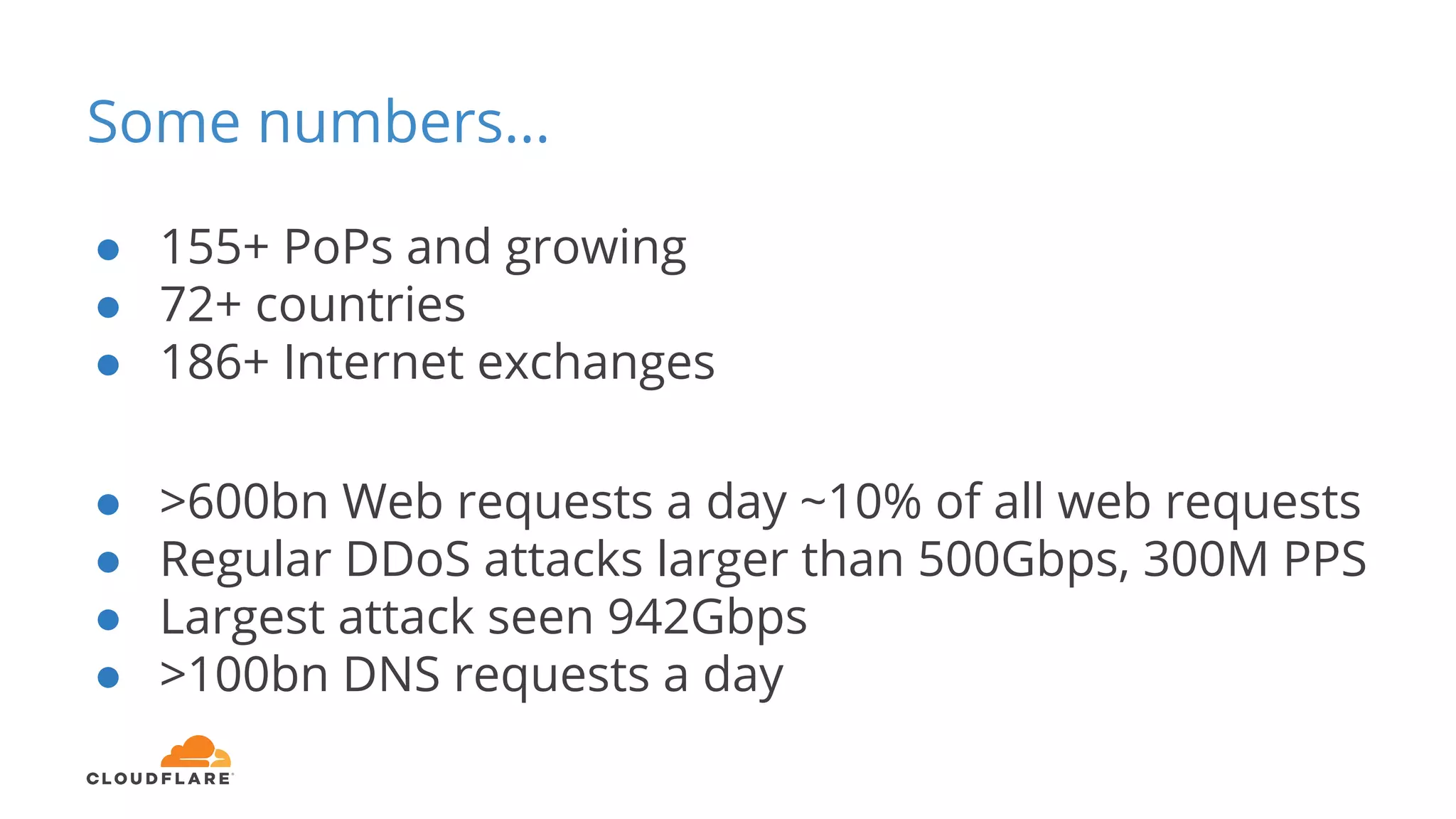
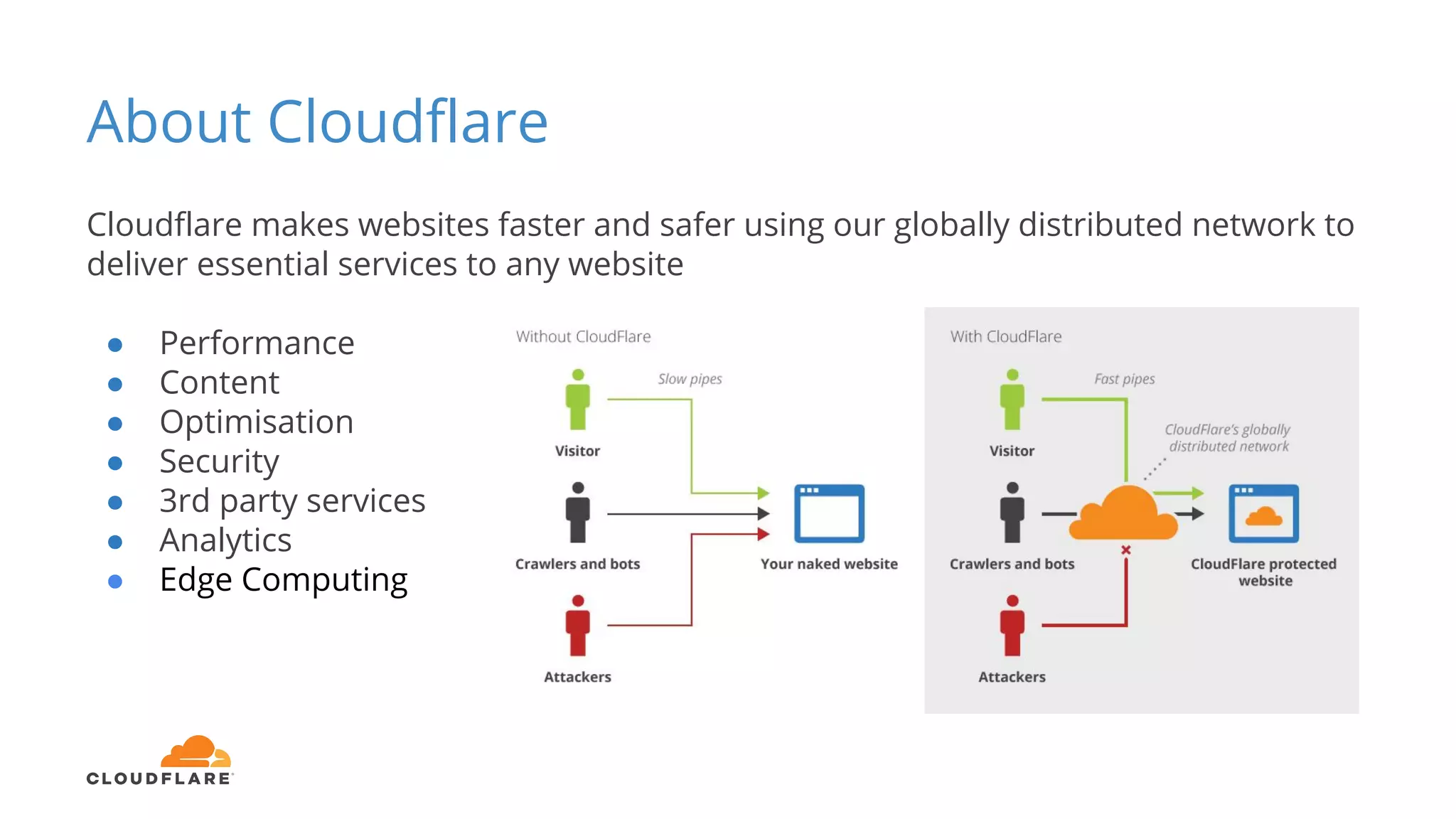
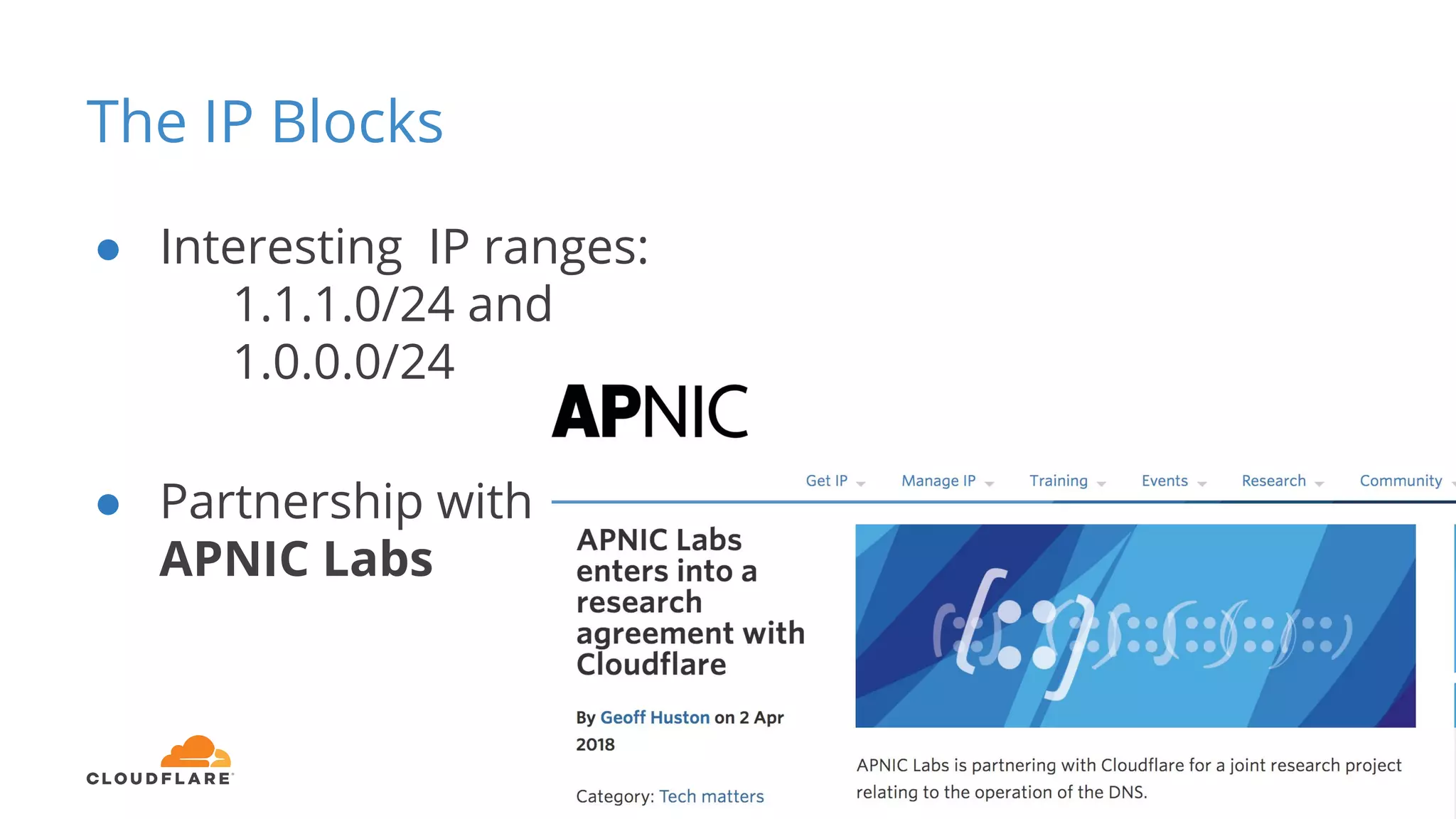
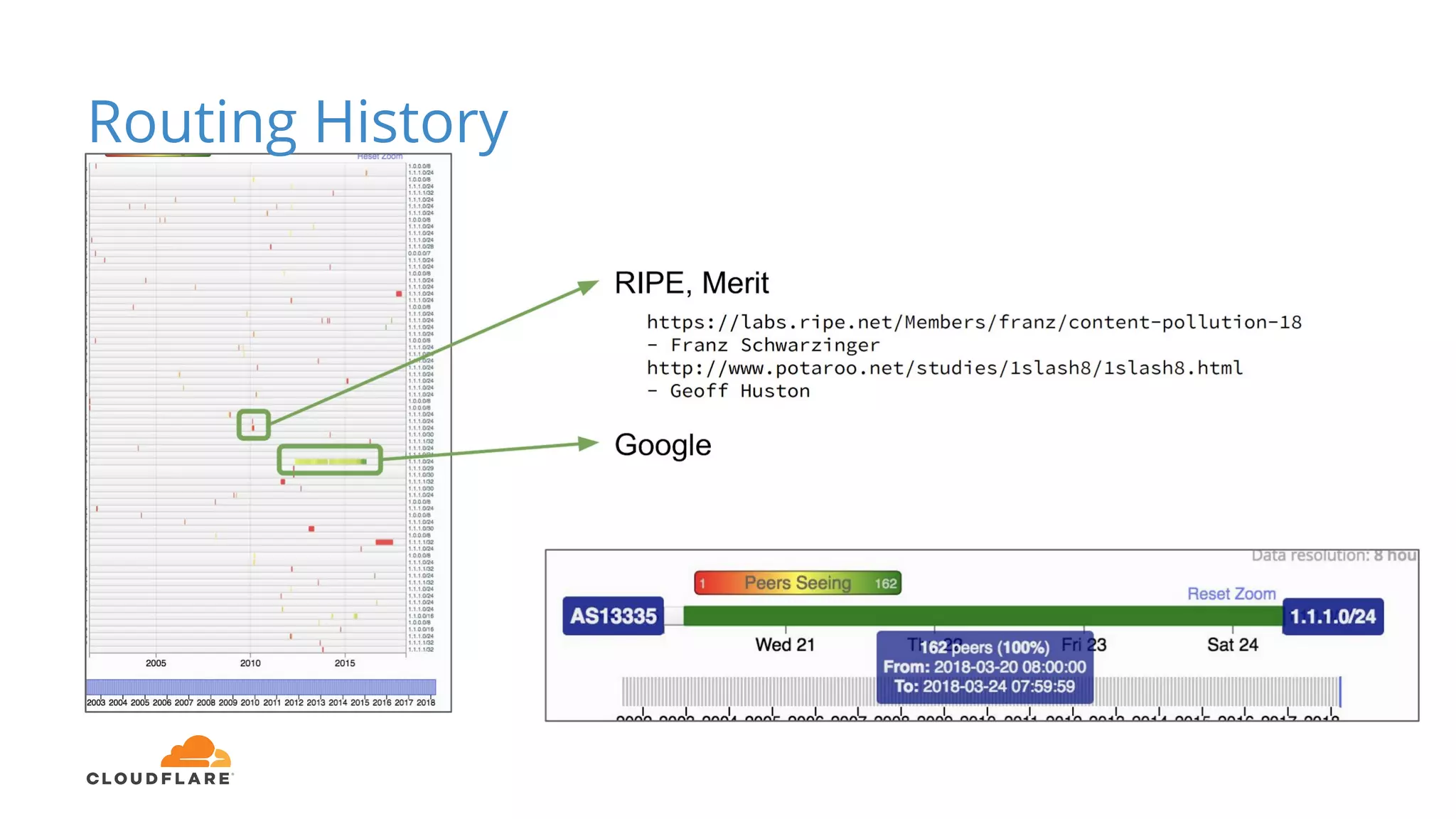
