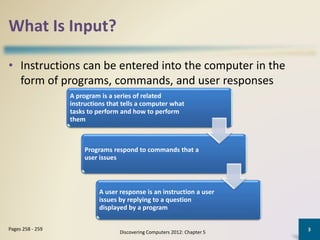
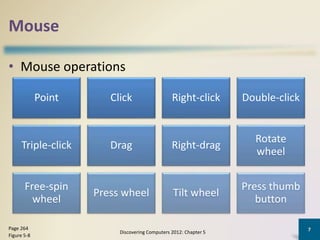
The document discusses different types of computer input, including data, instructions, programs, commands, and user responses. It describes several common input devices like the keyboard, mouse, touch screens, touch pads, and pen input. The keyboard allows users to enter text, the mouse is a pointing device controlled by hand movements, touch screens are touch-sensitive display screens, and pen input involves using a stylus to write or draw on a flat surface.