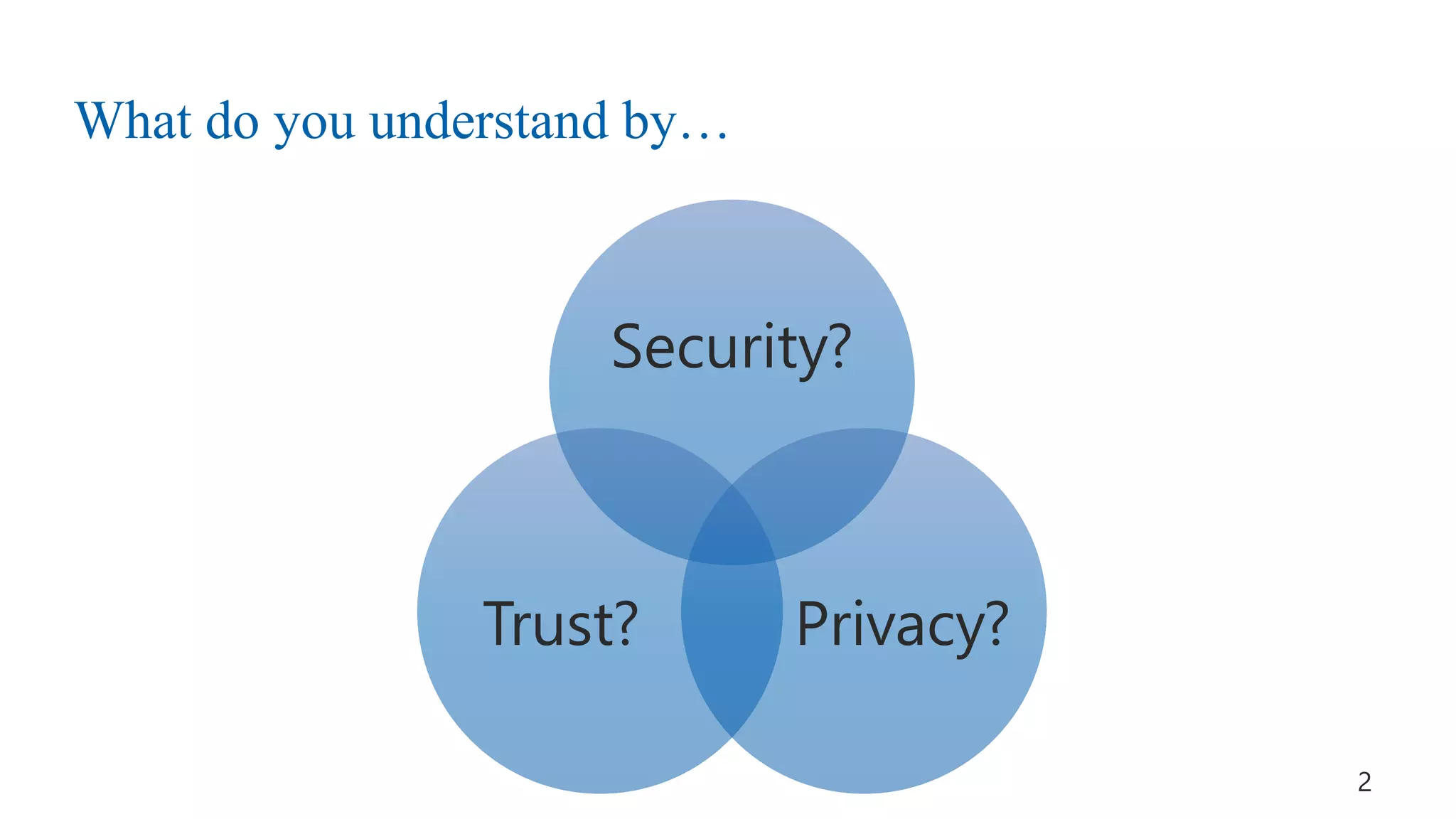
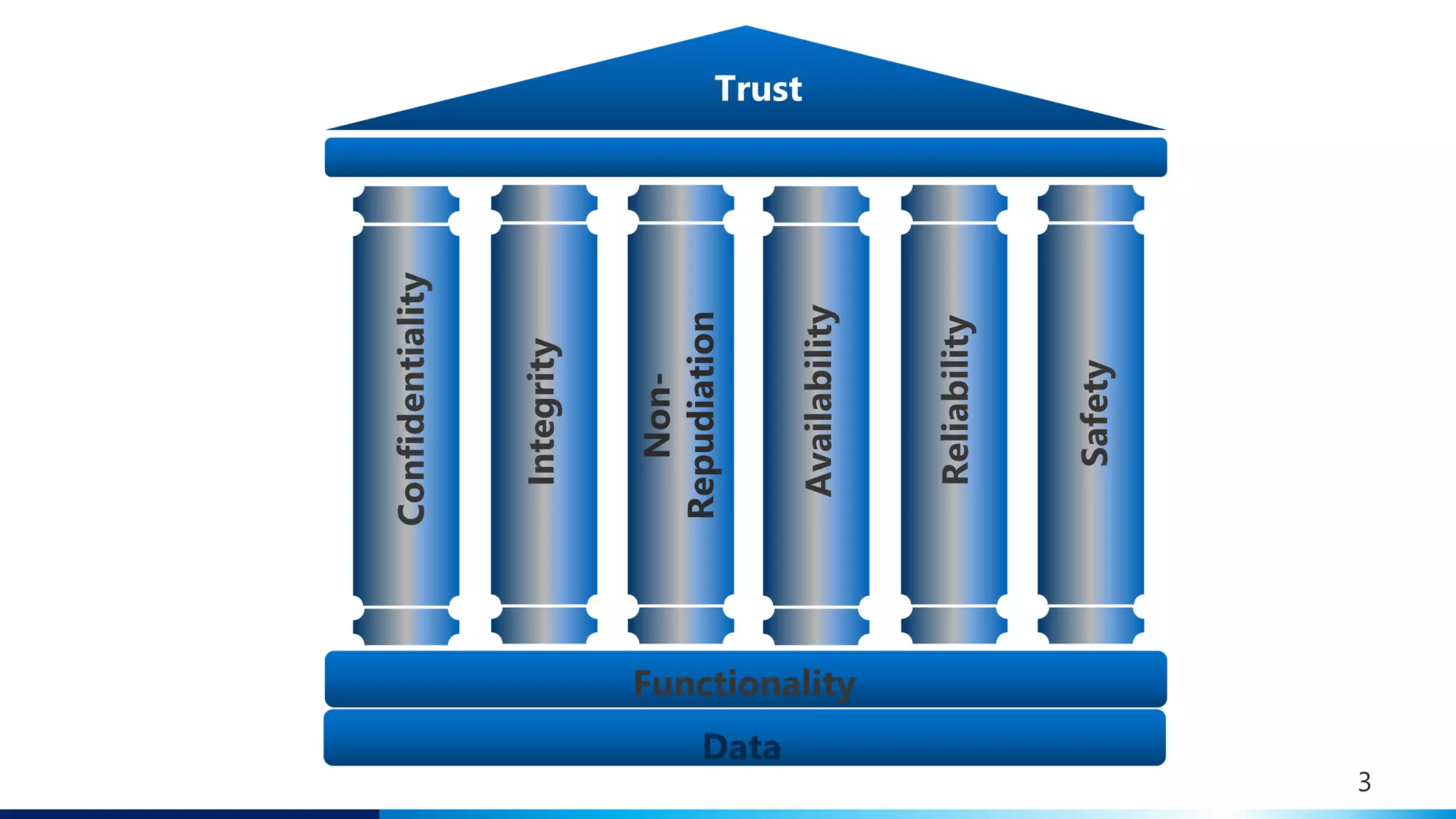
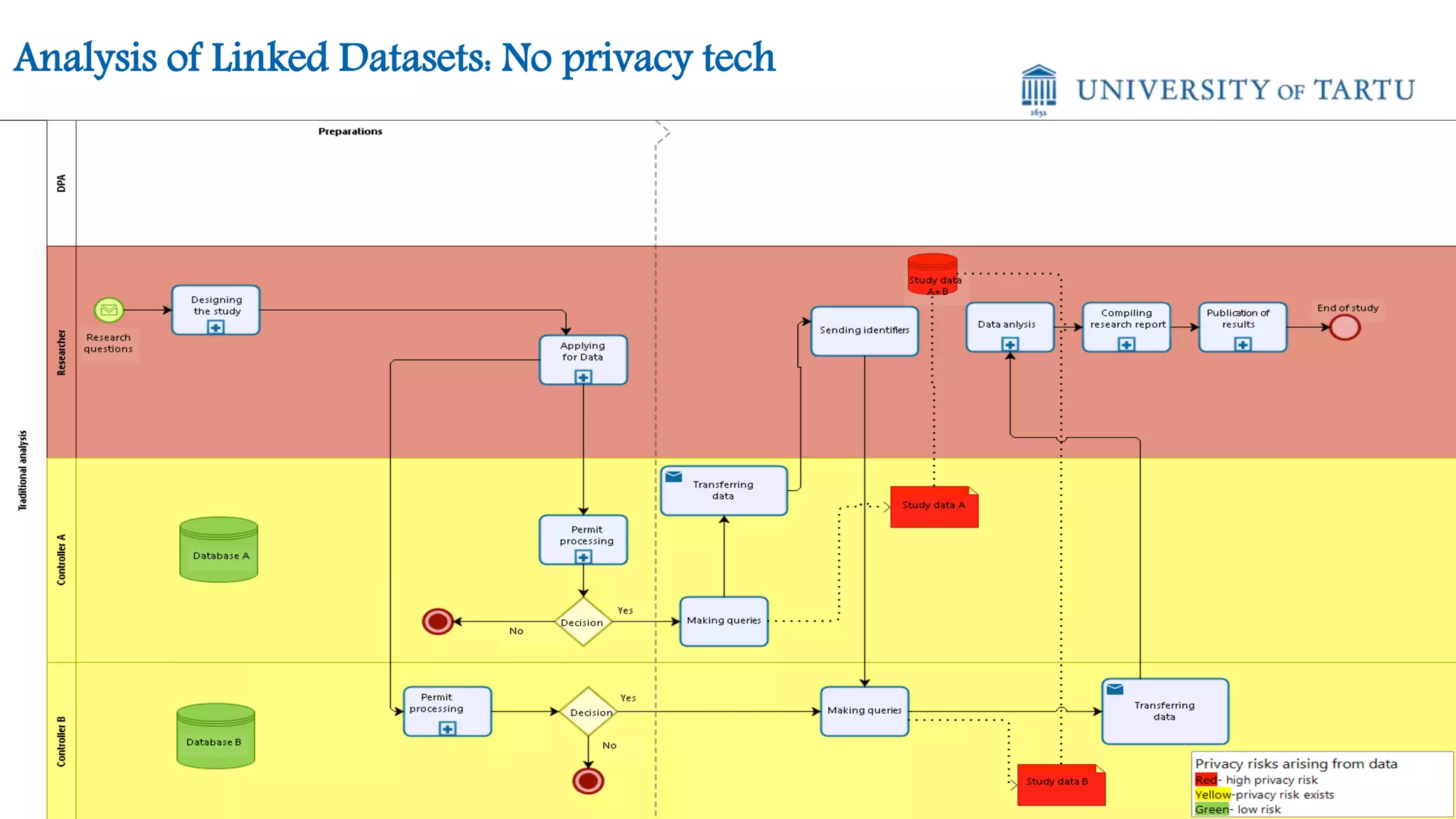
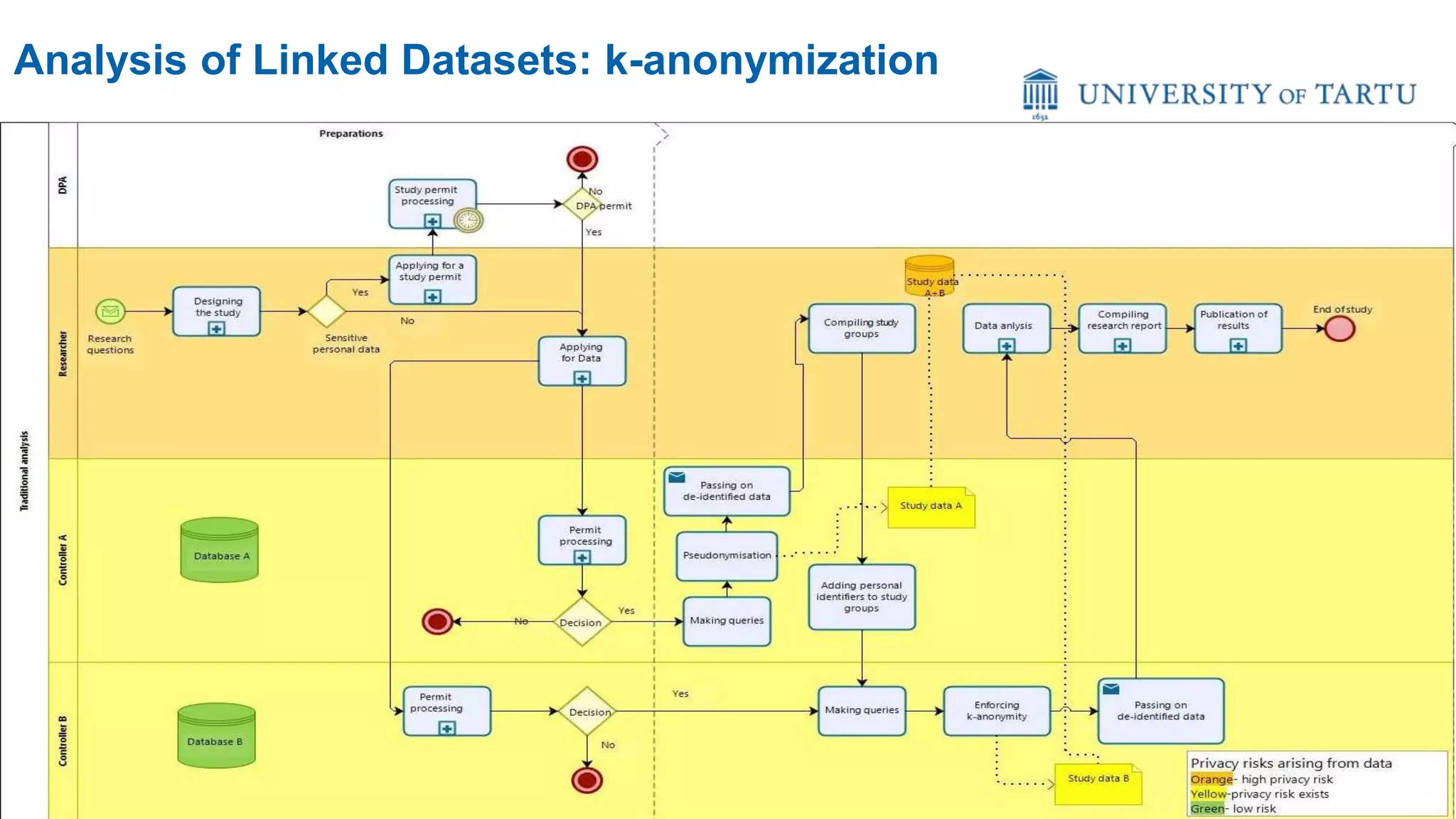
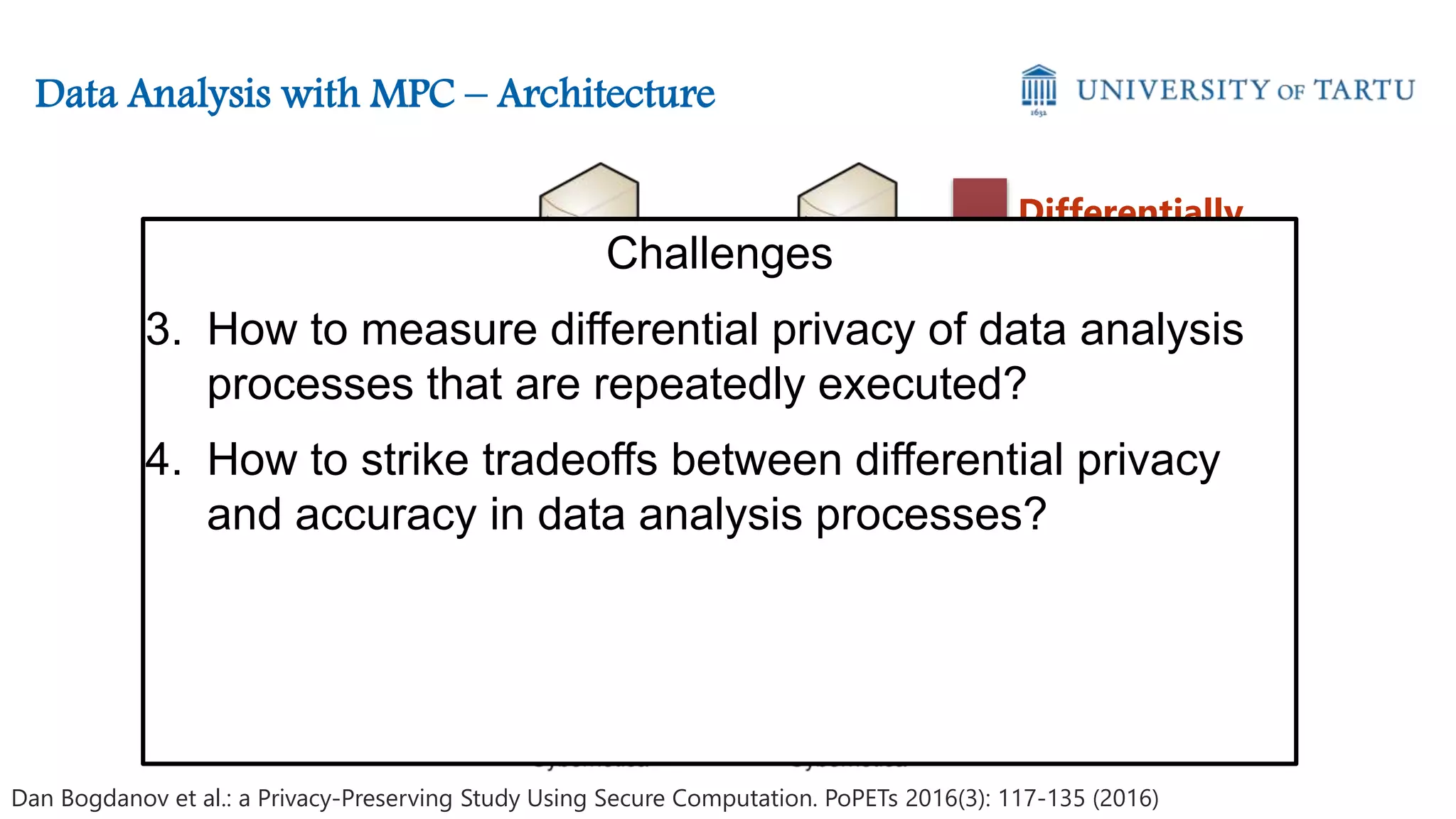
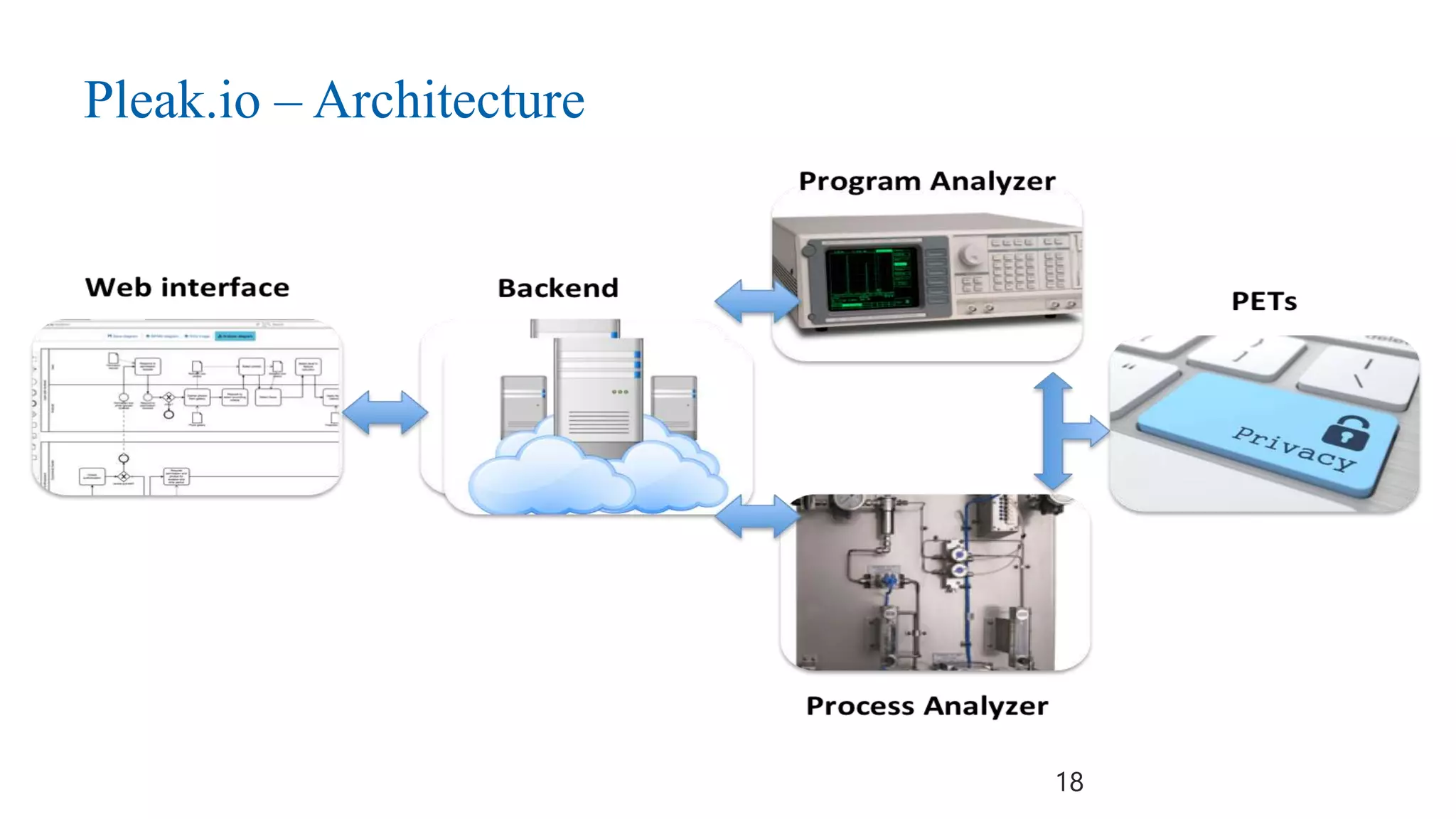
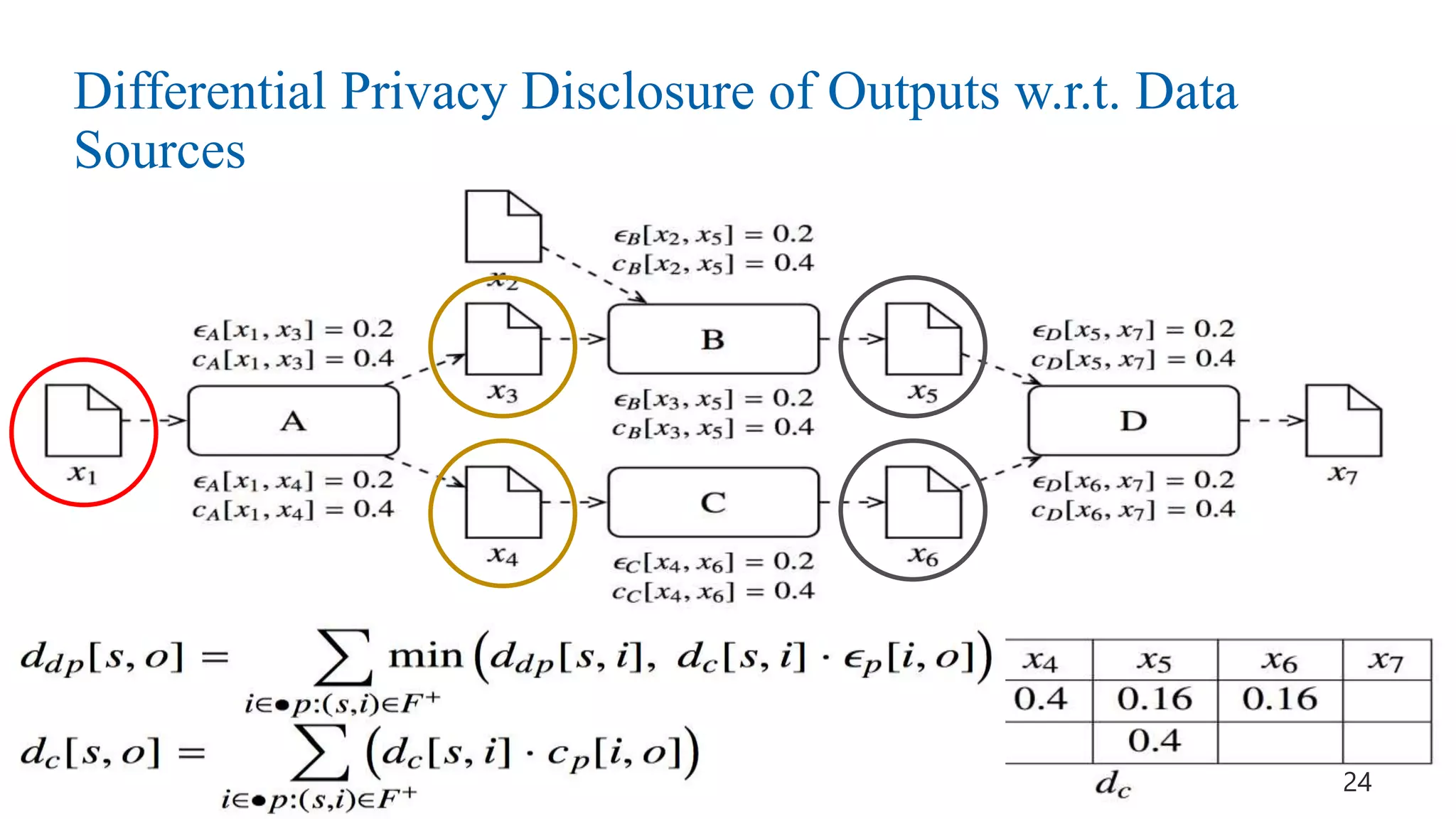
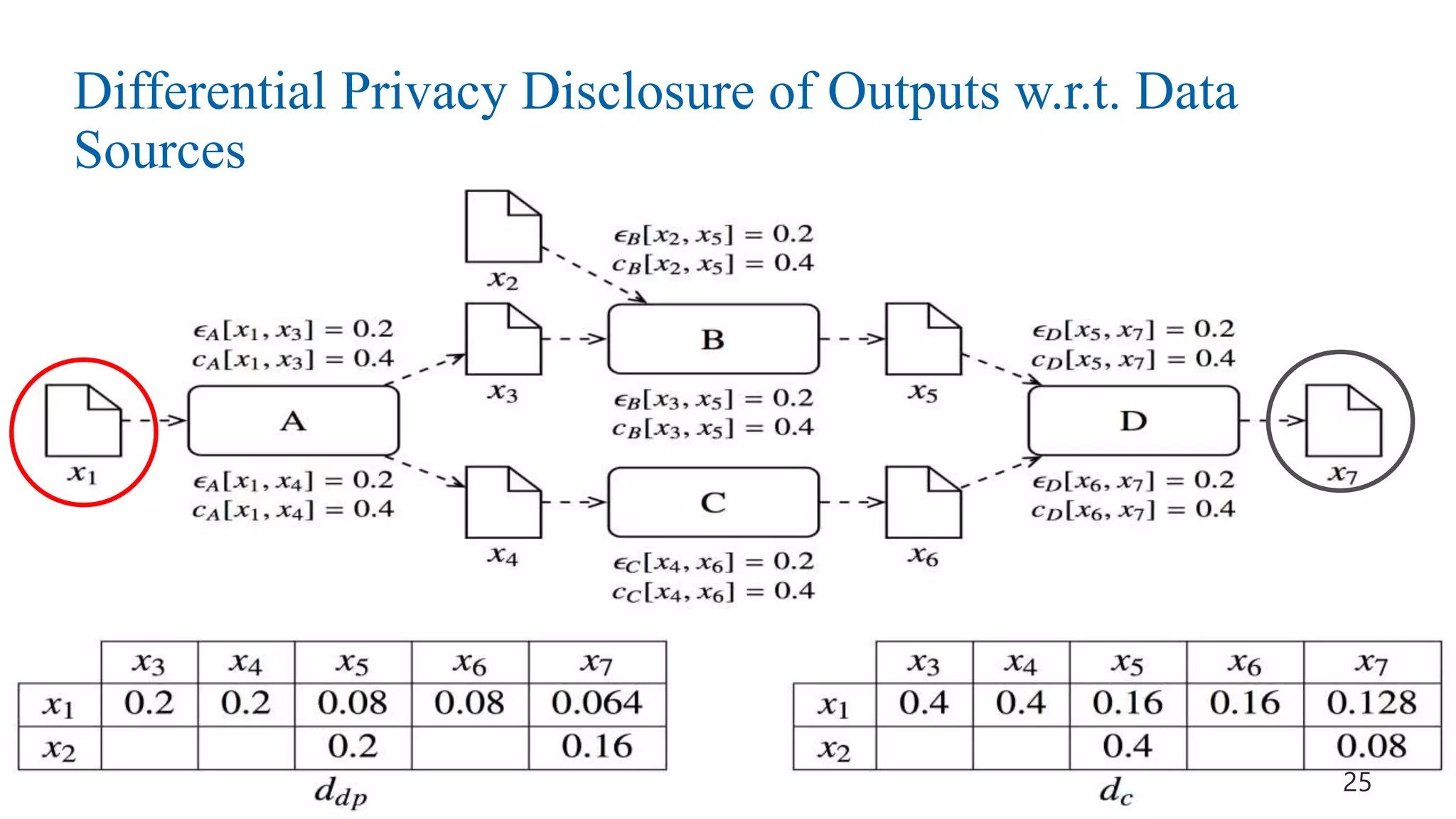
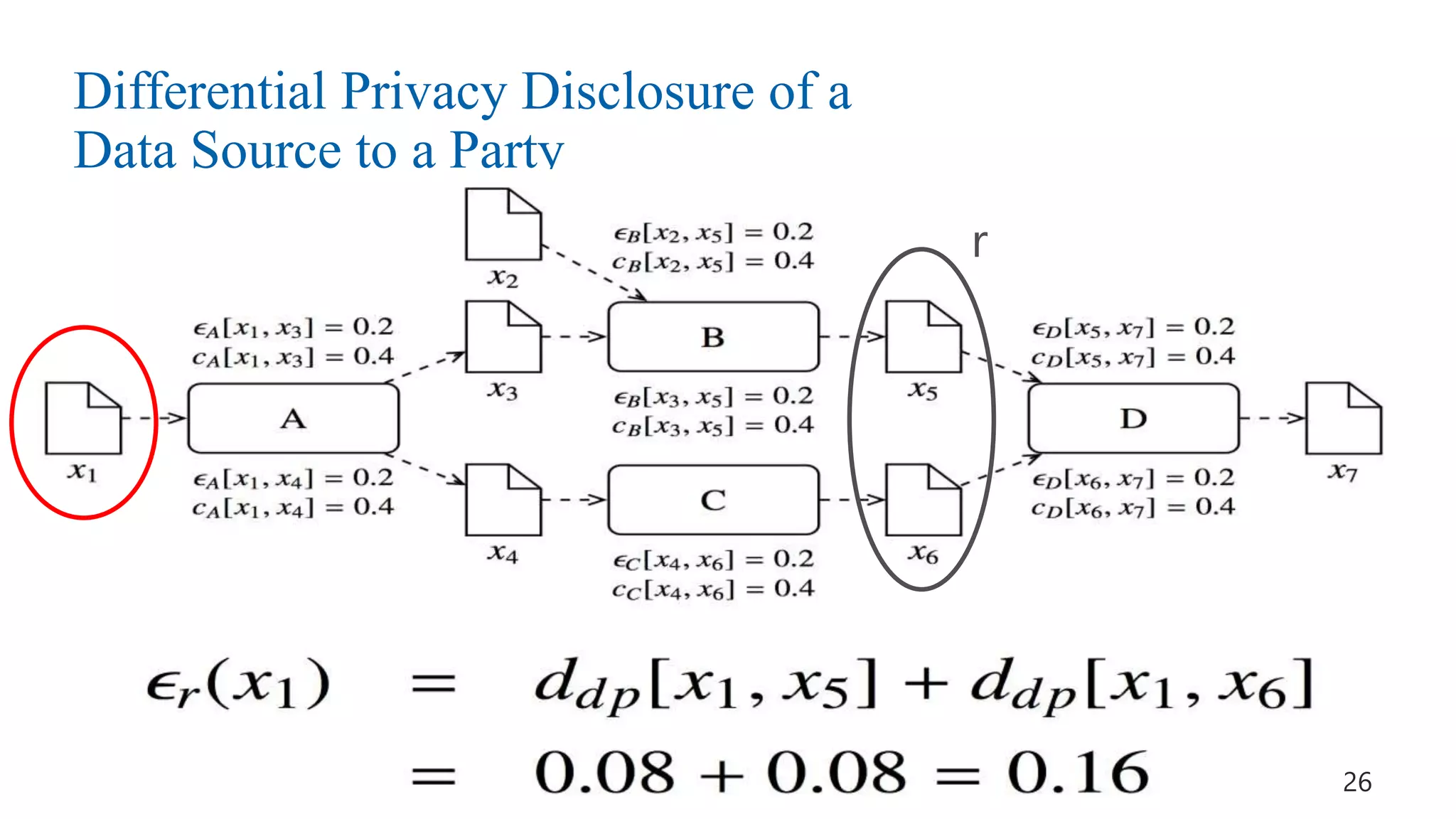
