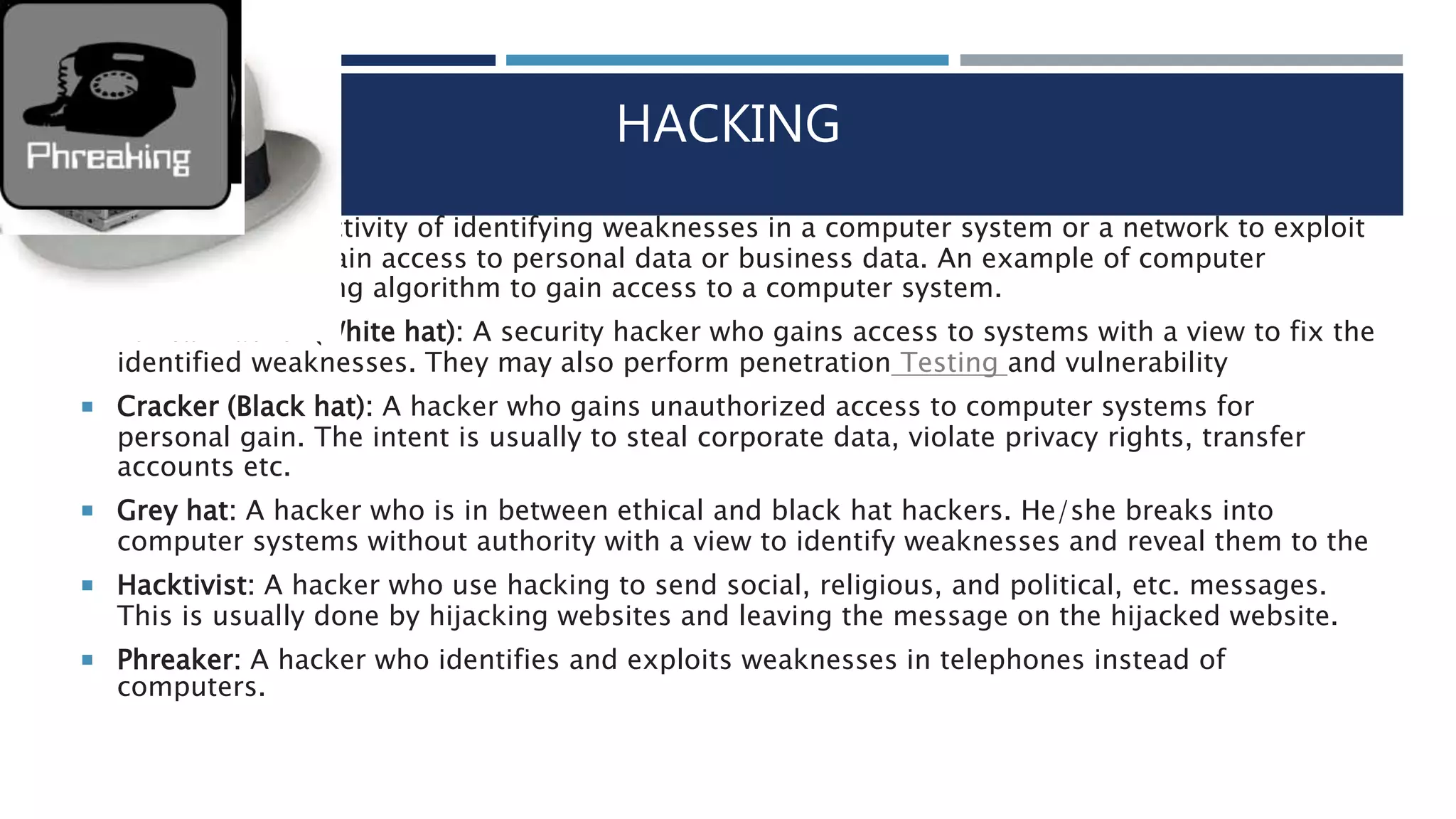
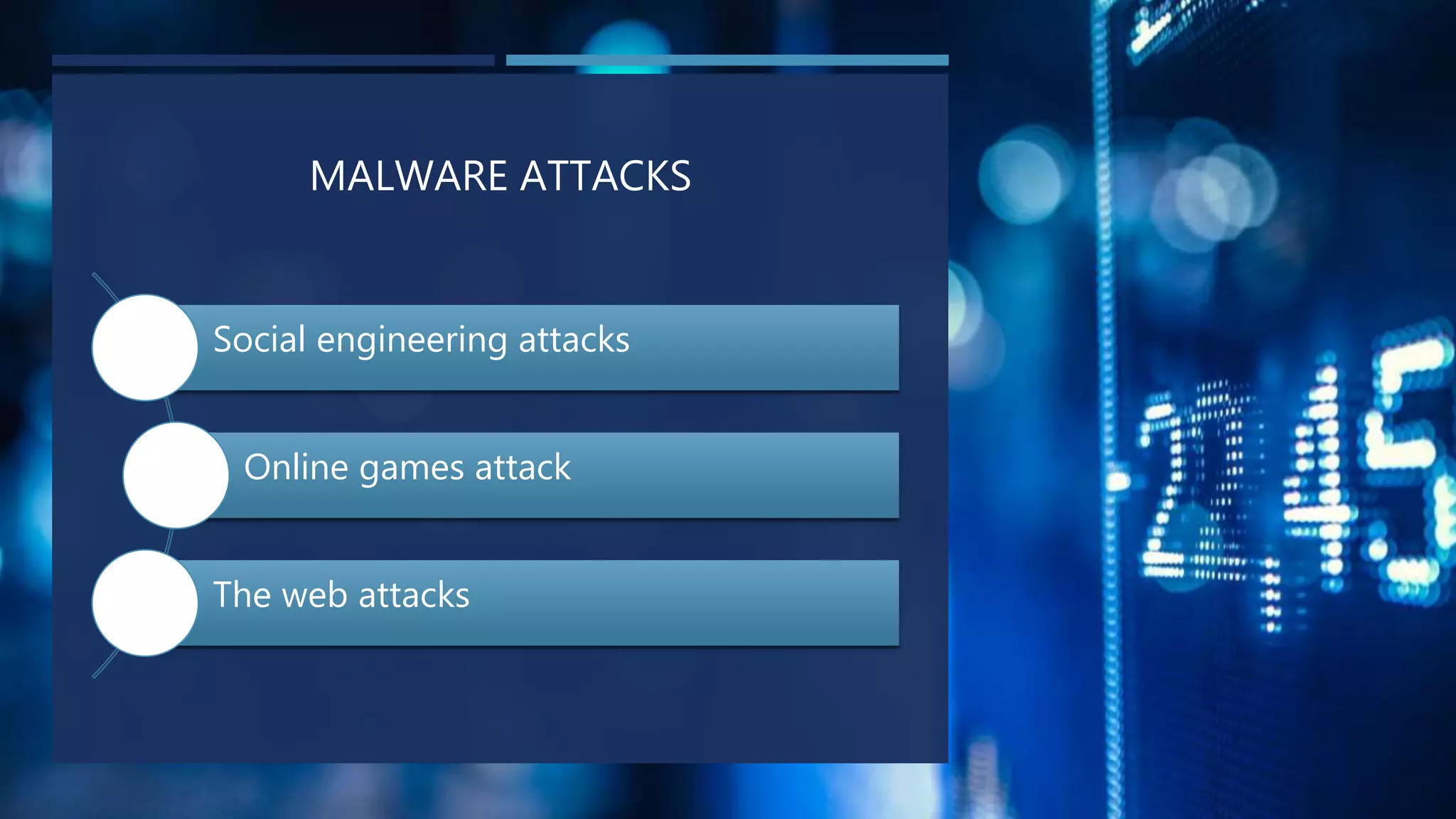
The document discusses various topics related to computer ethics. It begins by defining computer ethics as enforcing ethical implementation and use of computing resources through avoiding copyright infringement and unauthorized distribution of digital content. It then lists 10 commandments of computer ethics established by the Computer Ethics Institute in 1992. Some concepts that can lead to unethical computer use discussed include data stealing, cybercrime, hacking, and embezzlement. Cybercrime refers to criminal acts involving computers or networks. Common types of cybercrime are hacking, stealing software/data, and identity theft. Data theft is also common using devices like USB drives to copy large amounts of data. Hacking involves exploiting security weaknesses for unauthorized access, while social engineering and malware attacks are other risks.