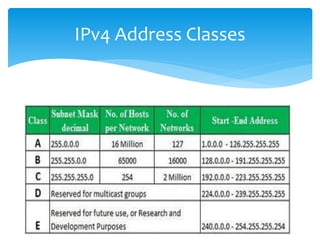
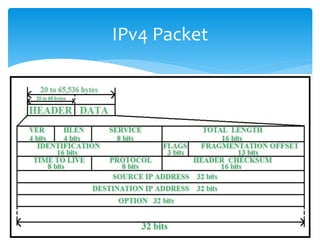
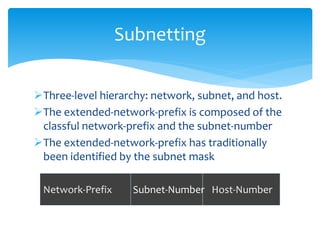
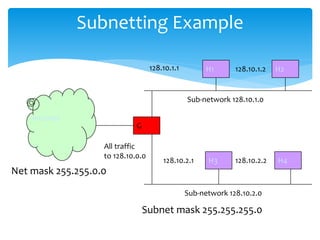
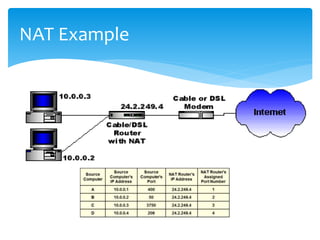
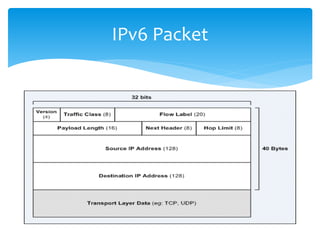
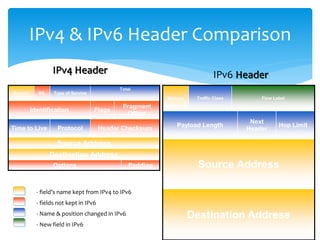
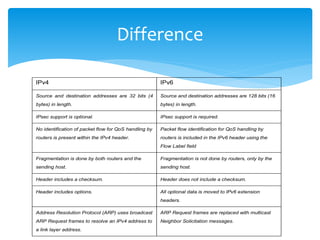
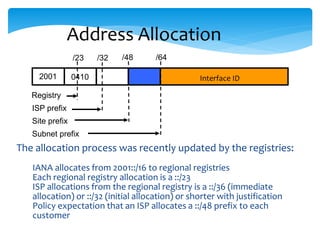
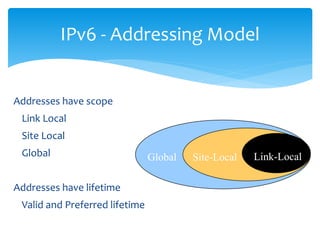
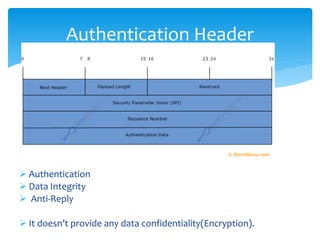
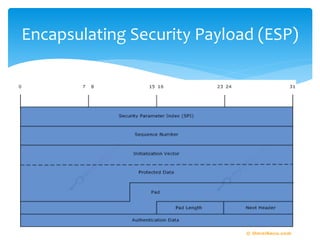
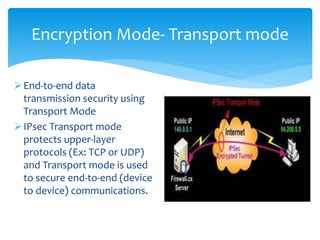
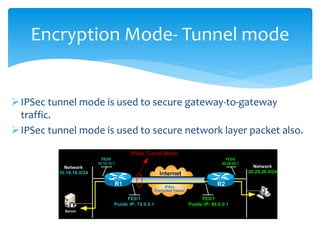
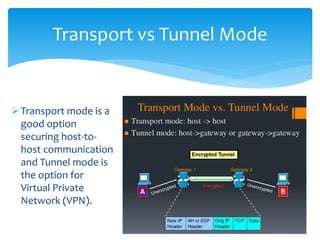
The document discusses IPv6, the successor to IPv4, highlighting its features such as a larger address space of 128 bits, enhanced security, and improved network management. It compares IPv4 and IPv6 in terms of packet structure, address allocation, and routing efficiency while also detailing the benefits and challenges of transitioning from IPv4 to IPv6. Additionally, it mentions the initiatives taken in India for IPv6 deployment and education.