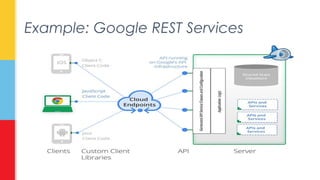
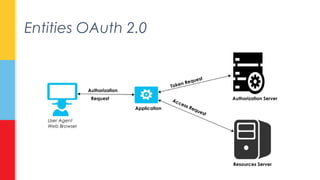
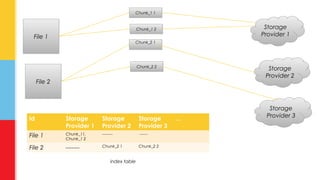
The document discusses the concept of 'storage leeching' in personal cloud services, where users exploit free accounts to gain extensive storage by utilizing open REST APIs. It presents a proof-of-concept application called Boxleech, which aggregates free storage from multiple platforms, and outlines potential solutions to mitigate abuse such as account verification and implementation of expiration mechanisms. The paper highlights the unintended consequences of personal cloud services' strategies to attract new users through free accounts and ease of API access.











![ The fraction of users that creates storage accounts of size
a when they arrive to the system is defined by fs ∈ [0,1]
We assumes that once user creates an account, he does
not cancel it after he leaves the system.
So the maximum amount of available storage (Sa) at time
n is
Sa(n)=n·λ·fs ·a](https://image.slidesharecdn.com/cloud-141123210538-conversion-gate02/85/Cloud-as-a-GIFT-Exploiting-Personal-Cloud-Free-Accounts-via-Rest-APIs-18-320.jpg)













![References:
[1] F. Research, “The personal cloud: Transforming personal
computing, mobile, and web markets,” 2011. [Online]. Available:
http://www.forrester.com/rb/Research/personal cloud transforming personal computing%2C mobile
%2C and/q/id/57403/t/2
[2] [Online]. Available: http://en.wikipedia.org/wiki/Dropbox (service)
[3] M. Jensen, N. Gruschka, and R. Herkenh¨oner, “A survey of attacks on web services,” Computer
Science - Research and Development, vol. 24, pp. 185–197, 2009.
[4] “A survey on security issues in service delivery models of cloud computing,” Journal of Network and
Computer Applications, vol. 34, no. 1, pp. 1–11, 2011.
[5] J. Somorovsky, M. Heiderich, M. Jensen, J. Schwenk, N. Gruschka, and L. Lo Iacono, “All your clouds
are belong to us: security analysis of cloud management interfaces,” in ACM CCSW’11, 2011, pp. 3–14.
[6] L. Vaquero, L. Rodero-Merino, and D. Mor´an, “Locking the sky: asurvey on iaas cloud security,”
Computing, vol. 91, pp. 93–118, 2011.
[7] J. Idziorek and M. Tannian, “Exploiting cloud utility models for profit and ruin,” in IEEE CLOUD’11, july
2011, pp. 33–40.
[8] J. Idziorek, M. Tannian, and D. Jacobson, “Attribution of fraudulent resource consumption in the
cloud,” in IEEE CLOUD’12, 2012, pp. 99–106.](https://image.slidesharecdn.com/cloud-141123210538-conversion-gate02/85/Cloud-as-a-GIFT-Exploiting-Personal-Cloud-Free-Accounts-via-Rest-APIs-33-320.jpg)
![References:
[9] M. Mulazzani, S. Schrittwieser, M. Leithner, M. Huber, and E.Weippl., “Dark clouds on the horizon:
Using cloud storage as attack vector and online slack space,” in USENIX Security, 2011, pp. 5–8.
[10] J. Srinivasan, W. Wei, X. Ma, and T. Yu, “Emfs: Email-based personal cloud storage,” in NAS’11,
2011, pp. 248–257.
[11] A. Traeger, N. Joukov, J. Sipek, and E. Zadok, “Using free web storage for data backup,” in
StorageSS’06, 2006, pp. 73–78.
[12] H.-C. Chao, T.-J. Liu, K.-H. Chen, and C.-R. Dow, “A seamless and reliable distributed network file
system utilizing webspace,” in WSE’08, 2008, pp. 65–68.
[13] E. Hammer-Lahav, “The OAuth 1.0 Protocol,” http://tools.ietf.org/html/ rfc5849, 2010.
[14] J. R. Douceur, “The sybil attack,” in IPTPS’01, 2002, pp. 251–260.
[15] R. Gracia-Tinedo, M. S´anchez-Artigas, A. Moreno-Mart´ınez, and P. Garc´ıa-L´opez, “FRIENDBOX:
A Hybrid F2F Personal Storage Application,” in IEEE CLOUD’12, 2012, pp. 131–138.
[16] B. Cohen, “Incentives build robustness in bittorrent,” in Workshop on
Economics of Peer-to-Peer systems, vol. 6, 2003, pp. 68–72.
[17] D. Karger, E. Lehman, T. Leighton, R. Panigrahy, M. Levine, and D. Lewin, “Consistent hashing and
random trees: distributed caching protocols for relieving hot spots on the world wide web,” in ACM
STOC’97, 1997, pp. 654–663.](https://image.slidesharecdn.com/cloud-141123210538-conversion-gate02/85/Cloud-as-a-GIFT-Exploiting-Personal-Cloud-Free-Accounts-via-Rest-APIs-34-320.jpg)