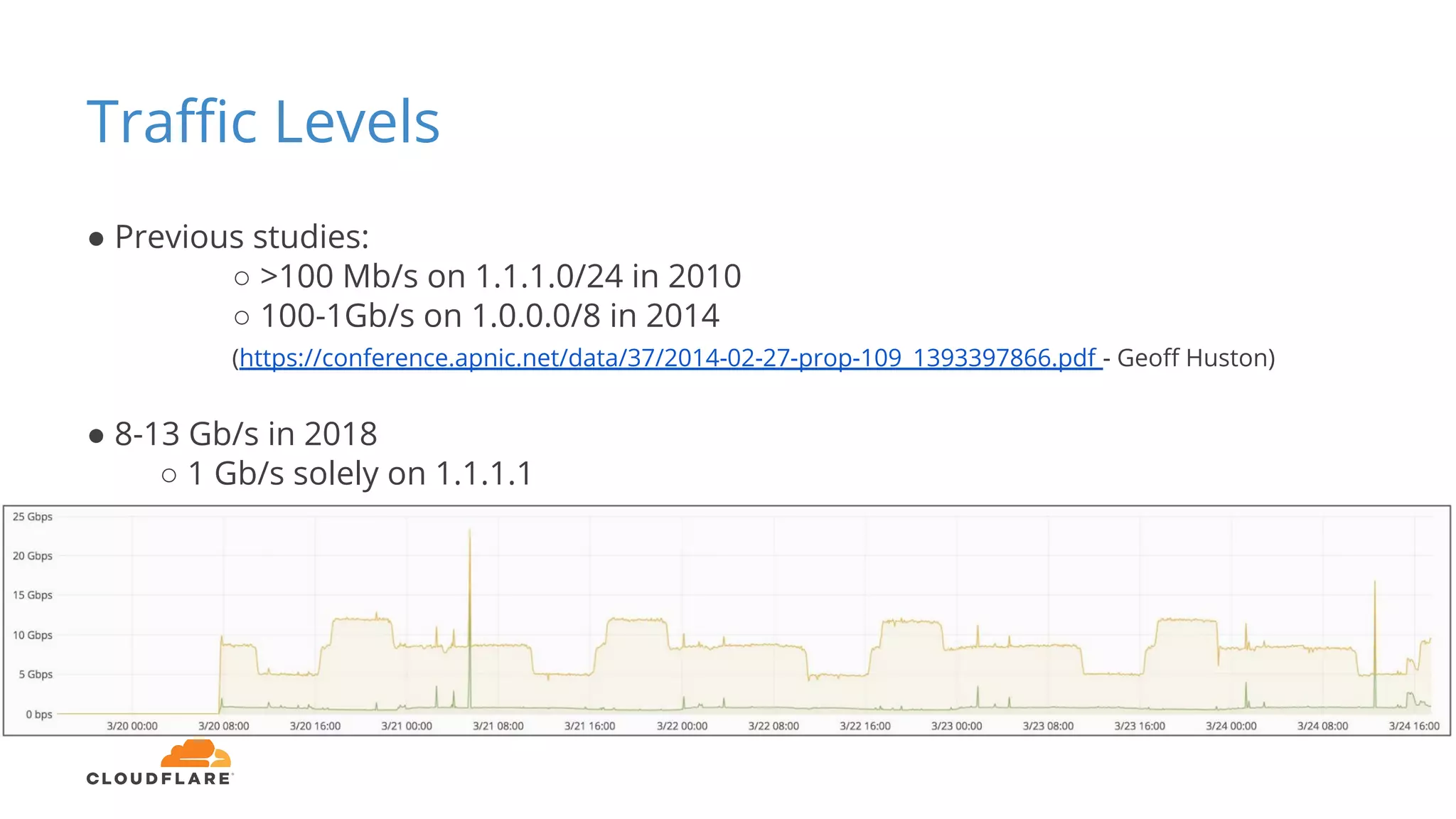
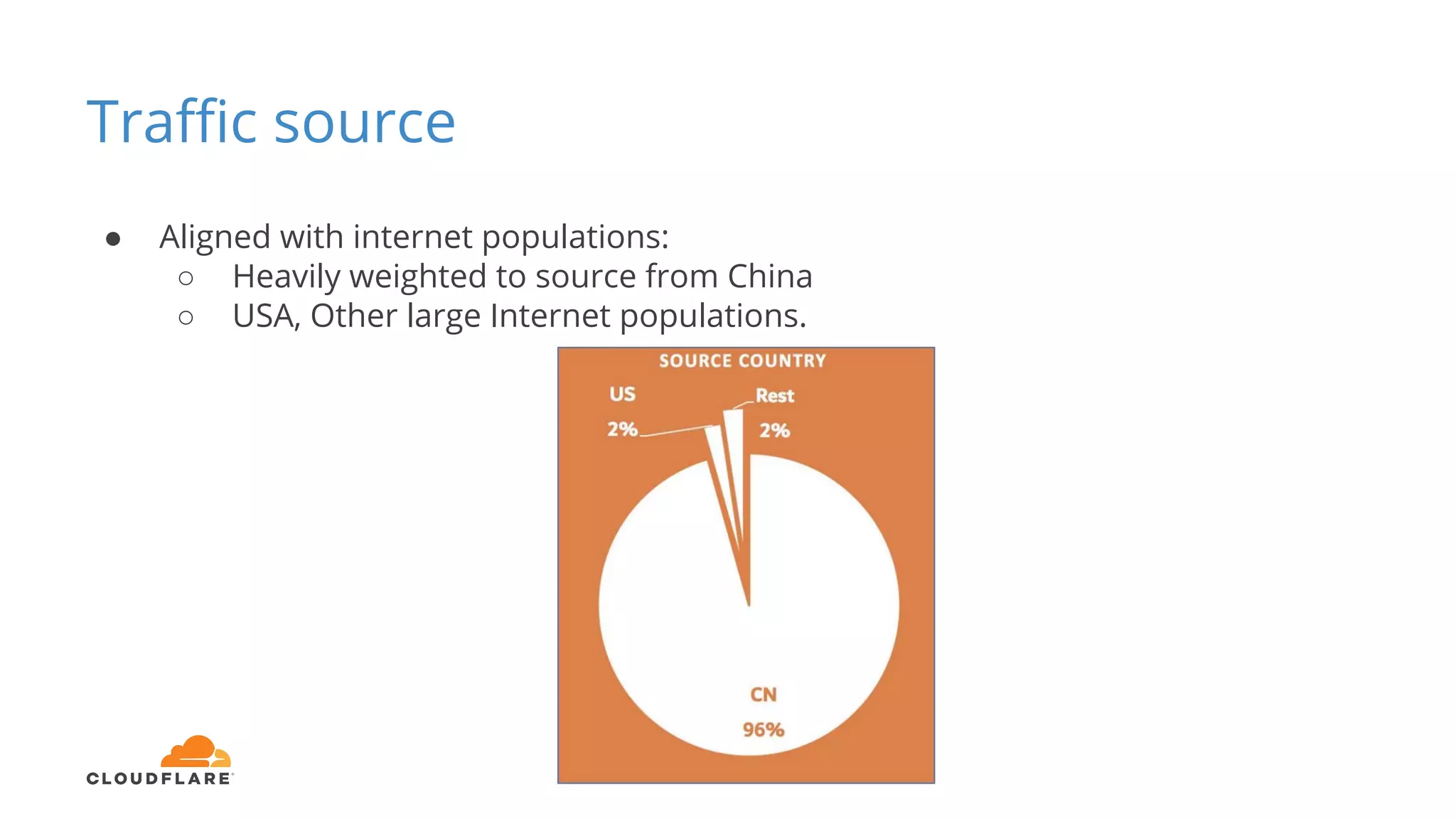
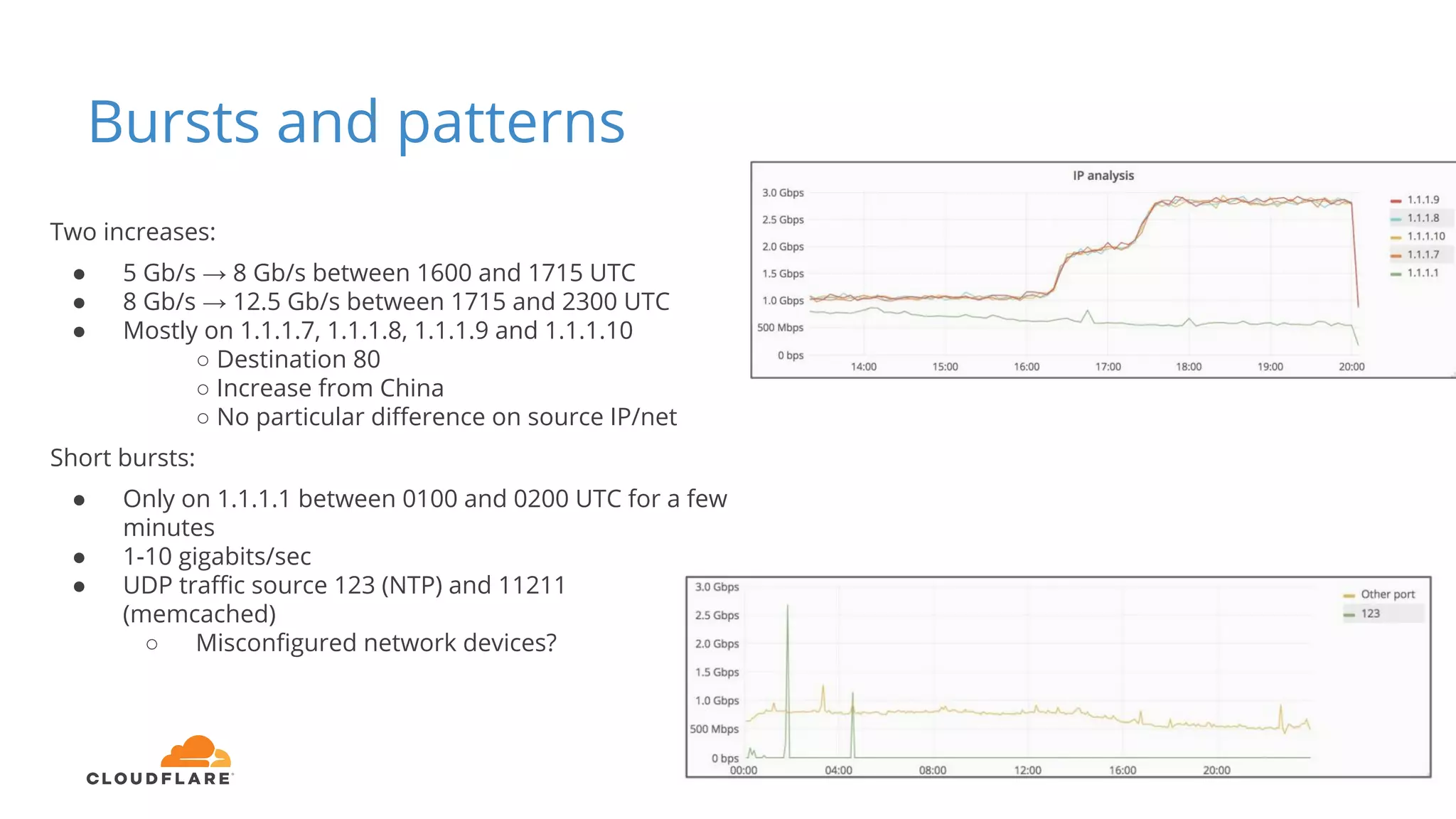
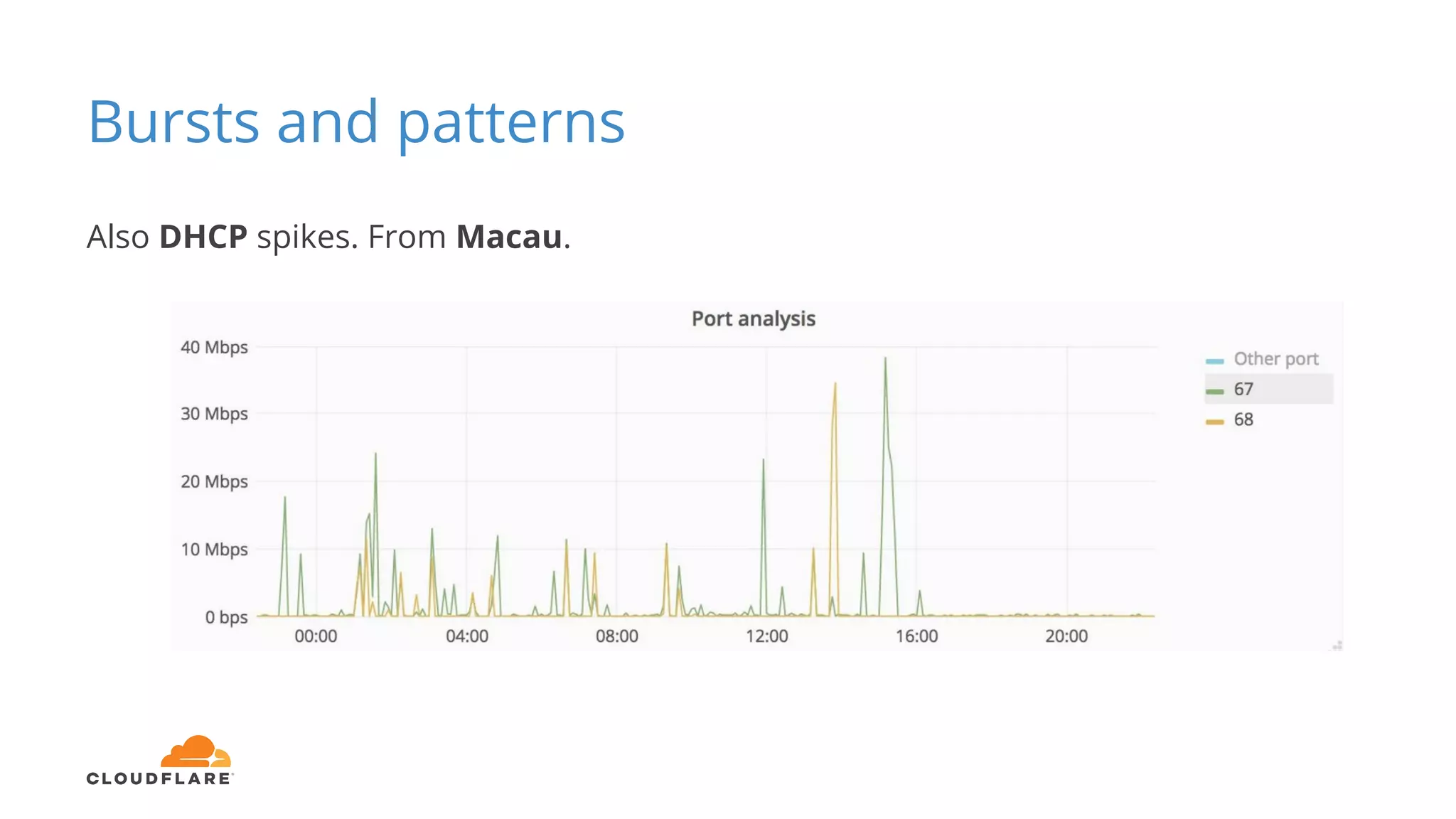
