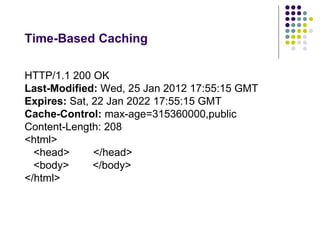
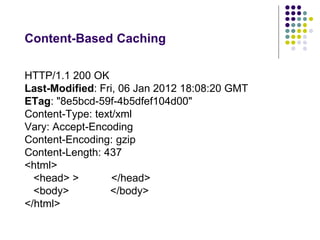
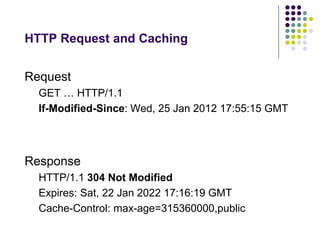
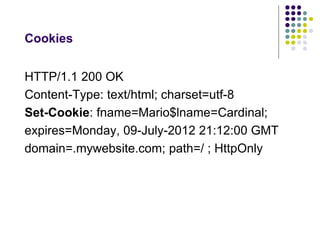
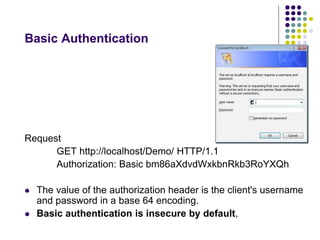
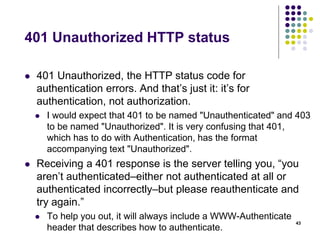
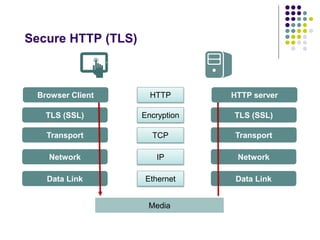
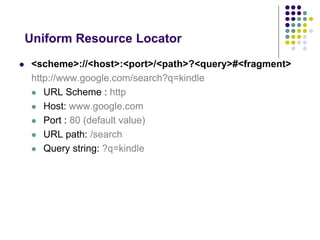
The document provides a comprehensive overview of HTTP fundamentals including resources, requests, responses, media types, and security measures. It explains components such as URL structure, headers, request methods (GET, POST, etc.), response status codes, authentication methods, and the importance of secure HTTP (HTTPS). The author, Mario Cardinal, presents these concepts in a way intended for developers looking to understand web communication protocols.







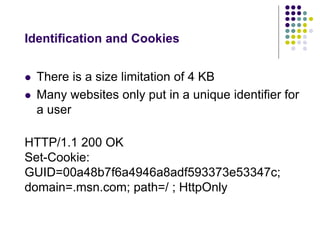
![HTTP Request Message
A full HTTP request message consists of the
following parts:
[method] [URL] [version]
[headers]
[body]](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-11-320.jpg)
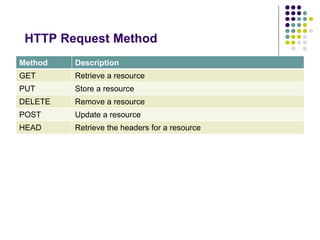
![HTTP Request Method
[method] [URL] [version]
[headers]
[body]
GET
http://mariocardinal.com/Articles/741.aspx
HTTP/1.1](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-13-320.jpg)

![HTTP Request Header
[method] [URL] [version]
[headers]
[body]
GET
http://mariocardinal.com/Articles/741.aspx
HTTP/1.1
Accept-Language: fr-CA
Date: Fri, 9 Aug 2013 21:12:00 GMT](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-15-320.jpg)

![HTTP Response Message
A full HTTP response message consists of
the following parts:
[version] [status] [reason]
[headers]
[body]](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-18-320.jpg)
![HTTP Response Message
[version] [status] [reason]
[headers]
[body]
HTTP/1.1
200
OK](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-20-320.jpg)
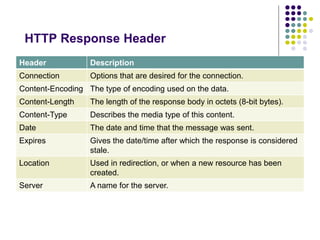
![HTTP Response Message
[version] [status] [reason]
[headers]
[body]
HTTP/1.1
200
OK
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/7.0
X-AspNet-Version: 2.0.50727
X-Powered-By: ASP.NET
Date: Sat, 14 Jan 2012 04:00:08 GMT
Connection: close
Content-Length: 17151](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-22-320.jpg)


![HTTP Response Message
[version] [status] [reason]
[headers]
[body]
HTTP/1.1
200
OK
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/7.0
X-AspNet-Version: 2.0.50727
X-Powered-By: ASP.NET
Date: Sat, 14 Jan 2012 04:00:08 GMT
Connection: close
Content-Length: 17151
<html>
<head>
<title>Hello</title>
</head>
<body>
... content ...
</body>
</html>](https://image.slidesharecdn.com/httpfundamentalsfordevelopers-141012231336-conversion-gate02/85/HTTP-fundamentals-for-developers-25-320.jpg)