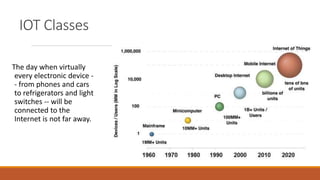
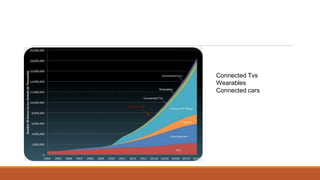
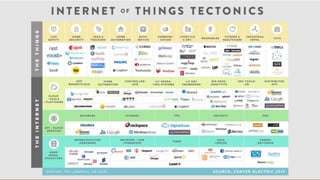
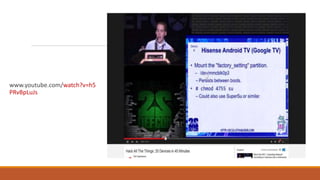
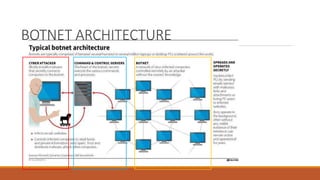
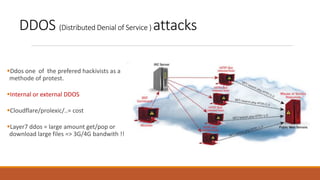
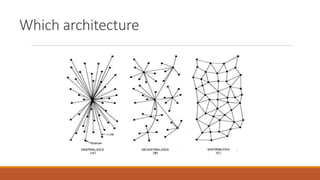
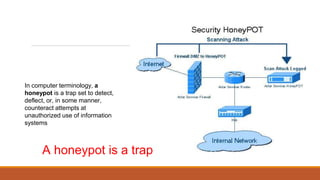
The document discusses the security risks posed by the growing Internet of Things (IoT). As more everyday devices become connected to the internet, they could be vulnerable to attacks that turn them into "thingbots" that are part of botnets controlled by hackers. This could allow hackers to launch large-scale distributed denial of service (DDoS) attacks or spy on users by accessing unsecured cameras and other smart home devices. Researchers have already discovered botnets made up of thousands of compromised IoT devices like routers, smart TVs and refrigerators. To address this, the document recommends steps like using secure chips and honeypots to detect malicious activity from IoT devices and help secure the growing IoT ecosystem.