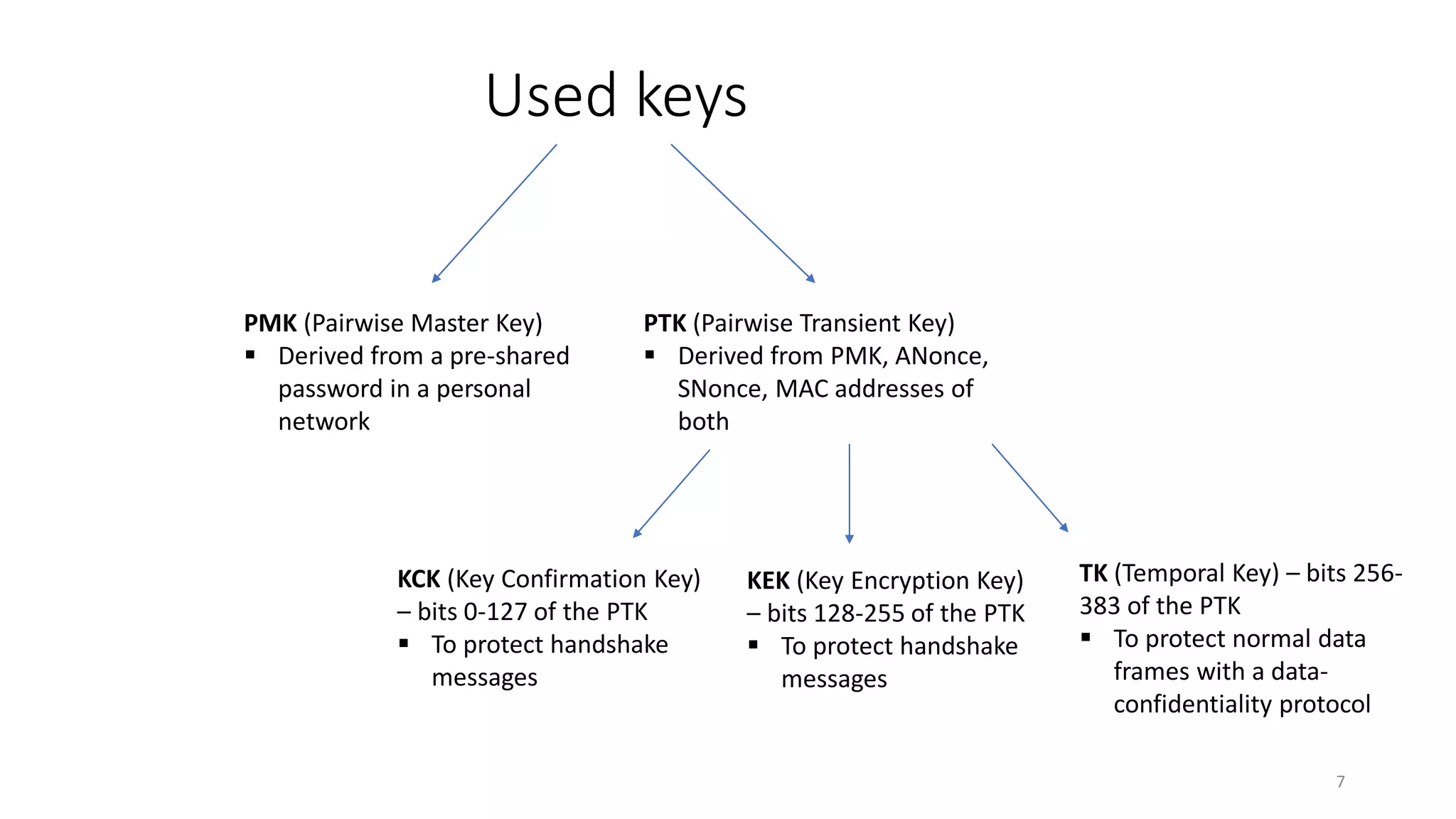
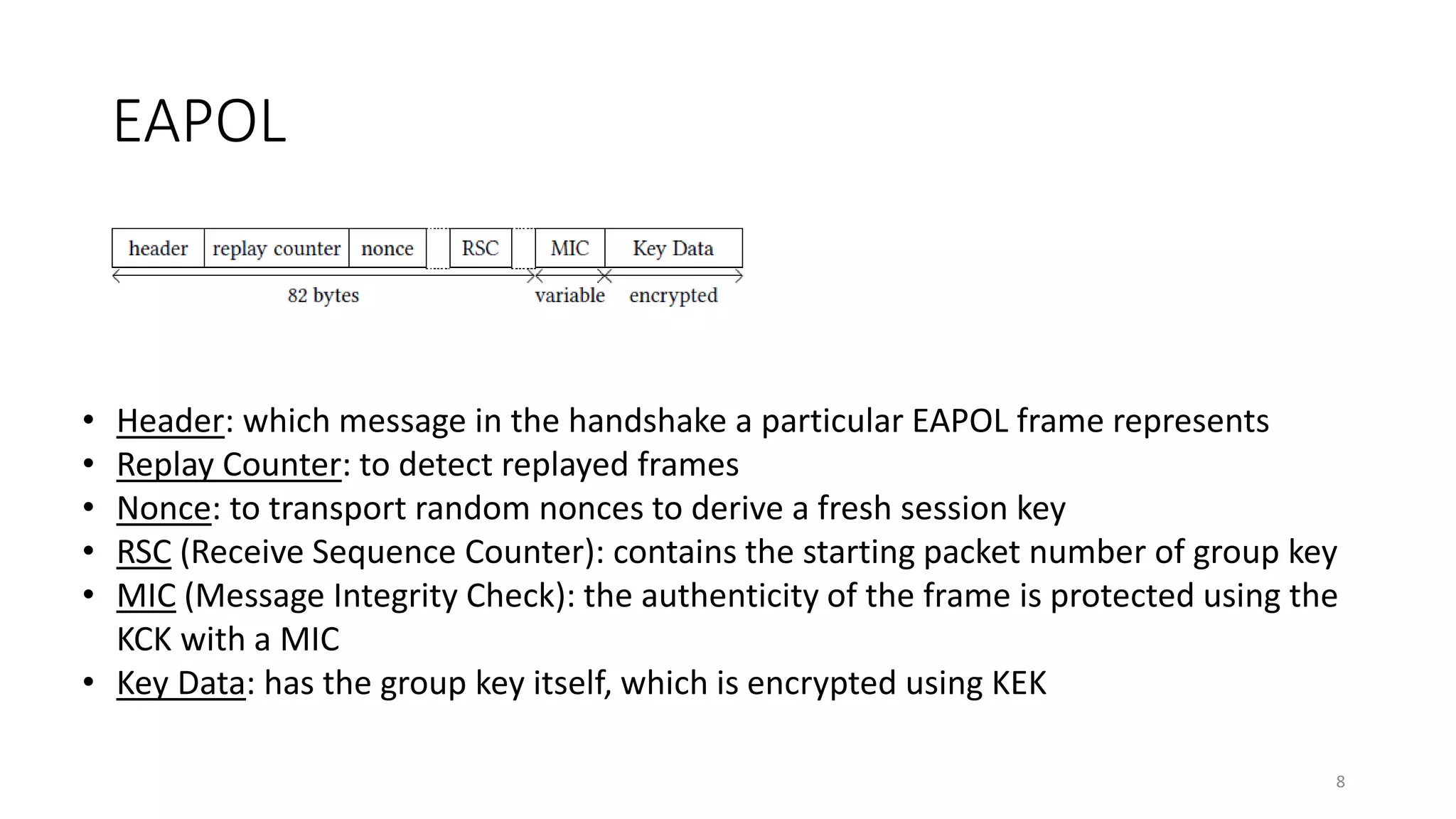
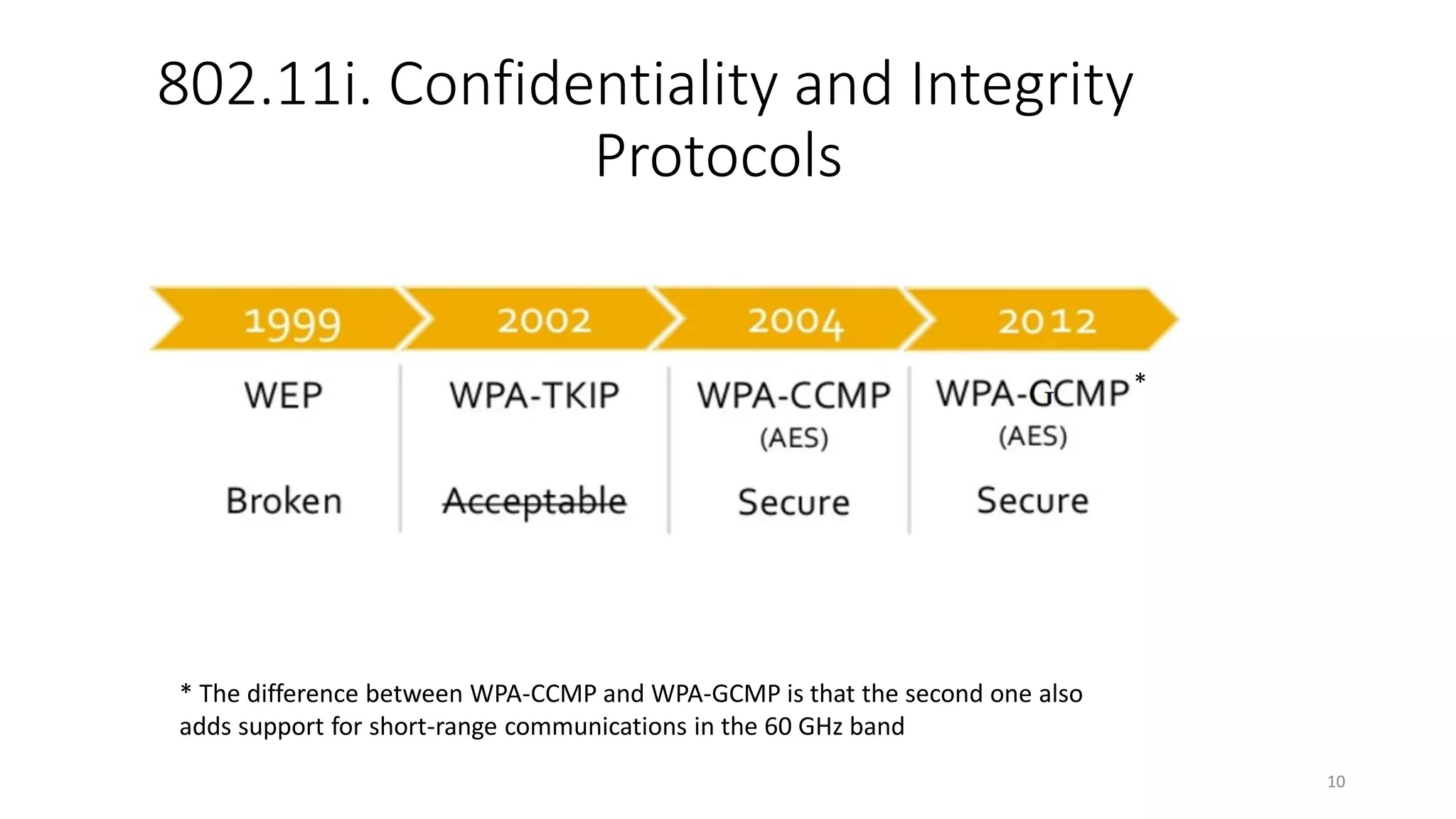
