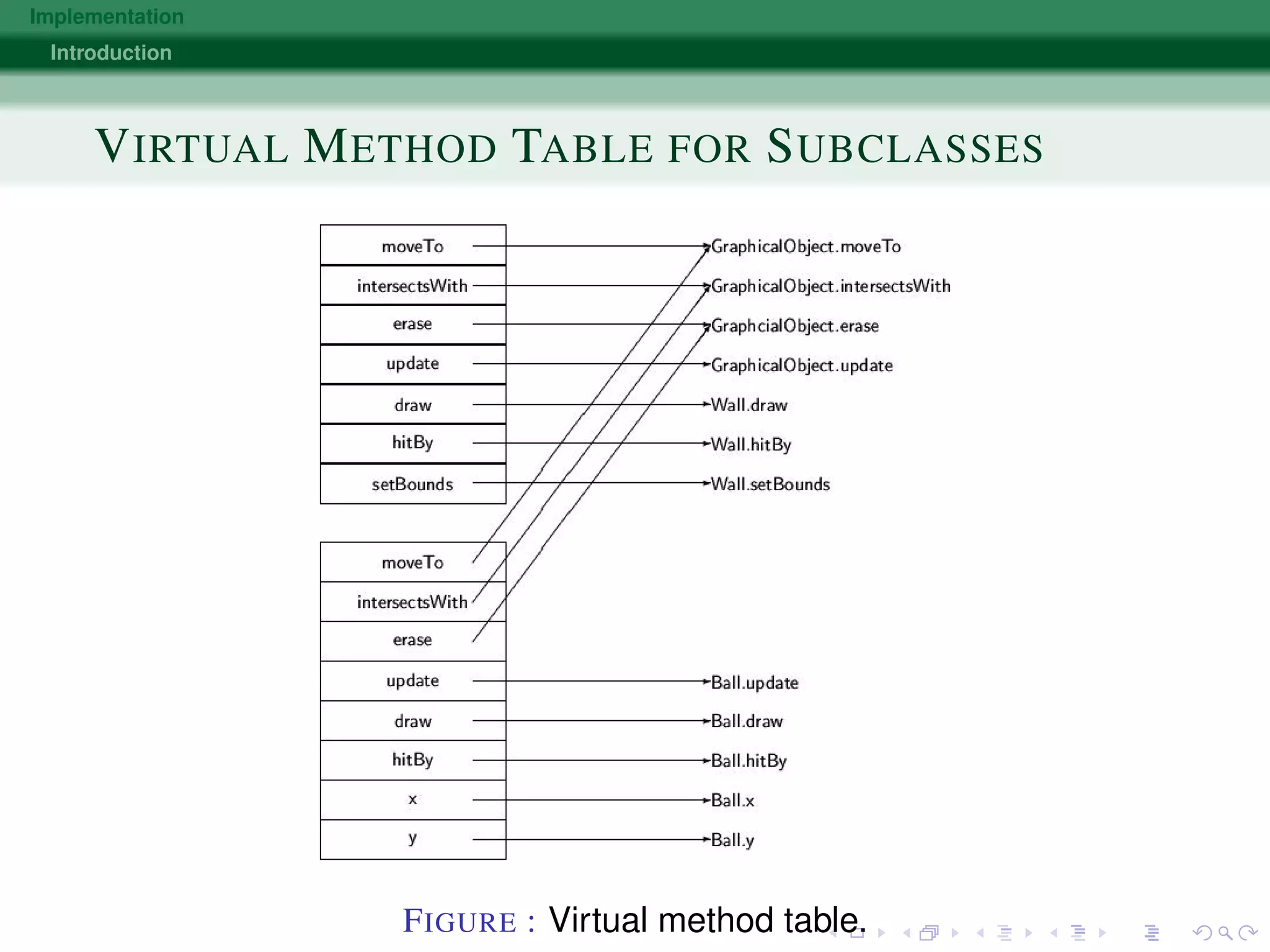
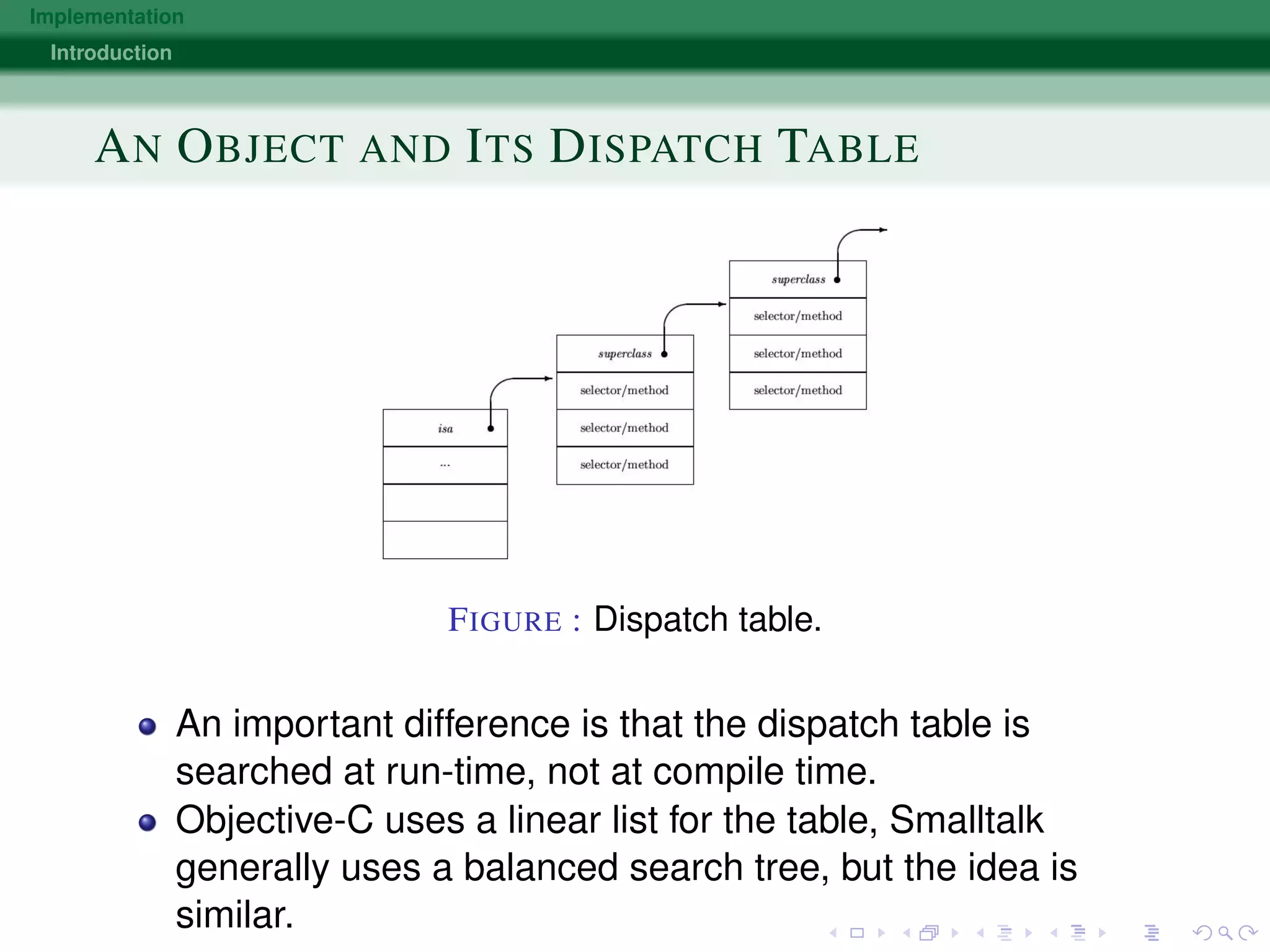
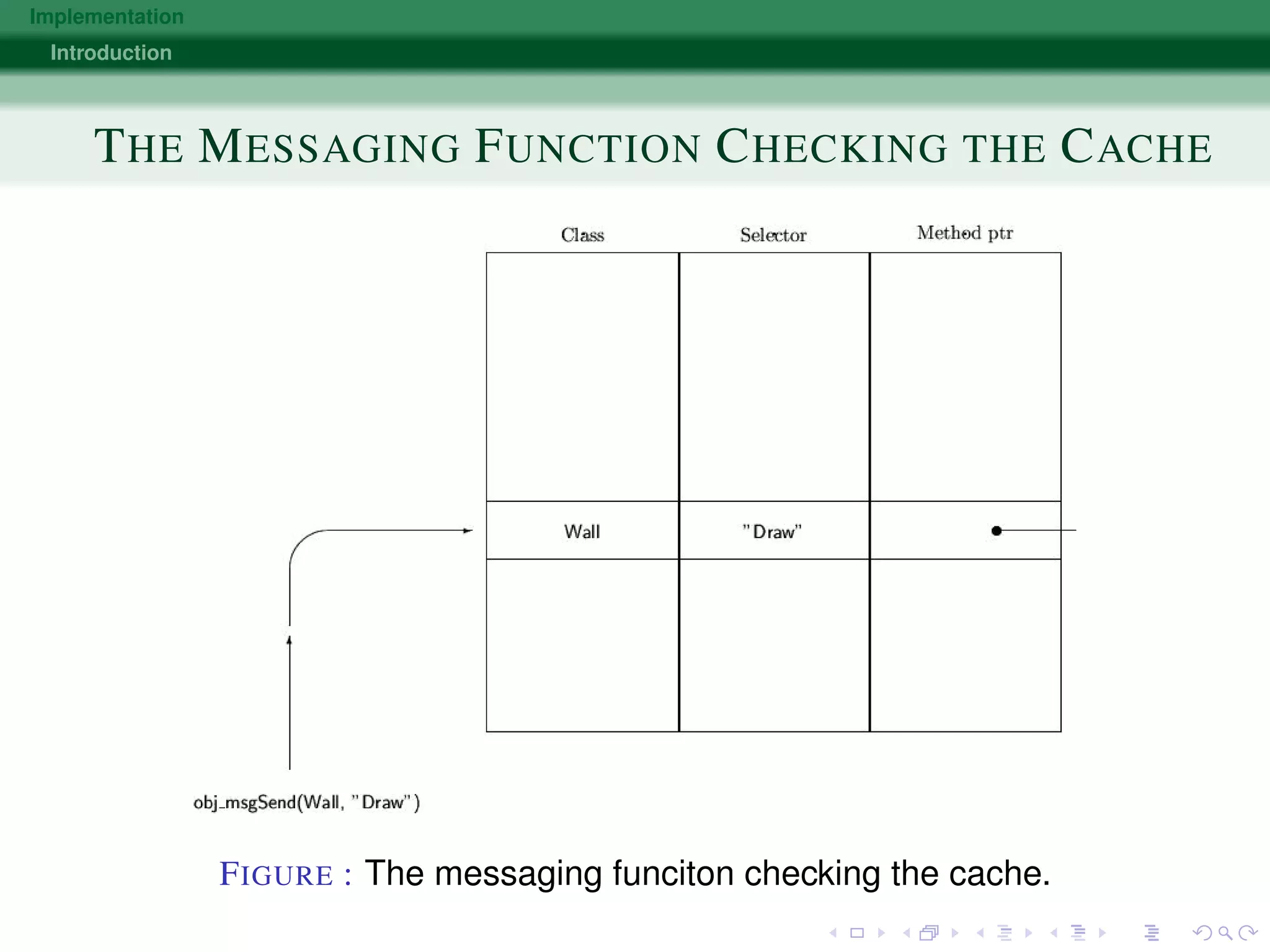
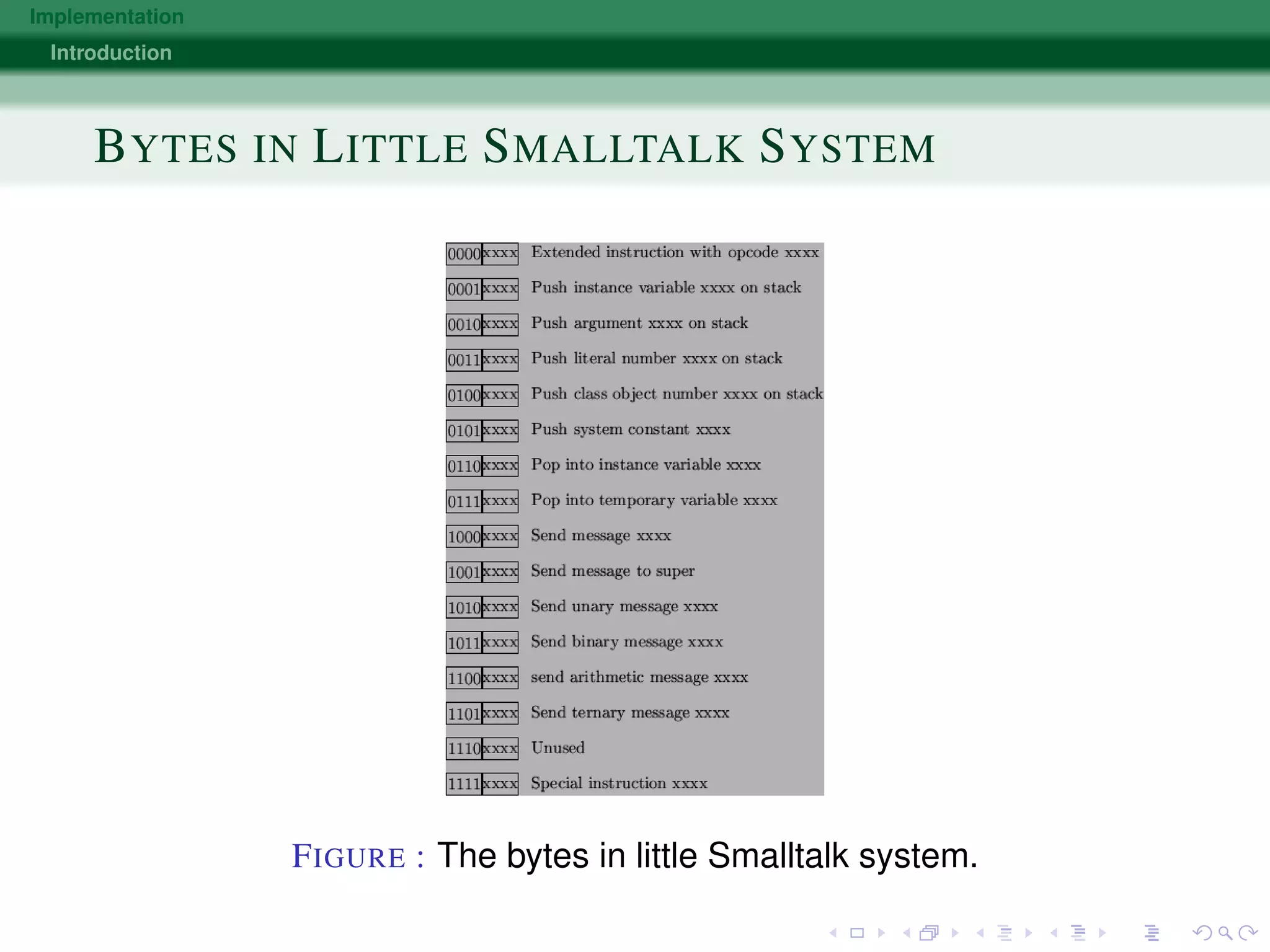
