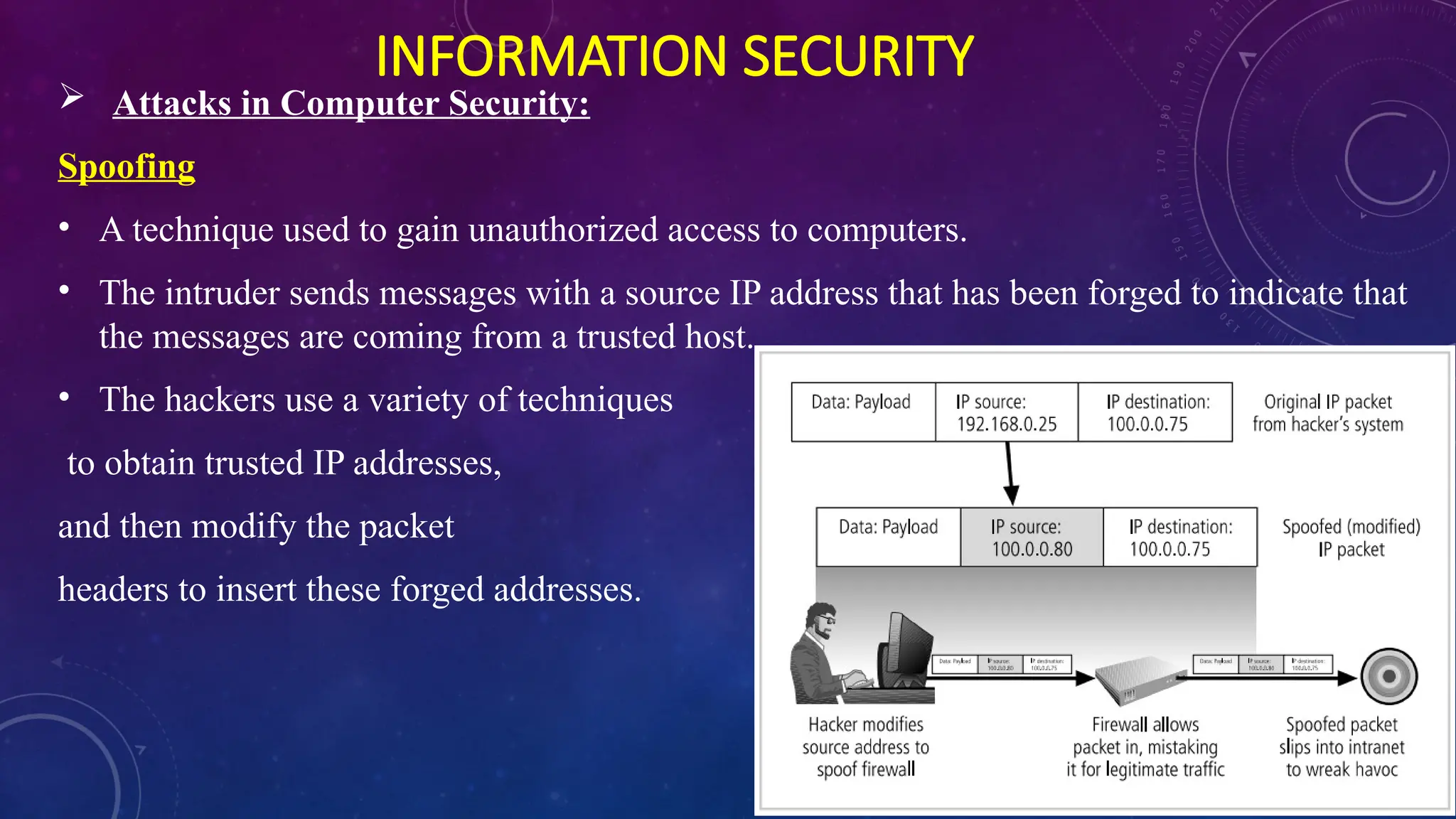
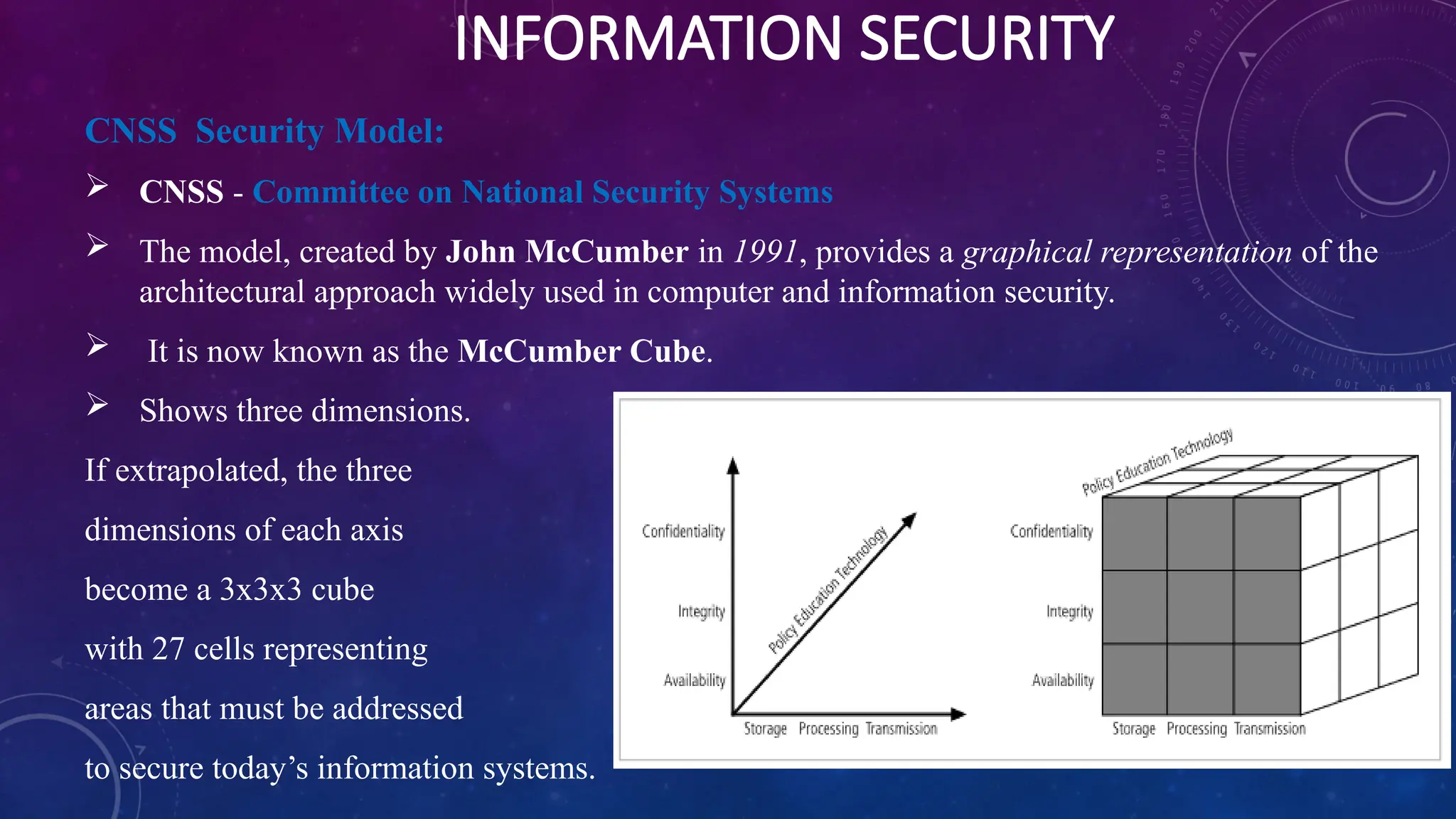
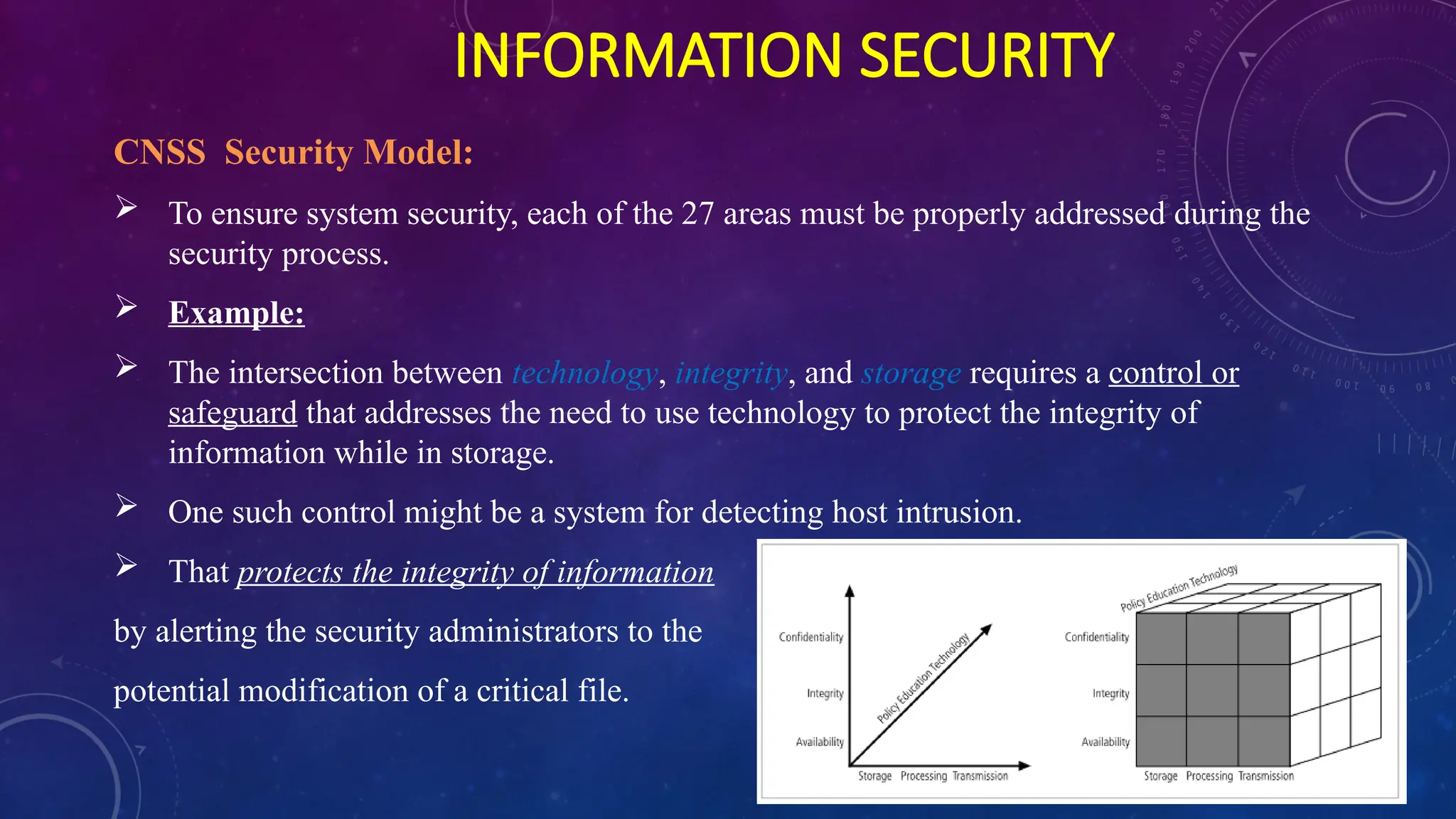
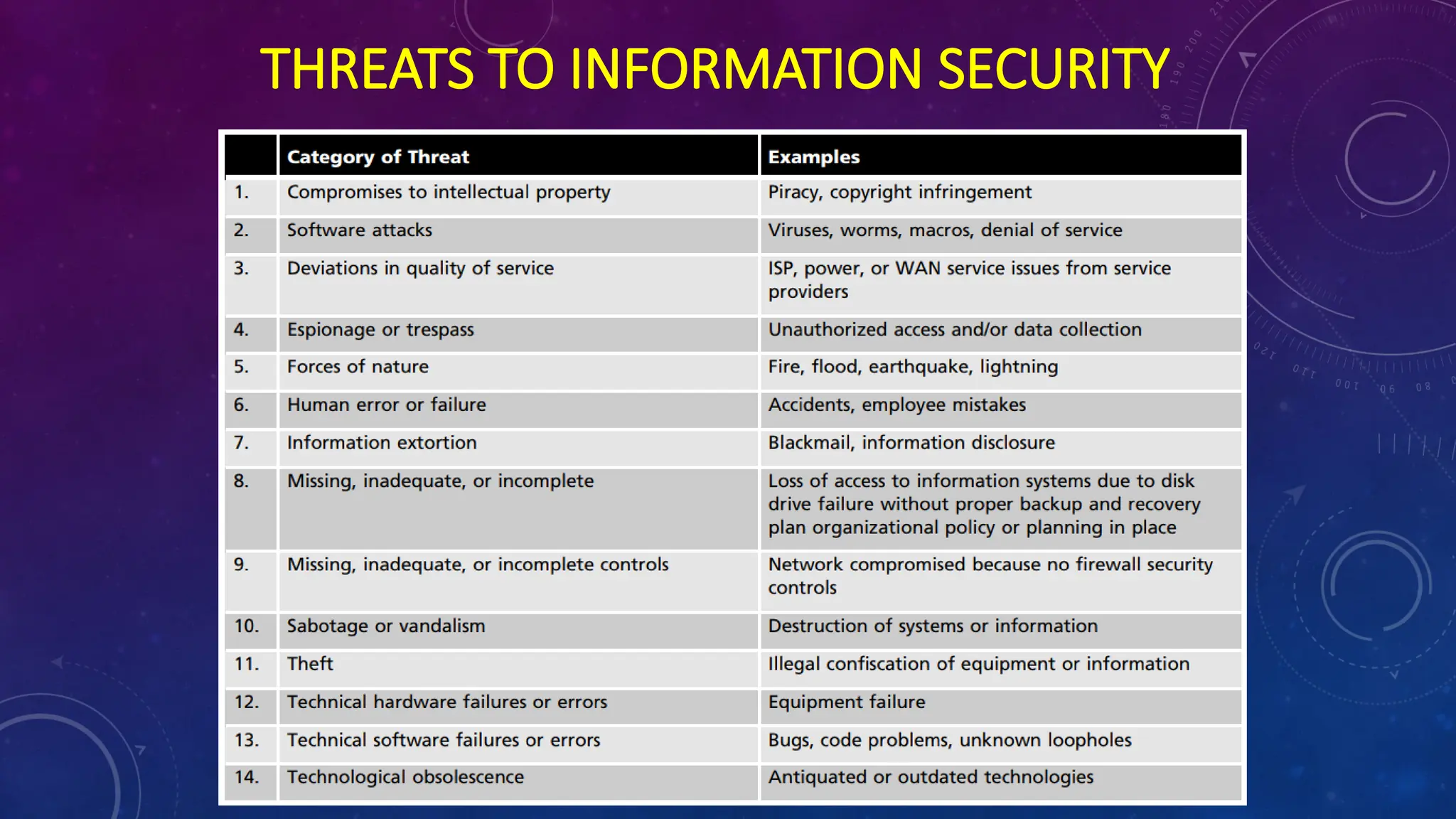
The document discusses information security in computers, detailing external and internal security measures, user authentication methods, and cryptography. It outlines various types of cyber attacks, including viruses, trojan horses, spyware, and denial-of-service attacks, along with prevention strategies such as strong passwords and antivirus software. Additionally, it introduces the CNSS security model and emphasizes the need for an integrated approach to protect information systems.