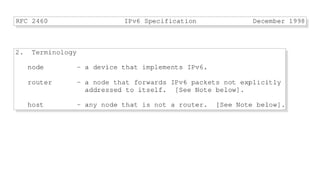
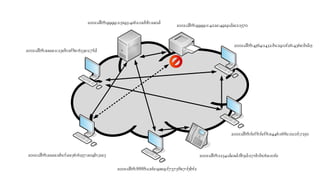
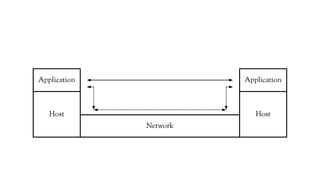
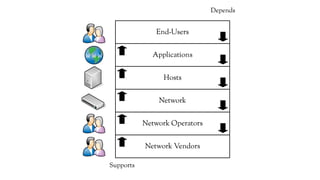
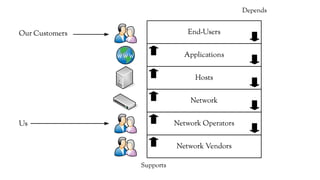
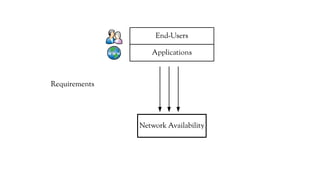
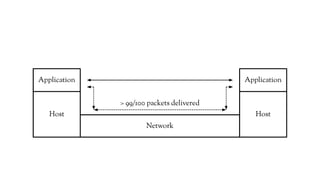
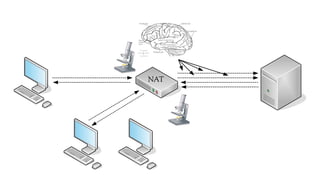
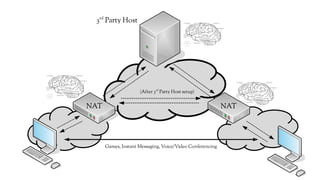
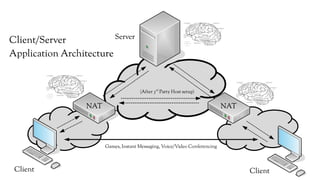
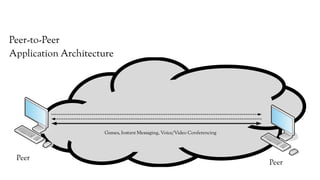
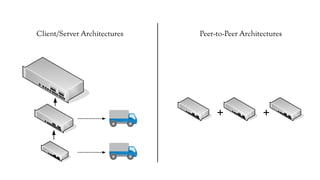
The document discusses the issues with Network Address Translation (NAT) and why the author cares about IPv6. It summarizes the key impacts of NAT, including that it prevents devices on the same network from acting as peers, relies on external hosts or relays, and is vulnerable to denial of service attacks and loss of state. The author argues that this goes against the intended peer-to-peer nature of the Internet protocols and that IPv6 removes the fundamental constraints of NAT by allowing nodes to use their own IP addresses and communicate directly.











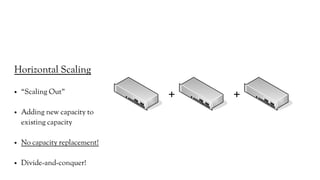












![Client/Server?
IPv4
[mark@x13 RFCs]$ egrep -i "(Client|Server)" rfc791.txt
[mark@x13 RFCs]$
IPv6
[mark@x13 RFCs]$ egrep -i "(Client|Server)" rfc2460.txt
[mark@x13 RFCs]$](https://image.slidesharecdn.com/2d39dbb9-7477-444b-bdff-204be2c142bb-160901002113/85/AusNOG-2016-The-Trouble-with-NAT-43-320.jpg)