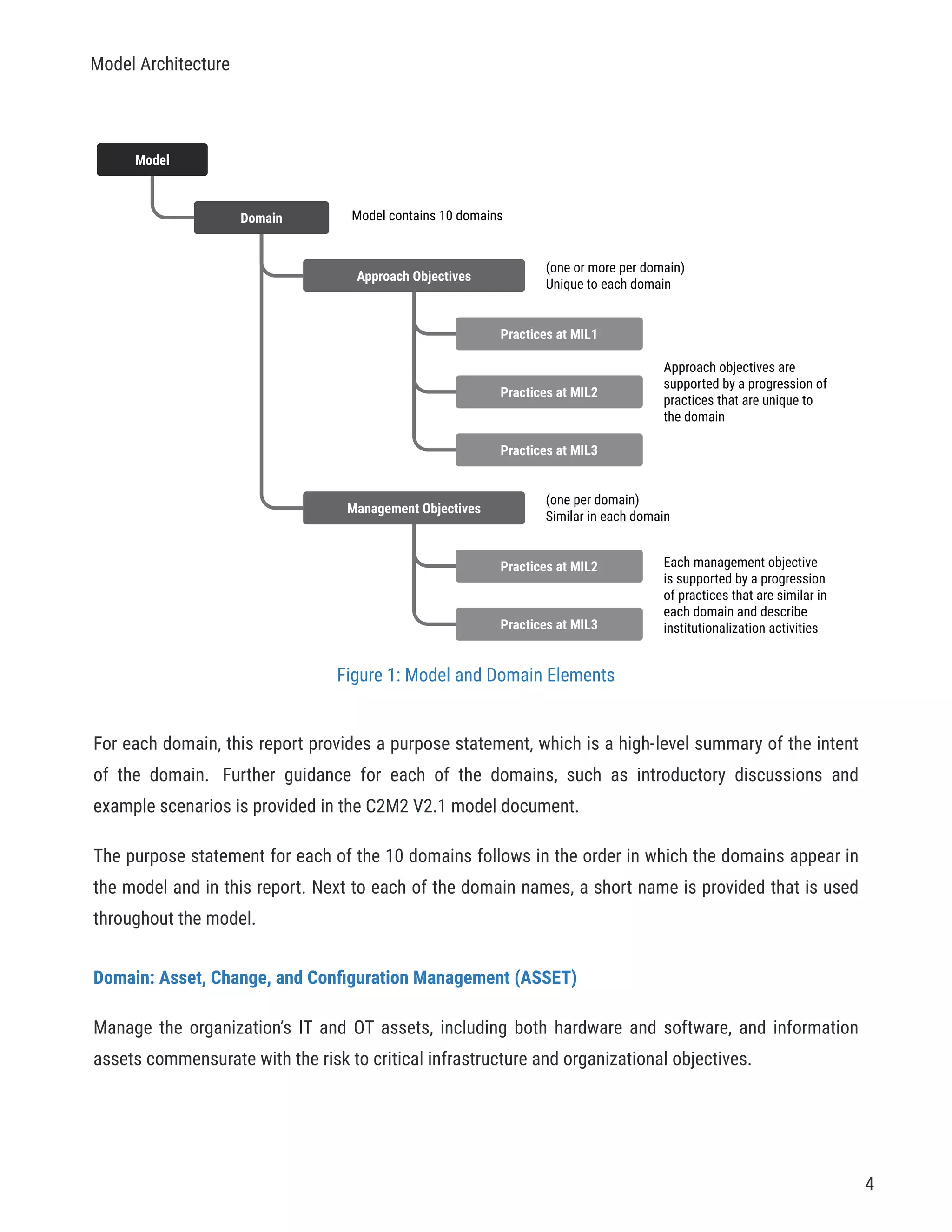
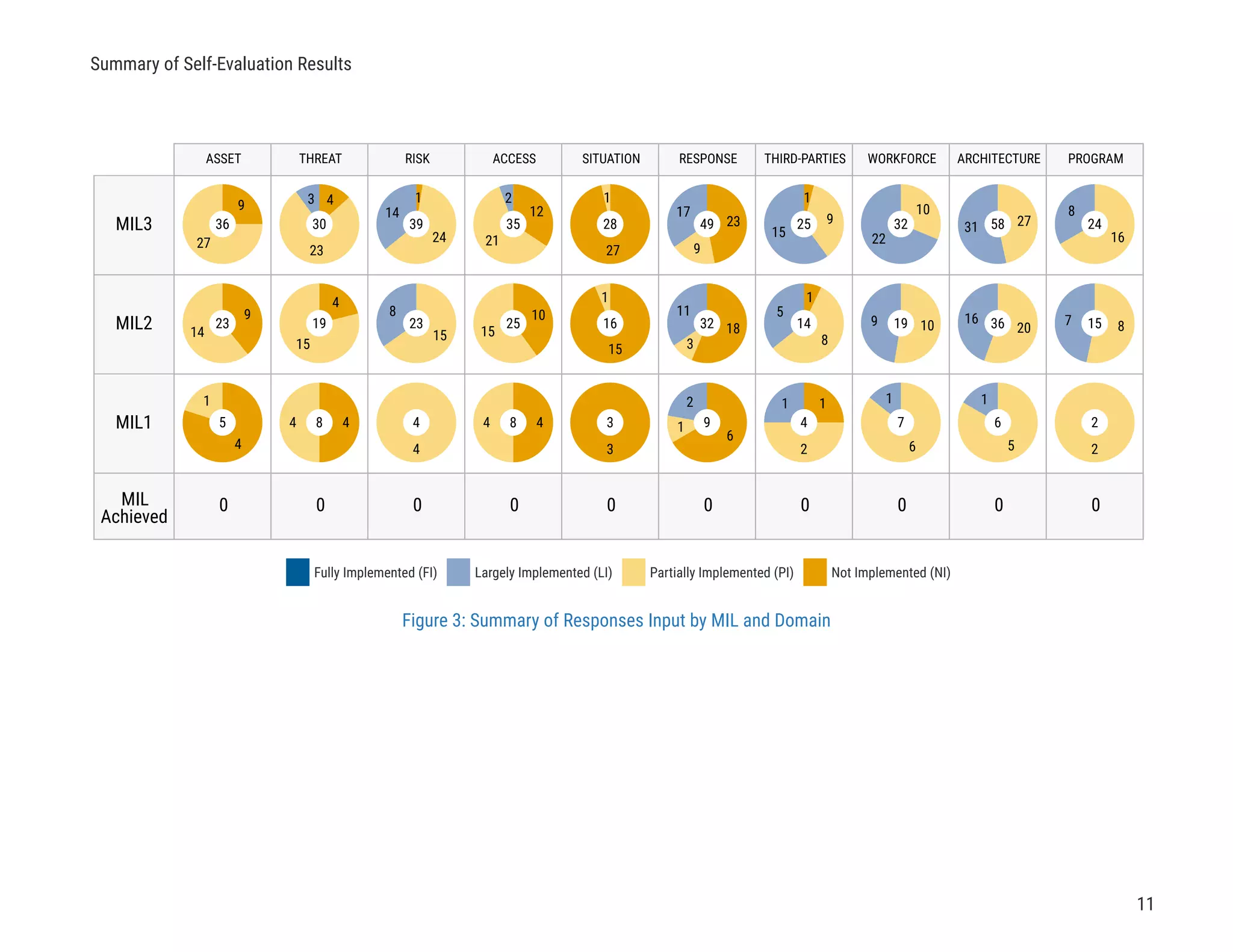
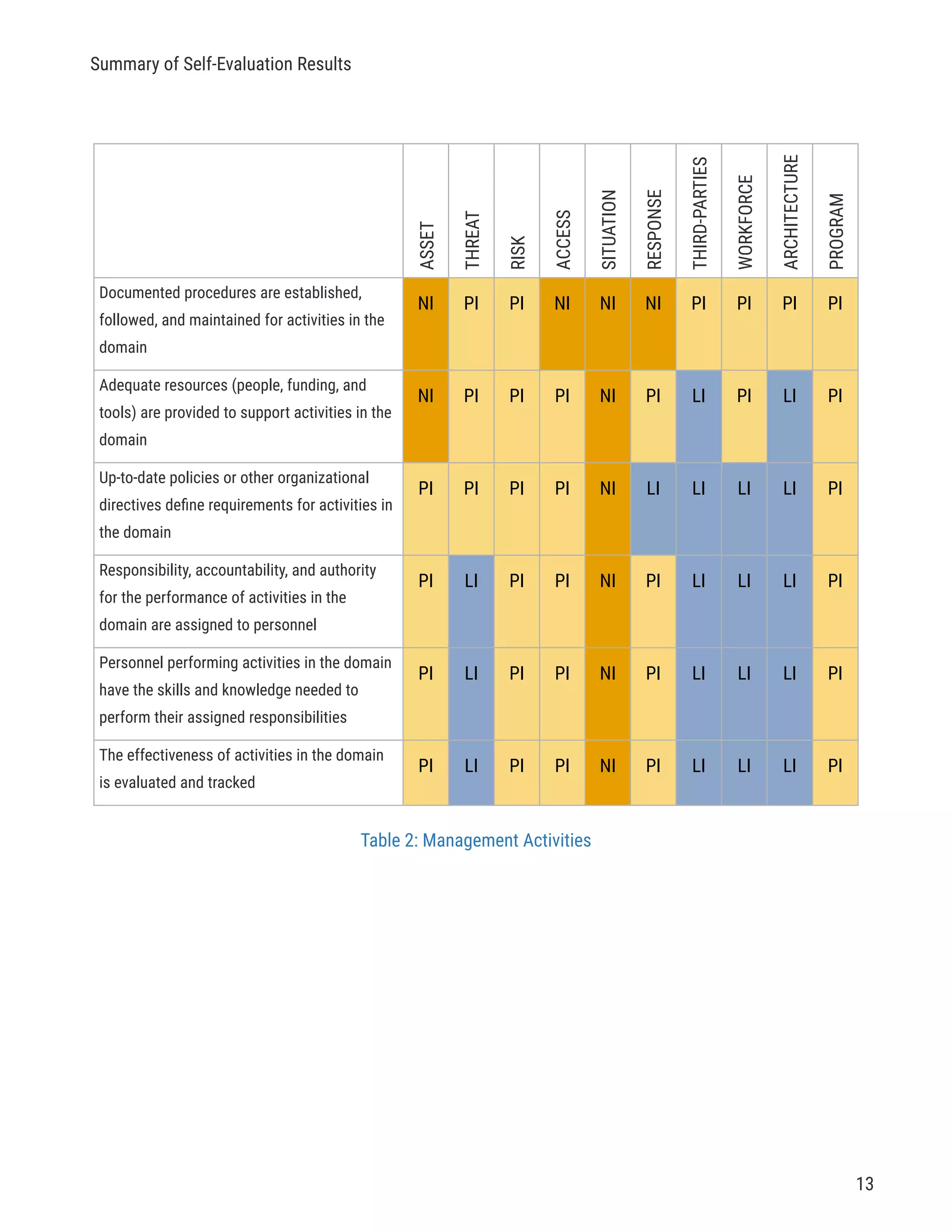
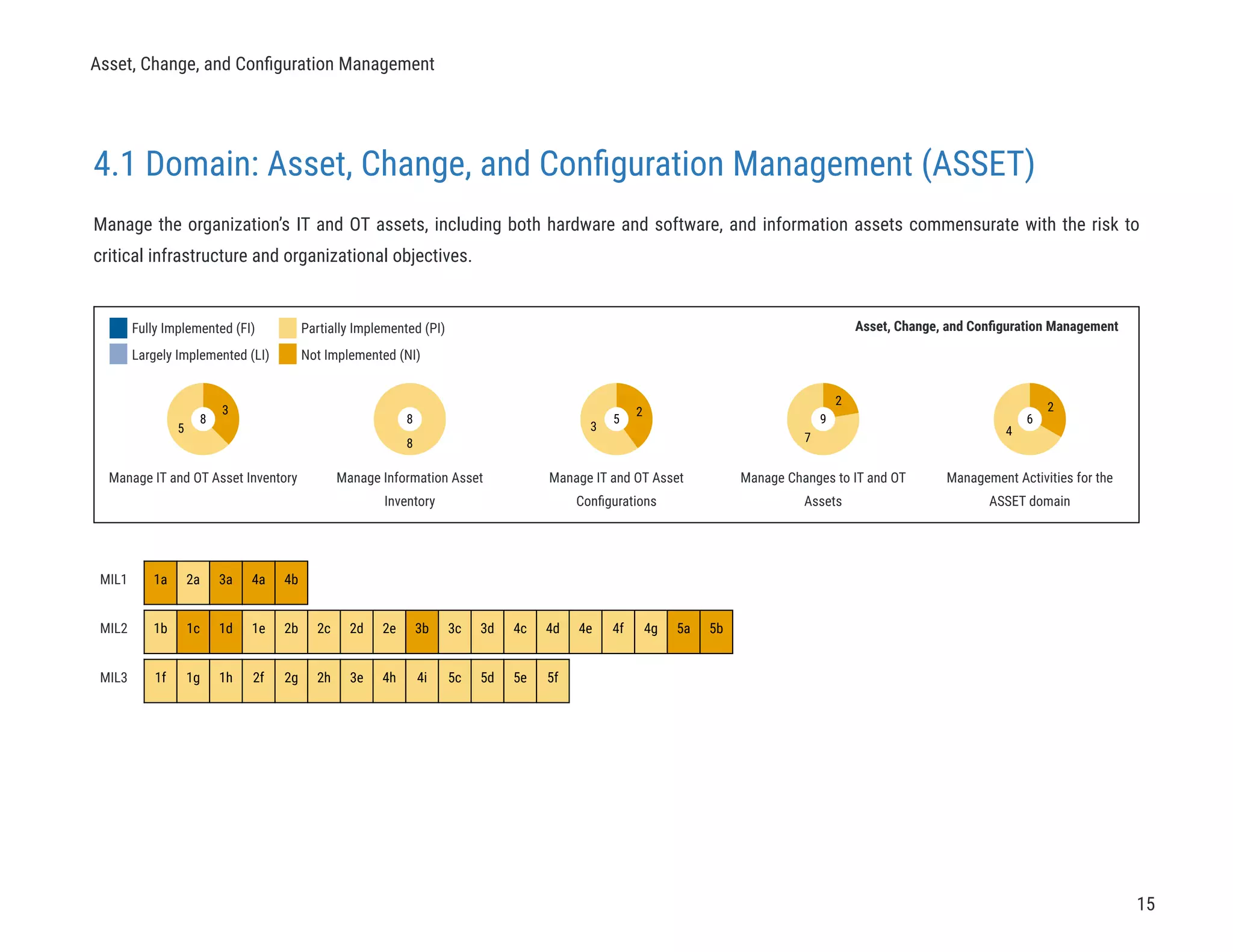
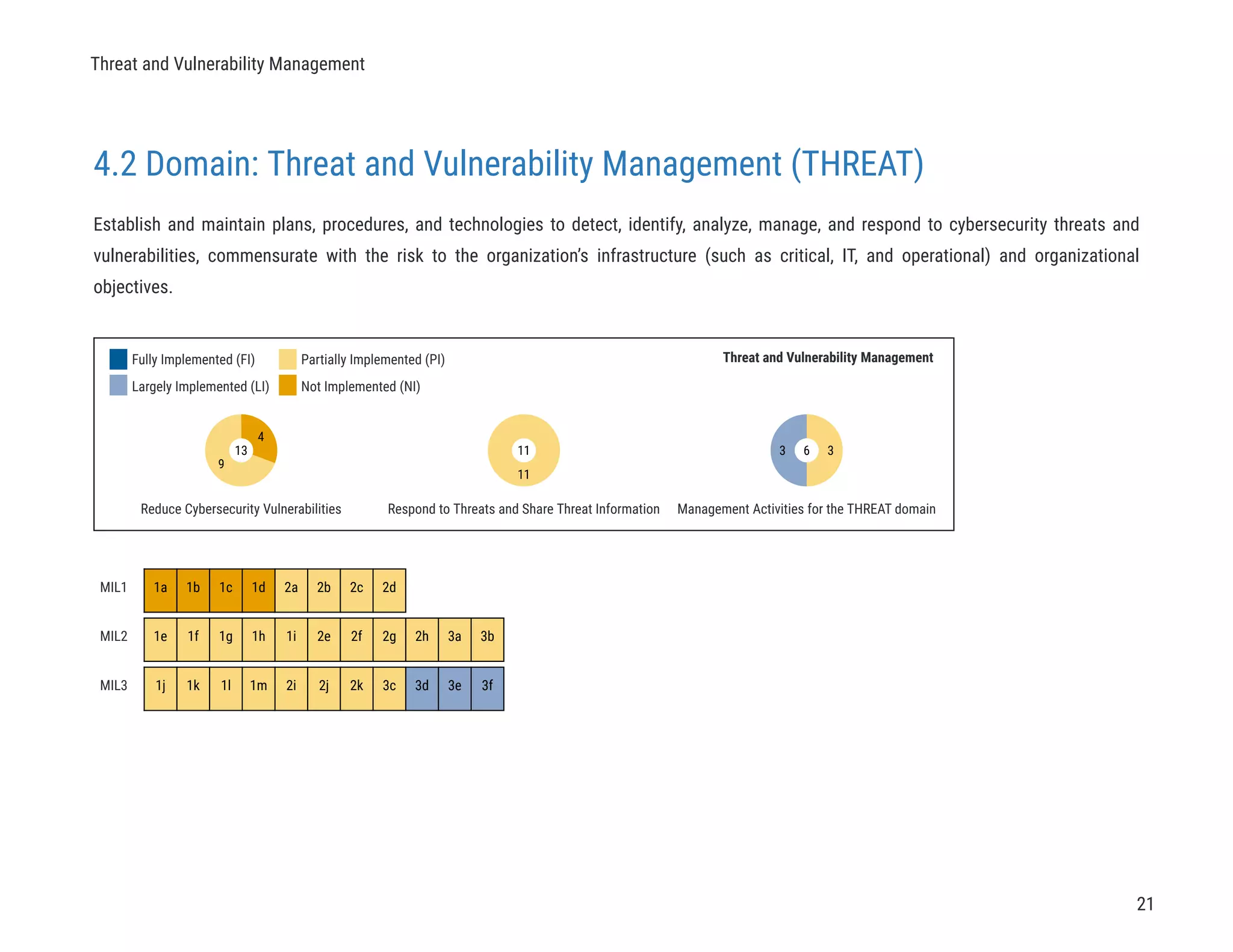
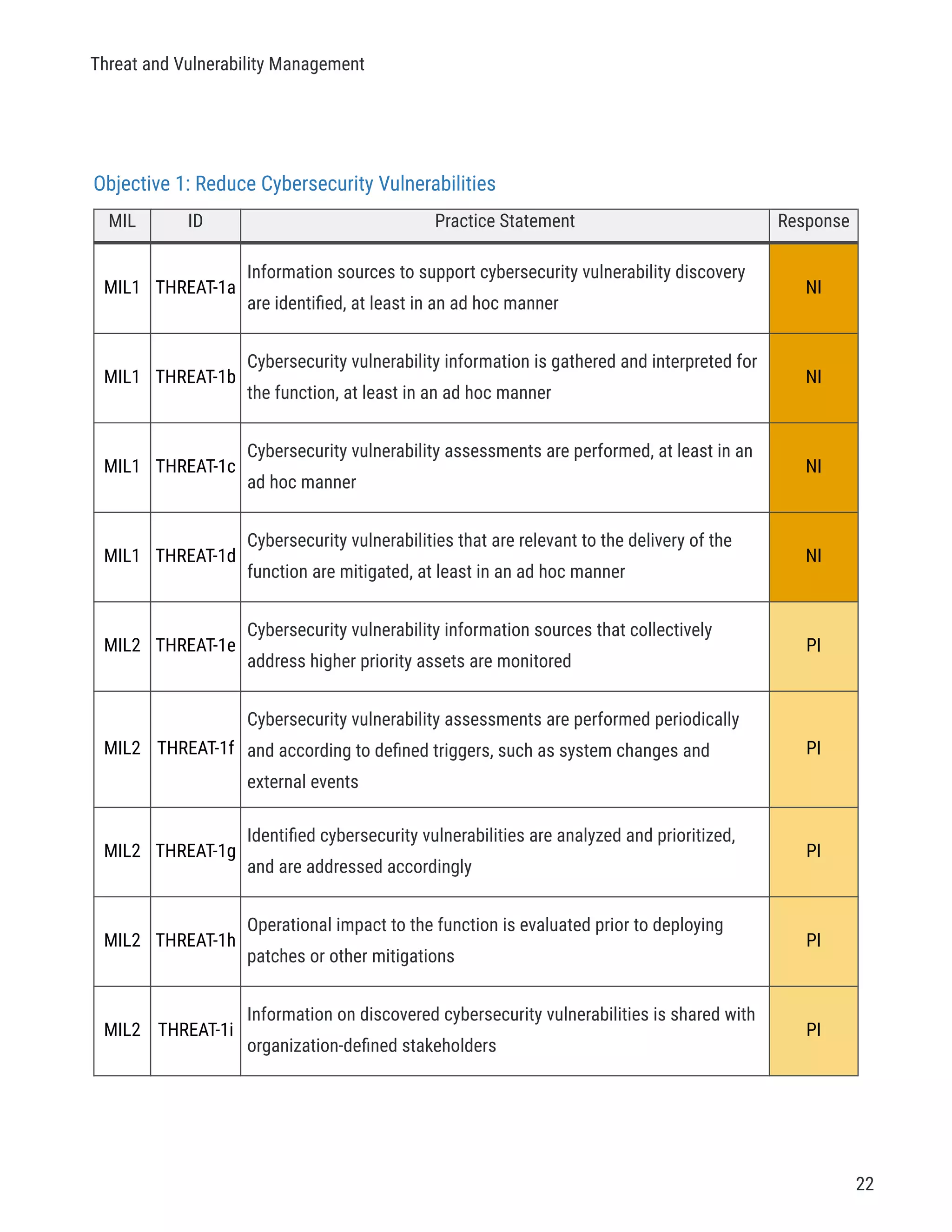
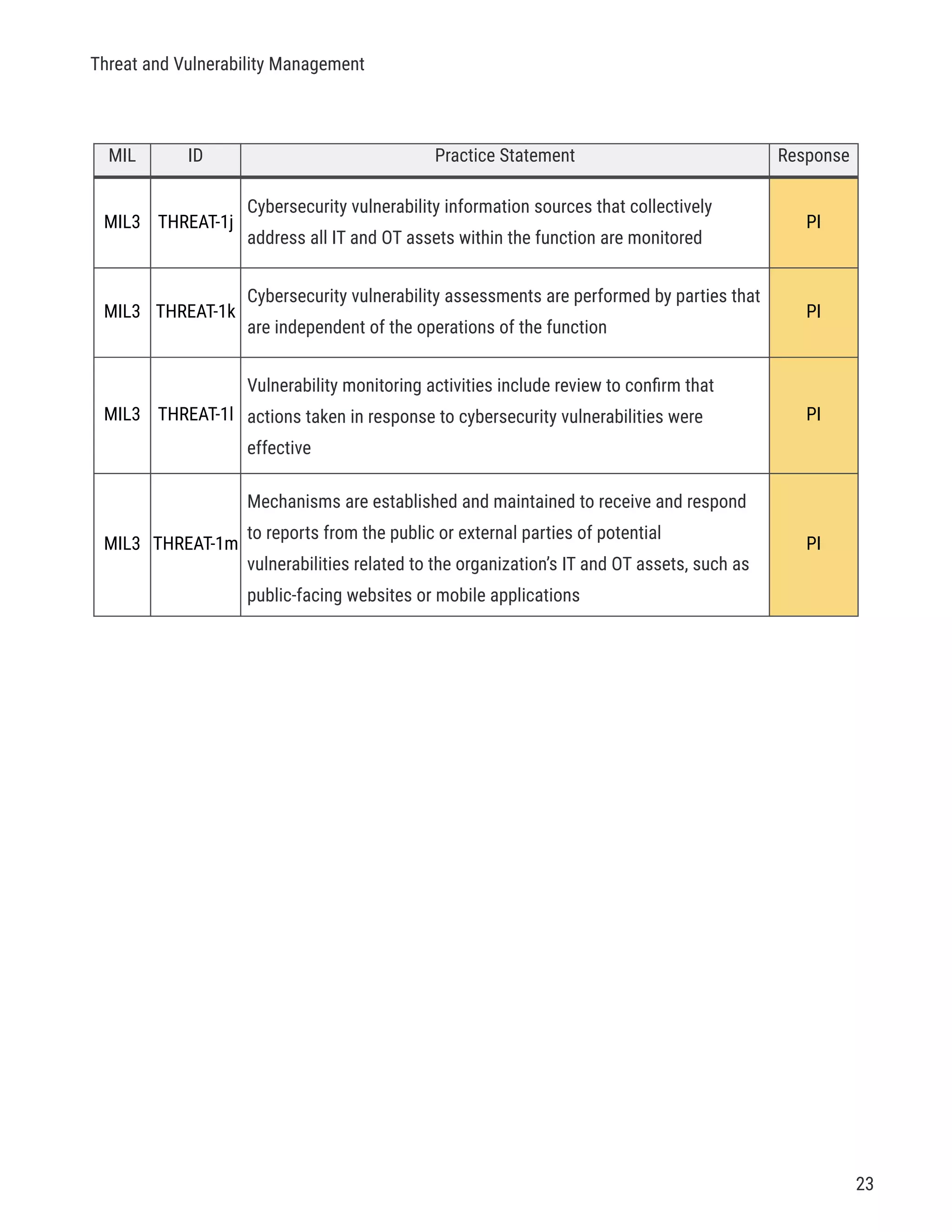
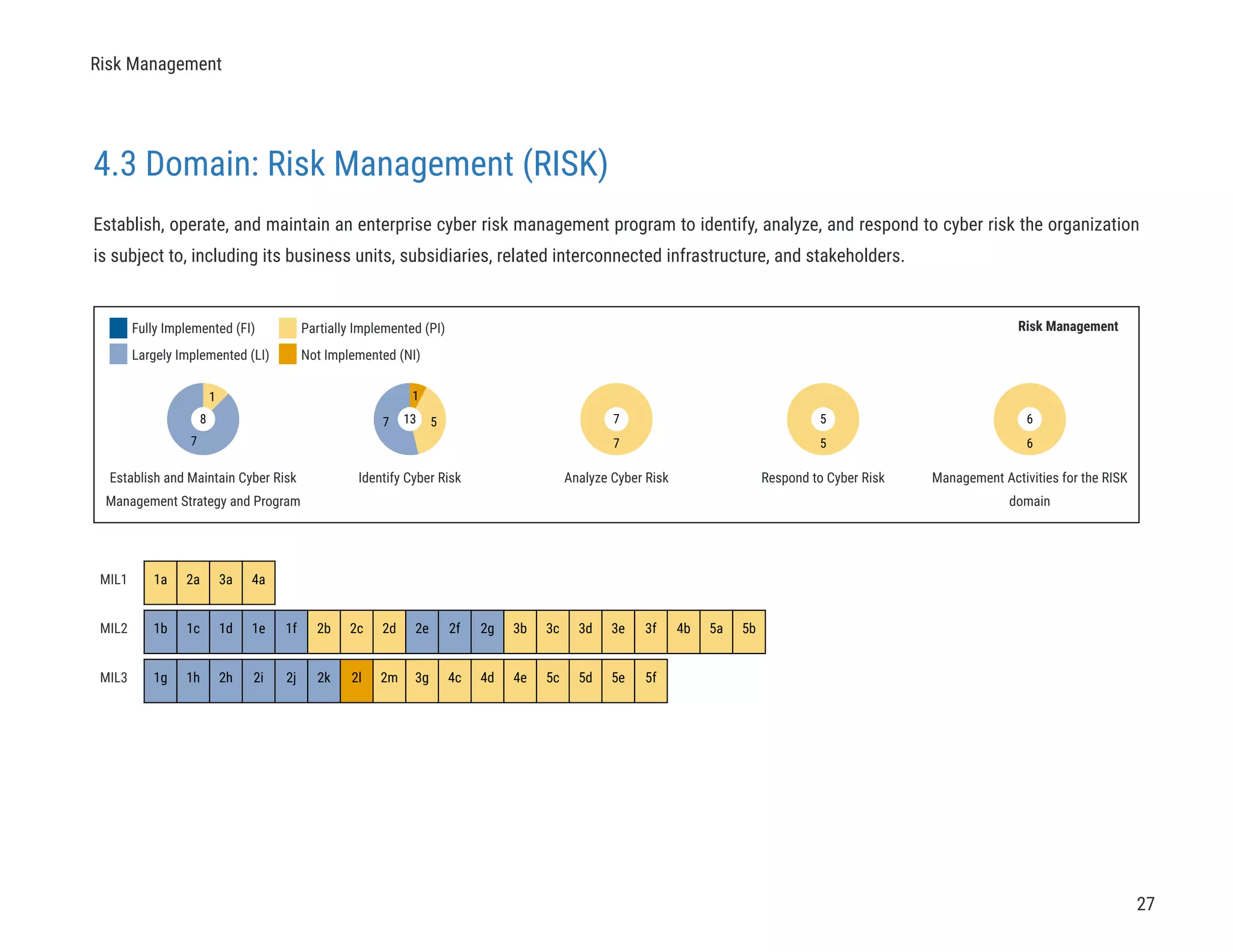
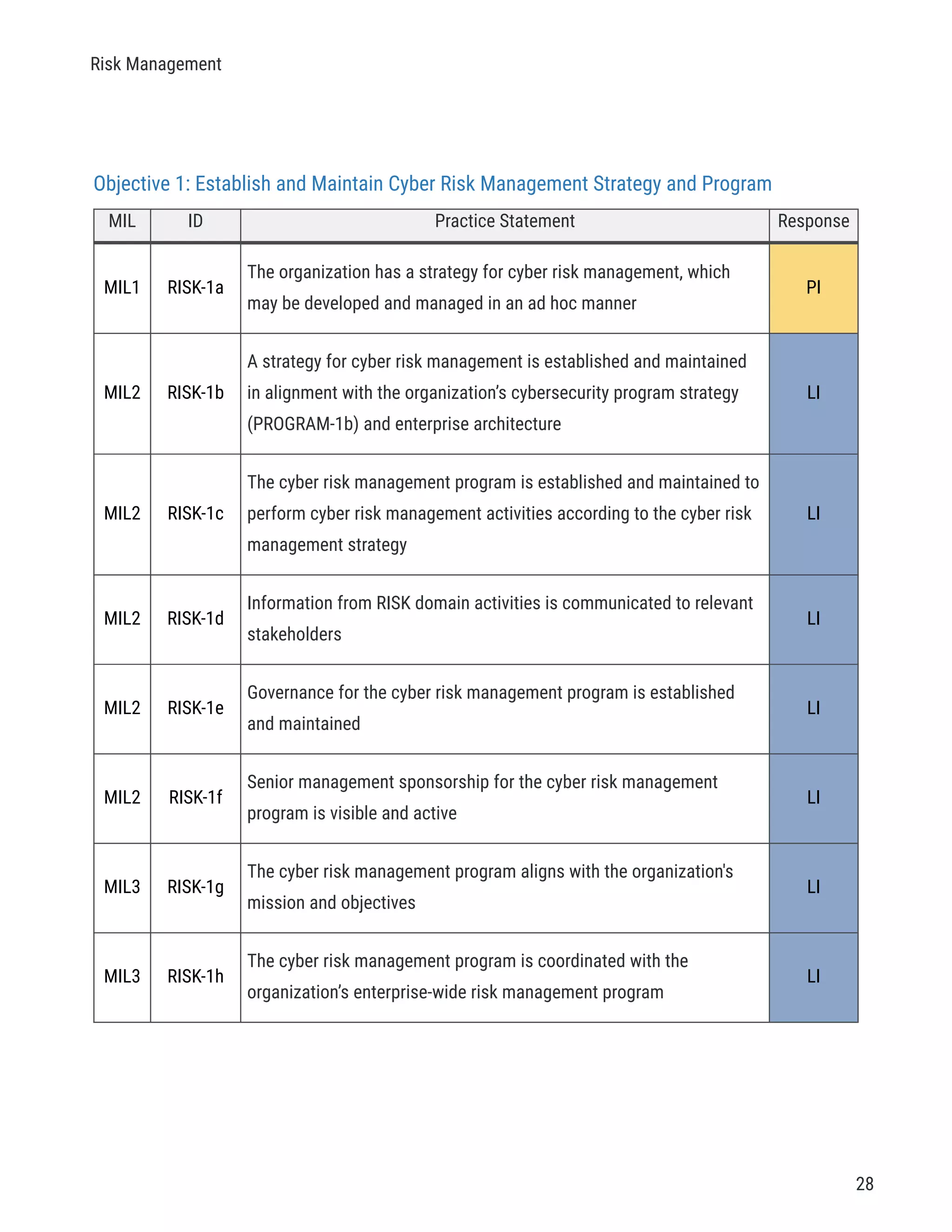
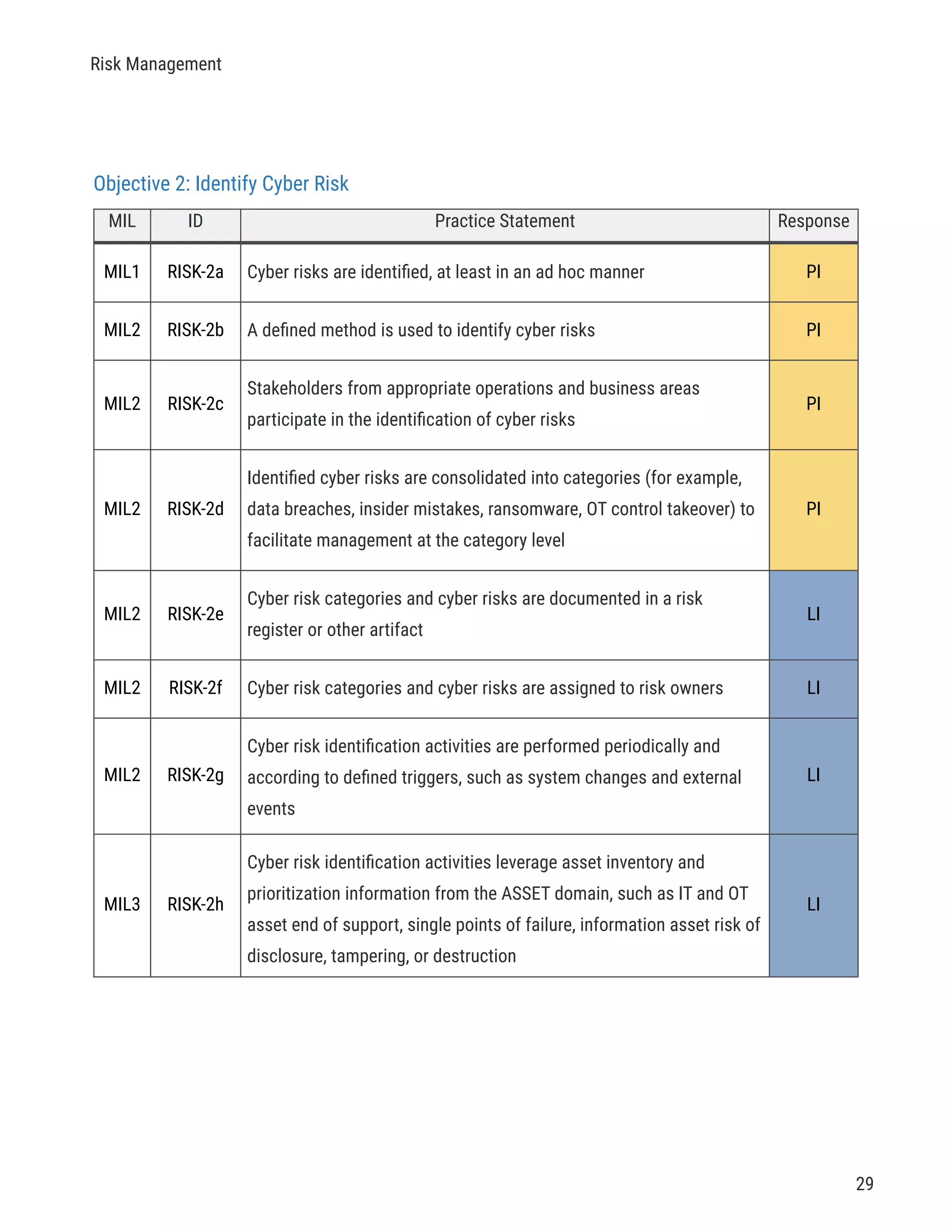
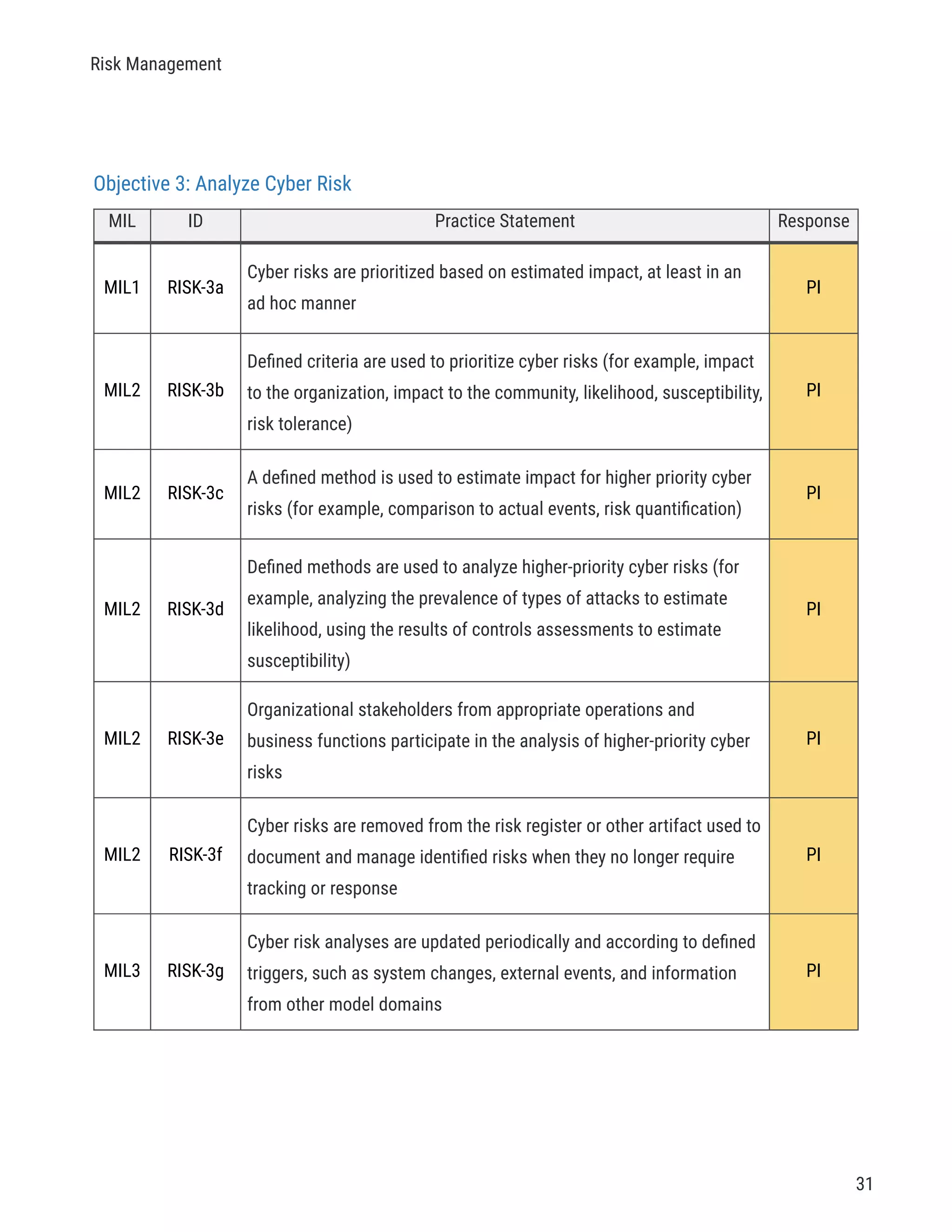
The document describes a cybersecurity self-evaluation conducted using the Cybersecurity Capability Maturity Model (C2M2). It includes an introduction, overview of the C2M2 model architecture which includes 10 domains grouped into objectives and practices at different maturity levels, and purpose statements for each of the 10 domains.


















