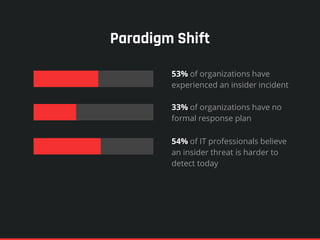
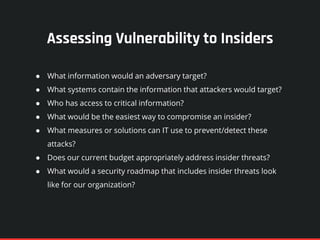
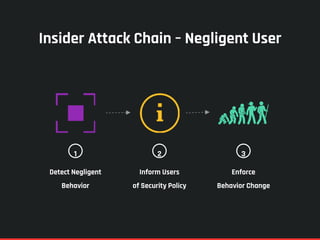
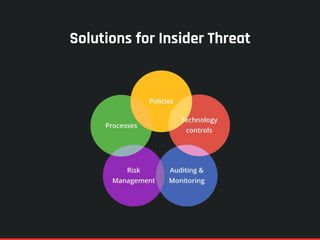
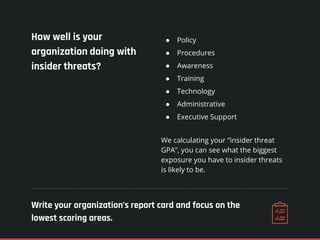
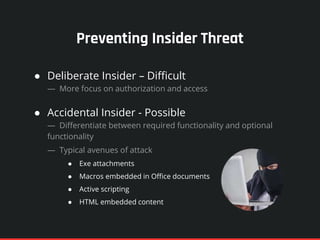
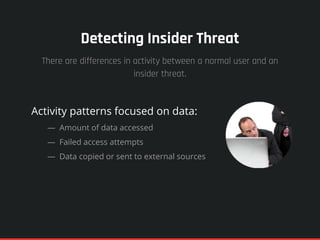
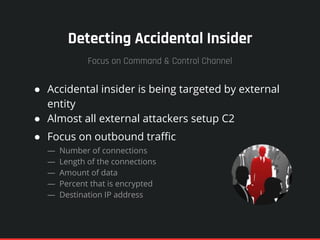
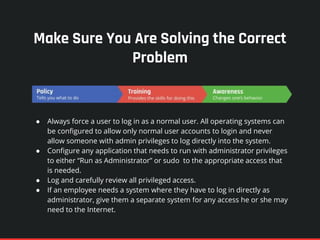
The document highlights the significance of insider threats, noting that a majority of organizations have faced such incidents without formal response plans in place. It outlines the two primary types of insider threats—deliberate/malicious and accidental—and emphasizes the need for comprehensive strategies to assess and mitigate these risks. Ultimately, it stresses the importance of proactive security measures, awareness training, and monitoring to protect against insider threats.