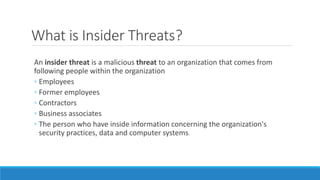
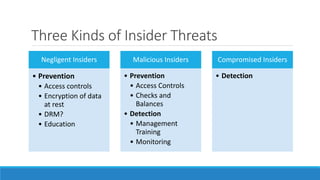
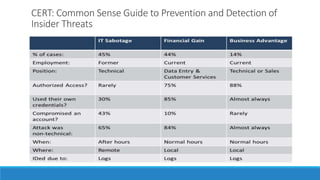
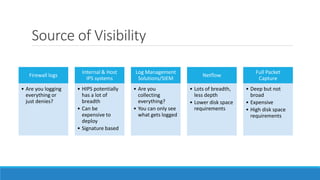
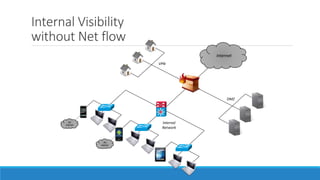
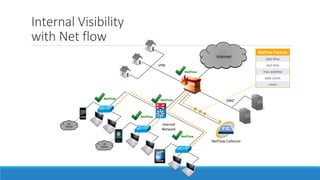
The document discusses insider threats, which are malicious risks to an organization posed by individuals within, including employees and contractors. It categorizes insider threats into negligent, malicious, and compromised insiders and outlines various measures for prevention and detection. The conclusion emphasizes the need for a multidisciplinary approach involving IT, HR, and legal considerations to effectively manage insider threats.