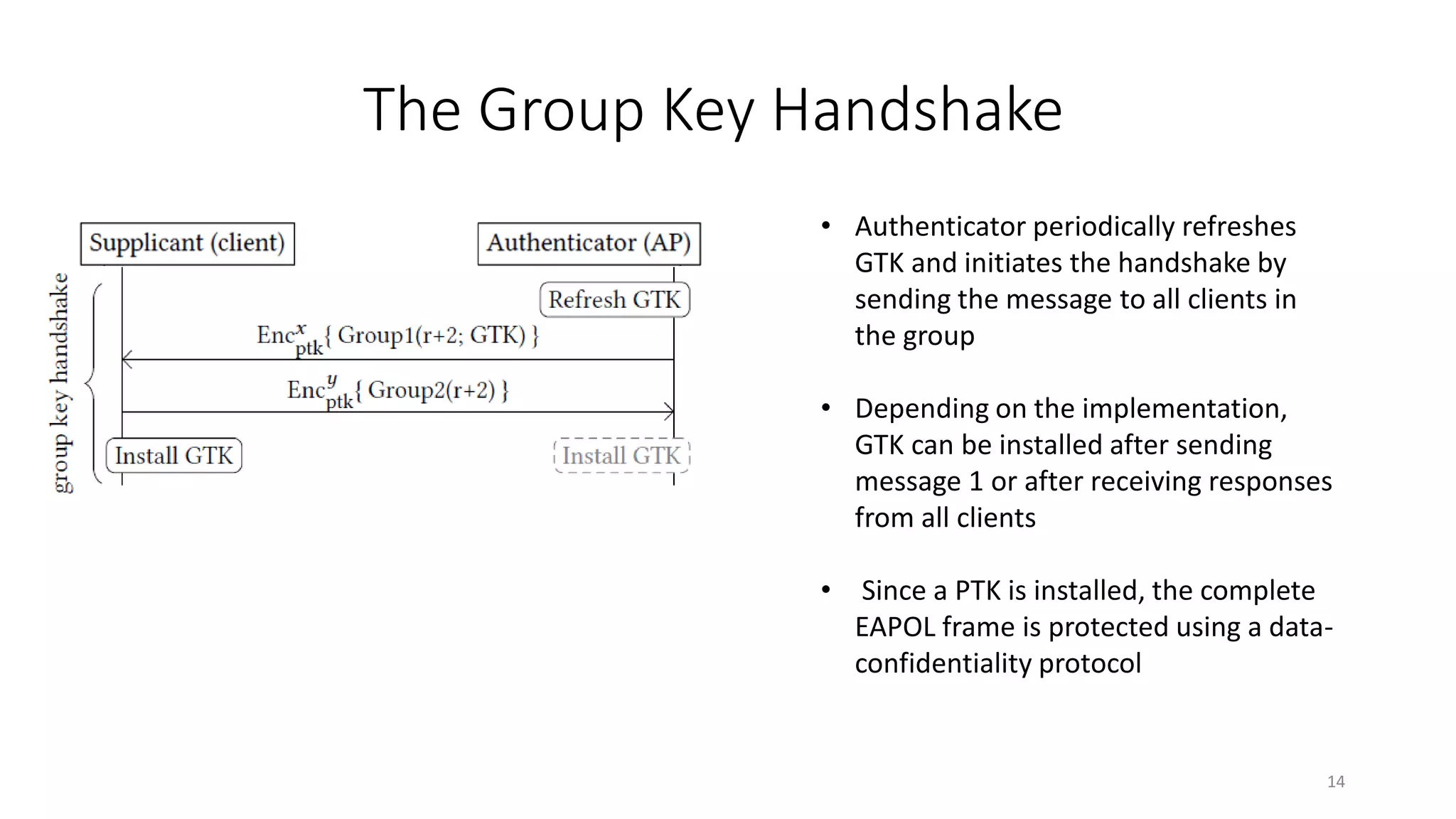
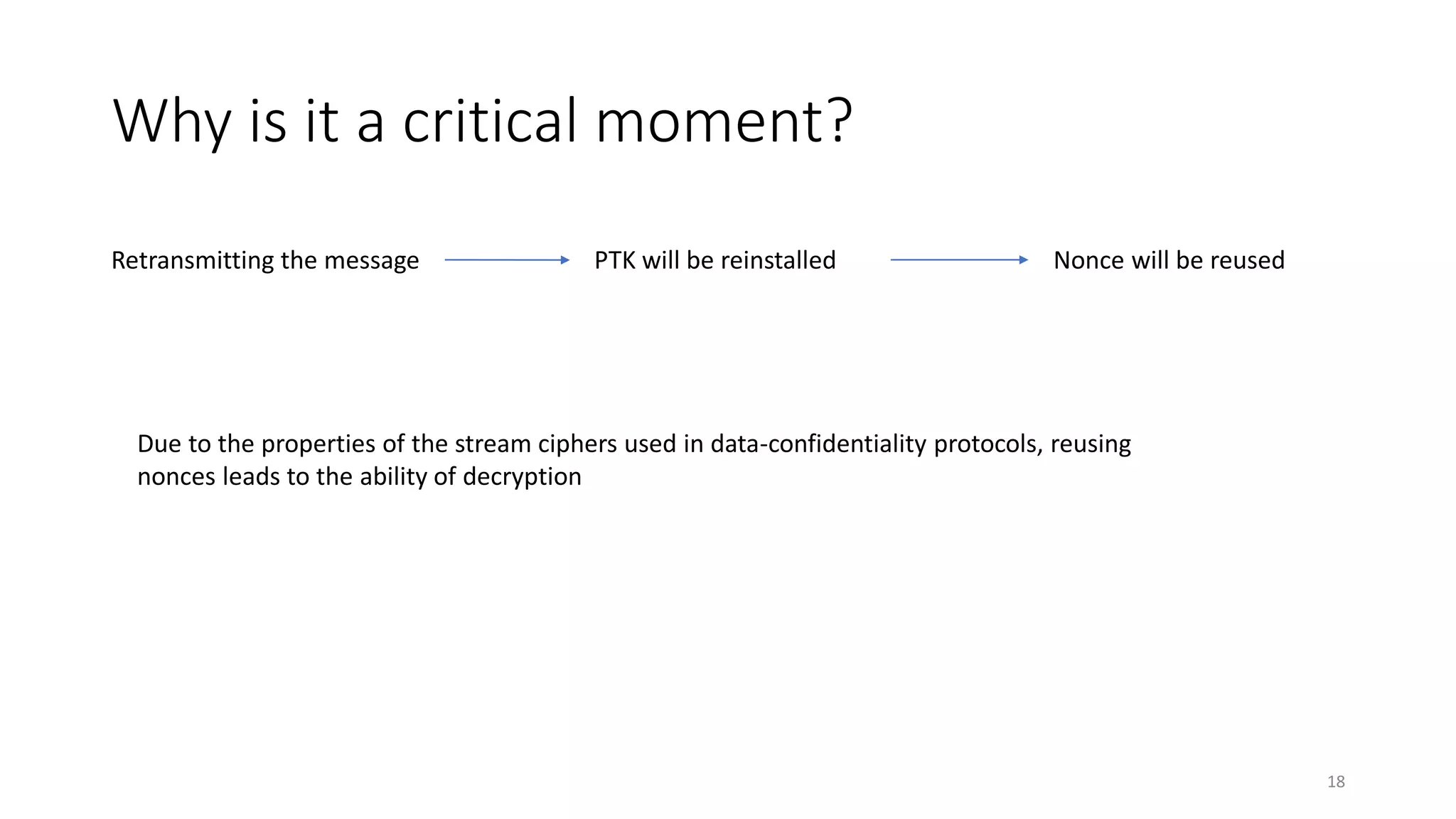