![Objective 2: Respond to Threats and Share Threat Information
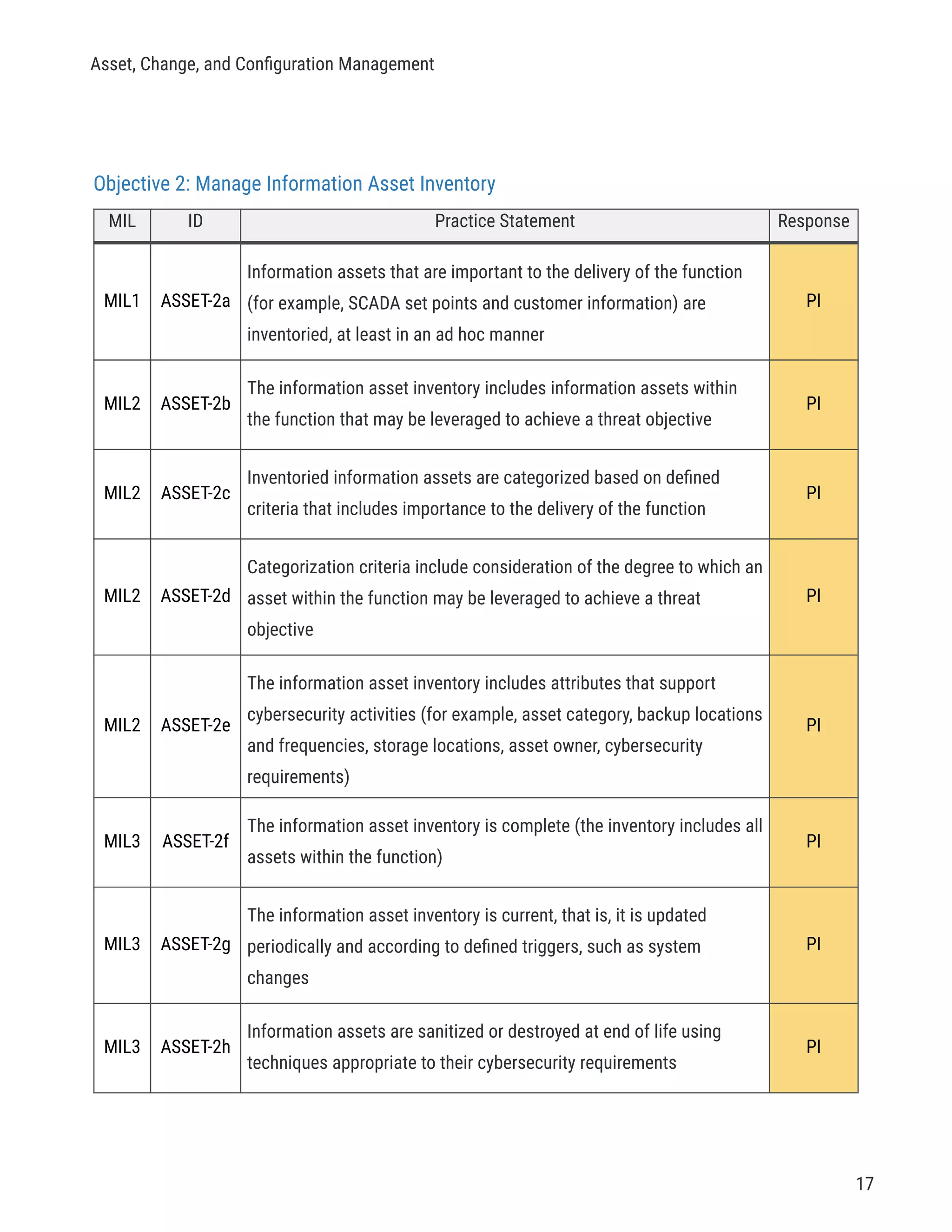
MIL ID Practice Statement Response
MIL1 THREAT-2a
Internal and external information sources to support threat
management activities are identified, at least in an ad hoc manner
PI
MIL1 THREAT-2b
Information about cybersecurity threats is gathered and interpreted
for the function, at least in an ad hoc manner
PI
MIL1 THREAT-2c
Threat objectives for the function are identified, at least in an ad hoc
manner
PI
MIL1 THREAT-2d
Threats that are relevant to the delivery of the function are addressed,
at least in an ad hoc manner
PI
MIL2 THREAT-2e
A threat profile for the function is established that includes threat
objectives and additional threat characteristics (for example, threat
