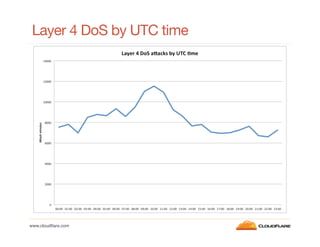
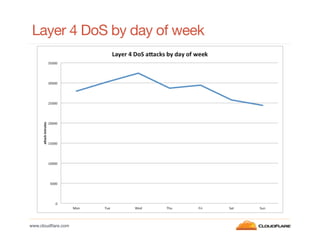
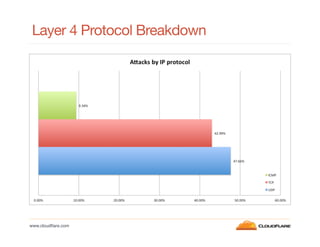
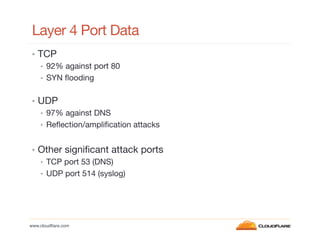
This document discusses internet background radiation and DDoS attacks seen by CloudFlare between January and July 2012. Some key points:
- CloudFlare sees 64 billion page views per month and the majority (95.5%) of DDoS attacks are layer 7. The largest attack was 65Gbps.
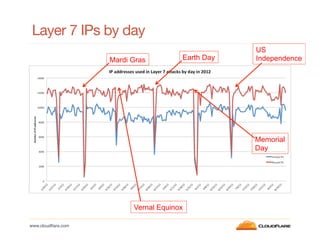
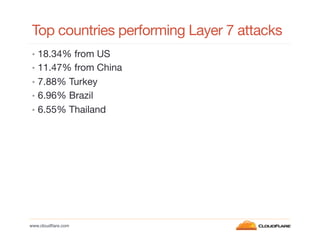
- Layer 4 attacks mainly target port 80 (TCP) and DNS (UDP), while layer 7 attacks originate from many different IPs but mostly the US, China, Turkey, Brazil and Thailand.
- Reflection and amplification attacks exploit protocols like DNS and SNMP to magnify small queries into large responses. Booter websites and botnets are also used to launch attacks.
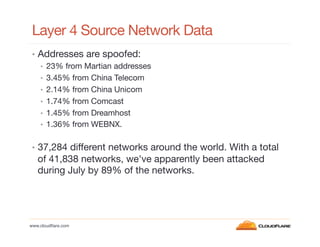
- Attacks are