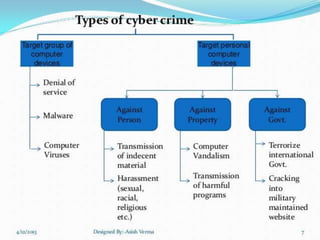
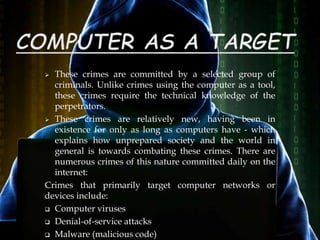
This document discusses cybercrime and various types of cybercrimes such as computer fraud, cyber extortion, cyberwarfare, crimes targeting individuals, and crimes targeting computer networks. It provides examples of different cybercrimes and highlights the importance of protecting personal information and computer security. The key challenges are that individuals and organizations of all sizes are vulnerable to cyber attacks, and that attitudes need to change to prioritize cyber security and incident detection.