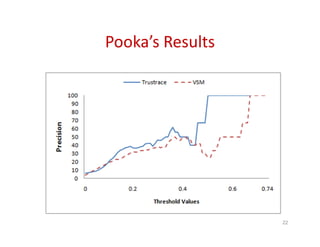
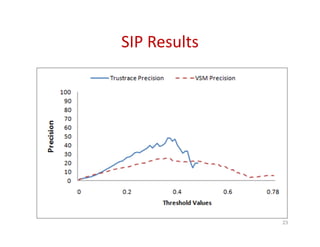
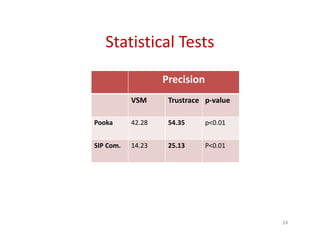
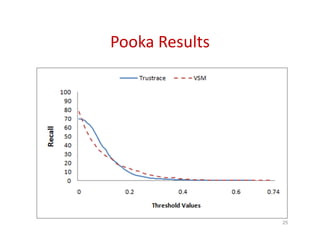
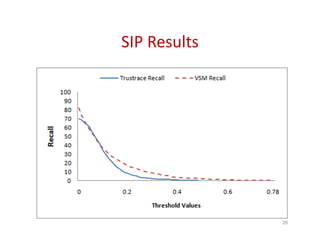
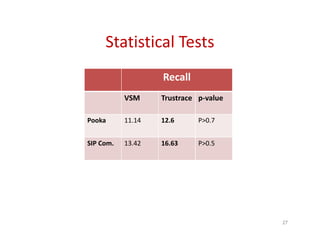
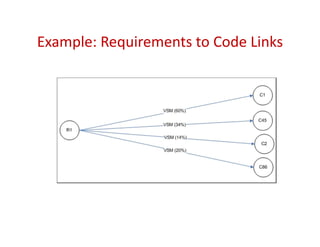
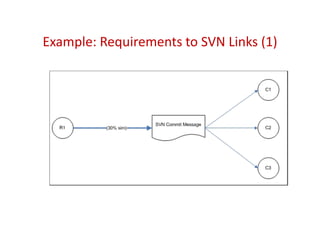
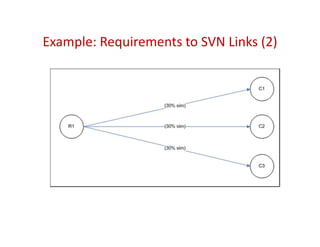
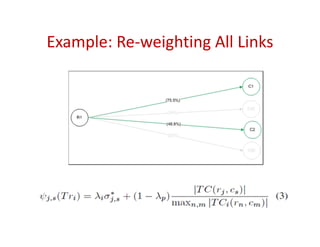
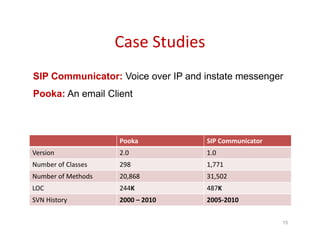
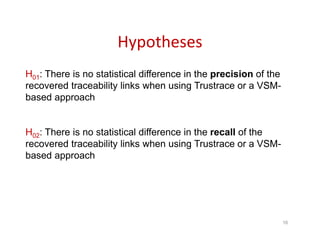
Trustrace is an approach that uses software repository links like SVN commits to improve the trust in automatically recovered traceability links between requirements and code. It calculates an initial trust value for links based on IR techniques like VSM, and then reweights the links based on additional information from the software repository. An evaluation on two case studies found Trustrace improved precision over VSM alone and showed no significant difference in recall, supporting the hypothesis that Trustrace can improve link recovery accuracy over IR-only approaches.












![Information Retrieval (IR) Methods
• Vector Space Model (VSM) (Salton et al., 1975)
– Each document, d, is represented by a vector of ranks of
the terms in the vocabulary:
vd = [rd(w1), rd(w2), …, rd(w|V|)]
– The query is similarly represented by a vector
– The similarity between the query and document is the
cosine of the angle between their respective vectors
21](https://image.slidesharecdn.com/icpc11c-171212151510/85/Icpc11c-ppt-21-320.jpg)