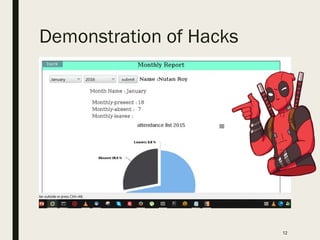
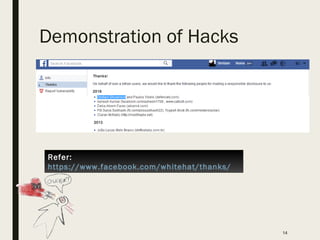
The document outlines the professional background and expertise of Shritam Bhowmick in information security, focusing on various domains such as application security, network security, and infrastructure security. It provides insights into his roles in penetration testing, security assessments, and threat intelligence along with a detailed agenda that includes demonstrations of hacks and security advisories. Additionally, it emphasizes the importance of ethical practices in handling security vulnerabilities and maintaining client confidentiality.