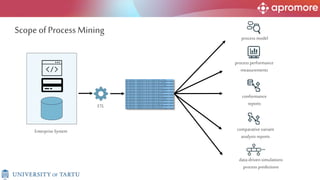
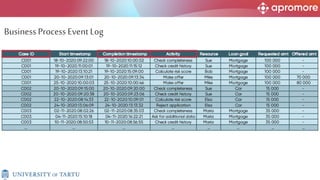
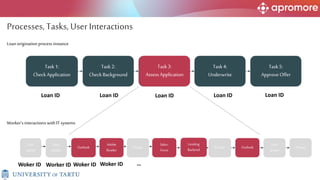
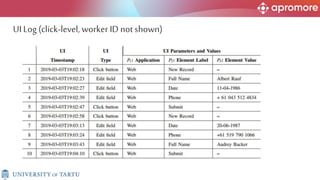
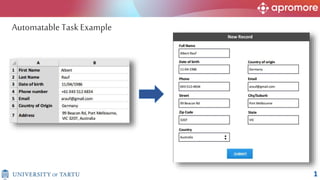
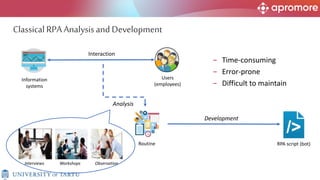
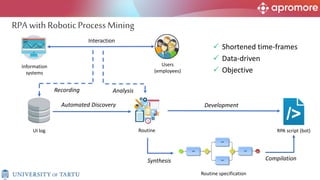
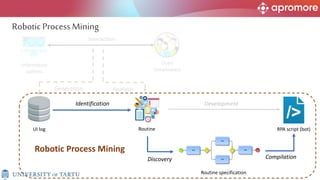
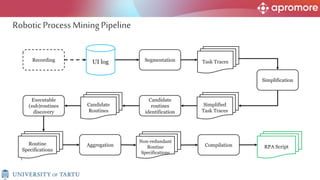
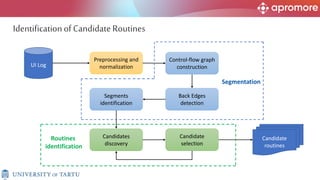
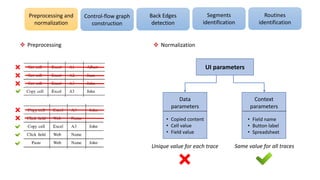
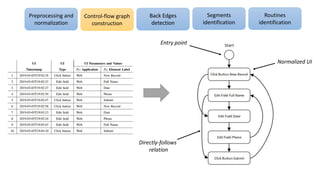
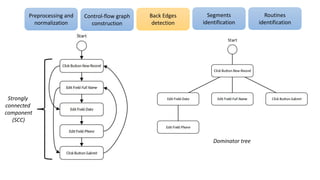
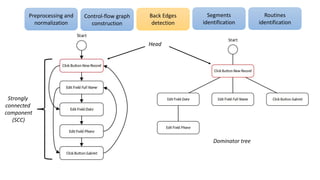
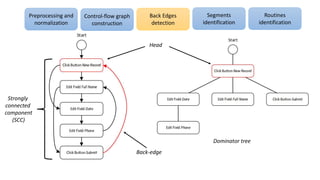
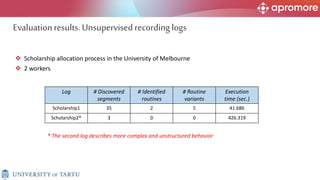
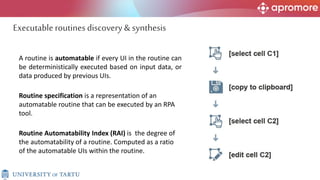
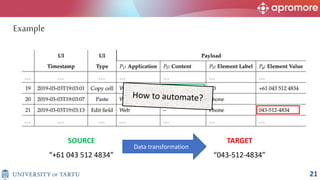
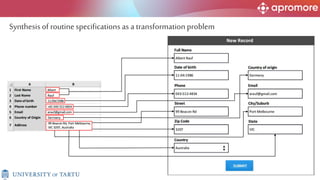
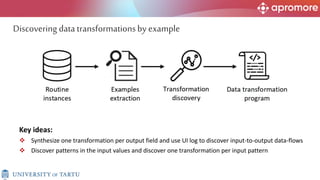
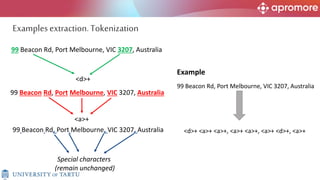
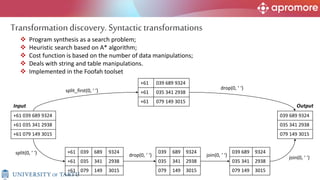
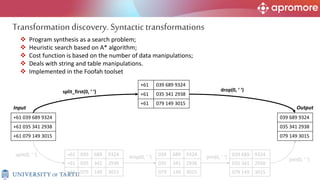
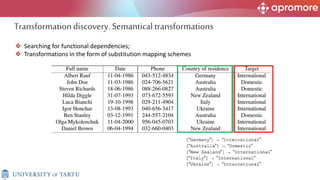
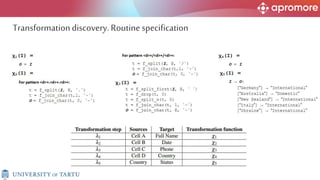
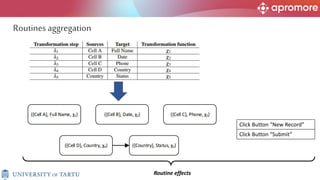
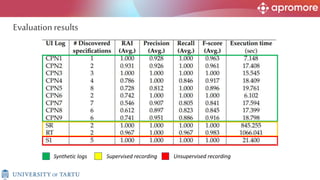
The document discusses applications of process mining in robotic process automation (RPA), emphasizing methods to analyze user interaction logs for task mining. It outlines techniques for segmenting UI logs and discovering automatable routines, aiming to optimize performance and compliance of business processes. The research addresses challenges in identifying and synthesizing routines suitable for automation and highlights the importance of data-driven approaches in RPA implementation.