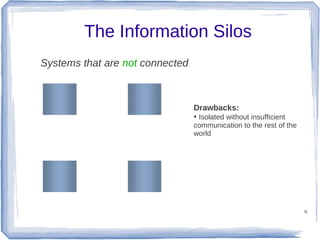
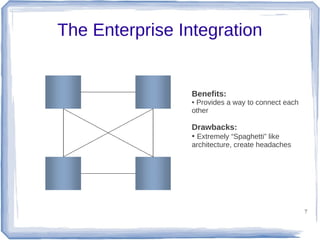
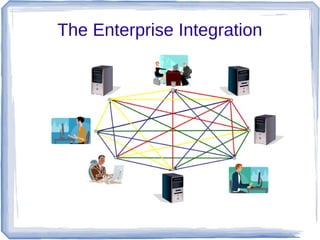
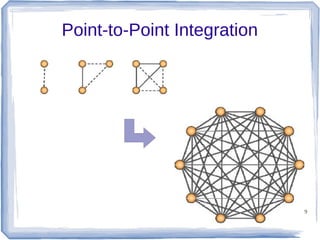
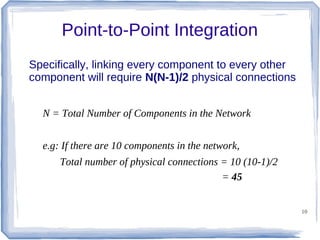
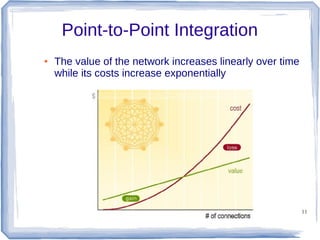
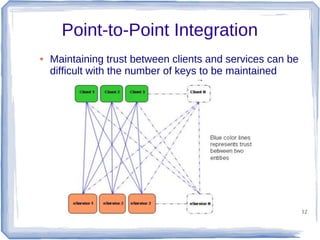
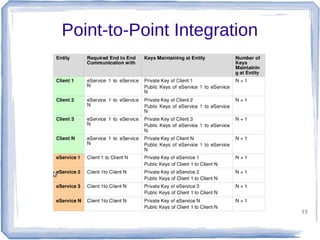
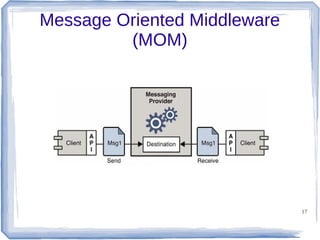
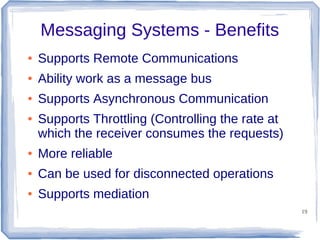
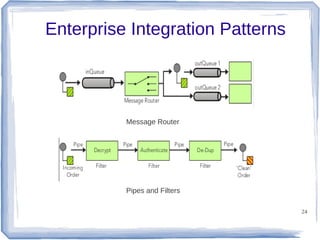
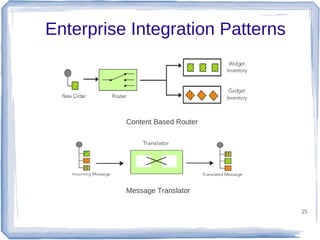
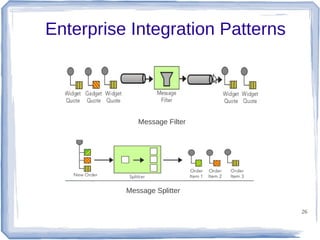
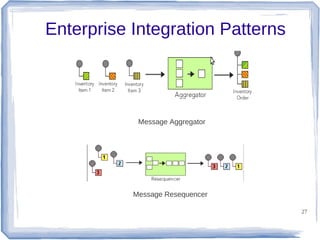
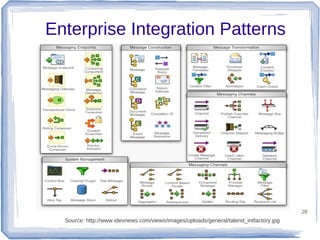
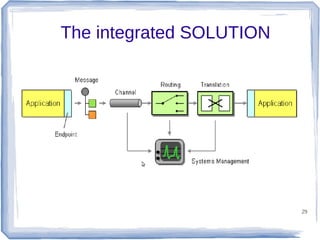
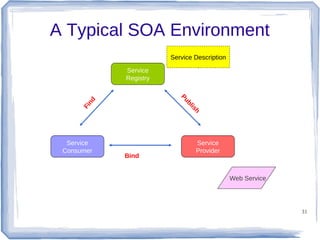
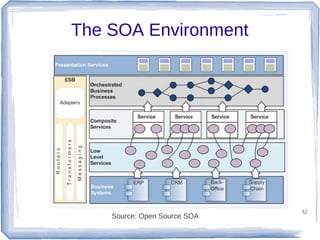
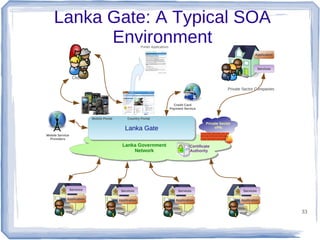
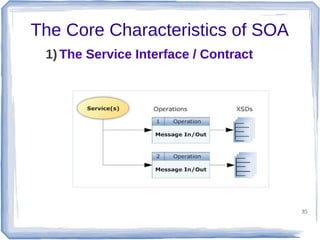
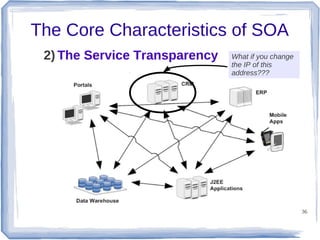
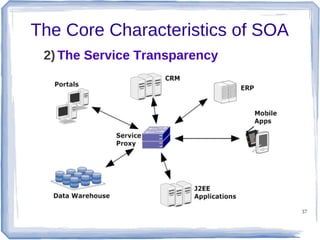
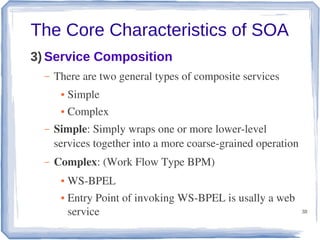