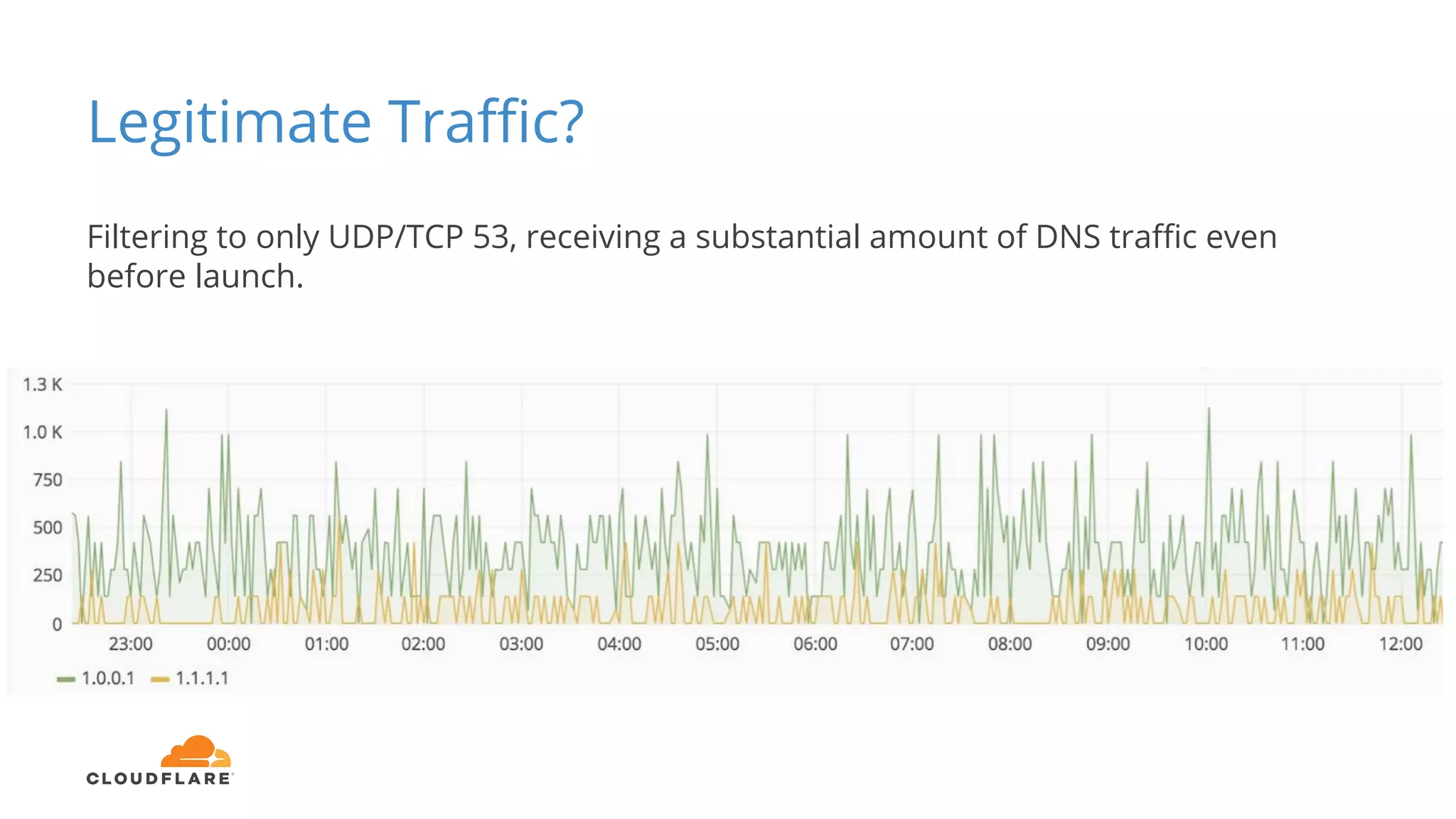
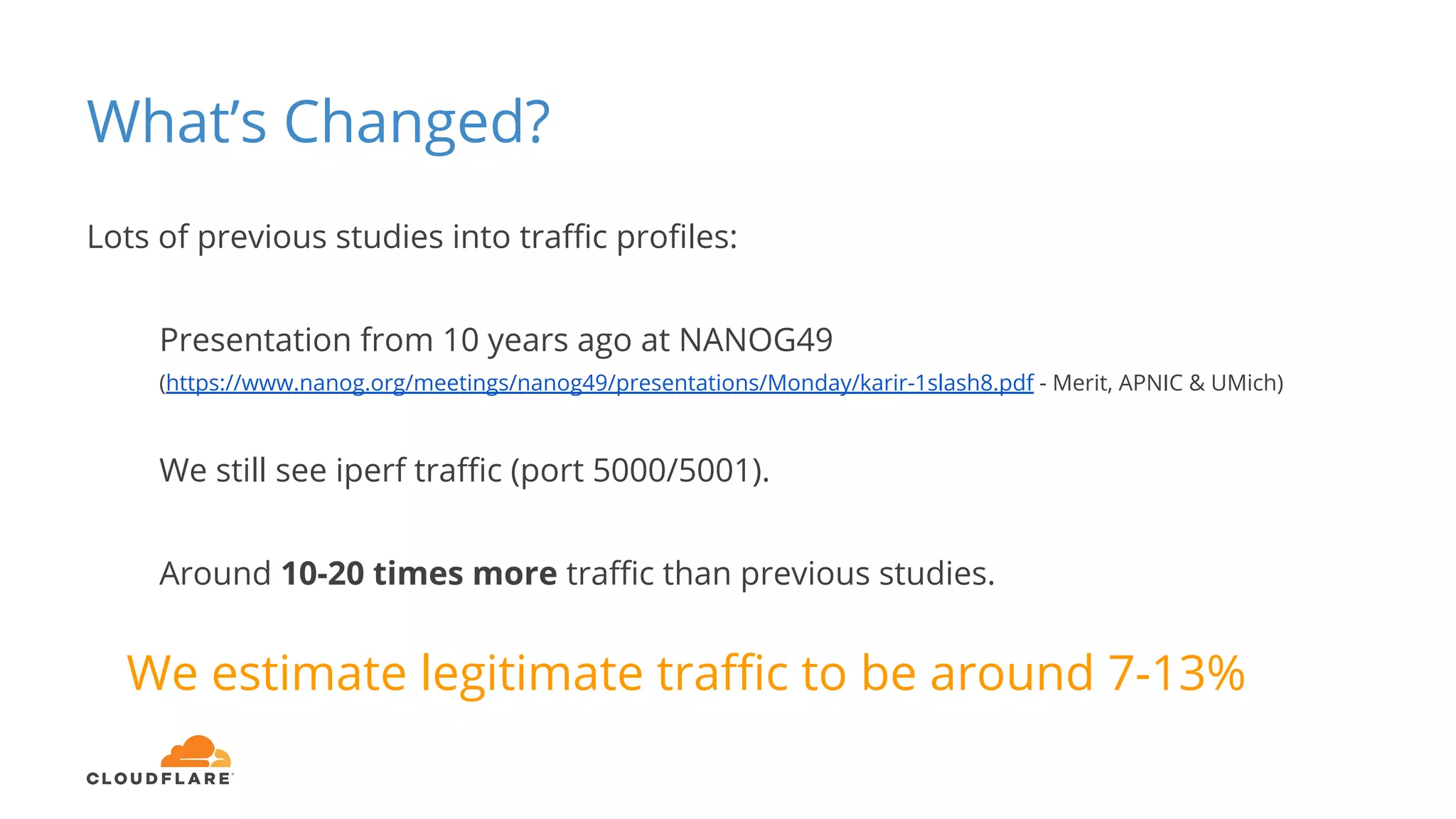
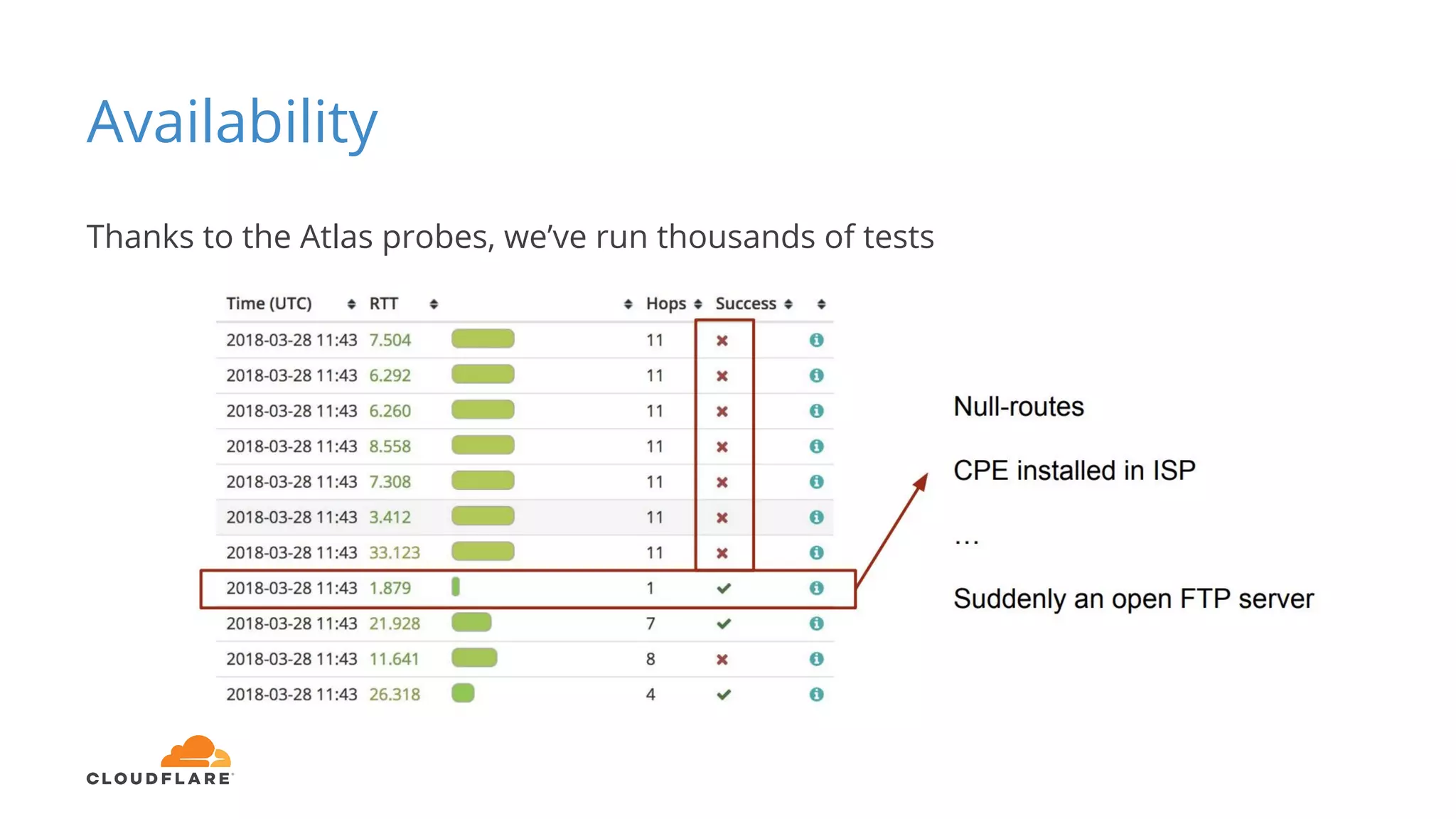
