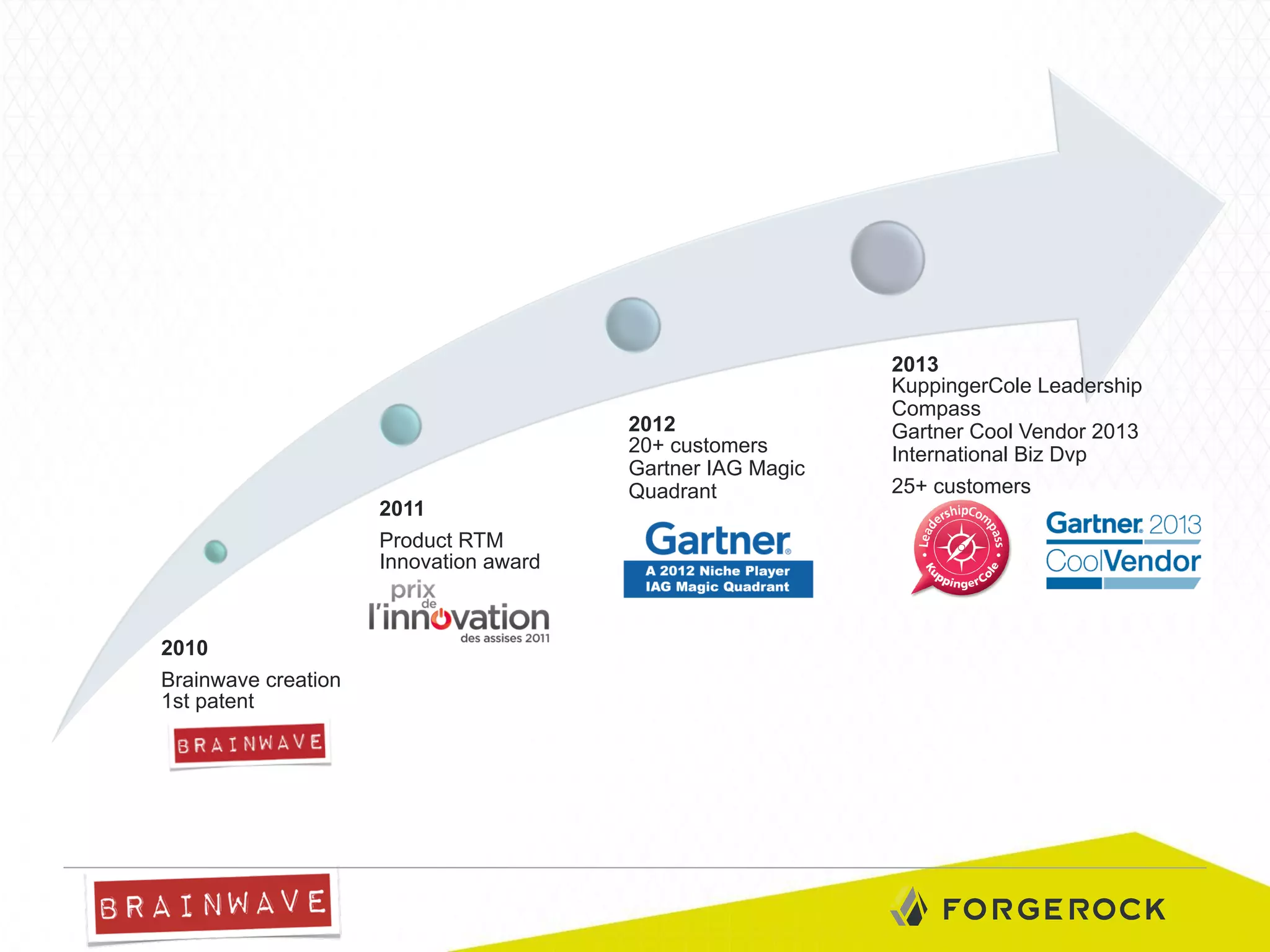
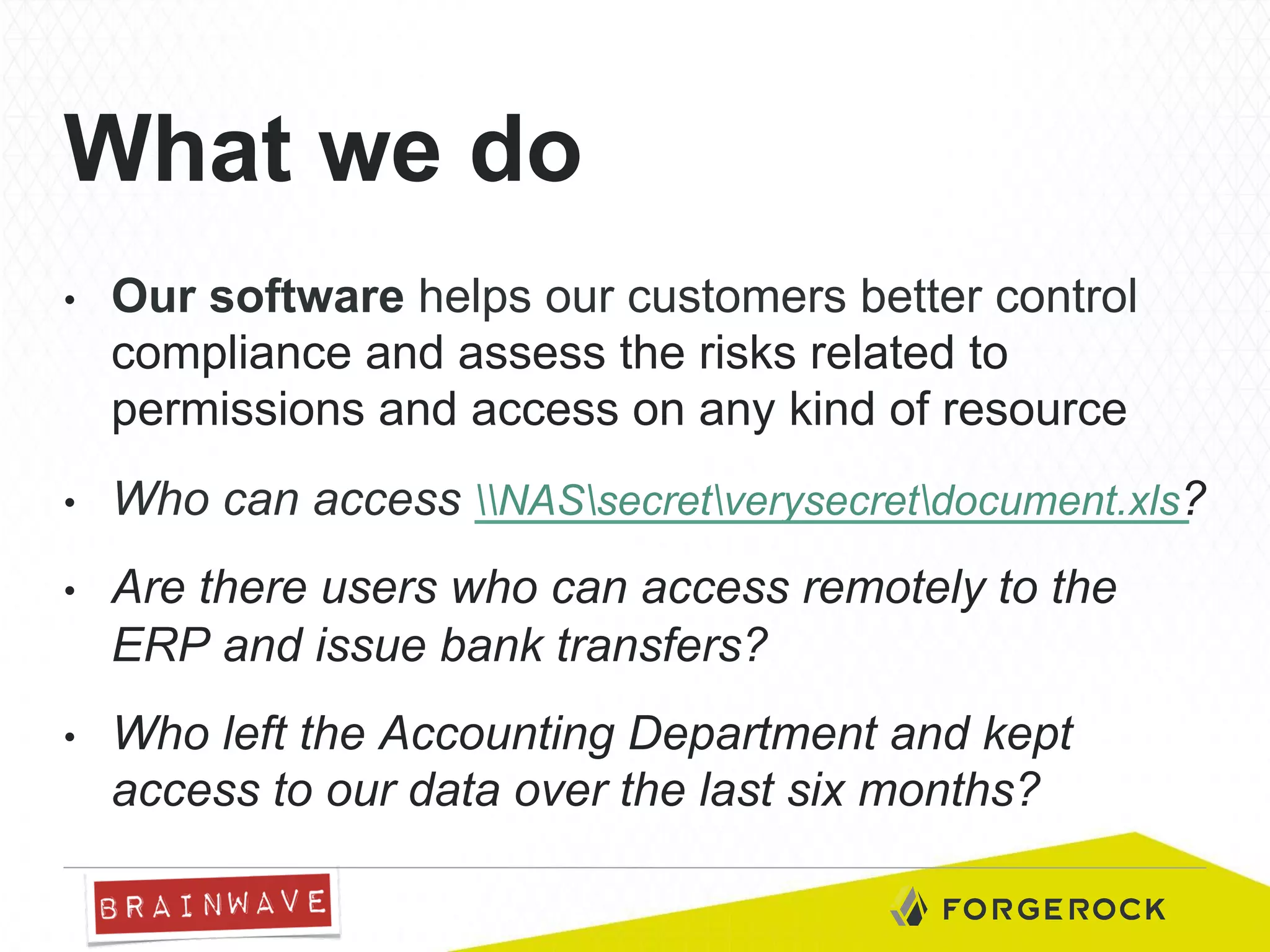
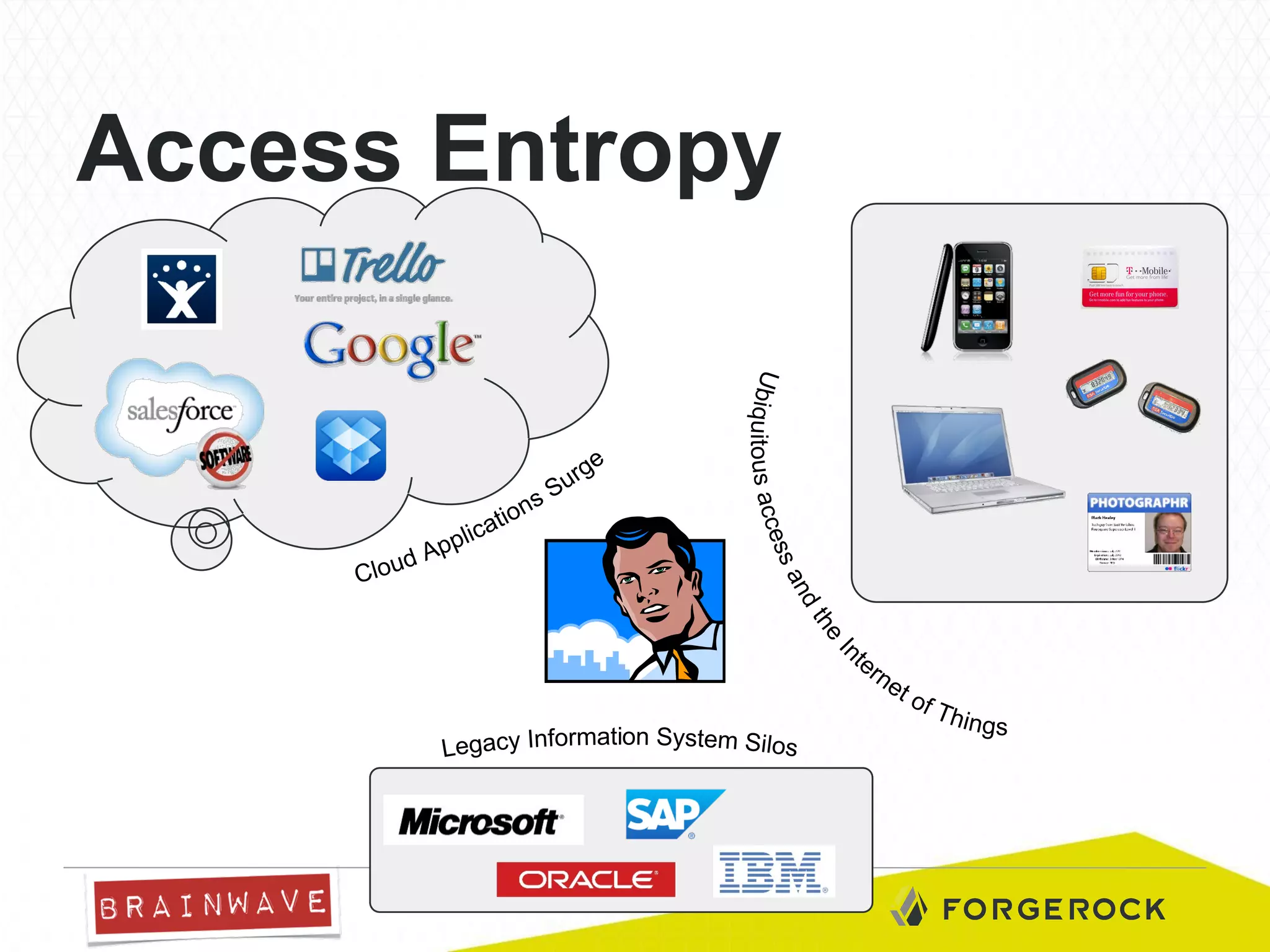