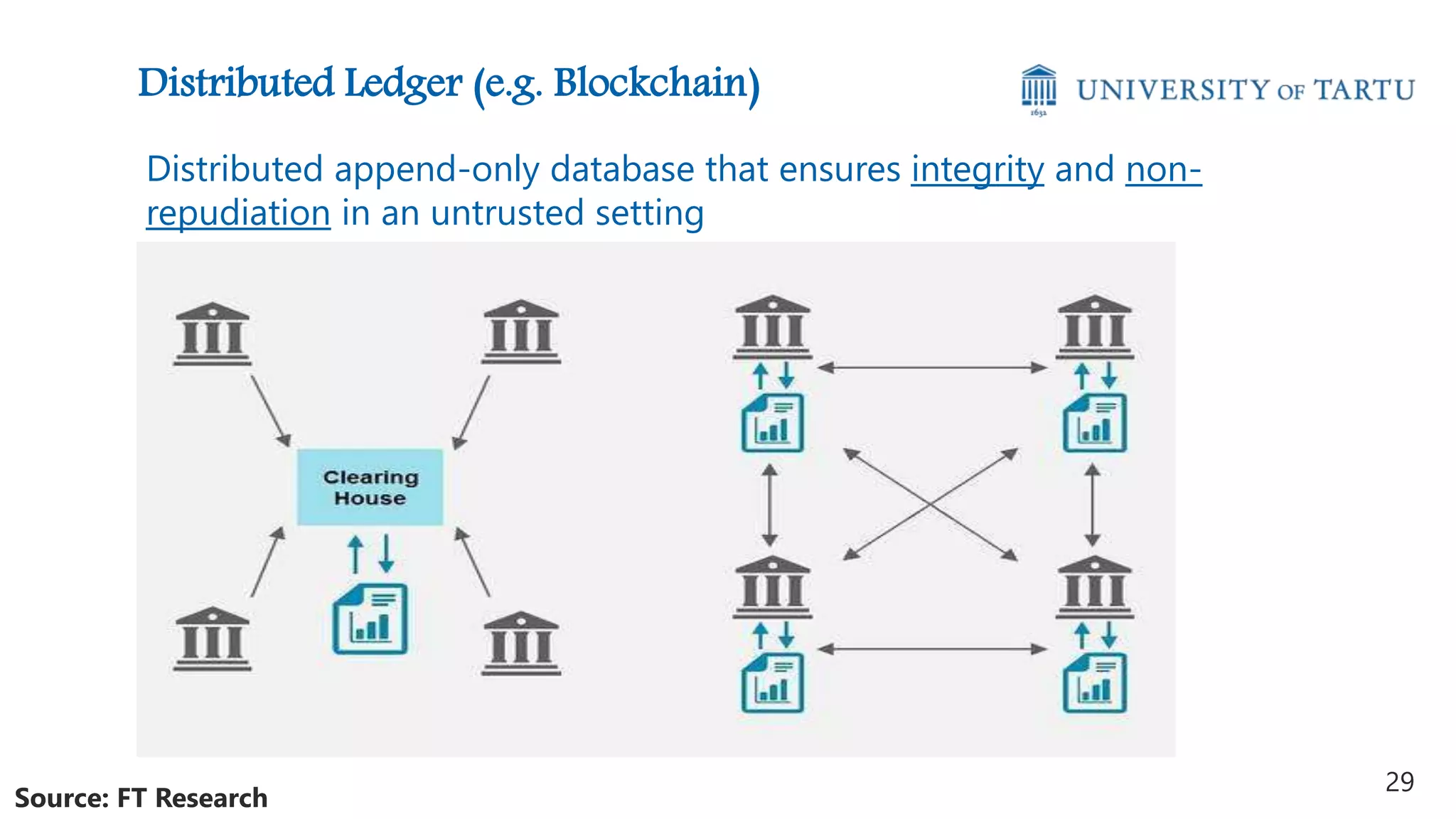
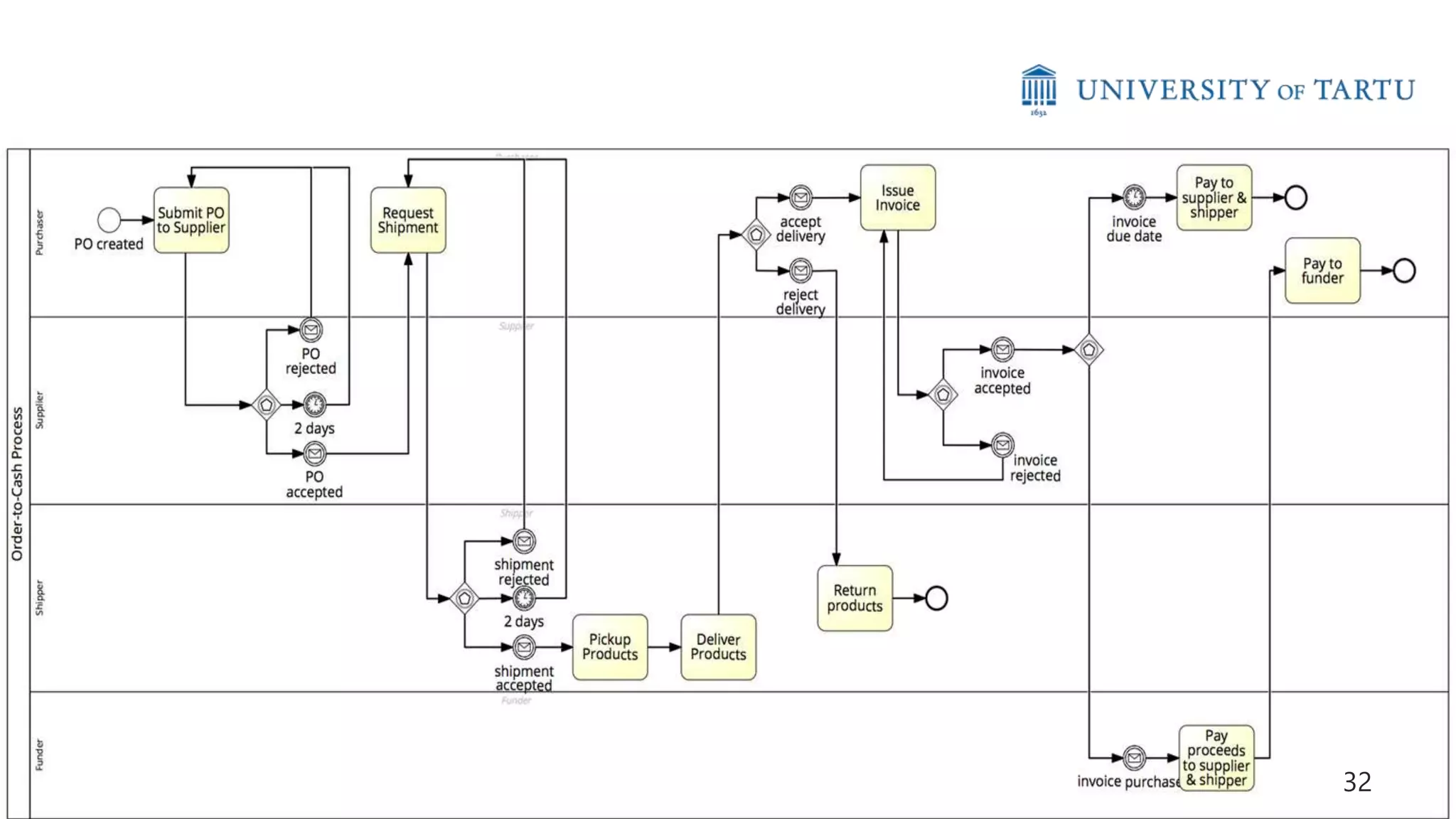
This document discusses challenges and opportunities around privacy and trust in business processes. It begins by defining key concepts like security, privacy, and trust. It then outlines topics related to business process security and privacy, such as access control, flow analysis to detect unauthorized data access, and