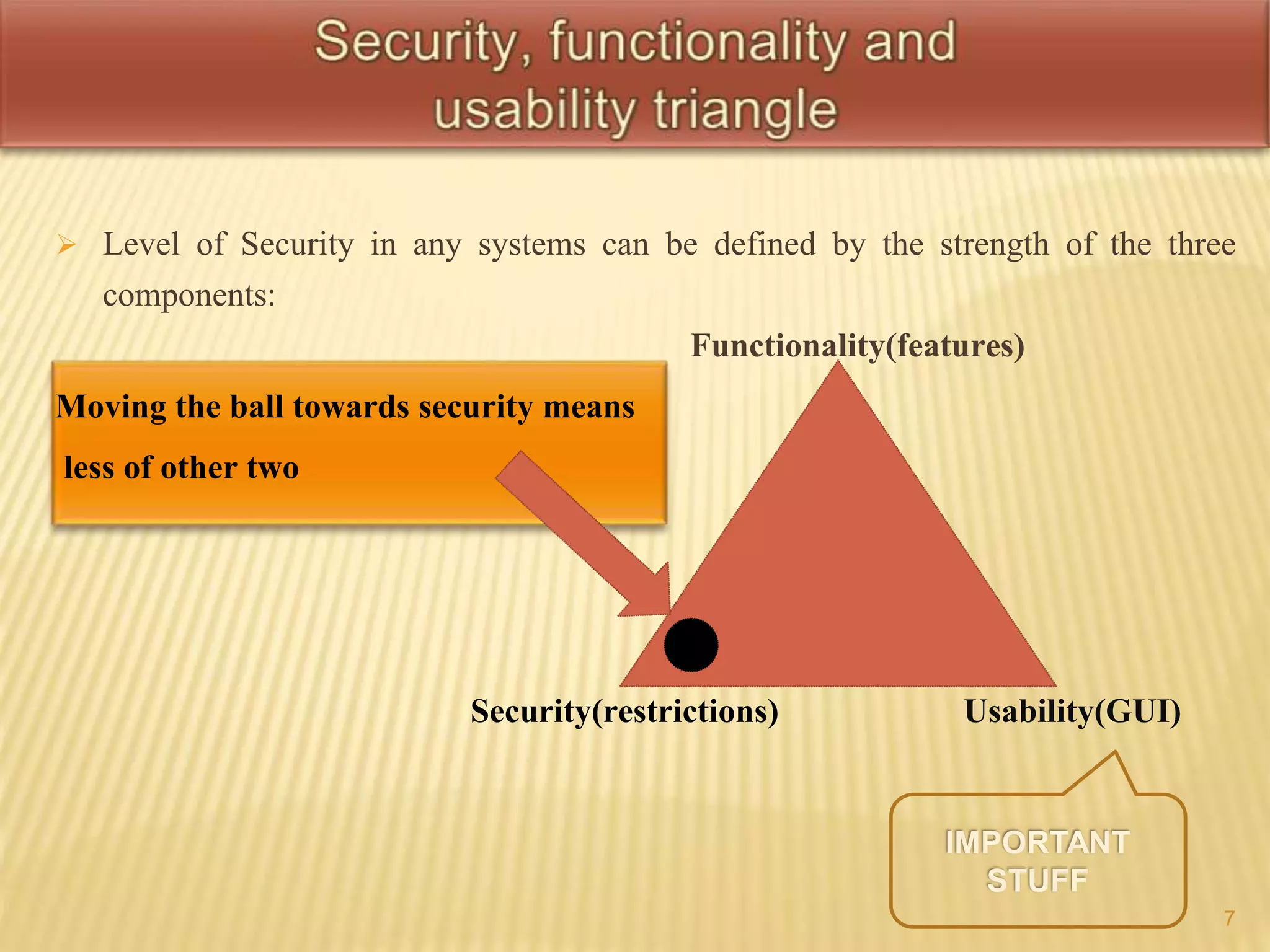
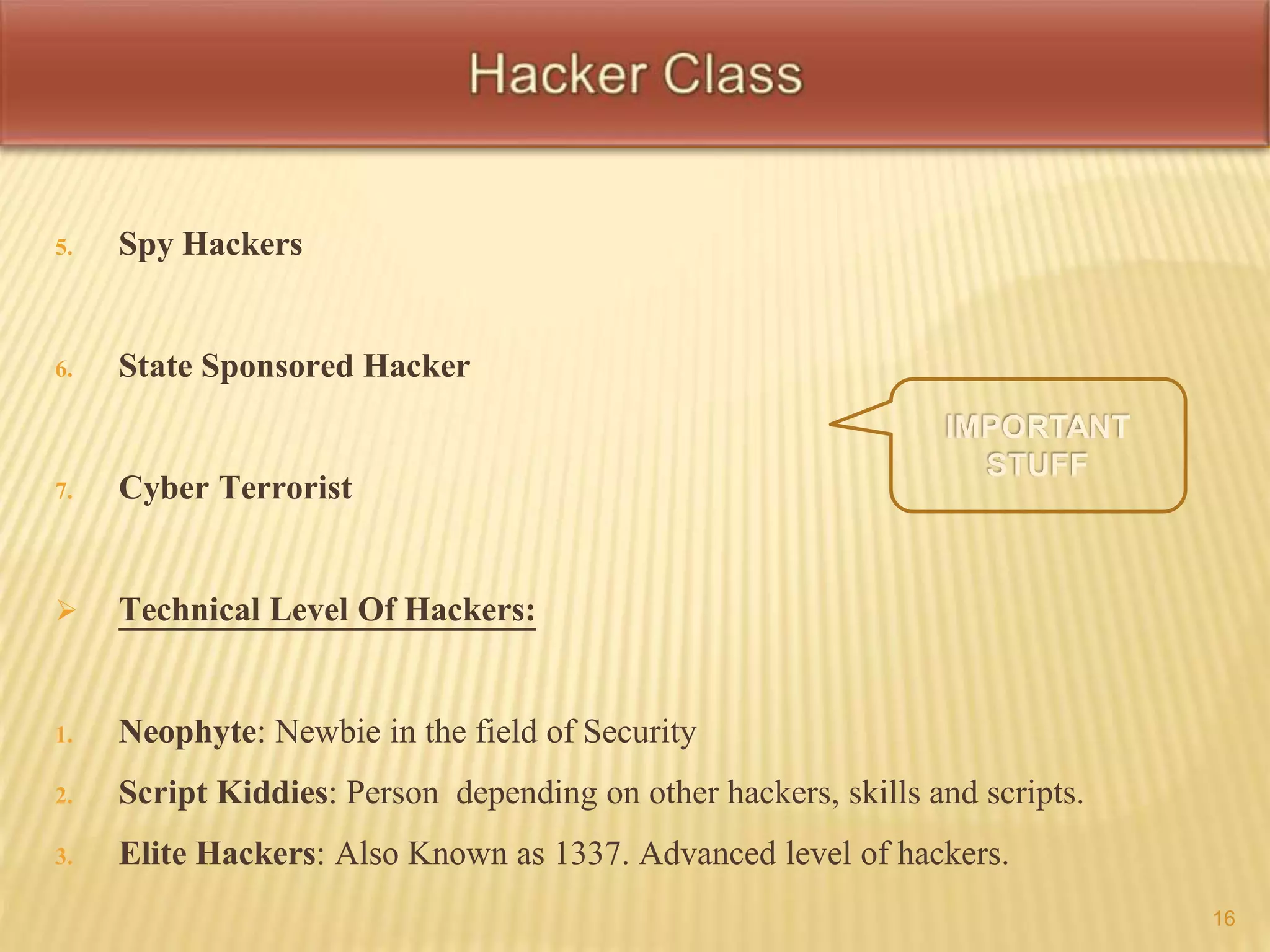
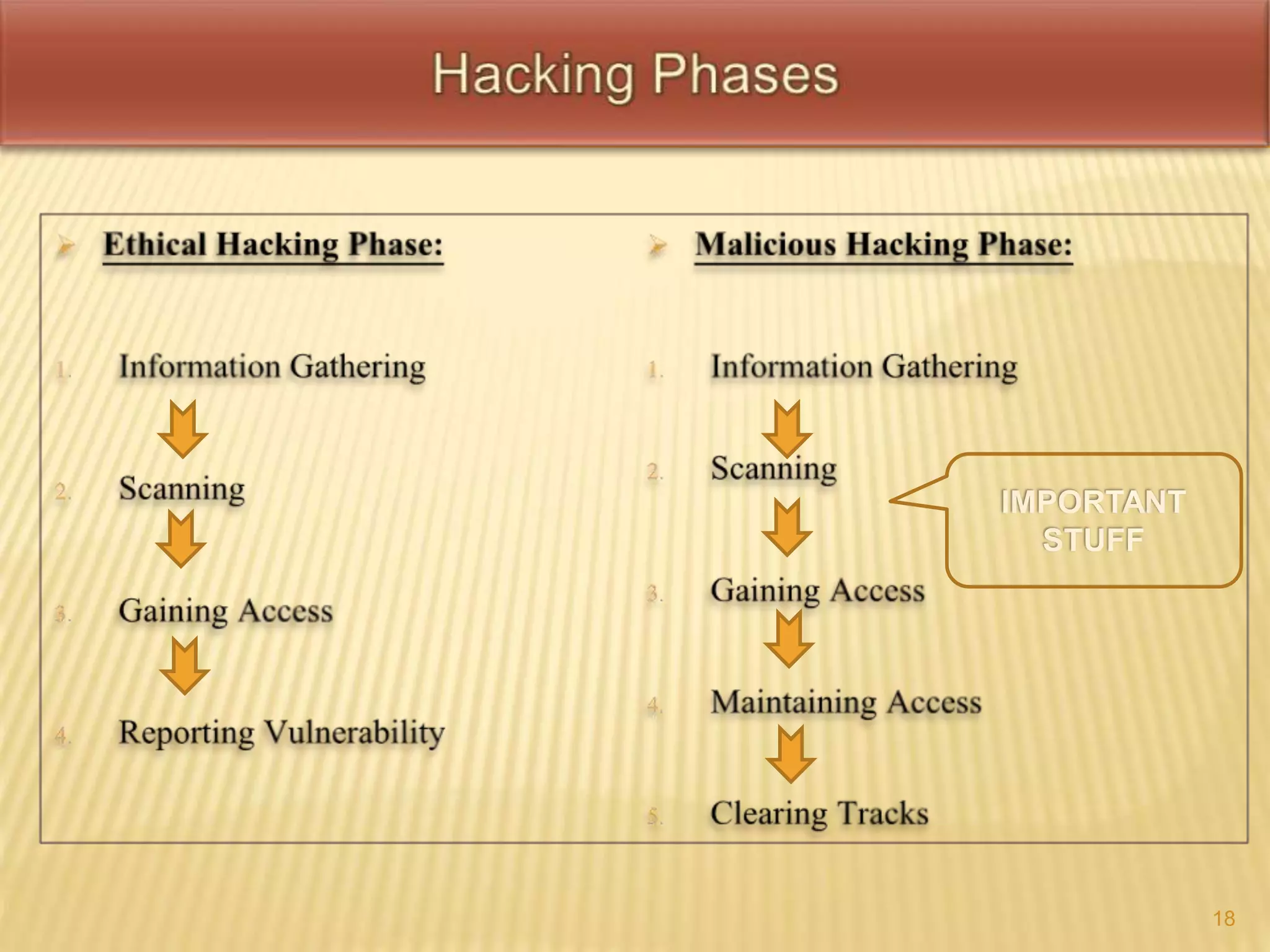
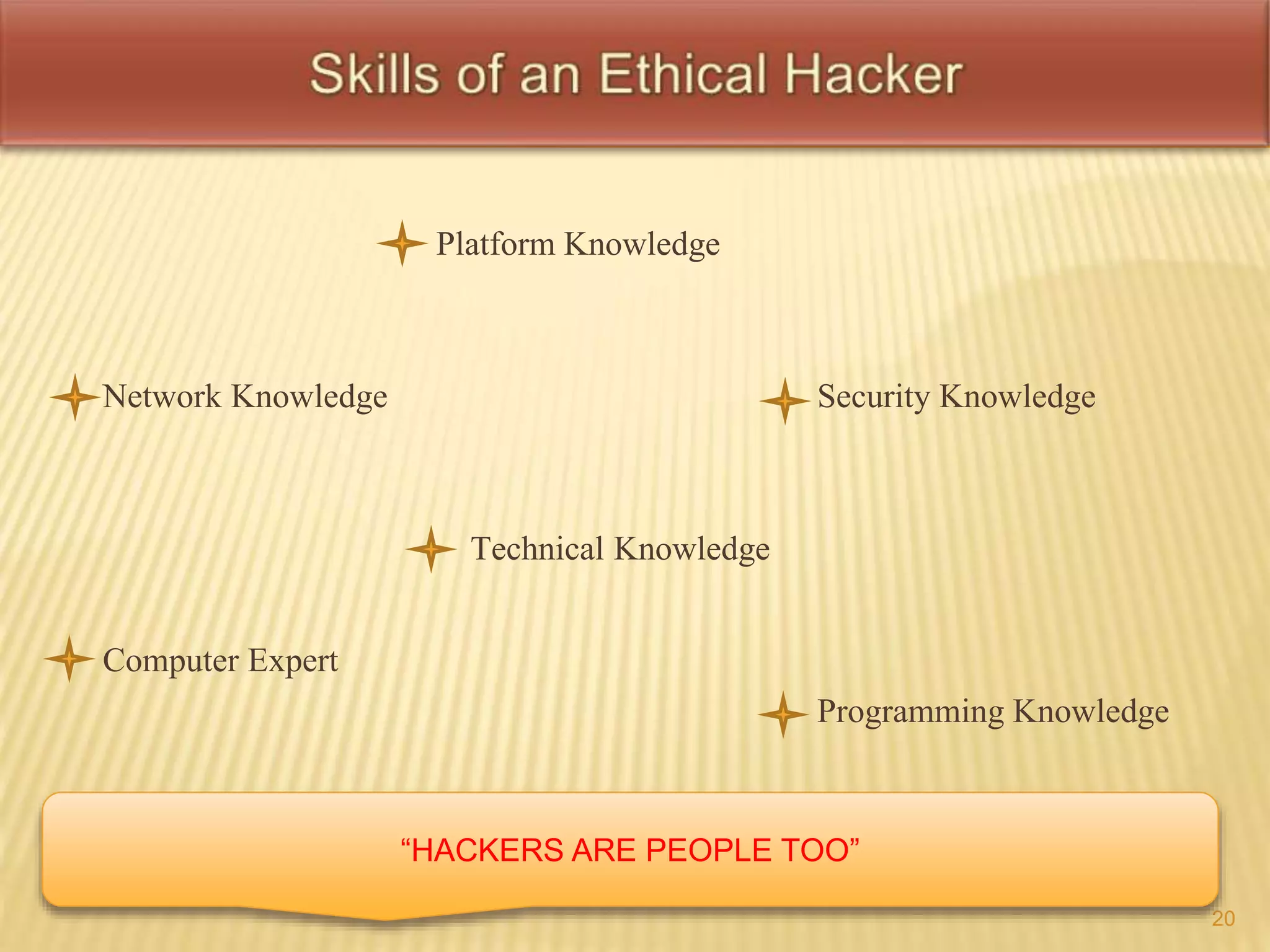
This document defines key terms related to hacking and cybersecurity, including hack value, exploits, vulnerabilities, and different types of attacks. It discusses the goals of security in terms of confidentiality, integrity, availability, authenticity, and non-repudiation. The document also categorizes information security threats and human threats, and differentiates between hacking and ethical hacking. It defines different types of hackers like black hat and white hat hackers and their motivations.