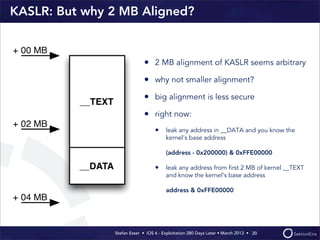
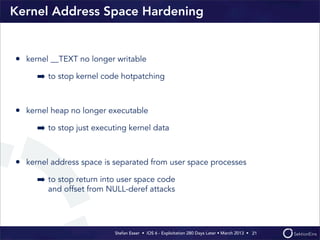
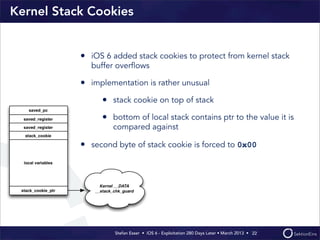
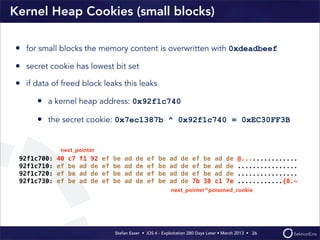
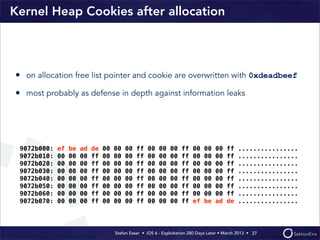
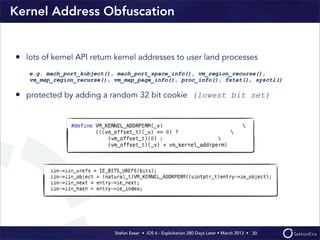
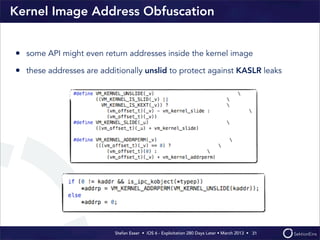
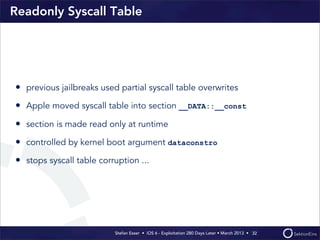
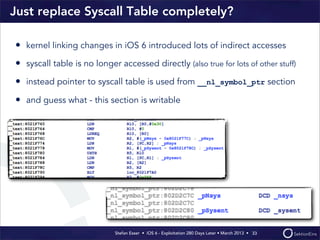
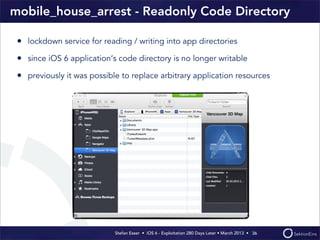
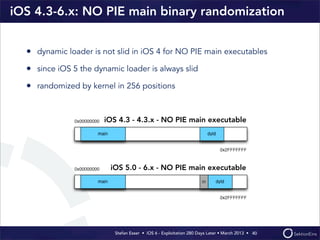
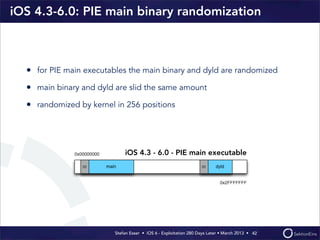
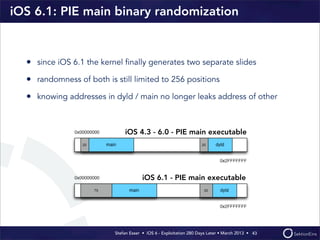
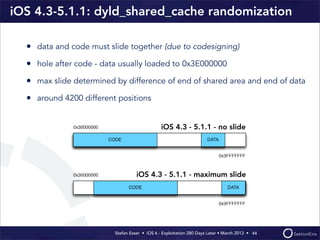
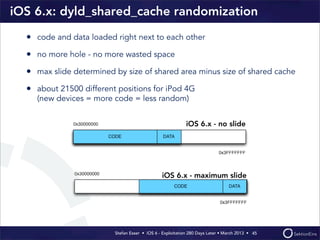
This document discusses the timeline of iOS security from 2012-2013. It begins with Stefan Esser's talk at CanSecWest 2012 about iOS 5 exploitation. It then discusses the release of iOS 6 in September 2012 and the subsequent jailbreak within a day. The document outlines various talks and research related to analyzing the security of iOS 6. It concludes by discussing new security features introduced in iOS 6 like KASLR and kernel stack and heap cookies.