privacy-aware business process execution. The document proposes approaches for privacy-aware business processes using techniques like k-anonymization and multi-party computation. It describes a system called Pleak.io that aims to model stakeholders, data flows, and privacy-enhancing technologies to quantify privacy leaks and accuracy loss in processes. The document concludes by discussing challenges around collaborative processes with untrusted parties and the potential use of distributed ledgers and smart contracts to address issues of




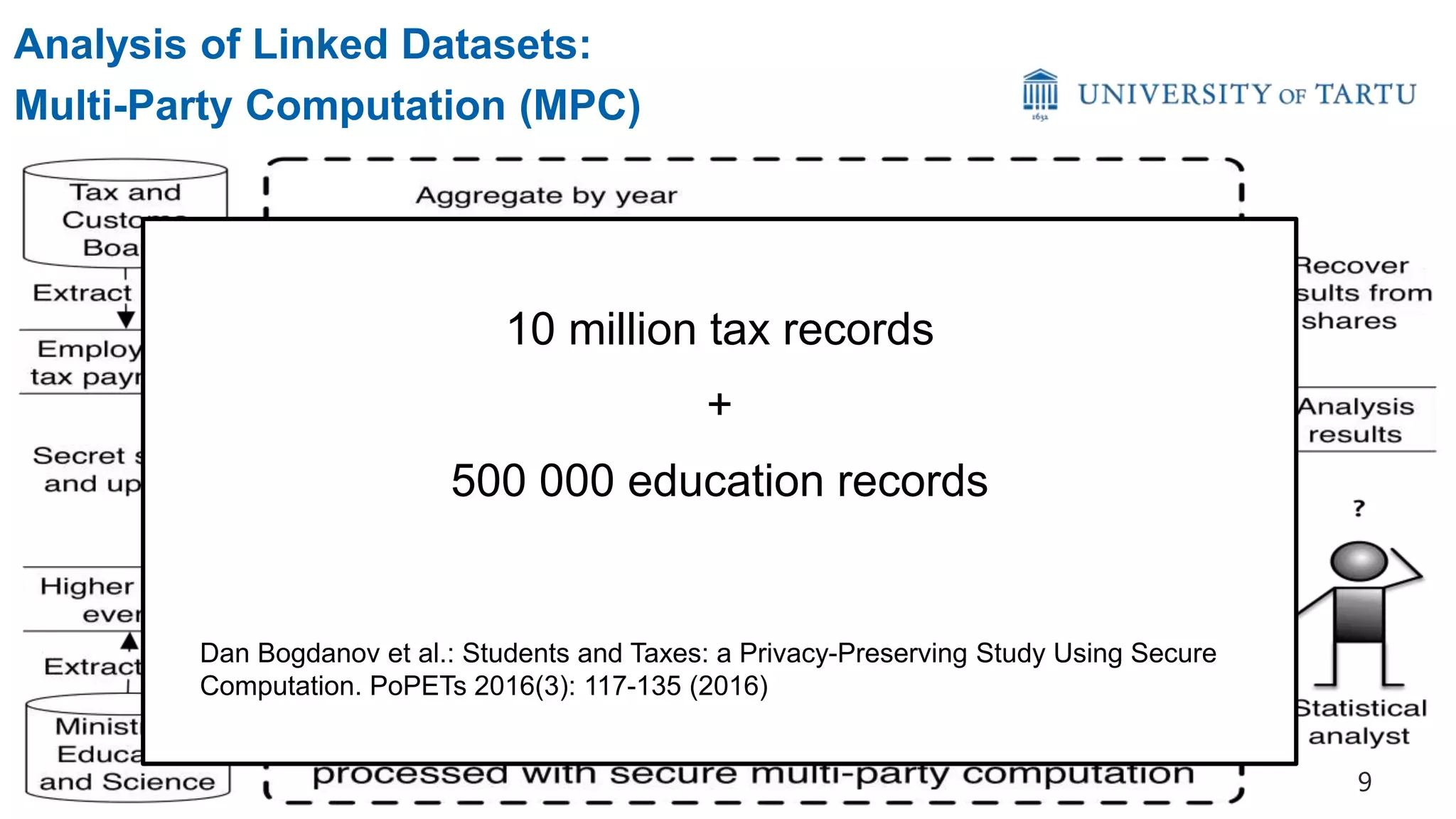
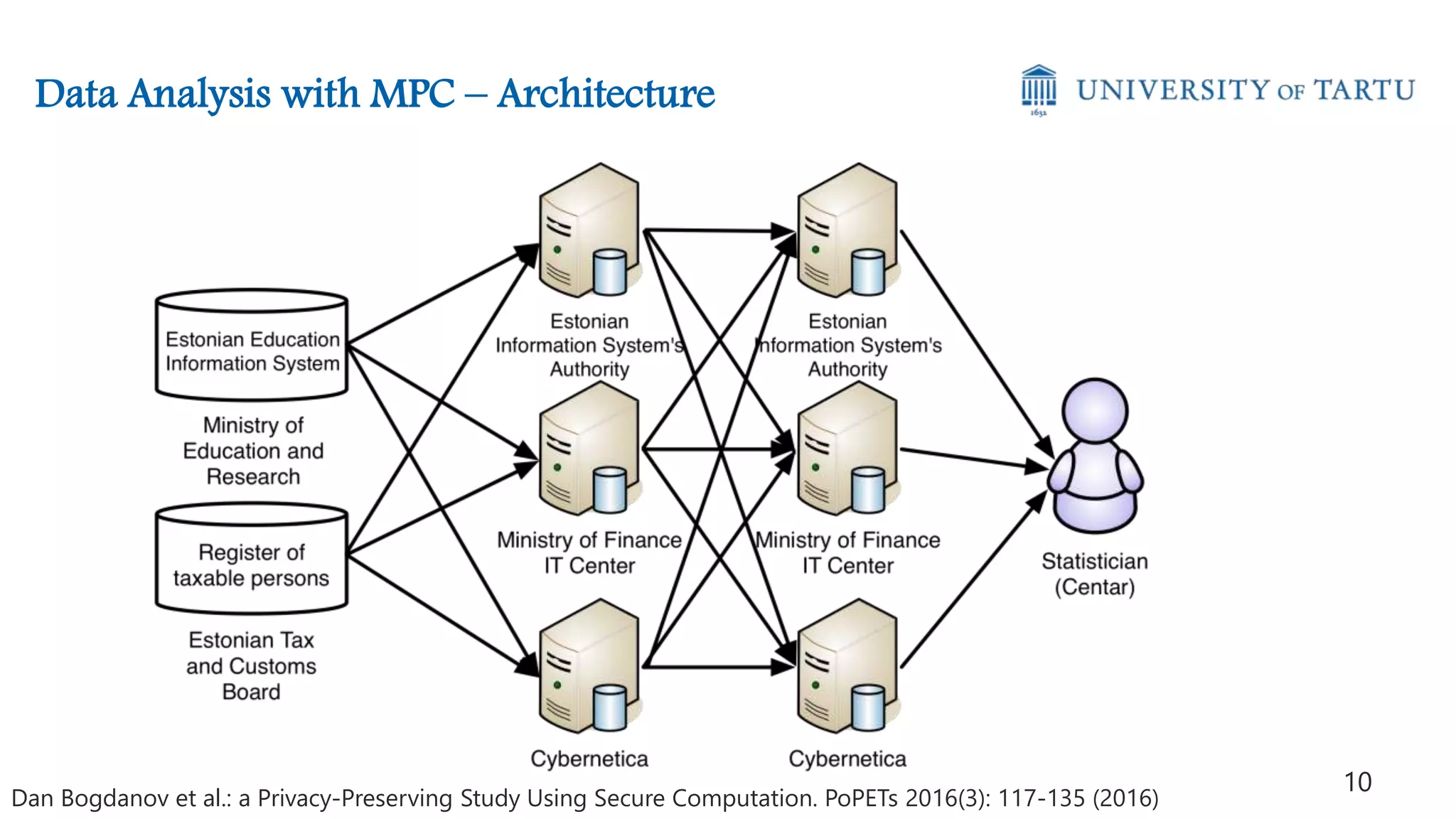
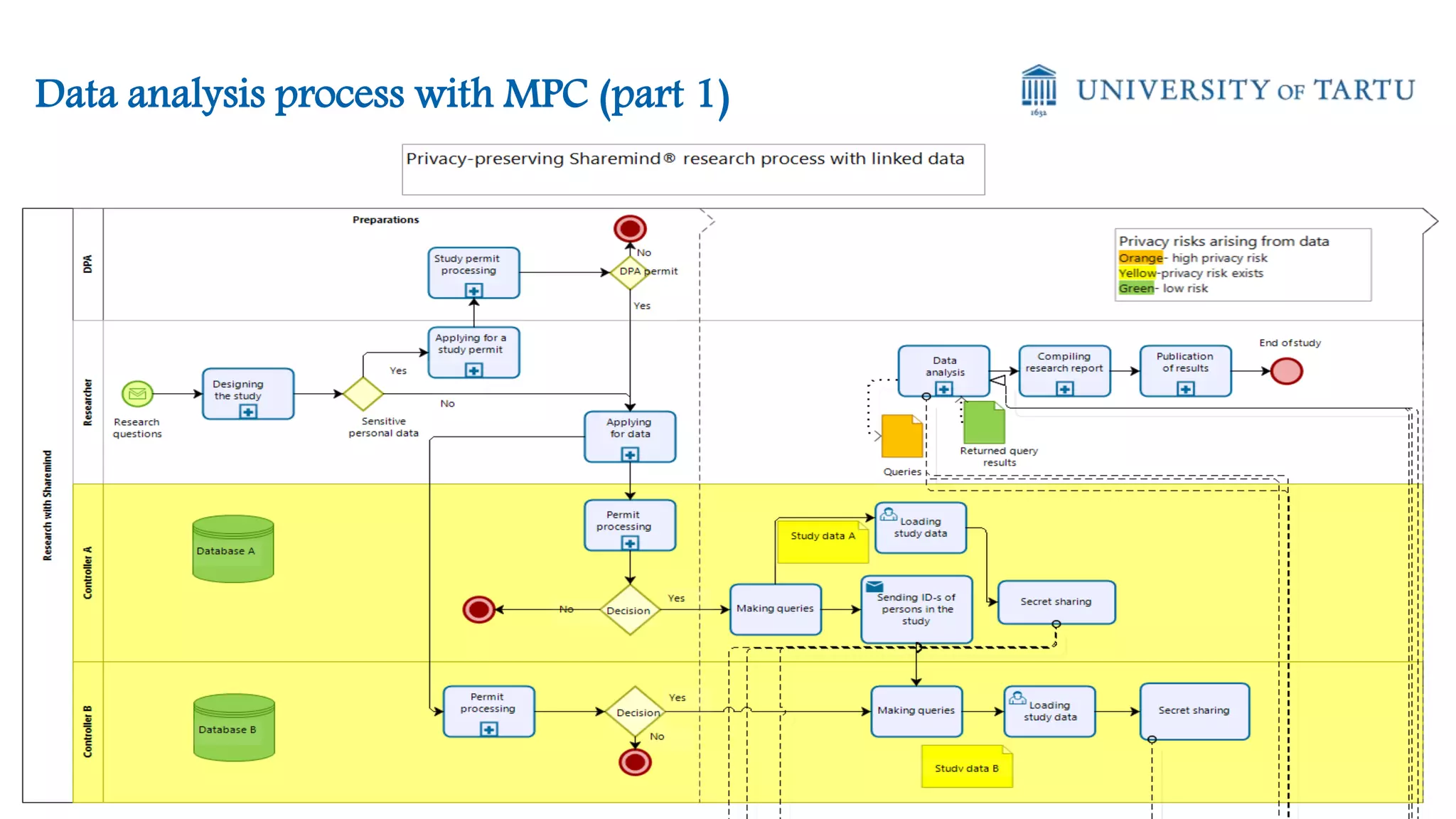
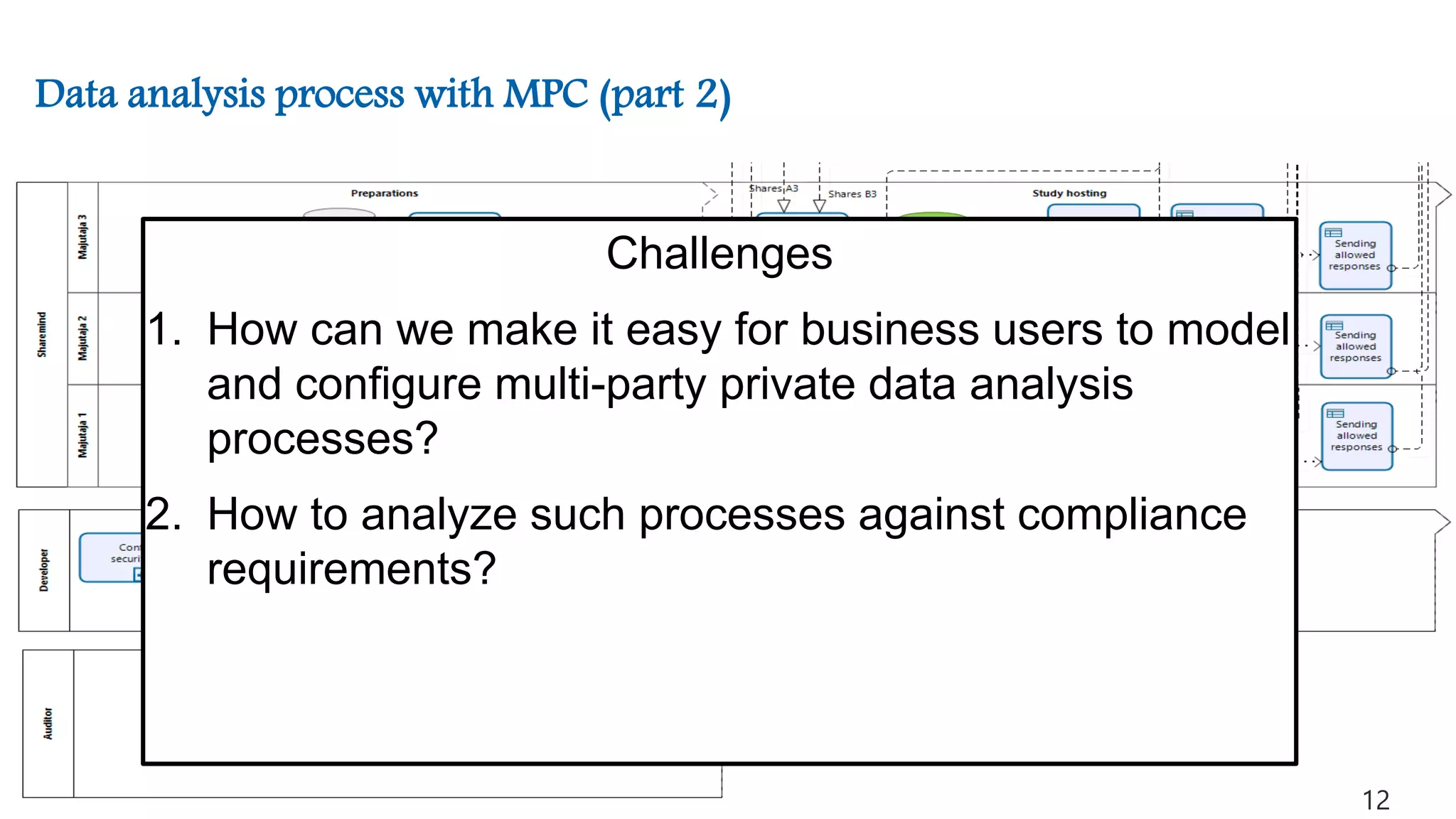

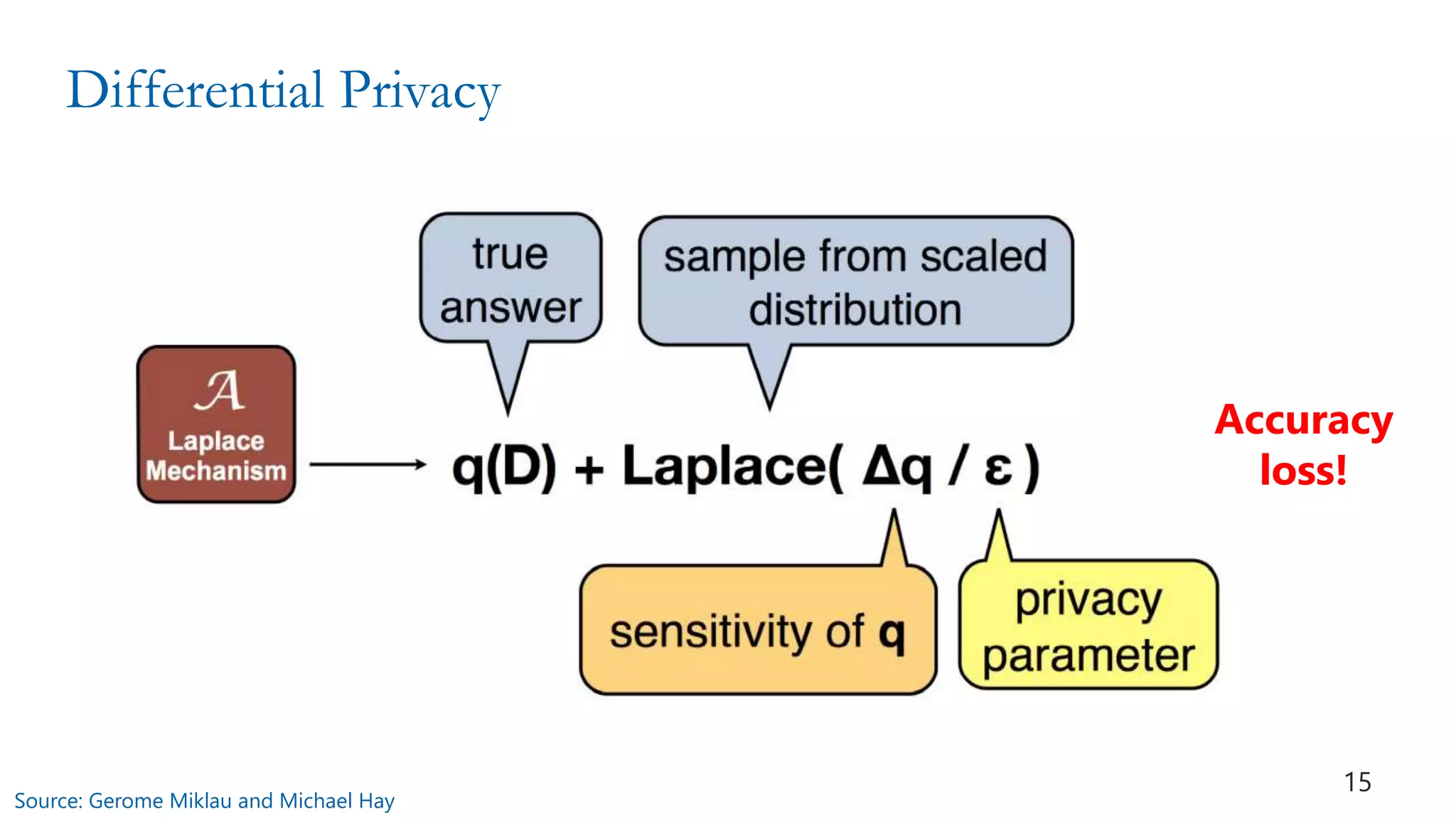
![Differential Privacy (Dwork 2006)
