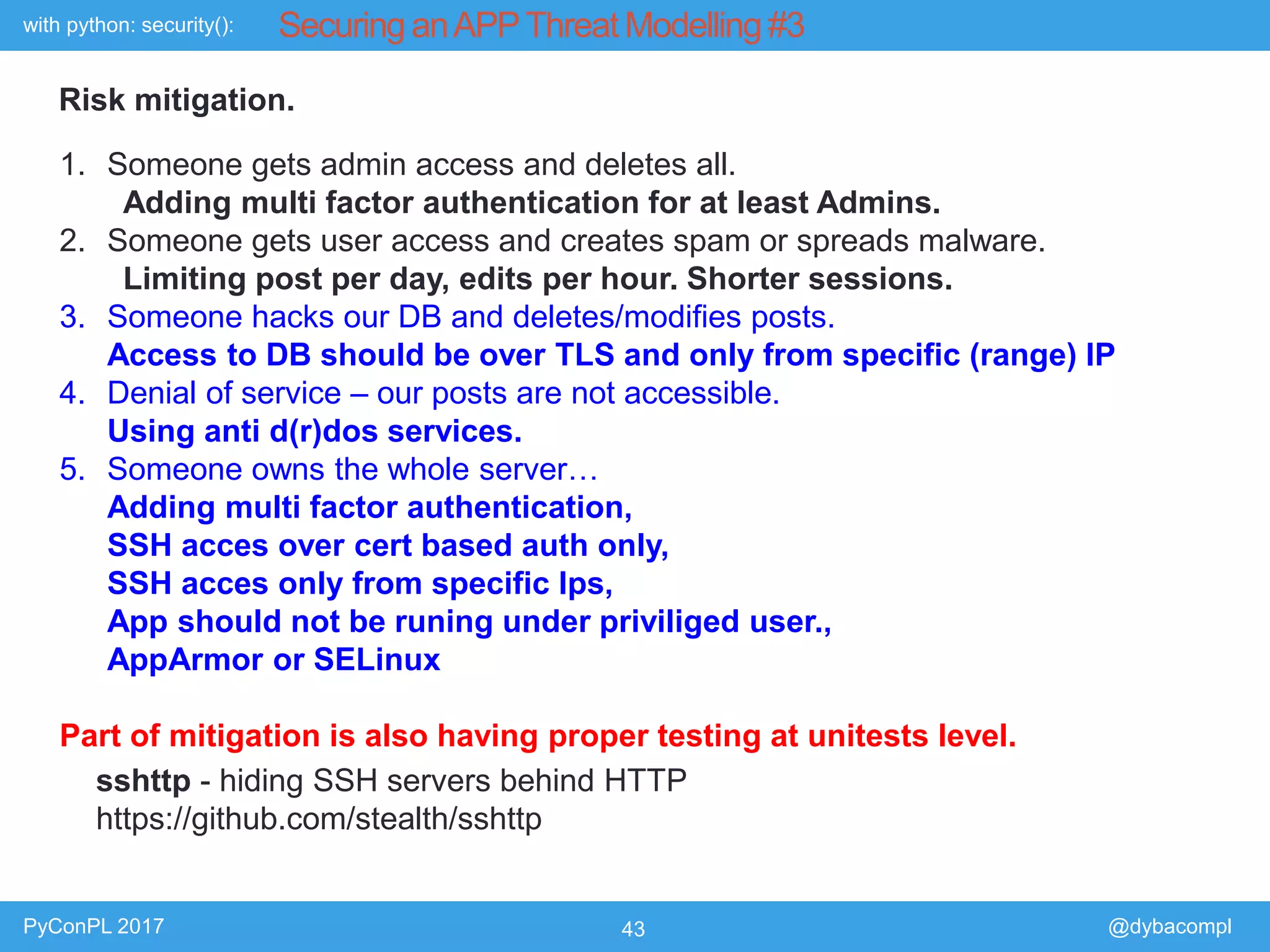
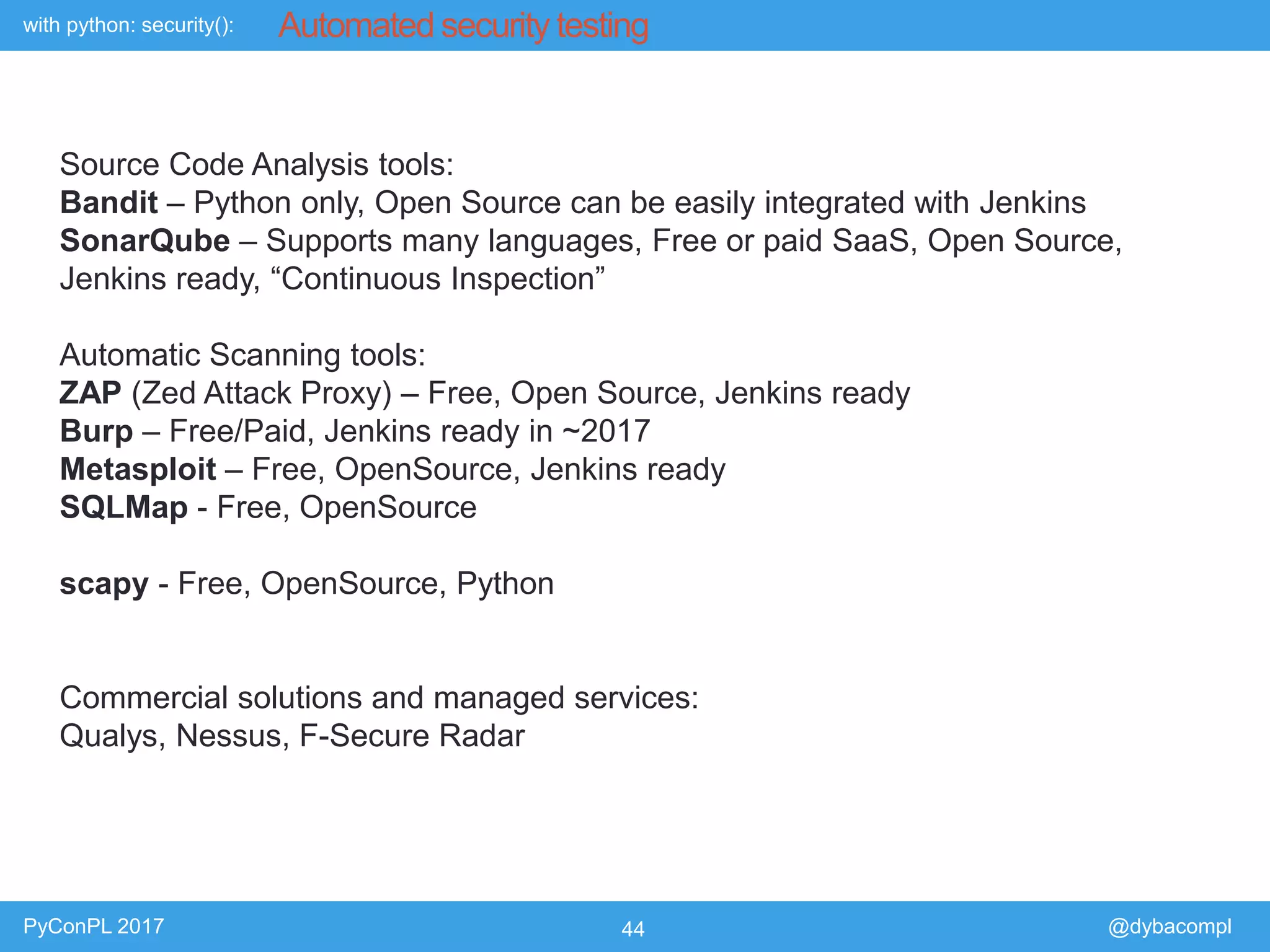
The document is a presentation by Piotr Dyba at PyConPL 2017 discussing cybersecurity from a developer's perspective, emphasizing the importance of cybersecurity awareness in organizations. It covers topics such as threat modeling, common attack vectors, and automated security testing, highlighting the need for proactive security measures in web applications and Python programs. The presentation also outlines various security frameworks and tools for identifying and mitigating vulnerabilities.