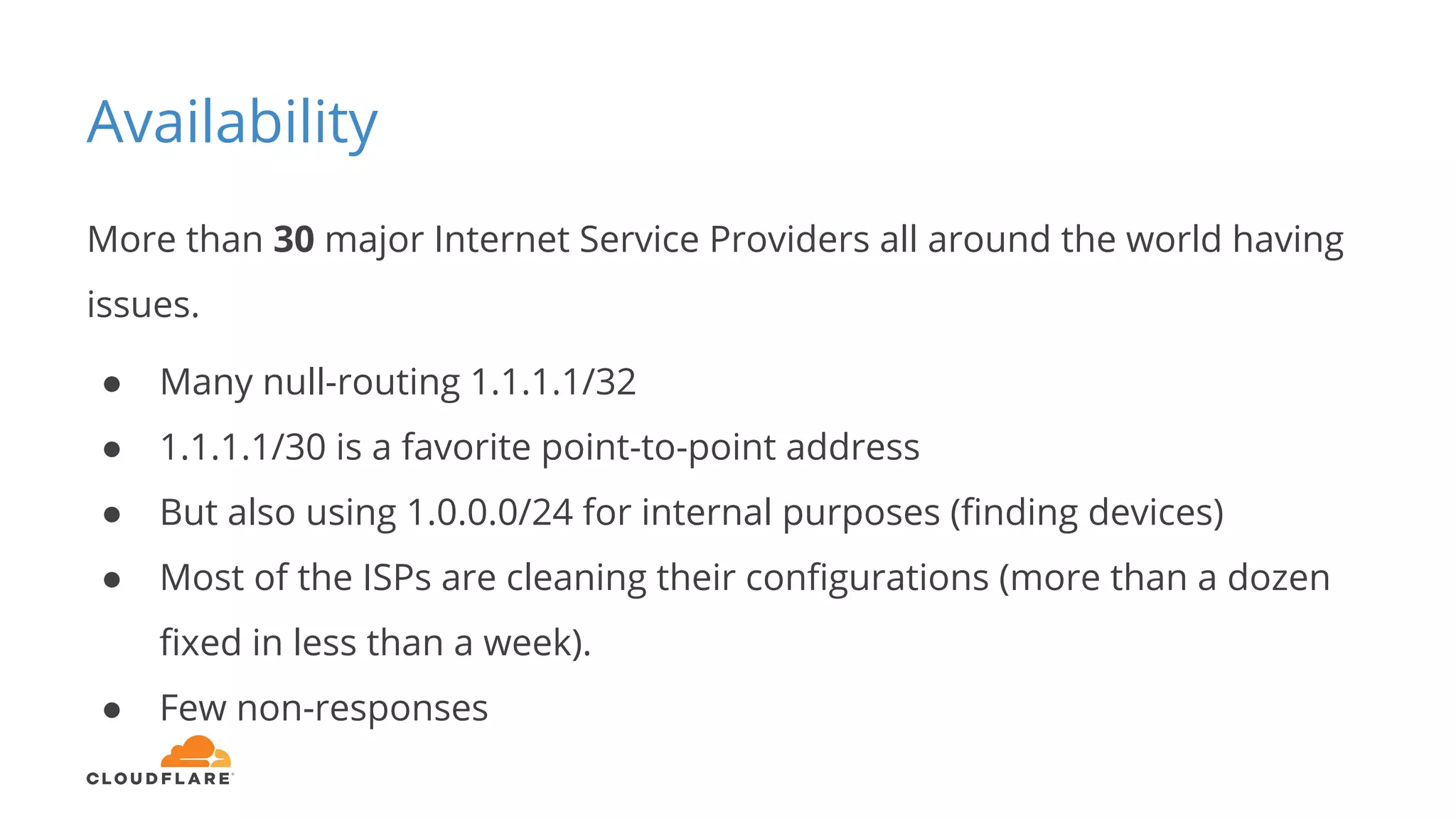
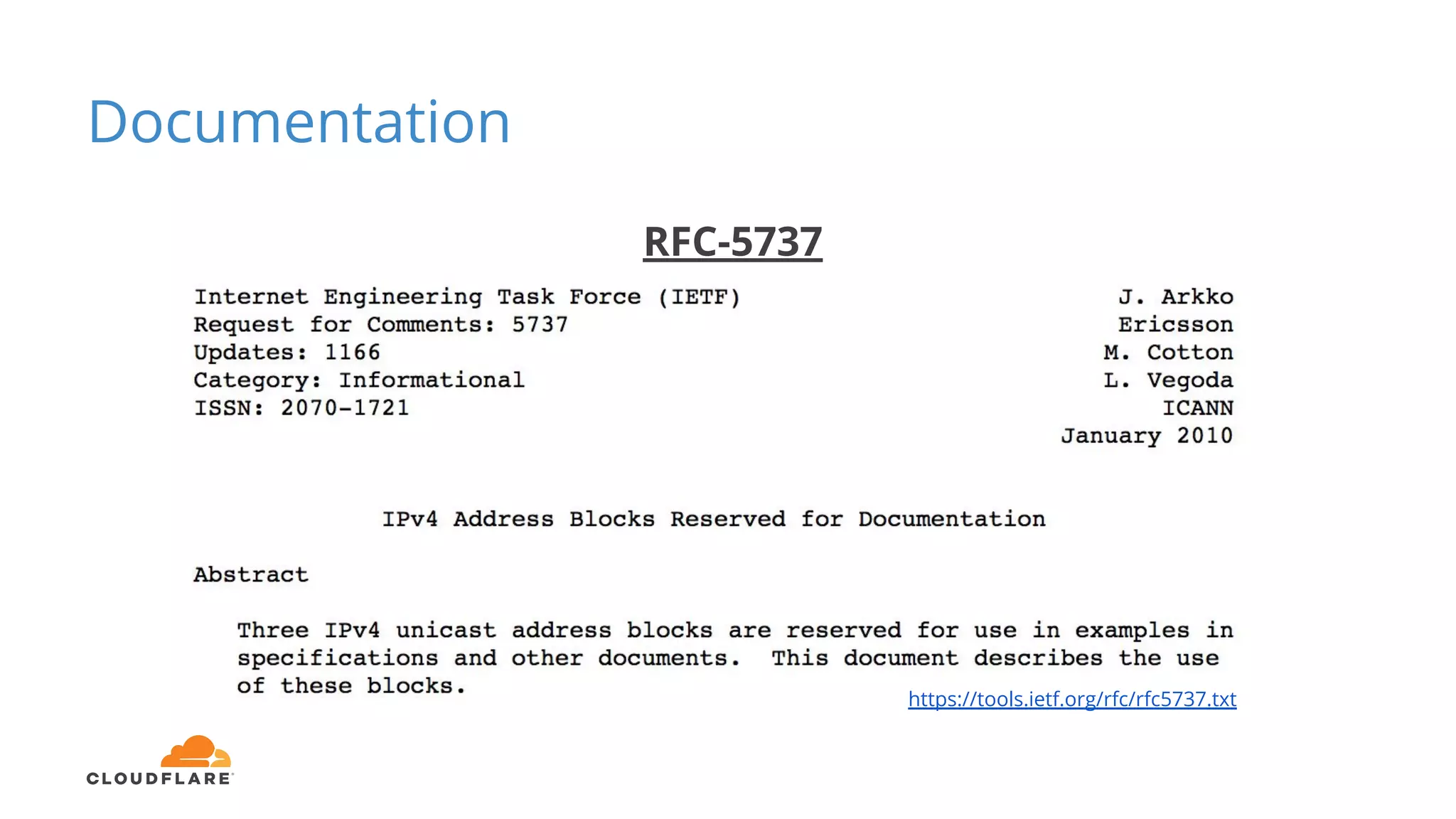
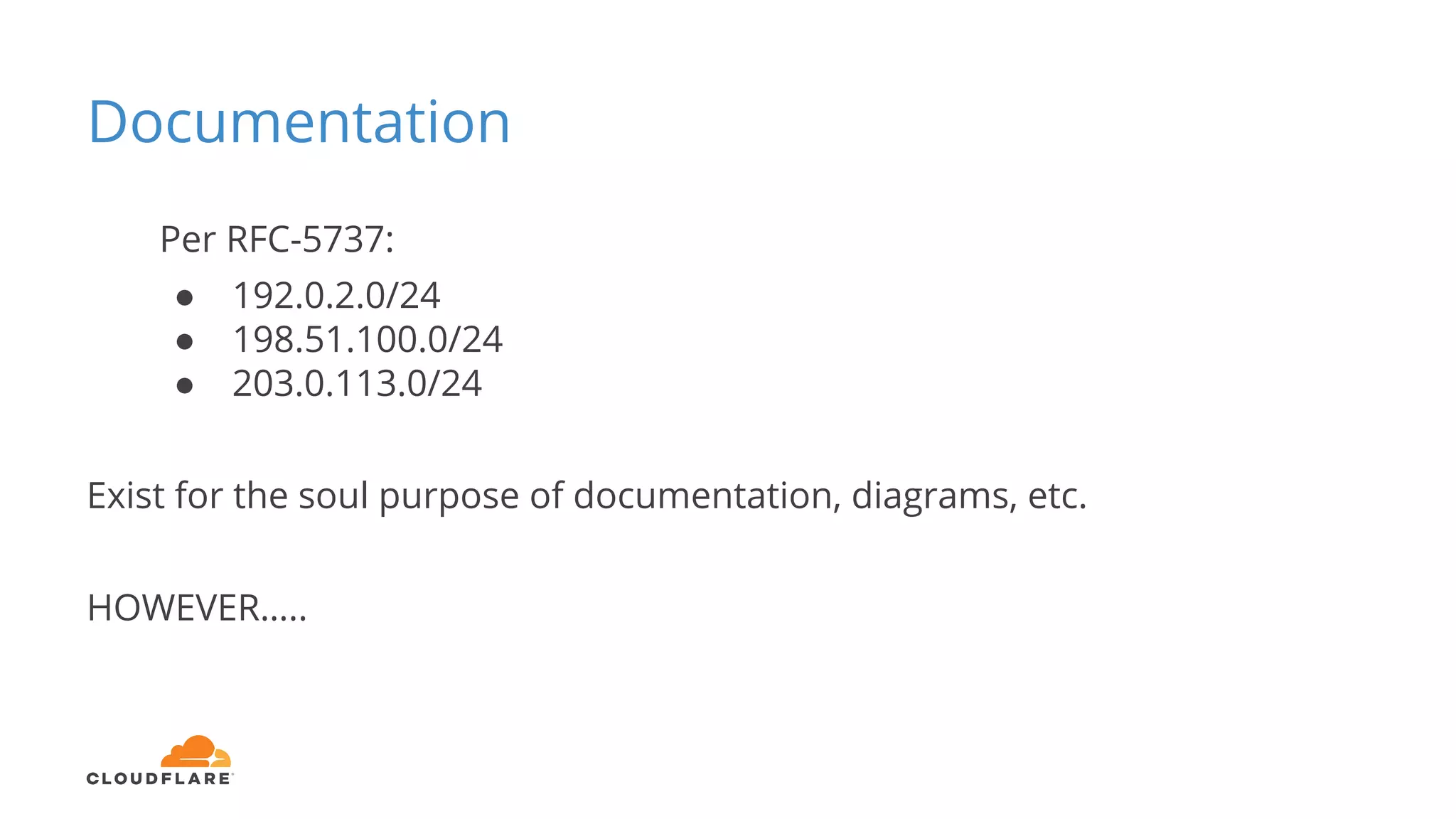
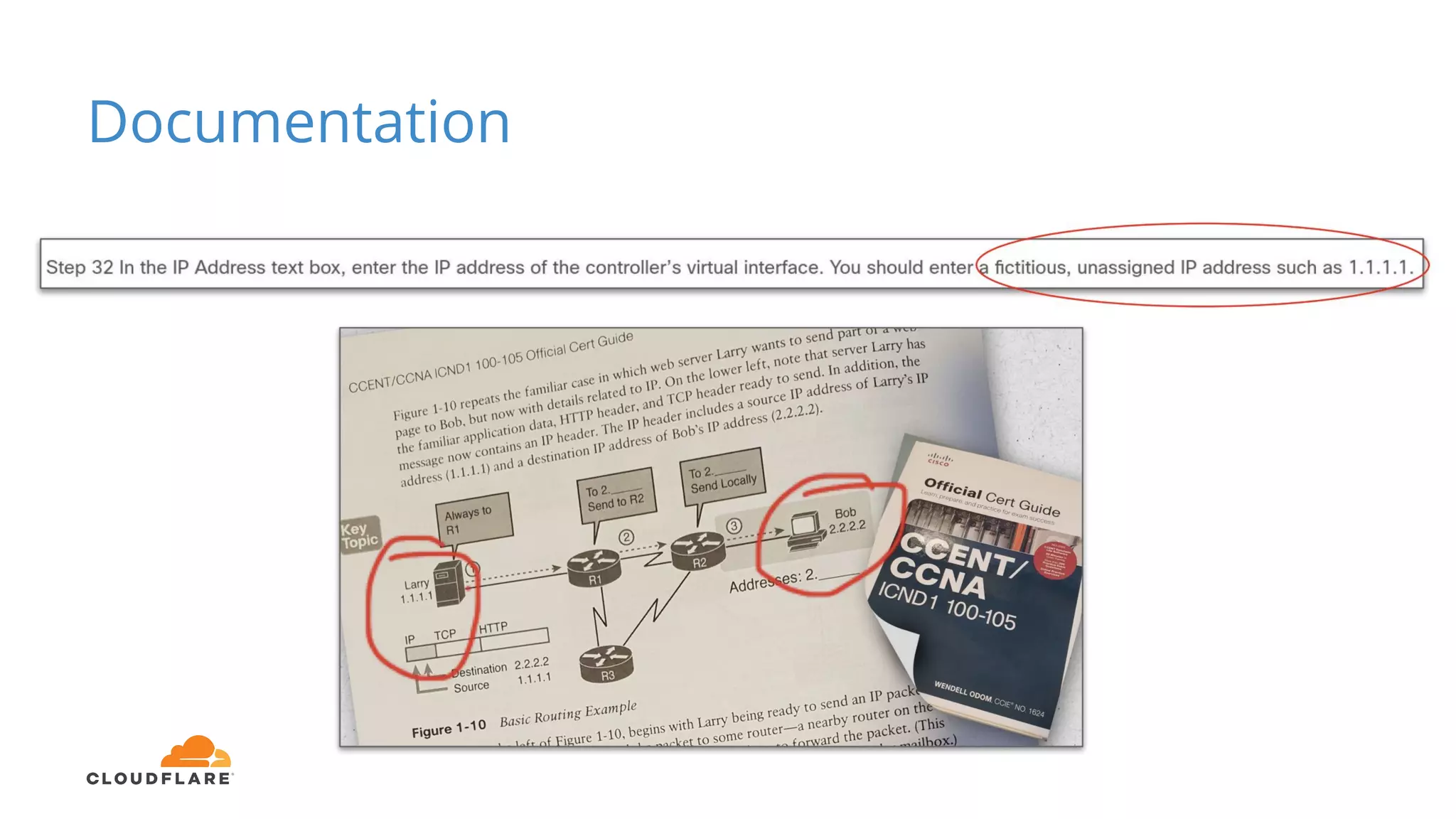