actor types, motives, capabilities, and targets)
PI
MIL2 THREAT-2f
Threat information sources that collectively address all components
of the threat profile are prioritized and monitored
PI
MIL2 THREAT-2g
Identified threats are analyzed and prioritized and are addressed
accordingly
PI
MIL2 THREAT-2h
Threat information is exchanged with stakeholders (for example,
executives, operations staff, government, connected organizations,
vendors, sector organizations, regulators, Information Sharing and
Analysis Centers [ISACs])
PI
Threat and Vulnerability Management
24](https://image.slidesharecdn.com/cybersecuritycapabilitymaturitymodelself-evaluationreportjan272023-230210062441-98d3ee3a/75/Cybersecurity-Capability-Maturity-Model-Self-Evaluation-Report-Jan-27-2023-pdf-27-2048.jpg)
































![Objective 2: Implement Network Protections as an Element of the Cybersecurity Architecture
MIL ID Practice Statement Response
MIL1 ARCHITECTURE-2a
Network protections are implemented, at least in an ad hoc
manner
PI
MIL1 ARCHITECTURE-2b
The organization’s IT systems are separated from OT
systems through segmentation, either through physical
means or logical means, at least in an ad hoc manner
LI
MIL2 ARCHITECTURE-2c
Network protections are defined and enforced for selected
asset types according to asset risk and priority (for example,
internal assets, perimeter assets, assets connected to the
organization’s Wi-Fi, cloud assets, remote access, and
externally owned devices)
LI
MIL2 ARCHITECTURE-2d