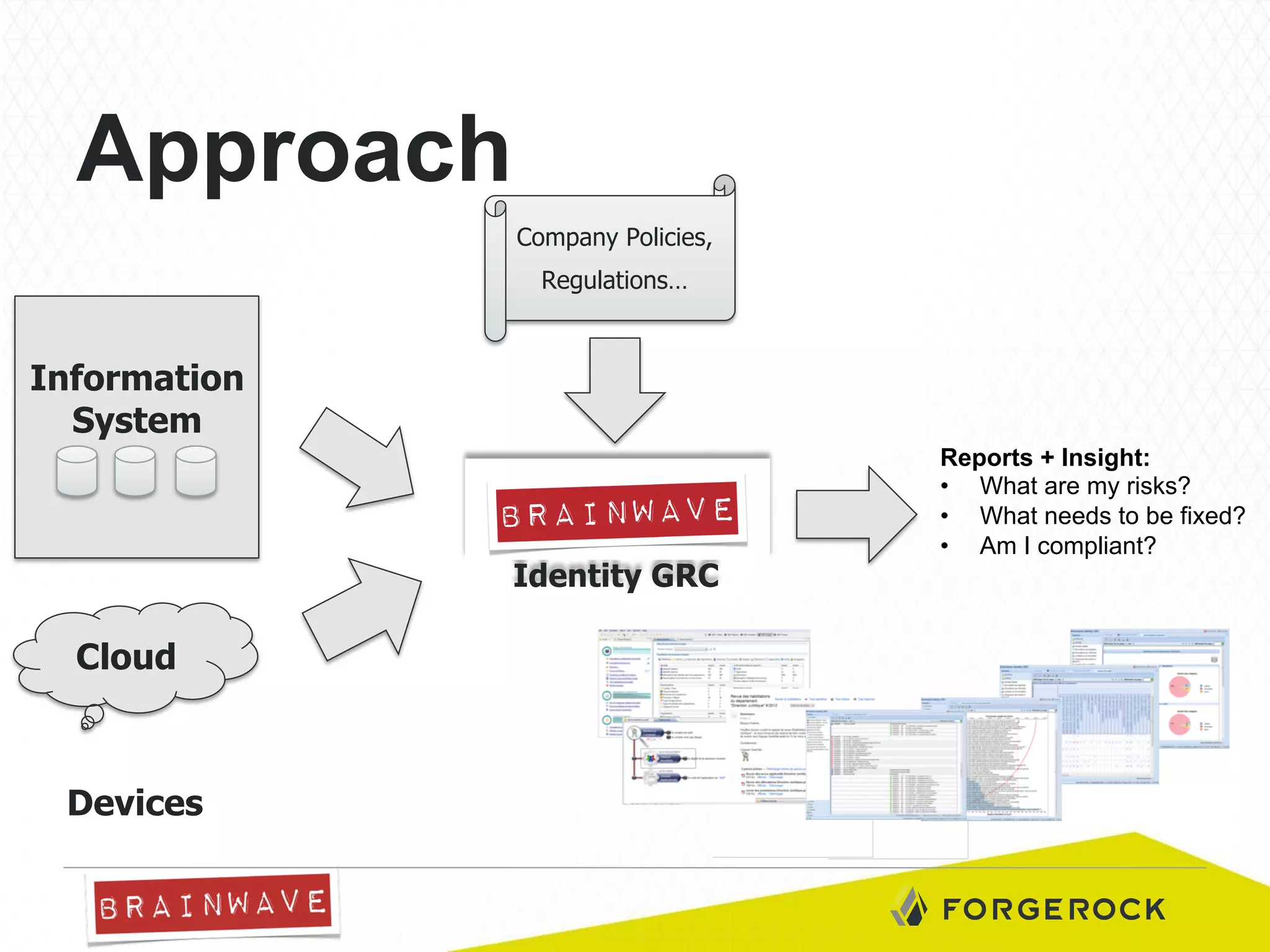
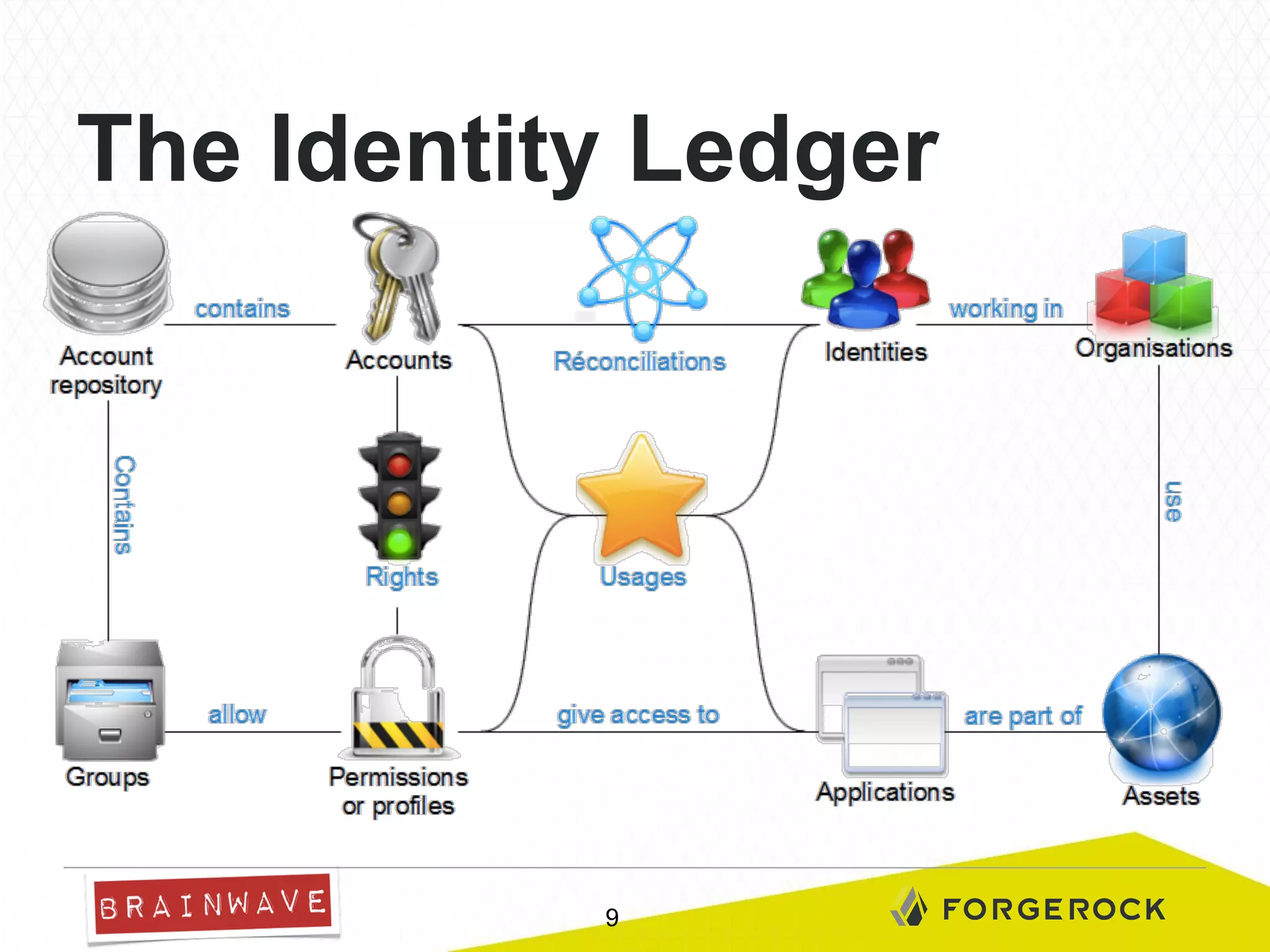