K gives e-differential privacy if for all values of DB, DB’
differing in a single element, and all S in Range(K )
Pr[ K (DB) in S]
Pr[ K (DB’) in S]
≤ eε ~ (1+ε)
ratio bounded
Pr [t]
14](https://image.slidesharecdn.com/processprivacy-berlin-june2016-160609102455/75/In-Processes-We-Trust-Privacy-and-Trust-in-Business-Processes-14-2048.jpg)

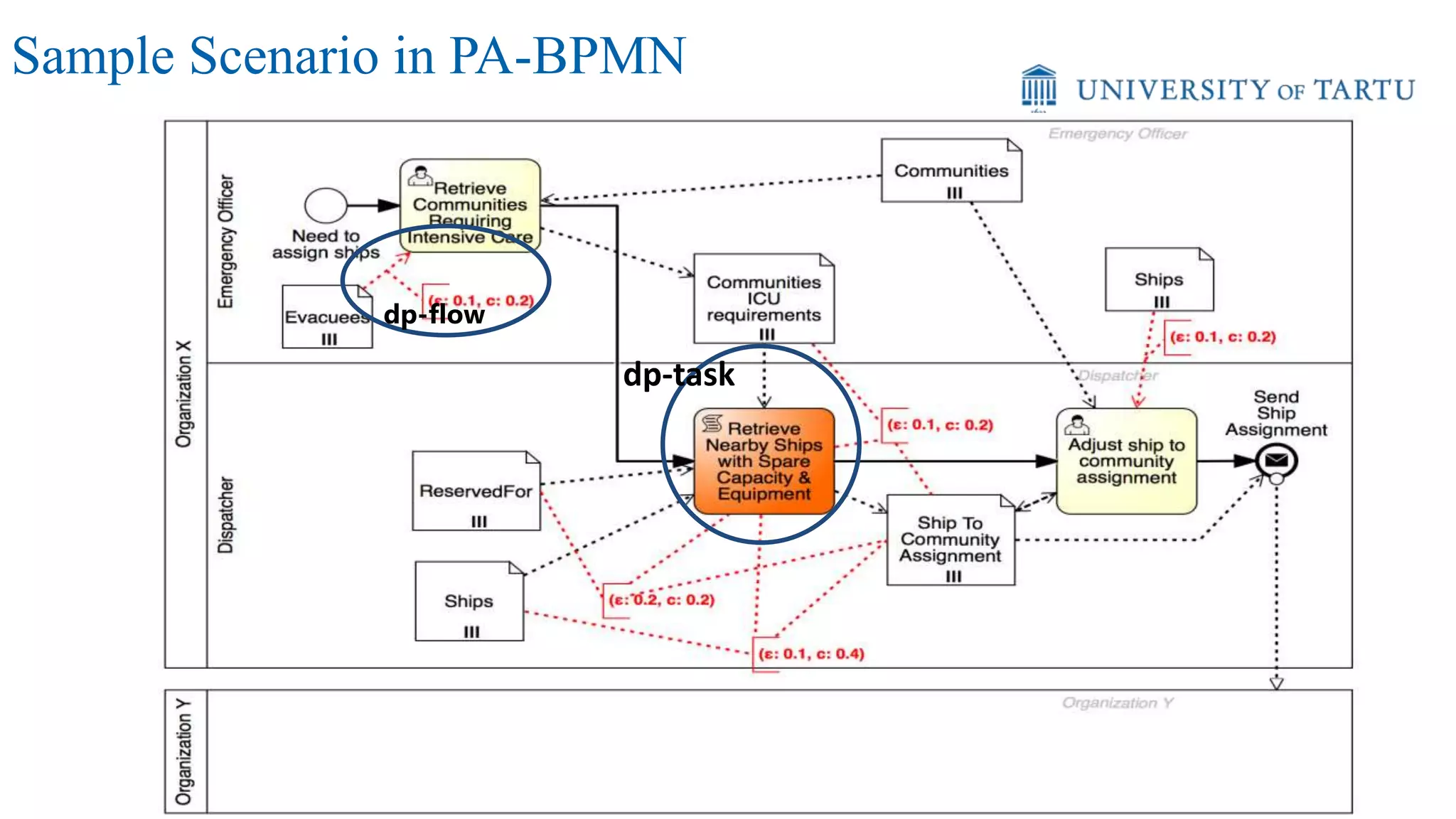