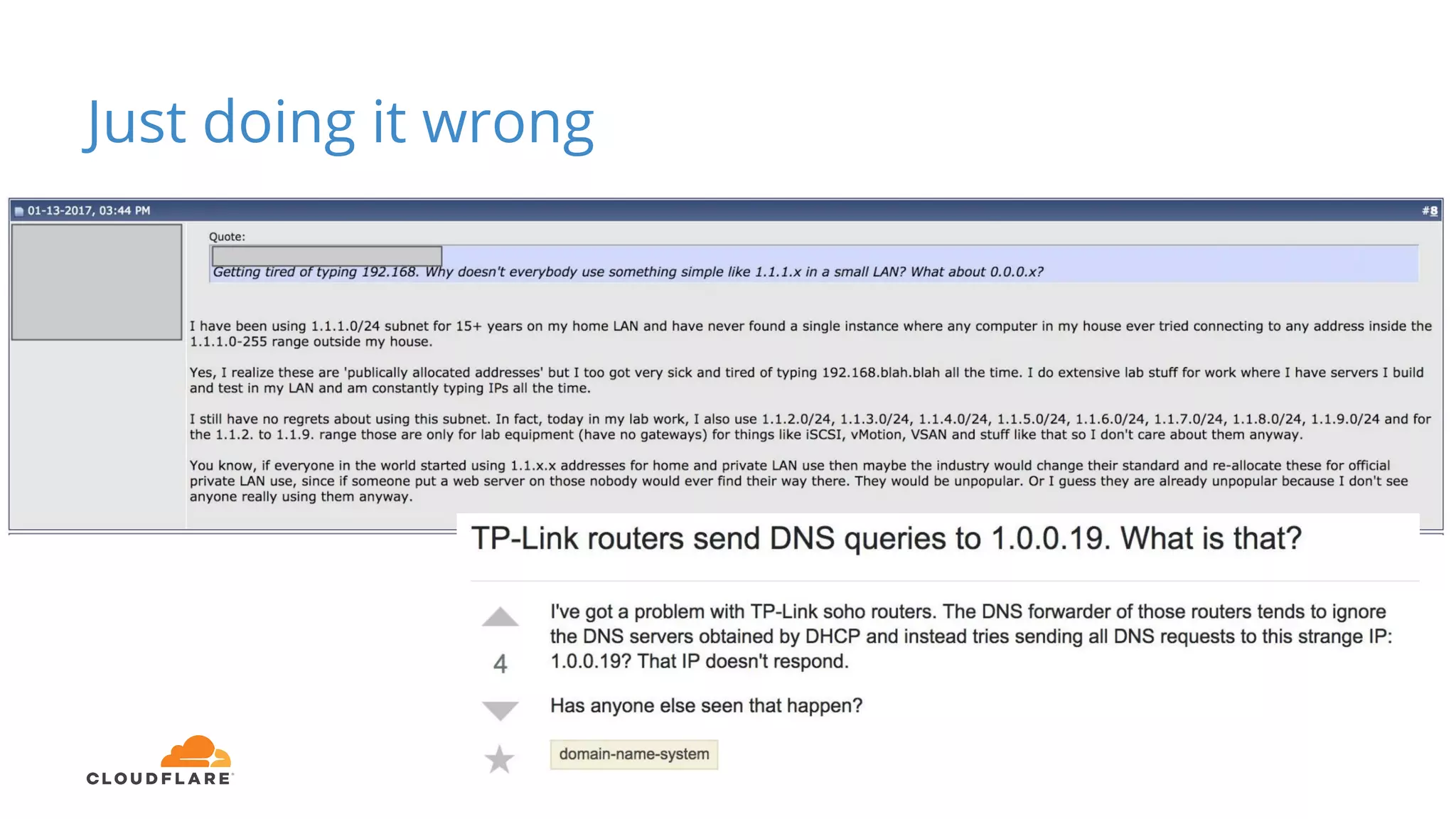
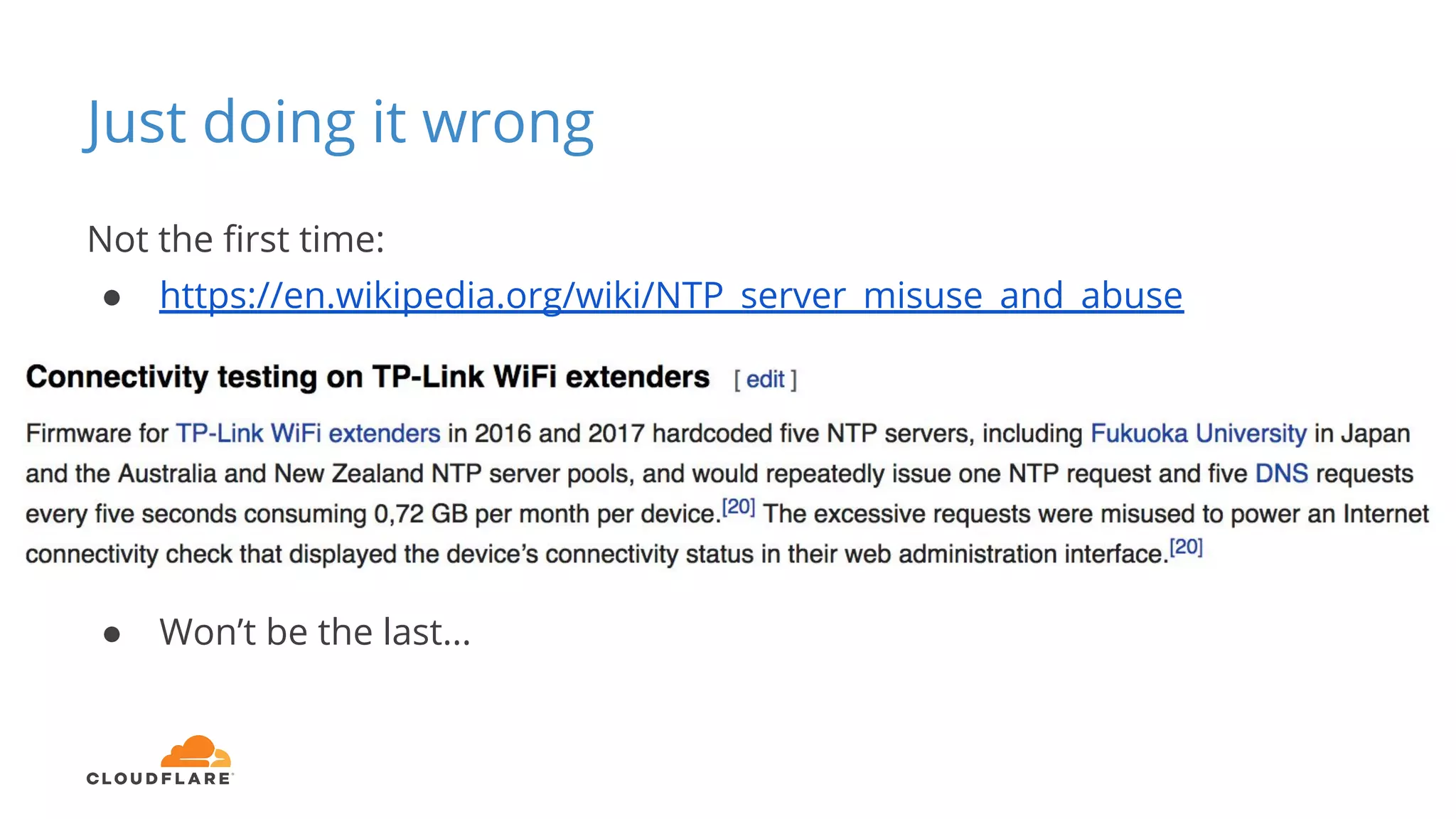
Tom Paseka from Cloudflare presented on internet noise received on the IP blocks 1.1.1.0/24 and 1.0.0.0/24. He discussed that these blocks receive unwanted traffic such as from misconfigurations and misuse. Traffic levels have increased to 8-13Gbps from previous studies. Legitimate traffic makes up an estimated 7-13% and includes DNS queries. Availability testing found issues with over 30 ISPs null routing or using the blocks internally. Documentation recommends blocks like 192.0.2.0/24 for examples but sometimes they are still misused.