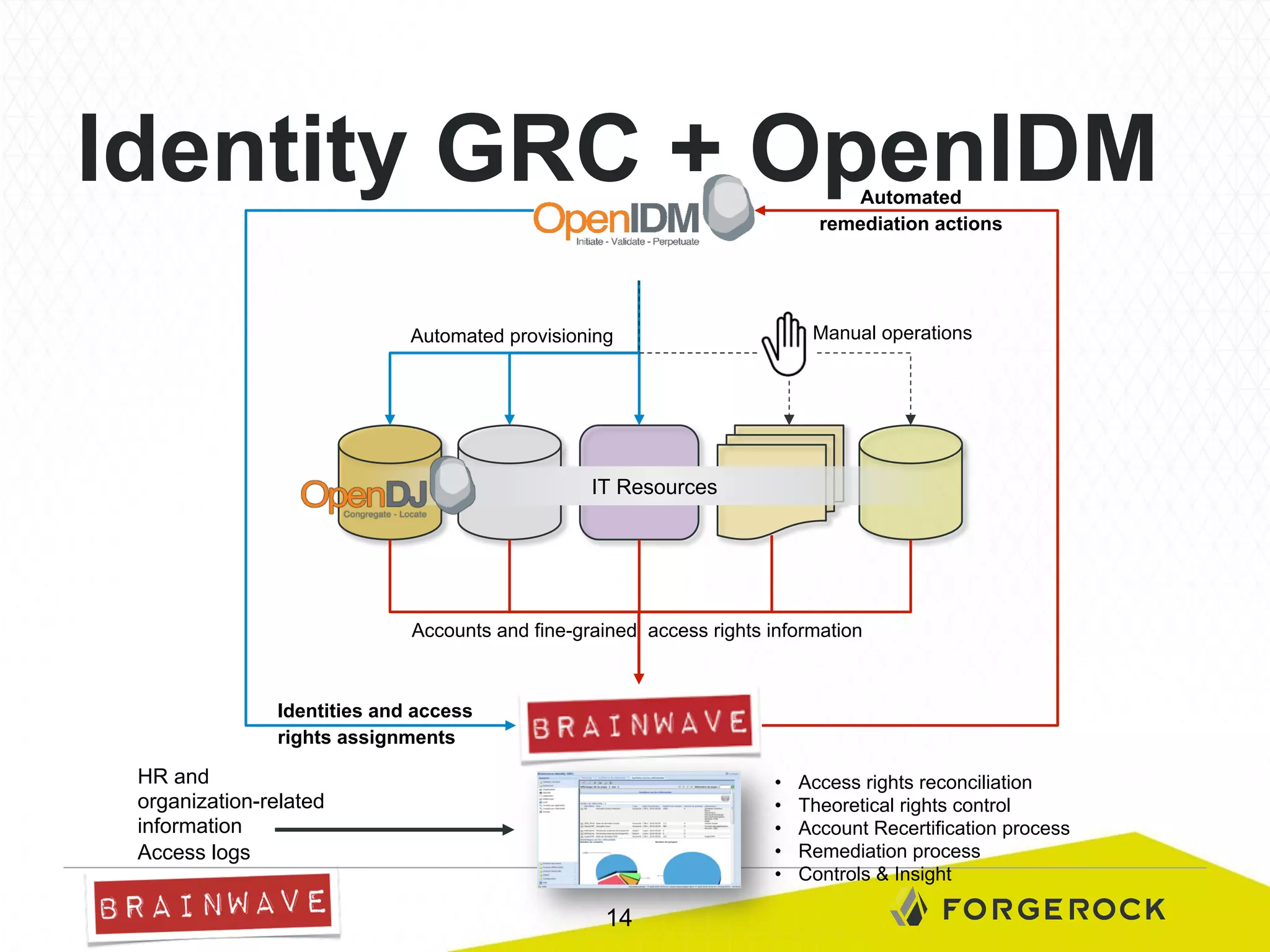
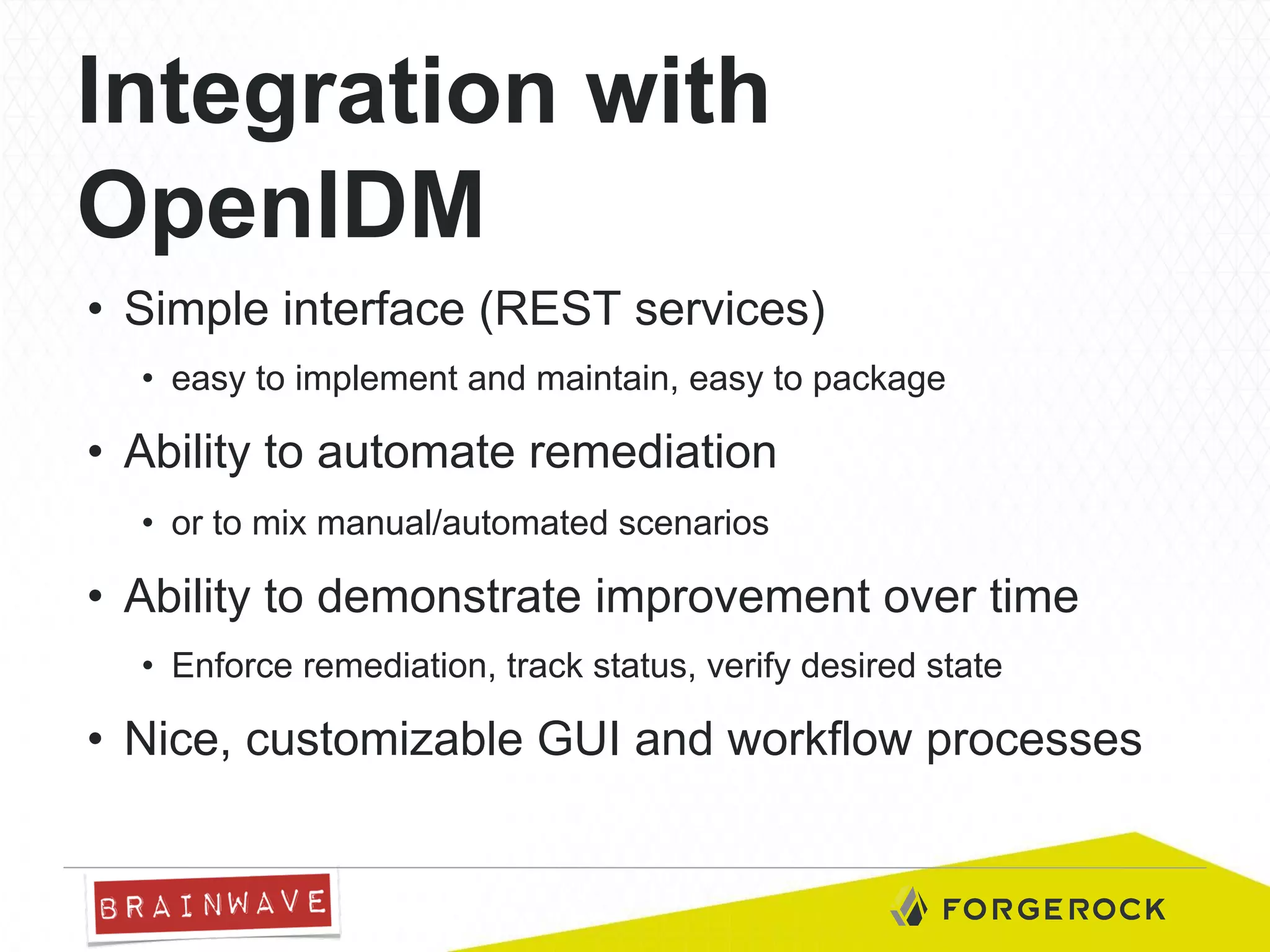
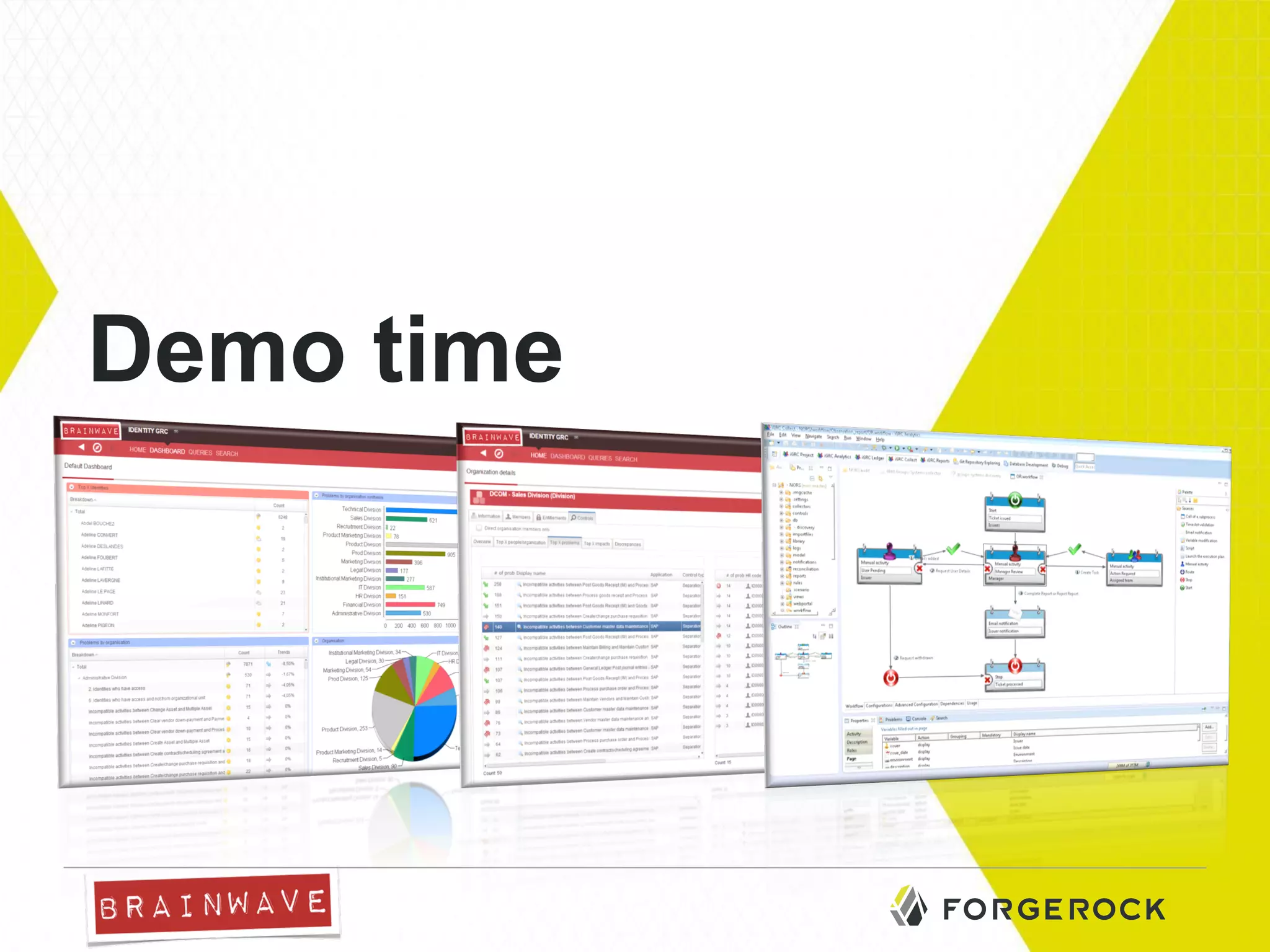
