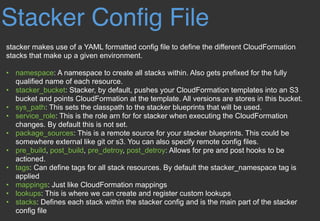
This document discusses using Stacker to deploy infrastructure as code using CloudFormation templates. Stacker allows defining CloudFormation stacks in a YAML configuration file and handles dependencies between stacks. It uses Troposphere to generate templates in Python code for reusability and testing. Stacker supports features like lookups, environments, outputs from other stacks, and stack orchestration for deploying infrastructure in AWS.







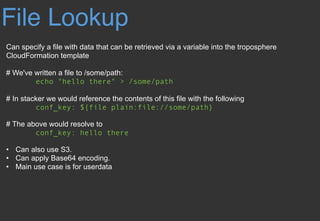
![DynamoDB Lookup
Can a value within a DynamoDB table as a stacker variable value. The syntax also allows you
to traverse through the item map
# We can reference that dynamo value:
BucketName: ${dynamodb
us-east-1:TestTable@TestKey:TestVal.BucketName}
# Which would resolve to:
DBUser: stacker-test-bucket
# Valid type values are:
“S”(String), “N”(Number), “M”(Map), “L”(List).
# We can reference keys within a DynamoDB item map
ServerCount: ${dynamodb
us-east-1:TestTable@TestKey:TestVal.ServerInfo[M]
.ServerCount[N]}](https://image.slidesharecdn.com/infrastructureascodedeployedusingstacker-180329051839/85/Infrastructure-as-code-deployed-using-Stacker-17-320.jpg)
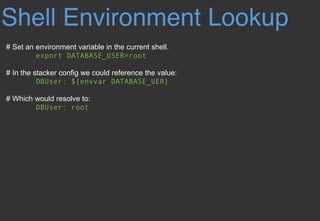
![EC2 AMI Lookup
# In the stacker config we could reference the latest ami of the following region, owner,
name_regex and other filter values:
ImageId: ${ami [<region>@]owners:self,888888888888,amazon
name_regex:server[0-9]+ architecture:i386}
Hook Data Lookup
# When using hooks, you can have the hook store results in the hook_data dictionary on the
context by setting data_key in the hook config. This allows you to lookup the data_key values.
Code: ${hook_data myfunction::TheCode}
Custom Lookup
# This allows you to create and register your custom lookup.](https://image.slidesharecdn.com/infrastructureascodedeployedusingstacker-180329051839/85/Infrastructure-as-code-deployed-using-Stacker-19-320.jpg)