Assets that are important to the delivery of the function are
logically or physically segmented into distinct security zones
based on asset cybersecurity requirements
LI
MIL2 ARCHITECTURE-2e
Network protections incorporate the principles of least
privilege and least functionality
LI
MIL2 ARCHITECTURE-2f
Network protections include monitoring, analysis, and
control of network traffic for selected security zones (for
example, firewalls, allowlisting, intrusion detection and
prevention systems [IDPS])
LI
MIL2 ARCHITECTURE-2g
Web traffic and email are monitored, analyzed, and
controlled (for example, malicious link blocking, suspicious
download blocking, email authentication techniques, IP
address blocking)
LI
Cybersecurity Architecture
70](https://image.slidesharecdn.com/cybersecuritycapabilitymaturitymodelself-evaluationreportjan272023-230210062441-98d3ee3a/75/Cybersecurity-Capability-Maturity-Model-Self-Evaluation-Report-Jan-27-2023-pdf-73-2048.jpg)
![MIL ID Practice Statement Response
MIL3 ARCHITECTURE-2h
All assets are segmented into distinct security zones based
on cybersecurity requirements
LI
MIL3 ARCHITECTURE-2i
Separate networks are implemented, where warranted, that
logically or physically segment assets into security zones
with independent authentication
LI
MIL3 ARCHITECTURE-2j
OT systems are operationally independent from IT systems
so that OT operations can be sustained during an outage of
IT systems
LI
MIL3 ARCHITECTURE-2k
Device connections to the network are controlled to ensure
that only authorized devices can connect (for example,