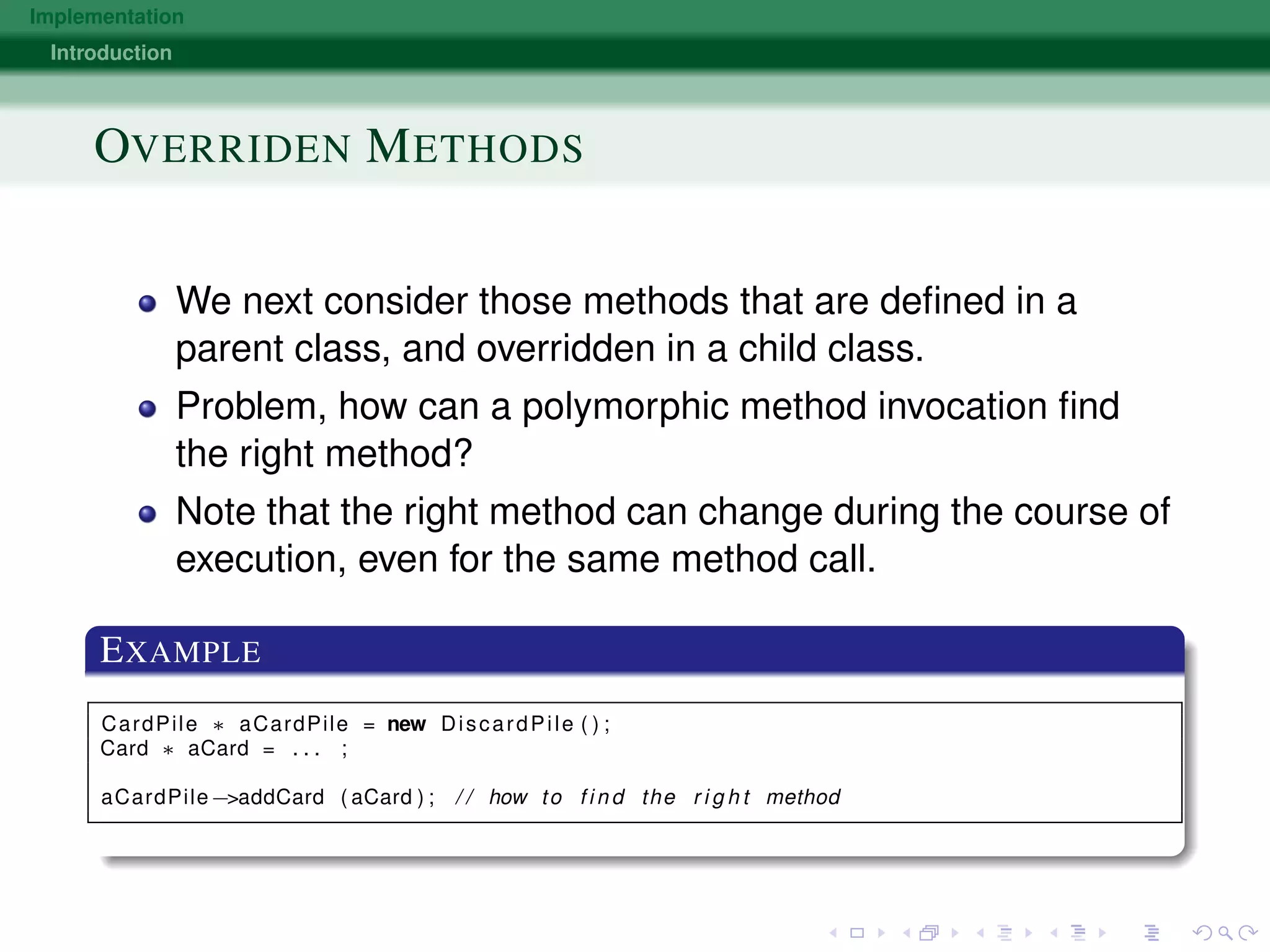
The document discusses various approaches to implementing object-oriented programming languages, including compilers vs interpreters, virtual method tables, inheritance, and just-in-time compilation. It covers topics like how receivers are passed as arguments, name encoding for unique method identifiers, inherited vs overridden methods, problems with multiple inheritance, bytecode interpreters, and using dispatch tables for dynamic languages. The key implementation techniques are using virtual method tables to dispatch overridden methods at runtime and just-in-time compilers that translate bytecode to native machine code for improved performance.



