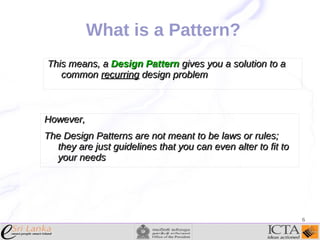
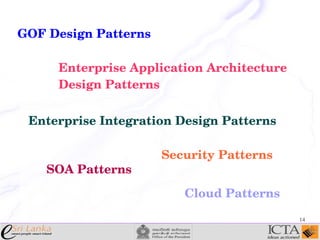
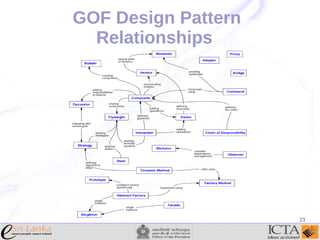
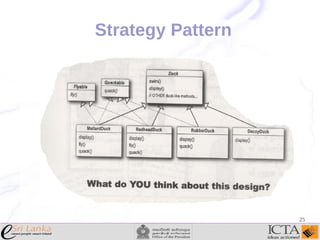
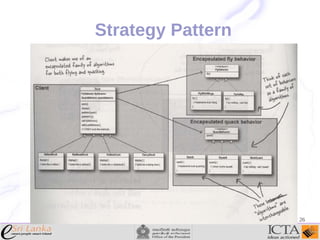
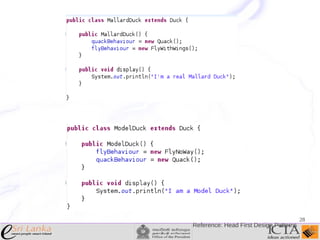
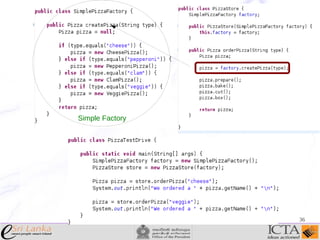
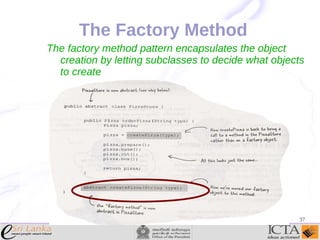
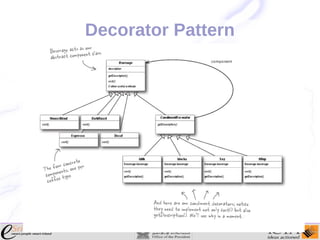
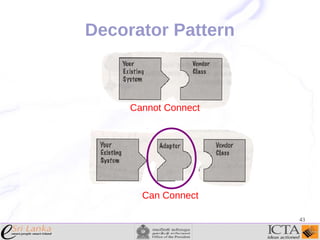
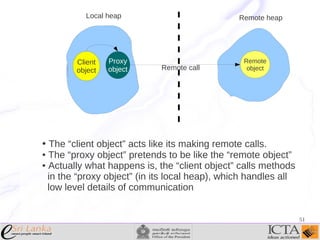
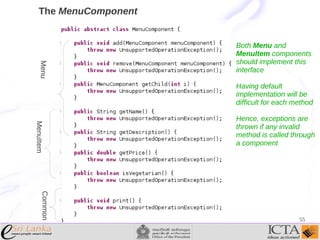
This document provides an overview and agenda for an enterprise application design patterns meetup. It discusses what design patterns are, common pattern catalogs like the Gang of Four patterns, and examples of specific patterns like Strategy, Observer, Command, Singleton, Factory Method, Decorator, Facade, Proxy, and Composite. The key points are that patterns provide reusable solutions to common problems, the Gang of Four catalog contains 23 fundamental patterns, and examples are given for creational, structural, and behavioral patterns.