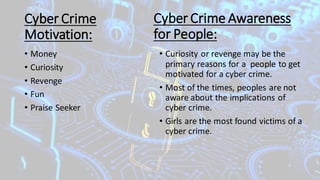
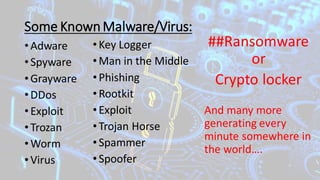
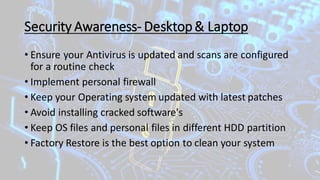
The document outlines a program aimed at educating employees about cybersecurity and the implications of using technology and the internet, emphasizing awareness and preventative measures against cyber threats. It discusses various types of cybercrime, motivations behind them, methods of spreading malware, and provides tips for online safety and security awareness. Additionally, it addresses the responsibilities of management, HR, and IT departments to enhance cybersecurity training and compliance within the organization.