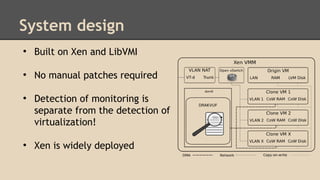
The document describes DRAKVUF, a dynamic malware analysis system that aims to improve scalability, fidelity, and stealthiness. It uses Xen virtualization and memory monitoring techniques like EPT to analyze malware behavior in a monitored virtual environment without the malware's knowledge. An evaluation analyzed 1000 malware samples, found key data only existed in memory, and showed throughput could be improved with memory deduplication. The system helps address issues with analyzing large malware sets but challenges remain like handling stalled code.