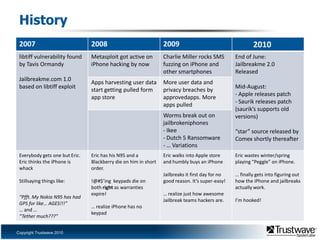
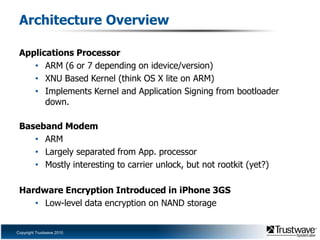
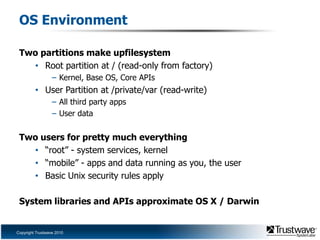
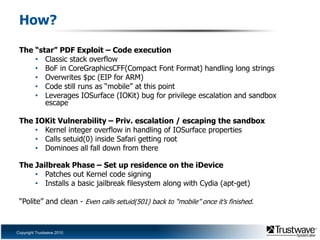
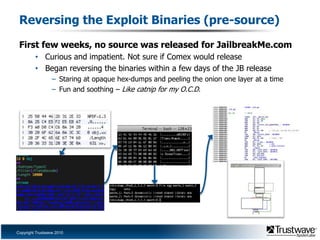
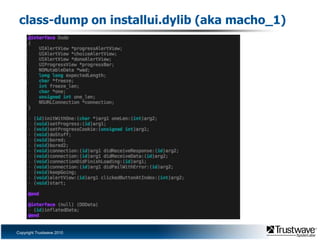
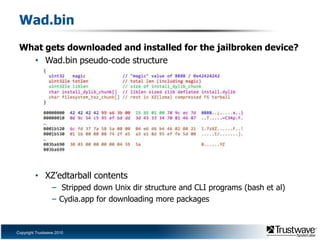
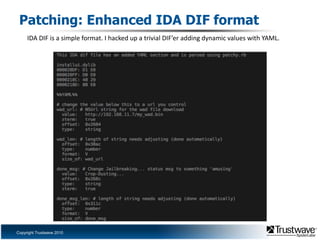
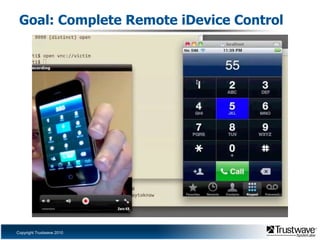
This document discusses a proof of concept iPhone rootkit developed by reverse engineering the JailbreakMe exploit and jailbreak tools. It describes patching the tools to remove security checks and pop-ups, and preparing a custom "wad.bin" filesystem containing backdoored system utilities and apps to enable remote access and control of an infected device without the user's knowledge. A demo is proposed using a Ruby Sinatra server to serve the exploit to a vanilla iOS device and install the rootkit via the existing JailbreakMe vulnerability. The rootkit aims to remain hidden using techniques like disguising process names and removing GUI indicators of running services.
















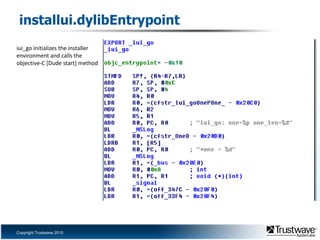






![installui.dylibEntrypointiui_go initializes the installer environment and calls the objective-C [Dude start] method](https://image.slidesharecdn.com/trimiphonerootkitekoparty2010-100927194201-phpapp02/85/EkoParty-2010-iPhone-Rootkit-There-s-an-App-for-that-34-320.jpg)


