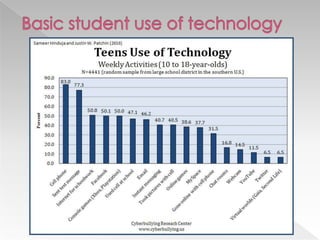
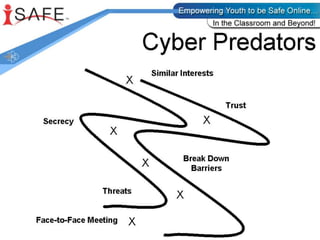
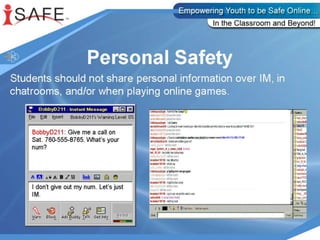
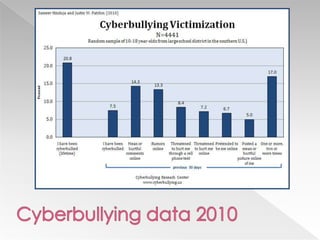
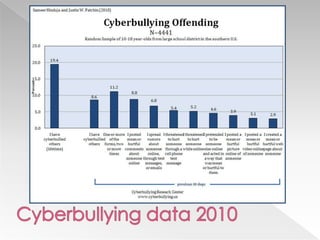
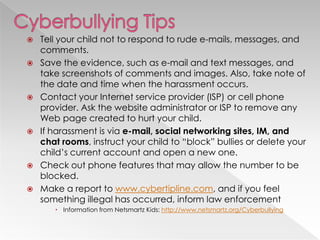
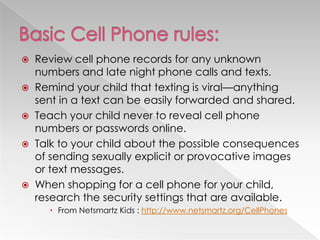
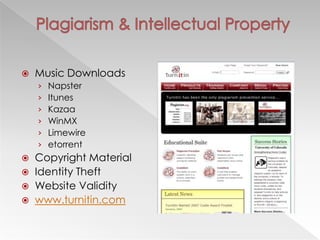
This document discusses various internet safety topics for children and parents. It covers internet predators, personal profiles, internet chat, gaming, and cyberbullying. It also addresses cell phones, plagiarism, intellectual property, viruses, spyware, and provides tips for parents. The goal is to educate both parents and students about potential online dangers and how to stay safe online.