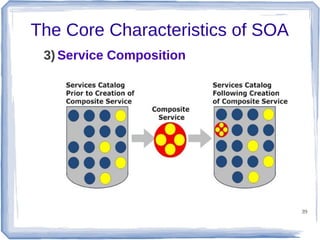
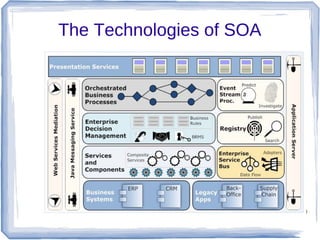
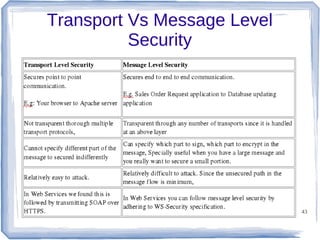
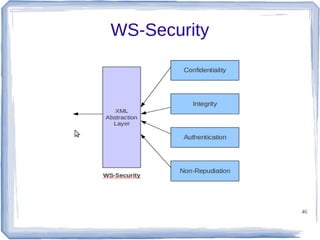
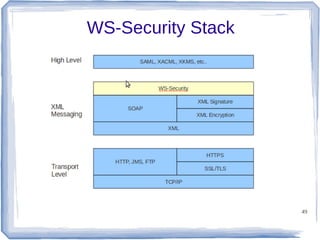
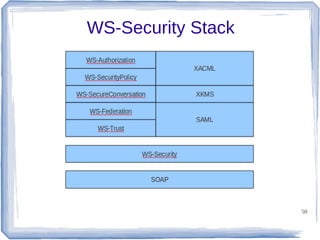
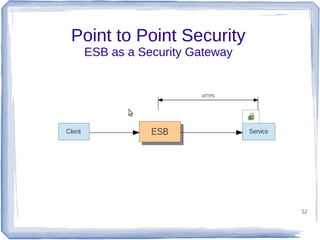
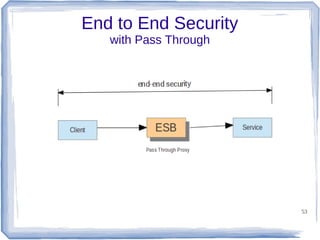
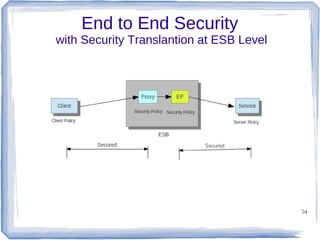
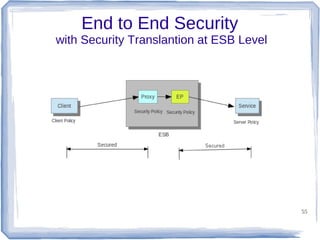
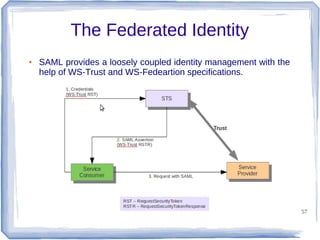
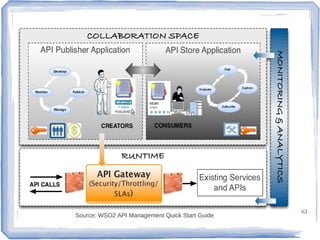
The document discusses enterprise application integration and related technologies. It begins with an introduction to enterprise applications and the benefits of integration. Common integration approaches are then described, including middleware, message-oriented middleware, enterprise integration patterns, and service-oriented architecture. The document also covers topics like SOA security, resource-oriented architecture, and API management.