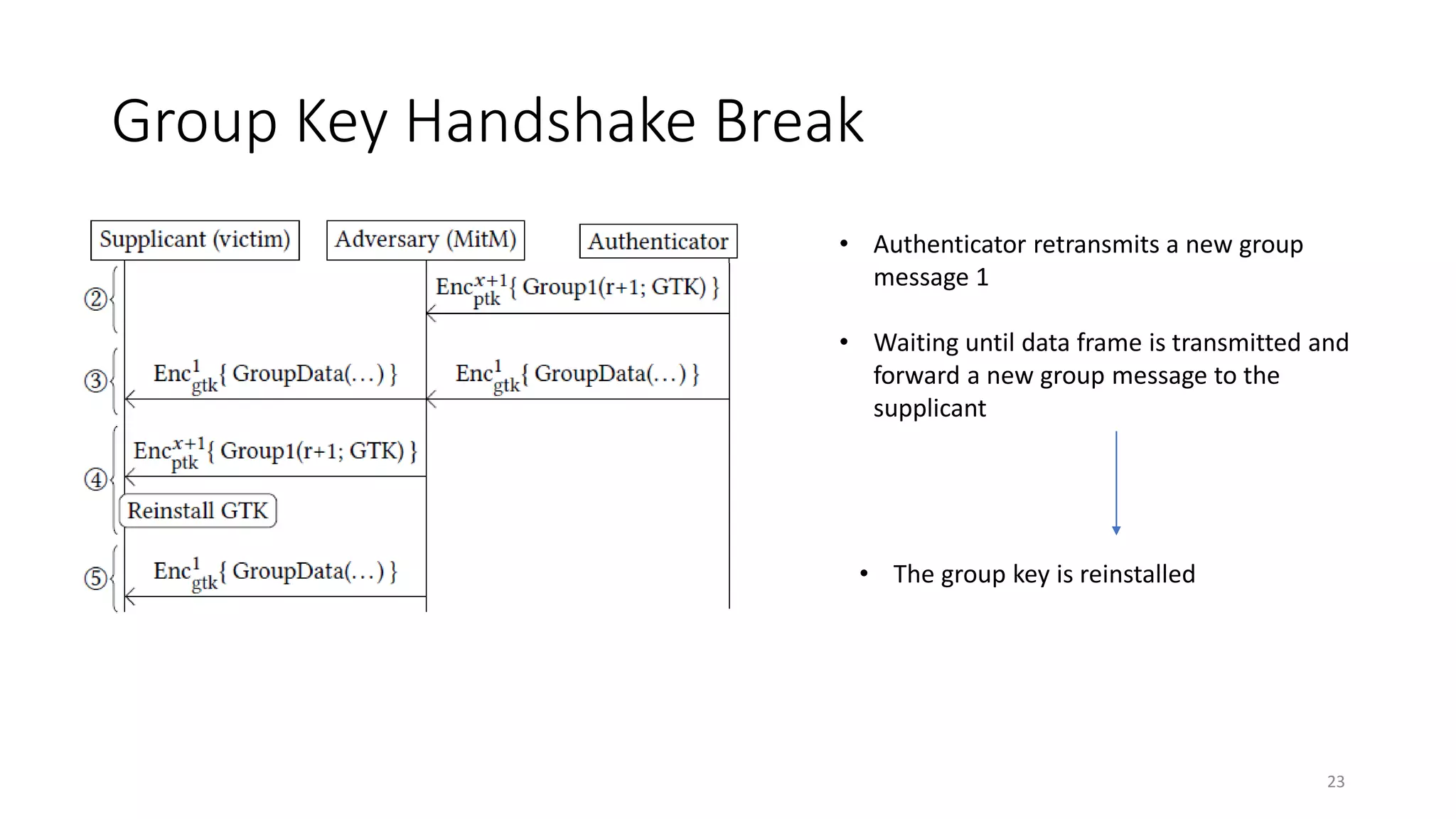
The document discusses the KRACK attack on the 802.11i four-way handshake, outlining the history and protocols of wireless security including WEP, WPA, and WPA2. It details the vulnerabilities in the four-way handshake that can be exploited through nonce reuse, leading to potential attacks such as plaintext retransmission. Countermeasures and ways to improve security against such attacks are also mentioned.