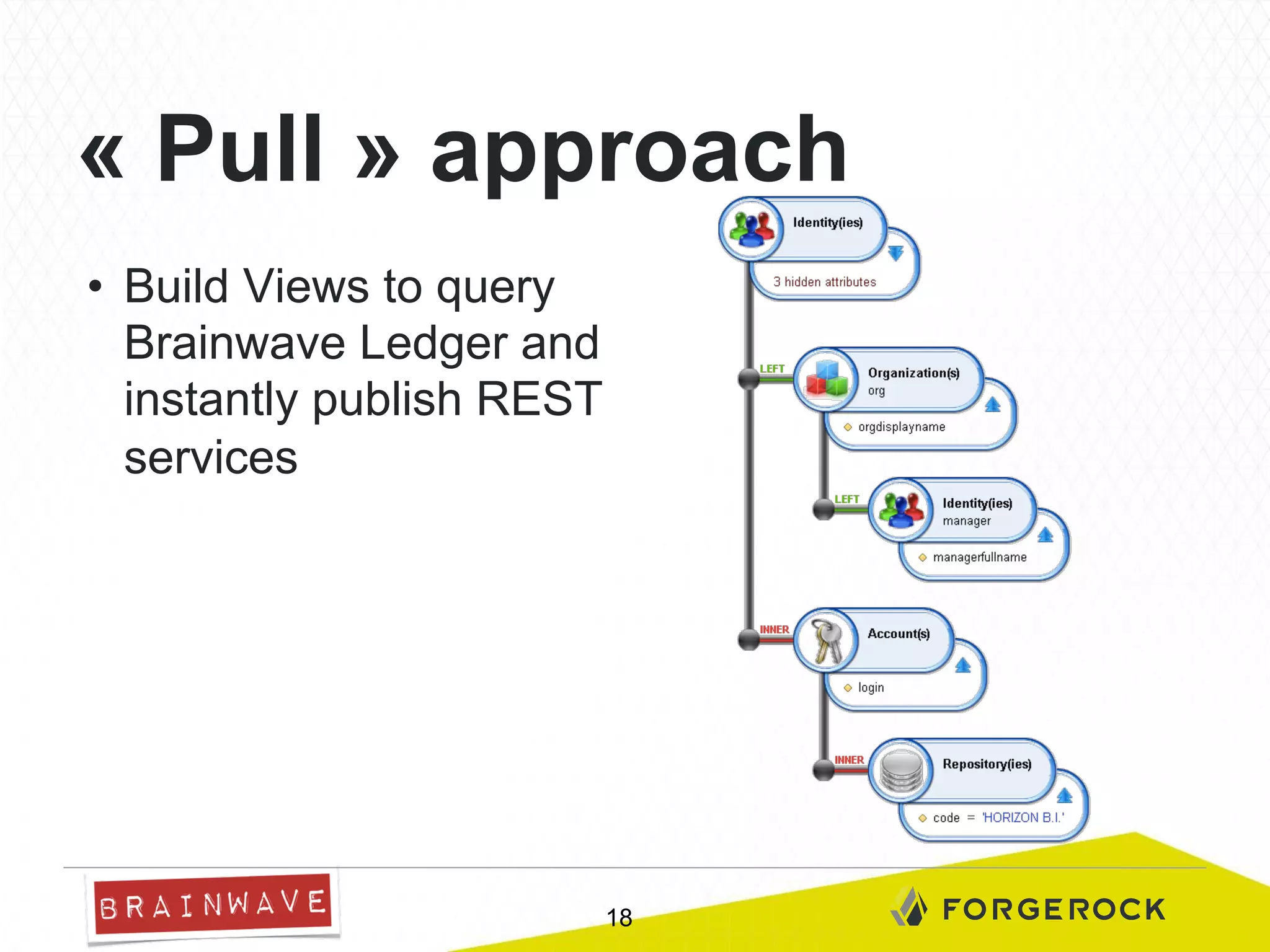
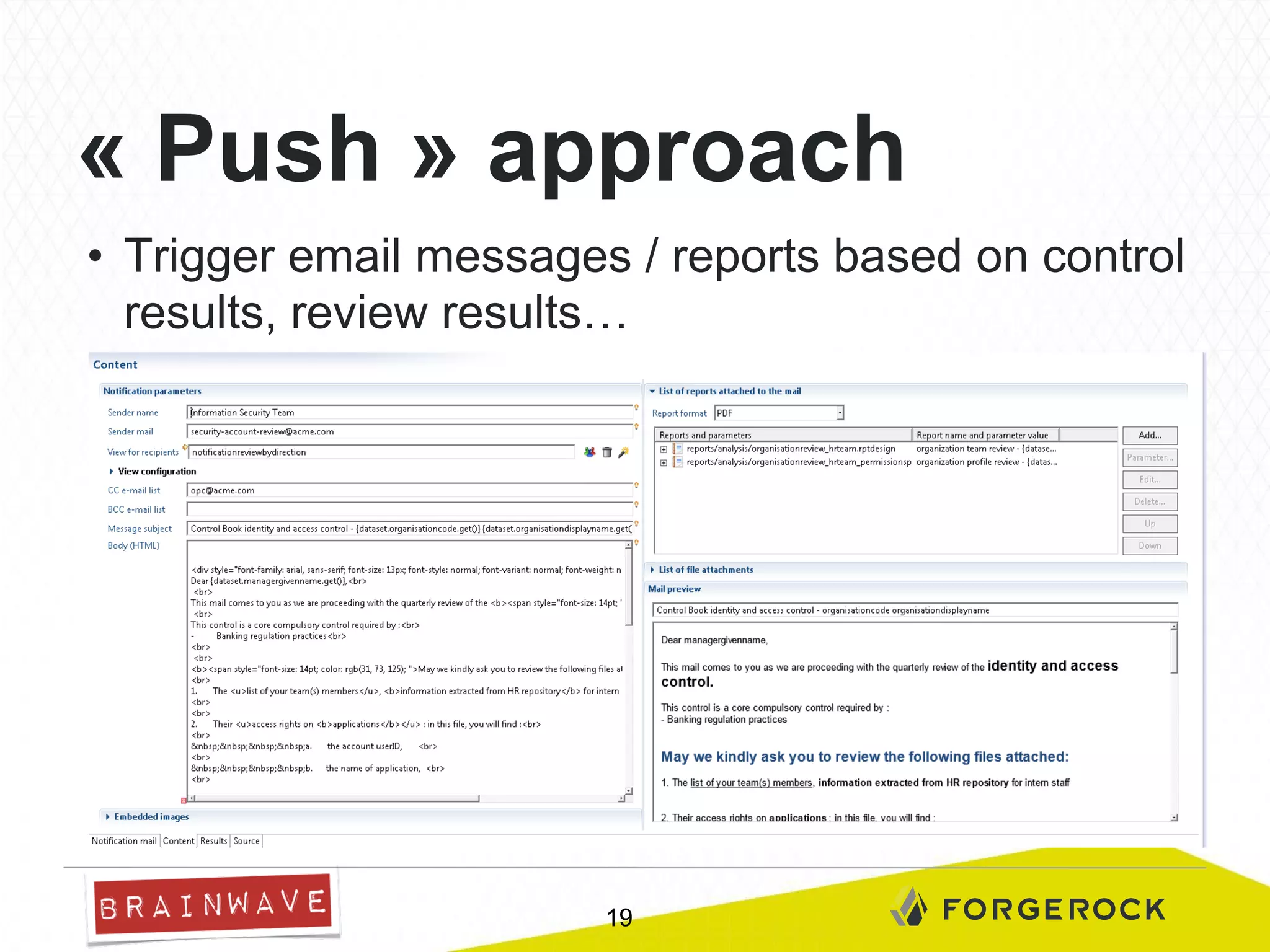
The document presents Brainwave's software solutions focused on access compliance and risk assessment, emphasizing the control of permissions across various resources. It highlights the importance of managing access rights to reduce compliance risks, as noted in Deloitte's security survey. Additionally, the software integrates with existing systems to automate remediation processes and improve operational reporting on access controls.