![(ships, disaster) -> {
avail_food = 0;
avail_ships = [];
for (ship in ships) do {
fuzzed_loc = ship.loc() + Lap2
(3);
if (dist(fuzzed_loc, disaster.loc()) / ship.speed() <= 2
&& ship.cargo_type() == "food"
&& !ship.contains(dangerous_materials) ) {
avail_food += ship.cargo();
avail_ships.append({ship.name(), fuzzed_loc});
}
}
avail_food += Lap(2);
return (avail_food, avail_ships);
}](https://image.slidesharecdn.com/processprivacy-berlin-june2016-160609102455/75/In-Processes-We-Trust-Privacy-and-Trust-in-Business-Processes-27-2048.jpg)






![Reference(s)
[1] Dan Bogdanov et al.: Students and Taxes: a Privacy-Preserving Study Using
Secure Computation. PoPETs 2016(3):117-135, 2016
[2] Marlon Dumas, Luciano Garcia-Banuelos, Peeter Laud: Differential Privacy of
Data Processing Workflows. In Proc. of GraMSec’2016
[3] Ingo Weber, Xiwei Xu, Regis Riveret, Guido Governatori, Alexander
Ponomarev, Jan Mendling. Untrusted Business Process Monitoring and Execution
Using Blockchain. In Proc. of BPM’2016
37](https://image.slidesharecdn.com/processprivacy-berlin-june2016-160609102455/75/In-Processes-We-Trust-Privacy-and-Trust-in-Business-Processes-37-2048.jpg)
