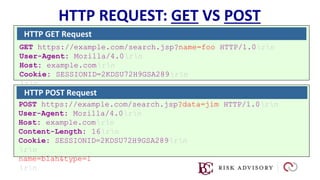
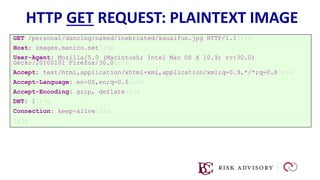
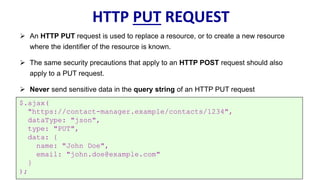
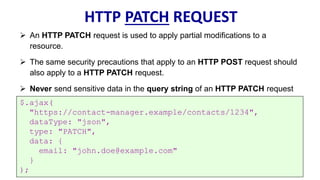
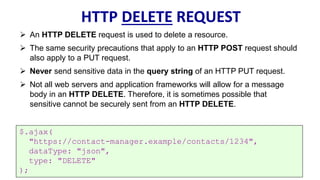
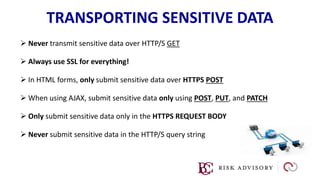
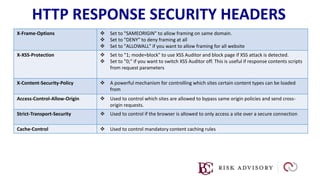
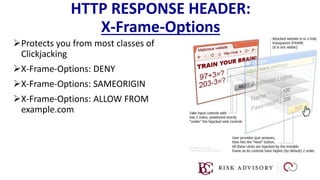
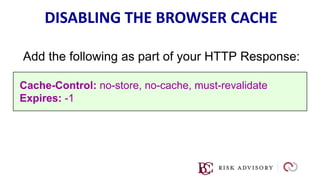
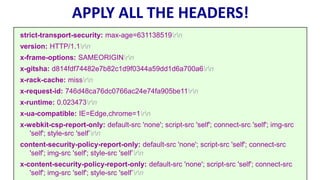
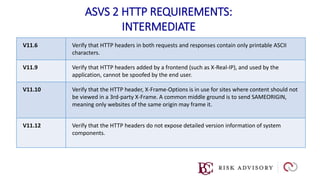
HTTP is the protocol used to transmit data over the web. It is stateless and requires sessions to track state. Requests and responses use headers to transmit metadata. Sensitive data should only be sent over HTTPS and only through POST, PUT, PATCH requests never in the URL query string. Response headers like HSTS, CSP, and CORS help secure applications by controlling caching, framing, and cross-origin requests.