network access control [NAC])
LI
MIL3 ARCHITECTURE-2l
The cybersecurity architecture enables the isolation of
compromised assets
LI
Cybersecurity Architecture
71](https://image.slidesharecdn.com/cybersecuritycapabilitymaturitymodelself-evaluationreportjan272023-230210062441-98d3ee3a/75/Cybersecurity-Capability-Maturity-Model-Self-Evaluation-Report-Jan-27-2023-pdf-74-2048.jpg)
























![MIL Response ID Practice Self-Evaluation Notes
THREAT-2f Threat information sources
that collectively address all
components of the threat
profile are prioritized and
monitored
THREAT-2g Identified threats are analyzed
and prioritized and are
addressed accordingly
THREAT-2h Threat information is
exchanged with stakeholders
(for example, executives,
operations staff, government,
connected organizations,
vendors, sector organizations,
regulators, Information Sharing
and Analysis Centers [ISACs])
THREAT-3a Documented procedures are
established, followed, and
maintained for activities in the
THREAT domain
THREAT-3b Adequate resources (people,
funding, and tools) are
provided to support activities
in the THREAT domain
3 Partially
Implemented
(PI)
THREAT-1j Cybersecurity vulnerability
information sources that
collectively address all IT and
List of Partially Implemented and Not Implemented Practices
96](https://image.slidesharecdn.com/cybersecuritycapabilitymaturitymodelself-evaluationreportjan272023-230210062441-98d3ee3a/75/Cybersecurity-Capability-Maturity-Model-Self-Evaluation-Report-Jan-27-2023-pdf-99-2048.jpg)


