![Implementation
Introduction
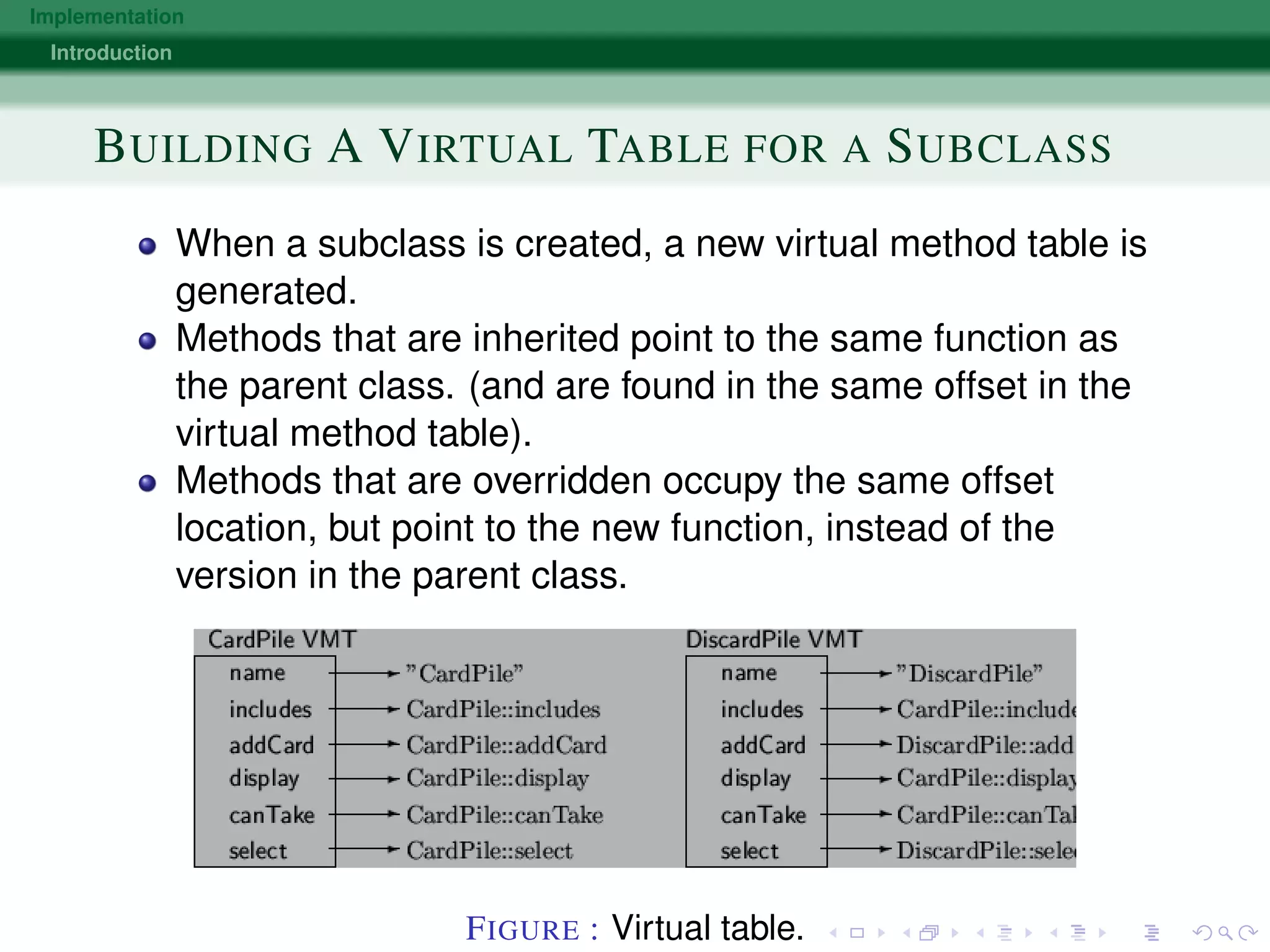
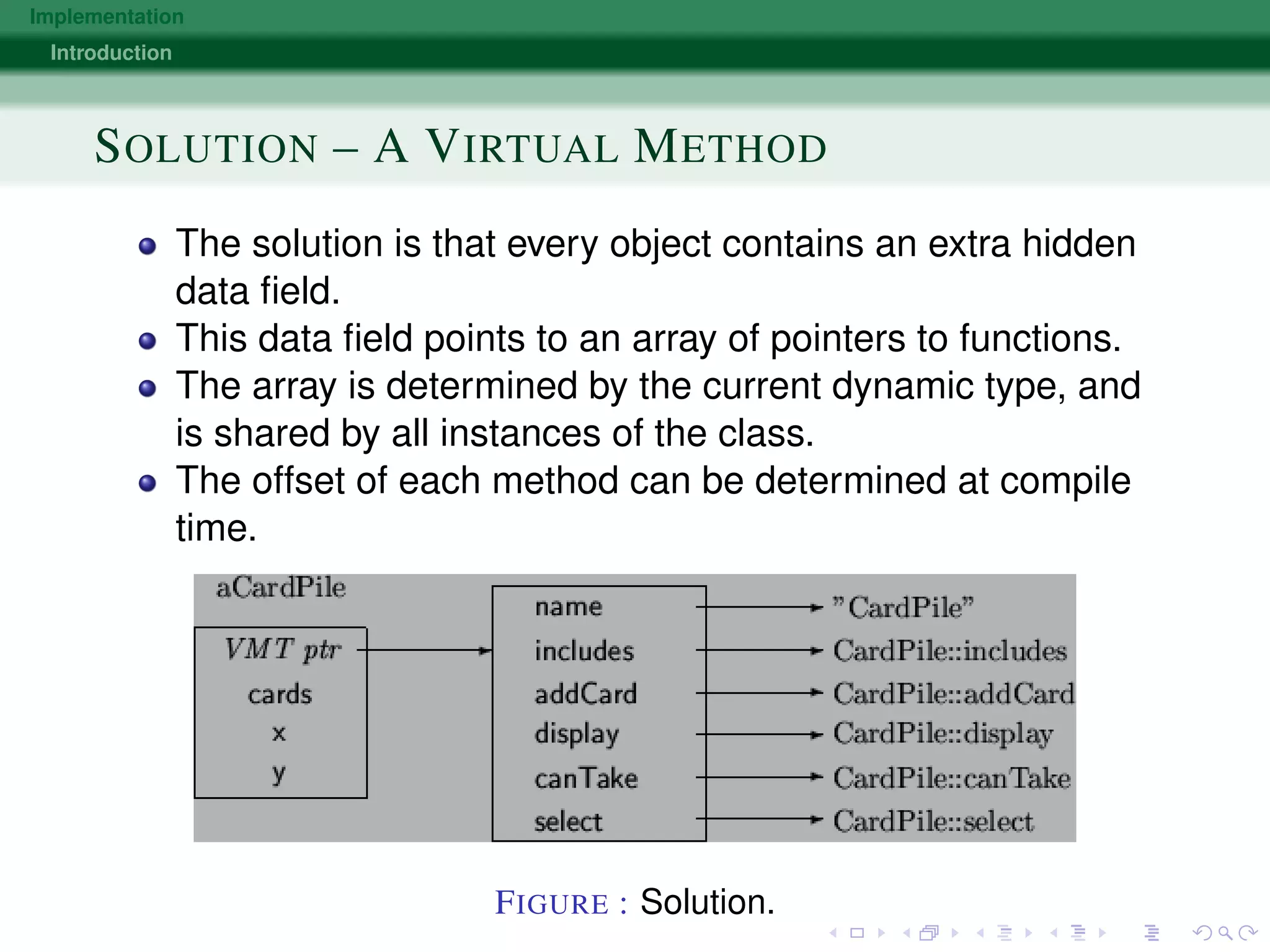
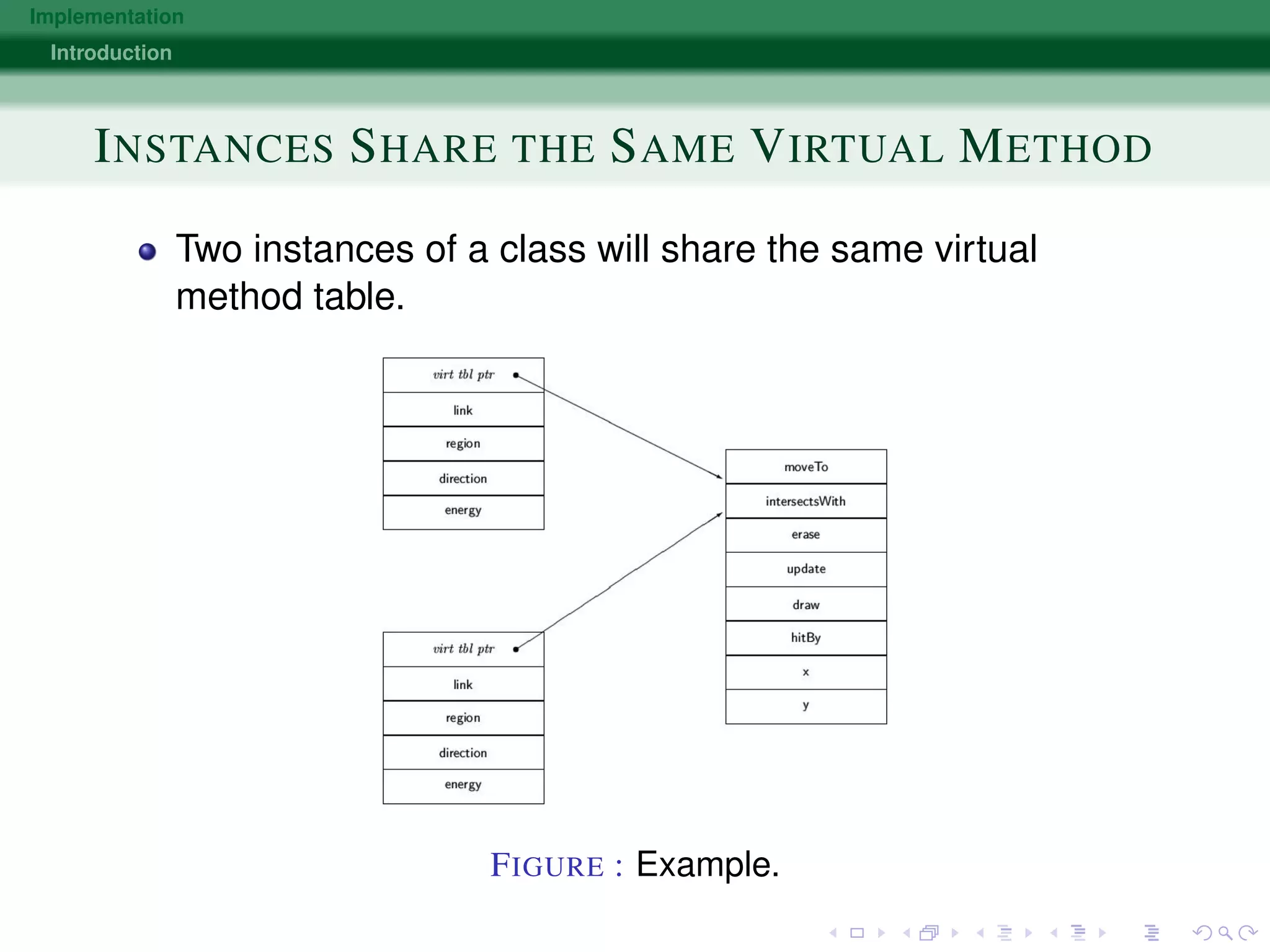
METHOD CALLS BECOME INDEXED OFFSETS
Each object maintains a pointer to a table, called the virtual
method table.
Virtual methods are identified by a fixed address in this
table.
A method call, such as:
A.foo(B, C)
is translated into
(* A.virTable[idx])(A, B, C)](https://image.slidesharecdn.com/presentation-150424013349-conversion-gate02/75/Implementation-17-2048.jpg)